ICEDID, QAKBOT Spreads via PDF Attachments in Hijacked Emails

Ever since Microsoft disabled running macros from Office
files downloaded from the internet or email attachments, threat actors have
been compelled to find new ways to spread malware. Such as malware, ICEDID and QAKBOT, were both observed being delivered via malicious PDF attachments
in spam emails.
ICEDID, also known as Bokbot, is a banking trojan first
discovered in 2017 and is known to steal login credentials, victim's personal
data, and other information. Similarly, QAKBOT is also a banking trojan known to
steal sensitive information from its victims. Both malware strains are also
notorious for delivering other malware as an additional payload that often
leads to ransomware infections.
These banking trojans are typically distributed through
malicious spam emails with an attachment or a malicious link. In the past few
weeks, several waves of malspam emails with PDF attachments were seen
delivering either ICEDID or QAKBOT. The spam emails leverage a technique called
thread hijacking which basically uses stolen email threads from previously
infected victims to make their spam emails appear legitimate. However, the spam messages are generic messages that have nothing to do with the email thread.
While the two malware strains use very similar delivery
techniques, they nonetheless differ in their infection flow.
ICEDID
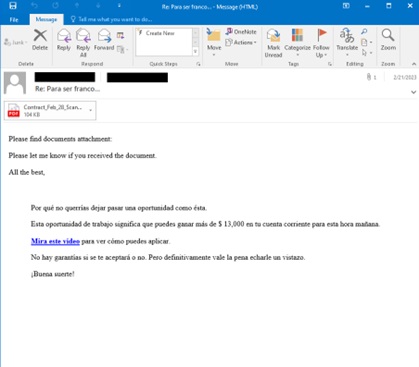

The PDF document in the ICEDID (detected as Trojan.PDF.ICEDID.A) spam instructs the user to open a password-protected document. Clicking the PDF usually redirects the user to a Firebase Storage link that will download a ZIP file. Then, the password-protected ZIP files can be opened using the password given in the PDF files. It will contain an executable file (detected as Trojan.Win64.ICEDID.AG) which will install the ICEDID malware in the user's computer system.
QAKBOT
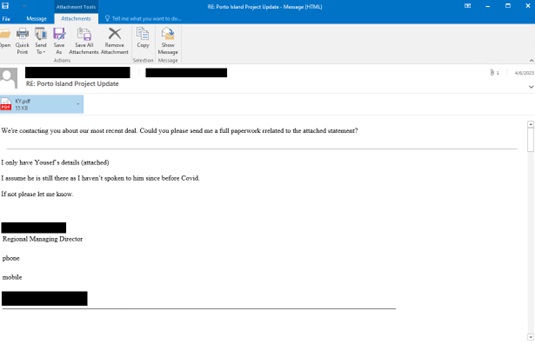

The QAKBOT PDF attachment (detected as Trojan.PDF.QAKBOT.J)
also lures the users to download an encrypted attachment. The PDF contains
links which usually lead to compromised websites that threat actors use to host
the malware. It will also download a password-protected zip file that contains
a malicious WSF script that will download QAKBOT DLLs to infect the victim's
computer.
These spam emails are already blocked by Trend Micro Email Security Solutions. However, we still advise users to avoid opening attachments from unsolicited emails.
- ENGINE:9.0.1004
- PATTERN:2.7576.000