Before Masque and WireLurker: iOS Threats That Cracked the Walled Garden
 Just this month, a lot of media coverage was done on the “Masque Attack”, a vulnerability that allowed cybercriminals to penetrate iOS devices and replace installed apps with fake ones. Though Masque was already reported in a conference in July, it's getting a lot more attention now mostly because its routines are similar to the WireLurker malware that affected both OS X and iOS devices, but with seemingly more serious consequences.
Just this month, a lot of media coverage was done on the “Masque Attack”, a vulnerability that allowed cybercriminals to penetrate iOS devices and replace installed apps with fake ones. Though Masque was already reported in a conference in July, it's getting a lot more attention now mostly because its routines are similar to the WireLurker malware that affected both OS X and iOS devices, but with seemingly more serious consequences.
The emerging problem with iOS here, partly brought to light by the Masque vulnerability, is the use of unencrypted app data. Should Masque allow cybercriminals access to iOS devices, and these devices have one of the previously tested popular iOS apps that don’t encrypt their data, users are likely to get even more sensitive information stolen. Researchers found users of a widely used email client and two IM apps among those vulnerable to this scenario.
[Read: The Other Side of Masque Attacks: Data Encryption Not Found in iOS Apps]
No Masque for the Buzz
Much like the WireLurker threat, the initial buzz around Masque is largely a result of it being among the first iOS threats to be able to attack even non-jailbroken devices. While there have been a number of iOS threats throughout the years, they mostly targeted jailbroken devices. In the case of Masque and WireLurker, even non-jailbroken devices are put at risk.
The way that the iOS environment is built is quite similar to a walled garden, where devices are only allowed to download digitally signed apps from the official Apple app store. This may not work for big companies that need to develop and rapidly deploy apps to their employees. To address this need, Apple created the “Developer Enterprise Program,” which assigns an enterprise with their own signing key so they can distribute apps through iTunes or their own app store. This process is better known as “enterprise provisioning” and this is how both the Masque and WireLurker threats get inside non-jailbroken devices.
“When users try to install an app via ‘enterprise provisioning’, a pop-up window would show up to ask users whether they trust the previously untrusted developer. If users agree to trust the developer, the app would be allowed to install,” notes Trend Micro threat researcher Spencer Hsieh.
Enterprise provisioning is problematic because the apps can be installed even in devices IT can’t control, the apps are not audited by Apple, and developers can exploit code in their own apps. In the case of WireLurker, a mobile app developer lost control of their signing certificate, which was used to allow malicious apps to be signed and therefore, trusted.
Spotting Cracks in Apple’s Walled Garden
Despite the security measures practiced by the Apple App Store, a number of other iOS threats have gone before Masque and WireLurker. Here are the times when iOS threats showed that a closed ecosystem for apps may not ensure total app security:
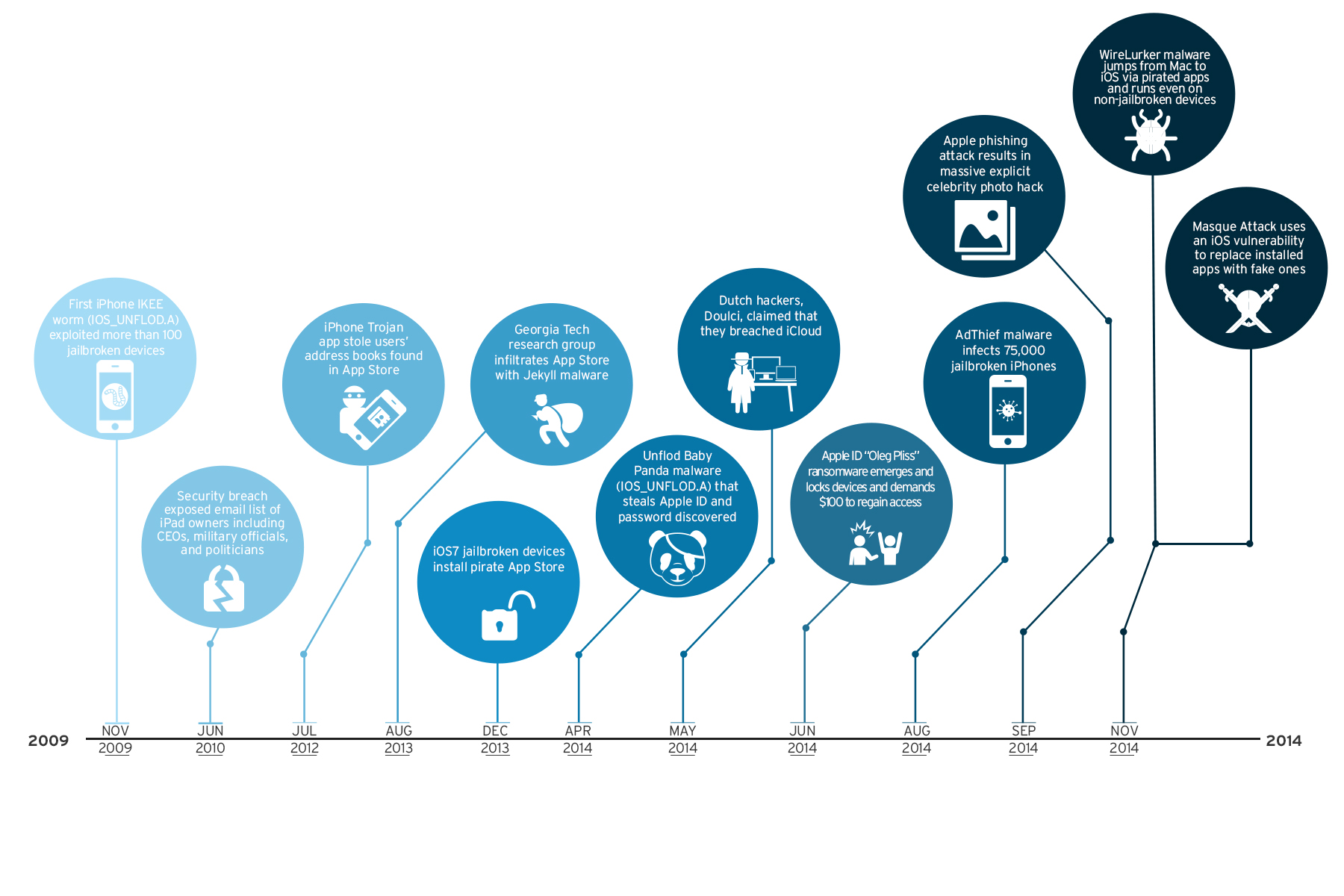
Timeline of iOS Threats
- When the first iPhone worm was discovered Imagine it was 2009 and you were randomly singing the catchy old tune “Never Gonna Give You Up” only to see its pop singer Rick Astley’s face on your iPhone device’s wallpaper. This is exactly how a number of device owners in Australia felt after the first iPhone worm, Ikee, broke into their devices. The Ikee worm affects jailbroken iPhones whose owners installed the Secure Shell (SSH) utility and did not change the default password, “alpine.”
- When CEOs, military officials, and politicians had their emails exposedBack in 2010, a breach exposed the email addresses of 114K early iPad 3G adopters, which included CEOs, military officials, and politicians. It was believed that information on all iPad 3G owners at the time were exposed, though researchers attributed the flaw to a major partner telecom company. A security company that points out software flaws exposed this issue in iPads by sending out a script on the telecom company’s site. Using the serial numbers from SIM cards (ICCID), the researchers were able to get the email addresses associated to users.
- When a Trojan app stole users’ address booksThe first malware to actually slip past the strict auditing of the Apple App Store, the “Find and Call” app is a Trojan that sends SMS spam to the victims’ address book contacts. The app developers dealt with issues of the app being malicious and in violation of user privacy. Notably, privacy issues on apps accessing peoples’ address books were raised closely before the incident, when the apps Hipster and Path were found uploading address book details to their servers.
- When a Georgia Tech research group infiltrated the App store with malwareIn 2013, researchers from Georgia Tech experimented with iOS security and published the seemingly benign “Jekyll” app on the App Store. In the paper, “Jekyll on iOS: When Benign Apps Become Evil," which was presented at the USENIX Security Symposium in Washington, D.C., the researchers were able to remotely launch the app and have it perform malicious tasks such as post tweets, take photos, steal device identity information, send email and SMS, attack other apps and exploit kernel vulnerabilities.
- When jailbroken iOS7 devices installed a pirate App storeWhen a team known for giving jailbreak instructions for iOS users released a jailbreak for iOS 7, users flocked to follow, only to find that an alternative app store containing cracked apps has been installed on their phones. The pirate store that contains cracked versions of real apps from the official App Store only appears if the device is set in Chinese.
- When the Unflod Baby Panda malware stole Apple ID and passwordA malware dubbed “Unflod Baby Panda” was found affecting jailbroken devices in April this year. It was unclear exactly how the malware got into the devices, but once it got in, the malware can listen into secure connections and try to steal Apple IDs and passwords. This threat further inculcates into iOS device owners the feeling that untrusted sources and pirated software are typically not the best way to go if they want to ensure the safety of their data.
- When the Dutch hackers Doulci claimed to breach iCloudA team of Dutch hackers calling themselves “Doulci” declared the breach of iCloud systems in May of 2014. The team first bought thousands of stolen devices so they can unlock them and access the data in the iCloud accounts for each. In one tweet, a member of Doulci claimed to have processed more than 5,700 devices in five minutes.
- When the AdThief malware infected 75,000 jailbroken iPhonesJailbroken devices were hit yet again when the AdThief malware came out in August this year. The said malware hijacks advertising revenues by siphoning them to the cybercriminals’ accounts instead of to the developers’. AdThief reportedly impacted around 22 million ad displays on 75,000 jailbroken devices. An independent security researcher discovered the security issue in March and was continued to be studied by another researcher months after, thus the delay in news reports.
- When phishing attacks leaked explicit celebrity photos In a widely publicized series of phishing attacks against iCloud accounts, explicit and private photos of a number of popular celebrities were exposed and left out in a forum for public viewing. Apple denied having technical flaws in their system and otherwise faulted human error and targeted guessing for the exposure of the accounts, which included that of Jennifer Lawrence, Ariana Grande, and Kate Upton.
The Core of Apple Threats
Apart from iOS threats, we have also previously reported a few notable and notorious threats that target the Mac OS. These and the iOS threats combined show the growing interest of cybercriminals in Apple users. Owing to the fact that the company attracts a certain group of high-paying customers for premium products, tapping into this market can be quite lucrative.
While the total count for Android threats reach millions, threats to Apple products may appear too few to even worry about. However, ultimately, it is this mindset of complacency that often leads to drastic consequences. The Masque threat, for one, is a reminder that relying on the operating system's closed setup isn't enough to protect one’s data. Users still have to be proactive against threats no matter what the platform.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One