 Download Threats to Manufacturing Environments in the Era of Industry 4.0
Download Threats to Manufacturing Environments in the Era of Industry 4.0
In the fourth industrial revolution, commonly referred to as Industry 4.0, cyber-physical systems (CPSs) combine physical components and digital networks to change how manufacturing companies automate processes and information sharing. Boosted by the industrial internet of things (IIoT), machine learning, and big data, Industry 4.0 fosters significant improvements to data exchange and industrial control in the manufacturing industry, as embodied in so-called “smart factories.” However, now that information technology (IT), operational technology (OT), and intellectual property (IP) assets are being integrated, a whole new range of security issues also arises.
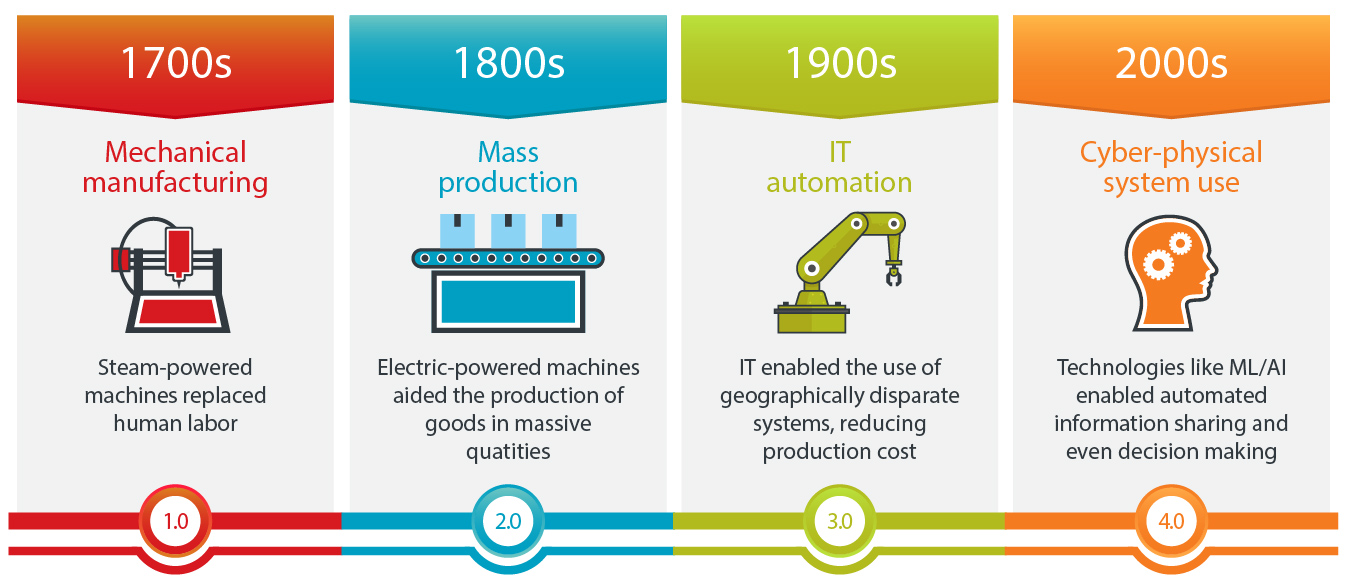
From mechanical manufacturing (Industry 1.0) to cyber-physical system (CPS) use (Industry 4.0)
As it continues to adopt Industry 4.0, the manufacturing industry can be considered as an appealing target for attackers. The convergence could be seen by attackers as an opportunity to move laterally across a manufacturing network, jumping across IT and OT systems for their malicious activities. They can take advantage of systems for industrial espionage, IP leakage, or even production sabotage. We take a look at some of the factors — risks to physical and digital manufacturing components — that can lead to these and other instances of compromise.
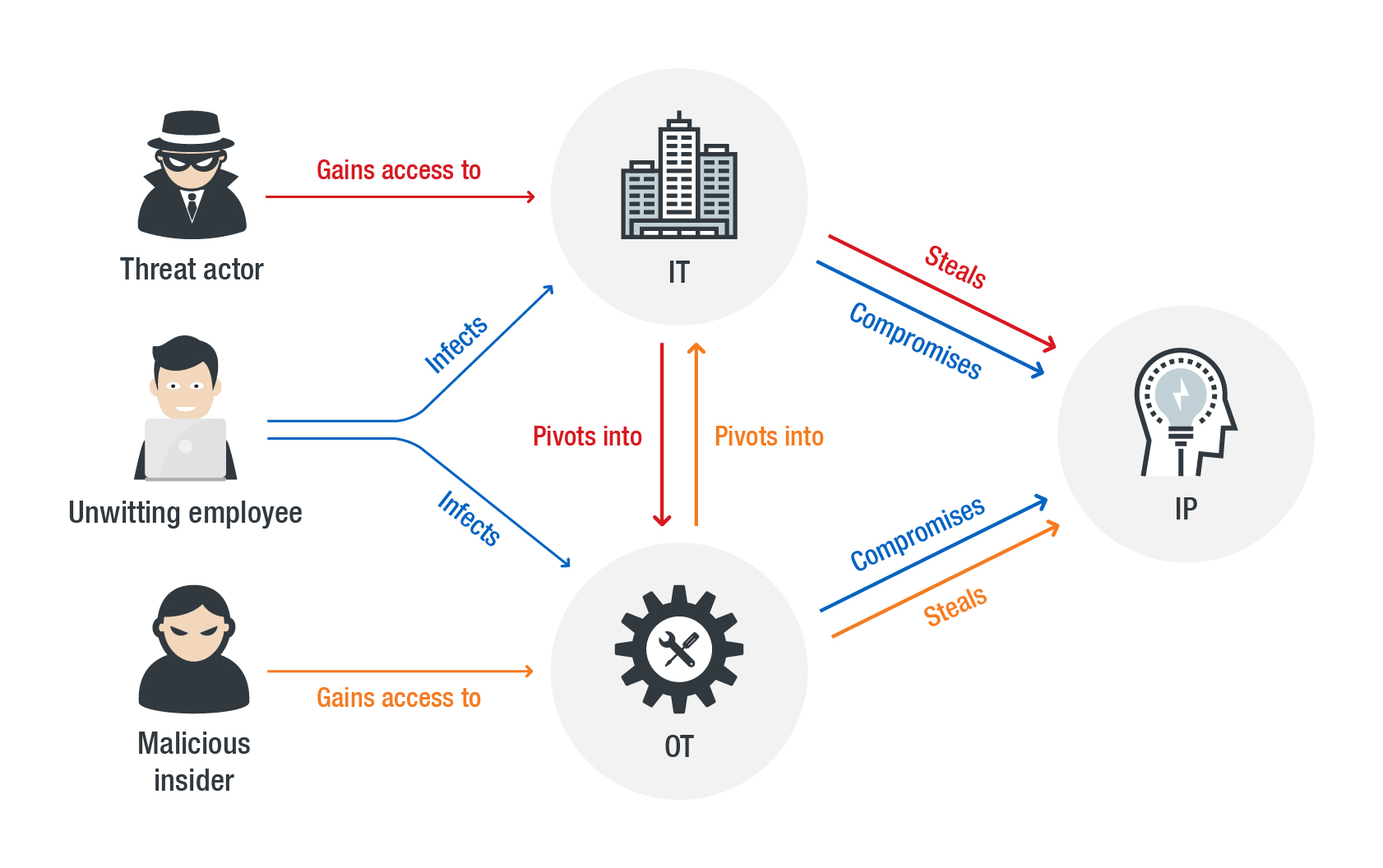
How threats can figure into the IT, OT, and IP convergence
Outdated Systems, Unpatched Vulnerabilities, and Poorly Secured Files
152,598
- Windows 7
- Windows 10
- Windows 8.1
- Windows XP
- Windows XP 64-bit
- Windows 8
- Windows Vista
- Windows 2000
757,989
- Windows 7
- Windows 10
- Windows 8.1
- Windows XP
- Windows XP 64-bit
- Windows 8
- Windows Vista
- Windows 2000
Distribution of operating systems in the manufacturing industry (left)(top) and in other industries (right)(bottom), based on data from the Trend MicroTM Smart Protection NetworkTM infrastructure for the period from July to December 2018
Percentage point differences between distribution of operating systems in the manufacturing industry and that in other industries, based on data from the Trend Micro Smart Protection Network infrastructure for the period from July to December 2018
Looking at data from the Trend MicroTM Smart Protection NetworkTM infrastructure, we found that the use of old and unsupported software like Microsoft Windows XP is relatively pronounced in manufacturing environments. As a result, old network-based worms such as Downad (aka Conficker), for instance, were found to have high detections in these environments. And since Windows XP will no longer be receiving security updates, system administrators will not be able to rely on patching to address security issues.
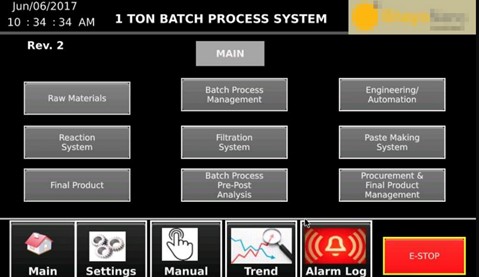
Exposed overview page displaying a batch process system and emergency stop (e-stop) option
OT systems could also be in a situation where security patches are not applied. As these systems are expected to be operated with minimal interruptions, updates may be considered as something that interferes with business continuity.
It is also worth noting that because many industrial control systems (ICSs) such as programmable logic controllers (PLCs), along with the human-machine interfaces (HMIs) used with them, are designed for isolated environments, adequate cybersecurity measures may not be in place for them. This makes it likely for ICSs to be exposed on the internet as a result of the increasing connectivity between OT and IT networks.
Trend of vulnerabilities affecting manufacturing-related equipment reported to the Industrial Control Systems Computer Emergency Response Team (ICS-CERT)
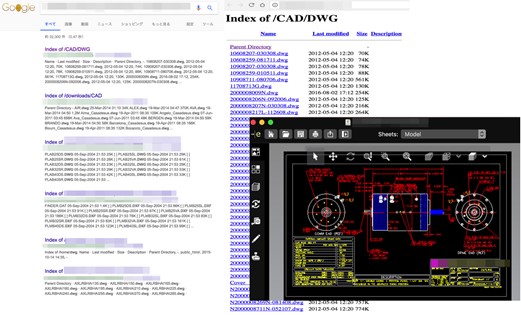
Search results for CAD files via open-source intelligence (OSINT)
Aside from publicly exposed ICSs, manufacturing companies also need to be wary of ICS components being vulnerable themselves. Manufacturing-related equipment has been reported to have increasing vulnerabilities over the years. And attackers have easy access to publicly available exploits and can deploy them anytime.
But perhaps what makes the manufacturing industry attractive for attackers is the involvement of IP. Malicious actors could be motivated to steal intelligence on processes, products, or technologies in use, which may include blueprints of confidential designs, secret formulas, or detailed assembly processes. Computer-aided design (CAD) or document files, for instance, contain proprietary information, and these can be illicitly obtained for the production of counterfeit goods, or even infected or trojanized to enable attackers to gain access to critical systems.
Security for Industry 4.0: Recommendations for Manufacturing Environments

Adopting Industry 4.0 means not only interconnecting IT and OT networks to build smart factories; it also means having shared responsibilities between IT administrators and OT engineers. These include accounting for assets such as equipment, underlying platforms, and protocols or services in use; assessing them for their criticality in the overall operations; and applying the appropriate protection to each asset.
In addition to ensuring that the aforementioned tasks are carried out, manufacturing companies also need to see to it that IP assets, such as technical documents and design files, are being shared, processed, and otherwise handled securely.
Manufacturing companies can avoid common security issues by implementing basic best practices such as the following:
- Individuals who are granted access to files and systems should be identified and given the most restrictive permissions. If they should not be able to modify information, read-only access should be given to them.
- The IT machines and production machines that are allowed to communicate with one another should be identified. There should be restrictions as to which devices in the IT network should be capable of information exchange with which devices in the OT network.
- Unnecessary services in the network should be disabled. Doing so can help prevent exploitation of vulnerable services.
Security is critical to the success of Industry 4.0 adoption. The resilience of production processes strongly depends on the manufacturing companies’ awareness of the current threat landscape and the employed security framework for protecting against attacks.
In our research paper, “Securing Smart Factories: Threats to Manufacturing Environments in the Era of Industry 4.0,” we discuss the most noteworthy threats to the manufacturing industry, identify the weak points that attackers may take advantage of, and provide relevant security recommendations.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- The State of Criminal AI: Market Consolidation and Operational Reality
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One