Cloud-Based IoT Solutions: Responding to Traditional Limits and Security Concerns
 The internet of things (IoT) pertains to the connection of sensors, devices, and other objects, sending and receiving data for communication of requests and commands through the internet and other networks. Given this traditional definition and the decades since the conception of the IoT, it’s no surprise that there has been a steady increase in the number of interconnected “things.” This has naturally resulted in greater amounts of data gathered, which in turn have made the handling and storage of information more challenging. The growing demand for fast product developments for end users’ conveniences and the subsequent rapid deployments have necessitated advancements in both hardware and software. And the need has emerged for data processing and analysis with the security infrastructure to match the increasing complexity of data associated with the IoT.
The internet of things (IoT) pertains to the connection of sensors, devices, and other objects, sending and receiving data for communication of requests and commands through the internet and other networks. Given this traditional definition and the decades since the conception of the IoT, it’s no surprise that there has been a steady increase in the number of interconnected “things.” This has naturally resulted in greater amounts of data gathered, which in turn have made the handling and storage of information more challenging. The growing demand for fast product developments for end users’ conveniences and the subsequent rapid deployments have necessitated advancements in both hardware and software. And the need has emerged for data processing and analysis with the security infrastructure to match the increasing complexity of data associated with the IoT.
In the face of challenges brought about by the continuing expansion of the IoT — a trend that is expected to be further amplified by the coming 5G era — many organizations have turned to cloud computing, particularly cloud-based IoT solutions. Built on the idea of providing “rented storage space,” cloud-based IoT solutions can respond to organizations’ needs in regard to integration, processing, scalability, and the all-important consideration of security.
IoT security has rightly become a focal point in discussions among manufacturers, developers, and organizations: Do service providers comply with the requirements of data regulations such as the General Data Protection Regulation (GDPR)? Can product updates be released as soon as vulnerabilities are reported or disclosed? Will migration to cloud servers be more efficient and secure in the long run? These and other questions warrant close examination and critical discussion by IoT adopters, including those involved in the development and implementation of cloud-based IoT solutions.
Comparing traditional IoT and cloud-based IoT solutions
Cloud service providers have proposed solutions to organizations according to their different business needs. And as more enterprises move their workloads to the cloud to reap the infrastructure’s benefits, these providers are also able to expand their product features to explore more business opportunities. Enterprises that have already availed of cloud services are offered more solutions specific to the IoT, requiring lower costs than what it normally takes to get into the IoT market — without dramatically affecting existing product infrastructure at that.
Vendors also get to redefine some business aspects for improvement, such as responding to existing security gaps in the IoT market. With the presence of API management resources at their disposal, an environment similar to one involving software as a service (SaaS) is ready for development, as well as a mechanism for certification and authentication management. Based on our research, cloud service providers can translate their expertise into cloud-based IoT developments. The table below compares the advantages and disadvantages of traditional IoT and cloud-based IoT solutions across different areas of concern — effectively highlighting the potential growth the latter can offer for enterprises.
| Traditional IoT | Cloud-based IoT | |
| Server | ||
|
Advantages |
|
|
|
Disadvantages |
|
|
| Data storage | ||
|
Advantages |
|
|
|
Disadvantages |
|
|
| Authentication | ||
|
Advantages |
|
|
|
Disadvantages |
|
|
| Connection | ||
|
Advantages |
|
|
|
Disadvantages |
|
|
| Device identification | ||
|
Advantages |
Not applicable. |
|
|
Disadvantages |
|
|
| Edge computing | ||
|
Advantages |
Not applicable. |
|
|
Disadvantages |
Not applicable. |
|
| Application isolation | ||
|
Advantages |
Not applicable. |
|
|
Disadvantages |
|
|
| Update channel (OTA) maintenance and software development kit (SDK) | ||
|
Advantages |
Not applicable |
|
|
Disadvantages |
|
|
Table 1. Comparison between traditional IoT and cloud-based IoT solutions for enterprises
Use case for benefits of cloud-based IoT solutions: Transport-sharing app
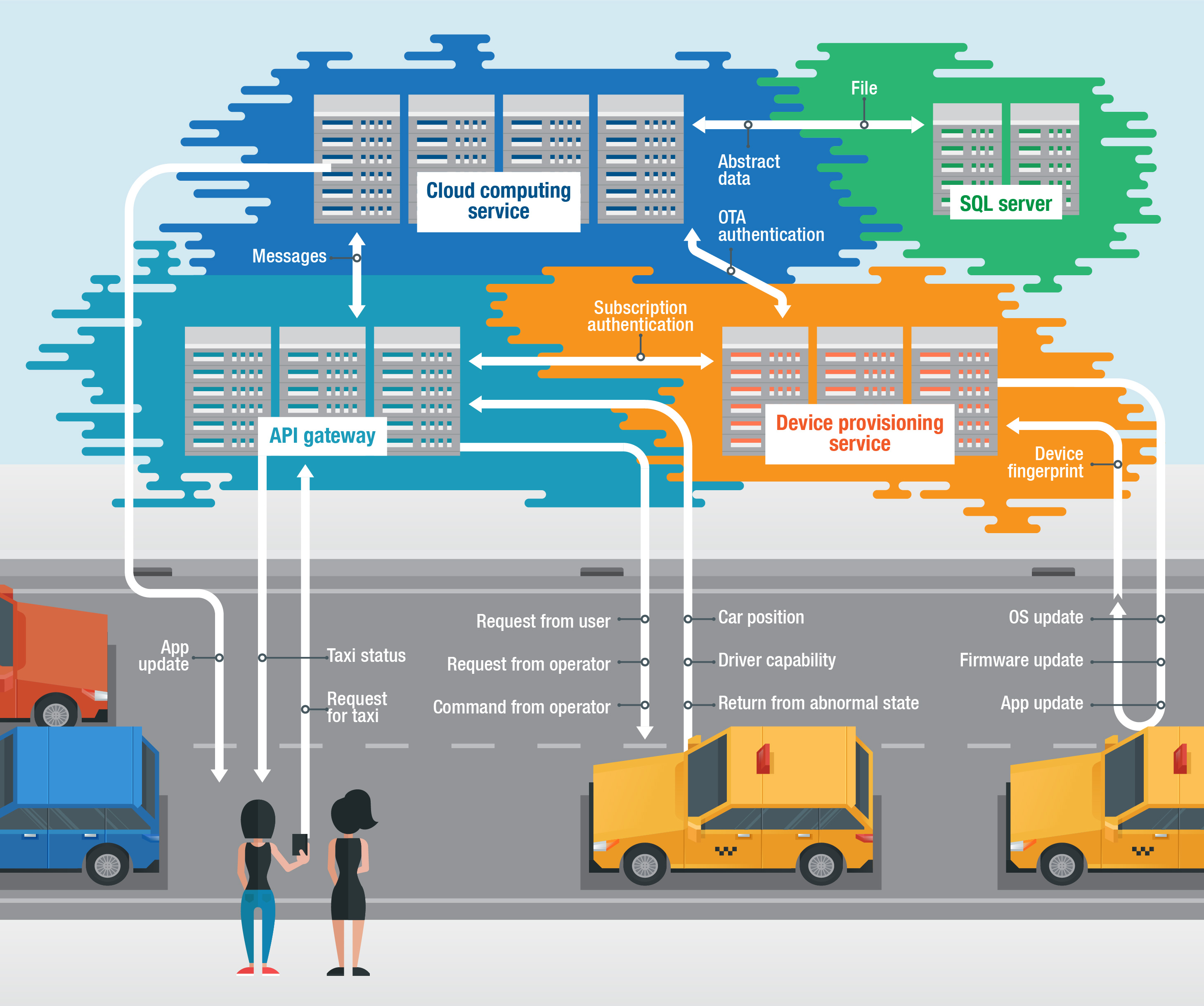
Figure 1. Transport-sharing app with a cloud-based IoT infrastructure
With the proliferation of IoT devices and the need to handle an exponentially increasing amount of data, enterprises can look into the developments afforded by cloud-based IoT solutions. Here we illustrate some of the benefits organizations can derive from adopting cloud-based IoT solutions. We take the case of a transport-sharing app as an example, specifically examining its scalability with cloud-based IoT features given the users and services it’s expected to deal with after its launch.
When necessary, the developers can scale up the app faster and easily account for the platform’s needed changes, such as time accuracy for both drivers and passengers. Since the platform can be treated as part of the IoT methodology — with the user, node, and edge found in the cloud as “loosely coupled architecture” — the cloud-based app can be designed to have periodic rewards and emergency returns. It can also have server-side anti-counterfeit/anti-spoofing features. Cloud-based IoT solutions are designed to use strict rule validations and hierarchical rights management to prevent unauthorized intrusion as the entire cloud environment can be compromised; without data or signal tests from the server terminal, commands do not follow through to the device or app.
Integrated with machine learning and artificial intelligence (AI), the app can constantly study the data for product development and improve drivers’ and users’ profiles. Since cloud-based solutions have multiple channels for communication, users and drivers can report their respective locations, speed information, and profiles in real time. These integrations can also help drivers in handling unexpected situations and condition violations, immediately warning them as needed either in real time or within a delay of 10 seconds. Downtime is reduced by 0.01% as new cloud-based solutions offer strong out-of-band capabilities to accommodate unexpected situations such as network and sensor signal changes.
Potential attack vectors in cloud-based IoT infrastructures
As evidenced by the disadvantages noted in the comparison table above, cloud-based IoT infrastructures are far from perfect. This is further demonstrated by several potential attack vectors that threat actors can take advantage of as cloud-based IoT solutions are developed and deployed.
API gateway misconfigurations
Using APIs is a common practice among manufacturers and developers for devices to communicate faster and more efficiently with IoT cloud servers. With APIs, an IoT device can request for specific actions from the cloud server using an API gateway, and vice versa. Functioning as a doorway to the cloud and limiting IoT device traffic, the gateway facilitates specific commands such as turning the device on or off, checking the status of the device, upgrading the firmware, downloading or uploading screenshots or videos, and accessing data.
A misconfigured device or a cloud service may thus be seen as a security liability. Threat actors can use it as an opportunity for malicious activities such as faking a command sequence by changing the logic between the APIs, invoking more vulnerabilities in the process. Other possible activities include user spoofing, man-in-the-middle (MiTM) attacks, and session replays.
Wrong authentication roles, policies, or assigned keys
Developers customize the rules and policies for IoT devices connected to cloud servers for identity and access management (IAM). In the process, every IoT device is expected to handle a big workload equivalent to the corresponding limitations for data access and streams. In addition, some cloud-based IoT devices use the same design, logic, and trust chain as some cloud-based servers and services use for alignment and ease of configuration.
However, IAM misconfigurations can not only block data traffic and access, but also enable hackers to breach the server, do more complex attacks, control the cloud service, or spoof a guest or legitimate device user.
Device, channel, and infrastructure weaknesses
As previously mentioned, APIs are commonly used for easier transmission and retrieval of data from the cloud via API gateways. Most platforms are designed such that the IoT infrastructure will use the same API gateway as the cloud server infrastructure for ease of use to the device owner.
However, misconfigurations and attacks in devices, cloud gateways, and infrastructures may highlight weaknesses in the security of data traffic or path, exposing the device or the cloud server as well. Several open-source websites have begun hosting performance tests on tools for API fuzzing and gateway misconfiguration, and on proofs of concept for hacking established cloud infrastructures that cybercriminals may use in the future.
Conclusion
In their relative infancy, cloud-based IoT solutions are of course not perfect be-all and end-all solutions. Product developers and the programmers tasked to maintain these platforms for their organizations may have to learn the technology from scratch. Configurations and customizations are still required from IT teams and developers to ensure uninterrupted services and daily operations, and to augment the existing multilayered protection systems inside the organizations. This implies more allocations for spending and resources required from enterprises, especially in the beginning.
But cloud-based IoT solutions do offer features that address certain security gaps. These include authentication mechanism enhancements, terminal device identity verification, tighter security connections, edge computing capabilities, app container design, OTA and SDK maintenance, and reduced attack surfaces. Given malicious actors’ predilection for hacking into vulnerable devices or exploiting misconfigured cloud storage settings, organizations would do well to consider cloud-based IoT solutions and their potential for improving security as well as integration, processing, and scalability.
Trend Micro solutions
Enterprises should choose security solutions that can offer a complete package of features that include threat detection, network intrusion prevention, and security management. The Trend Micro™ Deep Security™ for Cloud solution can provide proactive detection and prevention of threats, while Hybrid Cloud Security offers optimal security for hybrid environments that incorporate physical, virtual, and cloud workloads.
Businesses can also consider Trend Micro Deep Security as a Service, which is a dedicated protection system optimized for Amazon Web Services, Microsoft Azure, and VMware. It can help an organization’s IT department by securing servers without the need for any installations. It allows businesses to implement new upgrades without any downtime, and can instantly connect to the cloud and data center resources for proactive security measures.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One