Guide to Network Threats: Strengthening Network Perimeter Defenses with Next-generation Intrusion Prevention
Enterprises currently face an exciting era filled with new opportunities and innovations, with the coming of 5G, expanding IoT environments, and advancements in artificial intelligence. Unfortunately, new technology also introduces new threats in addition to existing ones.
This calls for the constant need to reevaluate the cybersecurity measures an enterprise has or needs to reap the full potential of new technology. It isn’t a simple question of installing a security solution, as all organizations and individuals must already be implementing some form of security measure. It is a question of whether current network perimeter defenses are resilient enough to withstand major attacks or if they are simply “good enough” defenses for basic threats. Industry-specific needs and the reality of attacks that can undermine “good enough” defenses emphasizes the need to redefine network perimeter defenses with next-generation intrusion prevention.
Some organizations might equate the right level of security to the application of current solutions such as next-generation firewall (NGFW). However, when it comes to choosing the right security tools, it is also important to look at the kind of threats enterprises face today, which next-generation intrusion prevention systems (NGIPS) could help cover.
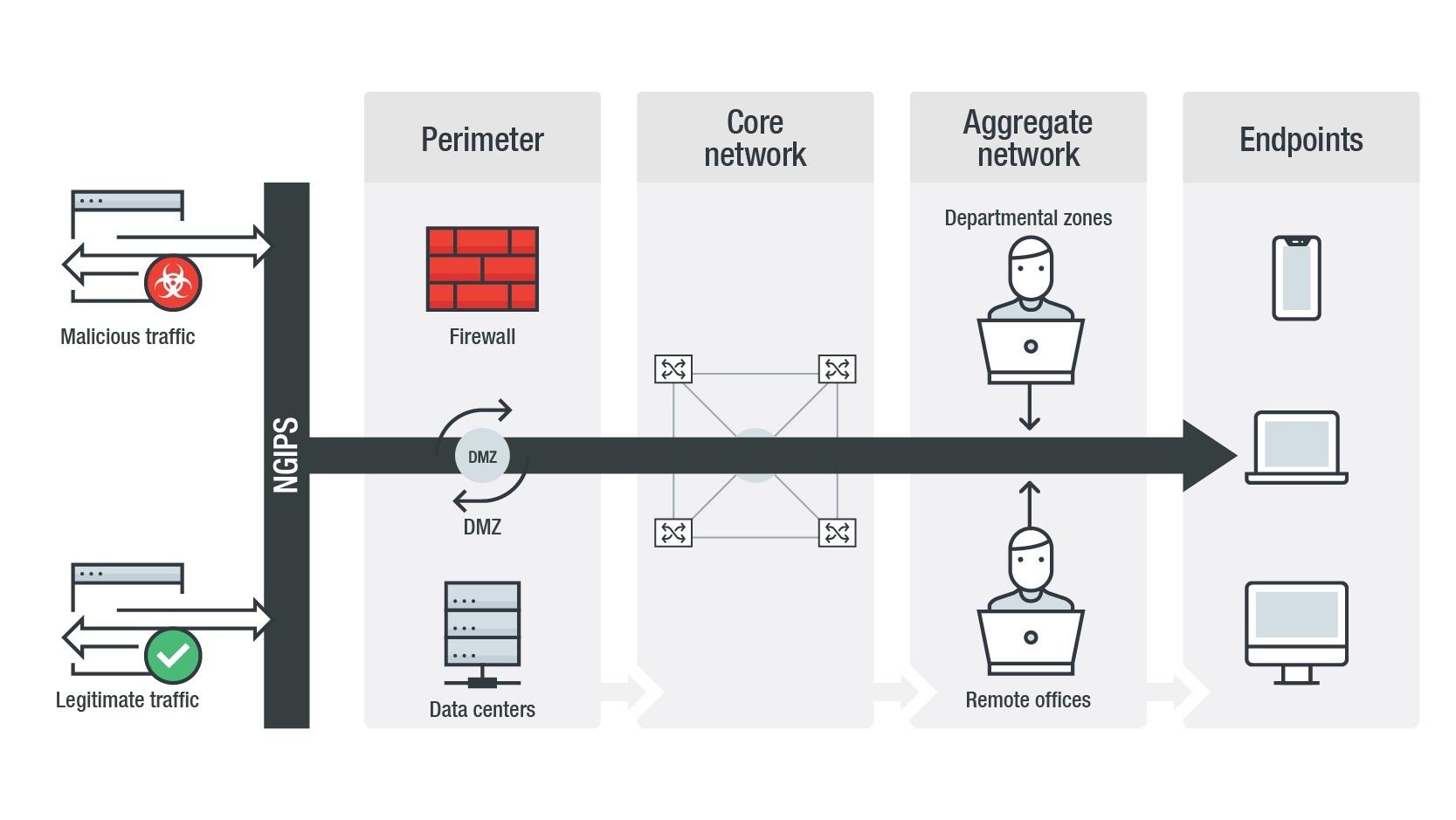
What are the network threats to consider?
Different forms of malware
Malware is a familiar and constant network threat. Malware families may decrease in activity, but the risk never truly disappears, as evidenced by the detections for ransomware families last year. Despite the general downward trend of ransomware families, detections for the infamous WannaCry family remained stable. This trend continued to the first quarter of 2019, as WannaCry garnered 42,050 total detections in March — a huge gap compared to the 7,959 combined total detections of the other ransomware families. Ransomware families like LockerGoga and Ryuk have also caused some recent shutdowns, with an uptick of Ryuk detections in early 2019.
In addition, when certain kinds of malware attacks die down, threat actors readily use other methods such as cryptocurrency-mining. Our more recent detection confirms this trend — Coinminer had the most detections in March with 63,116 total detections, which puts it just ahead of WannaCry. We also saw an increased use of fileless threats, which complicates detection as it frequently necessitates unique methods like traffic monitoring or sandboxing.
Considering such threats, enterprises can benefit from the best-of-breed breach detection system with malware sandboxing capabilities of NGIPS. The continuing adoption of cloud technology can also usher an increase in asymmetric traffic, where return traffic does not go through the same security engine. Faced with this possible reality, NGIPS is at an advantage when compared to NGFWs, as the former detects threats using packet level information without relying on flow information while the latter must implement complex flow-based architectures to detect threats within asymmetric traffic.
Vulnerabilities
Like malware, vulnerabilities are an incessant issue for network security. Old and new vulnerabilities present considerable risks to networks, depending on the security protocols and solutions implemented to defend against them. Meltdown and Spectre are two vulnerabilities that gained notoriety last year. These processor-level vulnerabilities affected a slew of different microprocessors and spawned new CPU attacks.
Malware that exploit vulnerabilities have become a significant threat, especially with the growing number of smart devices going online. Modified versions of Mirai (a threat found in Linux platforms), for example, have been used to exploit vulnerabilities in routers. Even disclosed and patched vulnerabilities come with potential risks as cybercriminals exploit such vulnerabilities on the assumption that some users don't immediately apply released patches, if at all.
While we saw a decrease in the number of vulnerabilities early this year, SCADA vulnerabilities comprised about a third of all vulnerabilities we saw from January to March. NGIPS can be a preventive measure against attacks from known and undisclosed vulnerabilities. For undisclosed vulnerabilities, NGIPS utilizes pre-disclosed filters. On average, this pre-disclosure feature can protect users from CVE-related threats for over 70 days before vendors publicly disclose them.
Threats to specific industries
The growing connectivity of critical infrastructures such as energy and water means that cyberthreats have a greater impact not only on these industries but also on the rest of the supply chain. In 2017, attackers used Triton malware to target a certain type of industrial control system (ICS), and it continues to be a threat to critical infrastructures. Vulnerabilities in these control systems could be used to deploy malware, as proven by the Stuxnet worm that was deployed via SCADA vulnerabilities back in 2010. Many of these had cascading effects, from downtime costs to lengthy power outages.
[Read: The State of SCADA HMI Vulnerabilities]
Aside from these mentioned cases, other critical infrastructures like healthcare, finance, and food production can and have been subjected to cyberattacks. Industries like healthcare handle sensitive information, making it a tempting target to exploit. Possible areas for attack include vulnerabilities in connected devices and even the protocols used in the industry, like in a recent discovery of a flaw that could allow the use of the DICOM medical imaging standard in an attack. Banking and finance industries attract cybercriminals because of its immediate monetary connection. In addition, several components related to banking can be susceptible to data breaches as well social engineering tactics.
The importance of security for such critical systems is exponentially multiplied because it also prevents the effects from cascading to other connected industries. NGIPS can provide additional protection to critical infrastructures and vulnerable applications through techniques like virtual patching. Again, pre-disclosure filters can play a big role in defending against all forms of vulnerability exploits ahead of a released patch. NGIPS helps protect even legacy applications and end-of-life systems that are still found in certain industries like healthcare.
Data breach
The challenge with data breaches is that it could be caused by different factors, from an active external attack to internal human error. Once a breach has happened, containing its cascading effects presents another challenge.
[Read: Data Breaches 101: How They Happen, What Gets Stolen, and Where It All Goes]
According to a Ponemon study, the average cost of data breach is US$ 3.86 million, and the average time it takes to identify a breach is 197 days. Stricter data regulations, like those outlined in the GDPR, further raises the stakes.
When it comes to data breaches, the cost depends on how fast they can be identified and contained. Again, a best-of-breed breach system will prove useful. Since most hackers build attacks on the assumption that a network’s internal security controls are less secure than its perimeter, it should follow that data breach security defenses should put equal focus on both perimeter traffic (ingress-egress) and lateral movement traffic (east-west), which is a characteristic of NGIPS.
Other attacks and the evolution of threats
Unfortunately, threat actors constantly look for the next big thing to exploit while still falling back on old tricks when the opportunity arises. While it is important to be knowledgeable of each of the threats listed here, being aware of the trends in the threat landscape is equally critical for creating adaptable defenses.
Aside from the increase in fileless malware, we also found that messaging threats grew in prominence. The continuing development in the field of IoT makes threats against it a considerable concern, especially for those who have or plan to integrate smart technology in their processes.
A solution that is versatile and less taxing to network performance can help defend against the evolving world of threats. NGIPS fit these characteristics better than NGFW. For one, NGIPS focus on threat-specific safeguards and policies based on threat assessments, unlike NGFW, which is based on traffic control safeguards with policies based on business and compliance rules.
This makes NGIPS more versatile as it can afford to have a default allow policy for traffic. NGIPS will only block malicious traffic, whereas NGFW will only allow traffic for which it has set rules. In addition, when it comes to visibility from the threat actor side, NGIPS are layer 2 devices, which may make it transparent and something of a surprise for attackers.
How can an enterprise achieve the right level of security?
According to our research, enterprises estimate an 80% likelihood of a successful cyberattack against them in the next 12 months. This kind of awareness is important for industries, but it's only beneficial if they use this knowledge to reduce the chances of a successful attack or mitigate its effects.
When evaluating security measures, a level that's "good enough" can only ever really be determined by an accurate estimate of one’s own enterprise and the threat landscape it has to navigate. Looking externally at what the industry faces, and internally at the specific needs of the organization, can help create a unique security architecture that is both adaptable and robust. Tools like NGIPS can help build this architecture, in addition to other facets like a good security culture within the enterprise and a comprehensive knowledge of cyberthreat trends and evolving technologies.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One