FAREIT


Threat Type: Trojan Spy
Destructiveness: No
Encrypted:
In the wild: Yes
OVERVIEW
FAREIT was discovered in 2012 and has been undergoing changes to bypass anti-virus detection. It is now one of the most successful information stealers deployed in spam campaigns. The source code of the malware has been leaked publicly, enabling cybercriminals to use it in their attack campaigns.
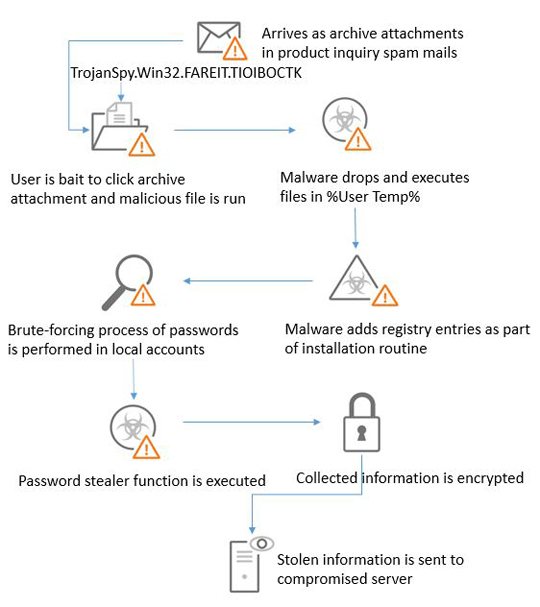
The current spam campaign of Fareit involves emails with order confirmation or contract, product inquiry and product order request sent to marketing officers of different companies. The malicious spam uses different file extensions such as .iso, .bat, .com, .cab or .scr attachments. This information steales sends the data it gathers from its victims to a compromised server.
Its most common routines include:
- Steals stored account information used in different installed File Transfer Protocol (FTP) clients or file manager software
- Steals stored email credentials of different mail clients
- Gets stored information such as user names, passwords, and hostnames from different browsers
- Performs brute forcing capabilities on local accounts based on acquired password list
- Replicates other Remote Desktop Protocol (RDP) utilities’ mutexes to mask execution in the background, then deletes itself after execution
- Downloads additional malware payload
It is capable of the following:
- Information Theft
- Download Routine
FAREIT typically follows the infection chain below: