Successful ransomware attacks are debilitating because the malware can spread to other computers on the same network, jumping from one device to the next and rendering them unusable. One compromised home worker can be used as a launching point into an enterprise network. Then, the ransomware actor usually demands a hefty price to decrypt all the files and allow the user or enterprise to resume operations normally.
The article below will provide home workers with an overview of how ransomware attacks work, giving them actionable insight on weak points in home setups. We also list prevention guidelines that will help workers avoid the threat altogether.
How Ransomware Attacks Work
Ransomware actors are looking for big targets. They want access to the corporate network that you may be connected to from home via a VPN, or to the cloud-hosted systems you use for work or sharing files. Their goal is to spread across your organization’s network, first to steal and then encrypt data.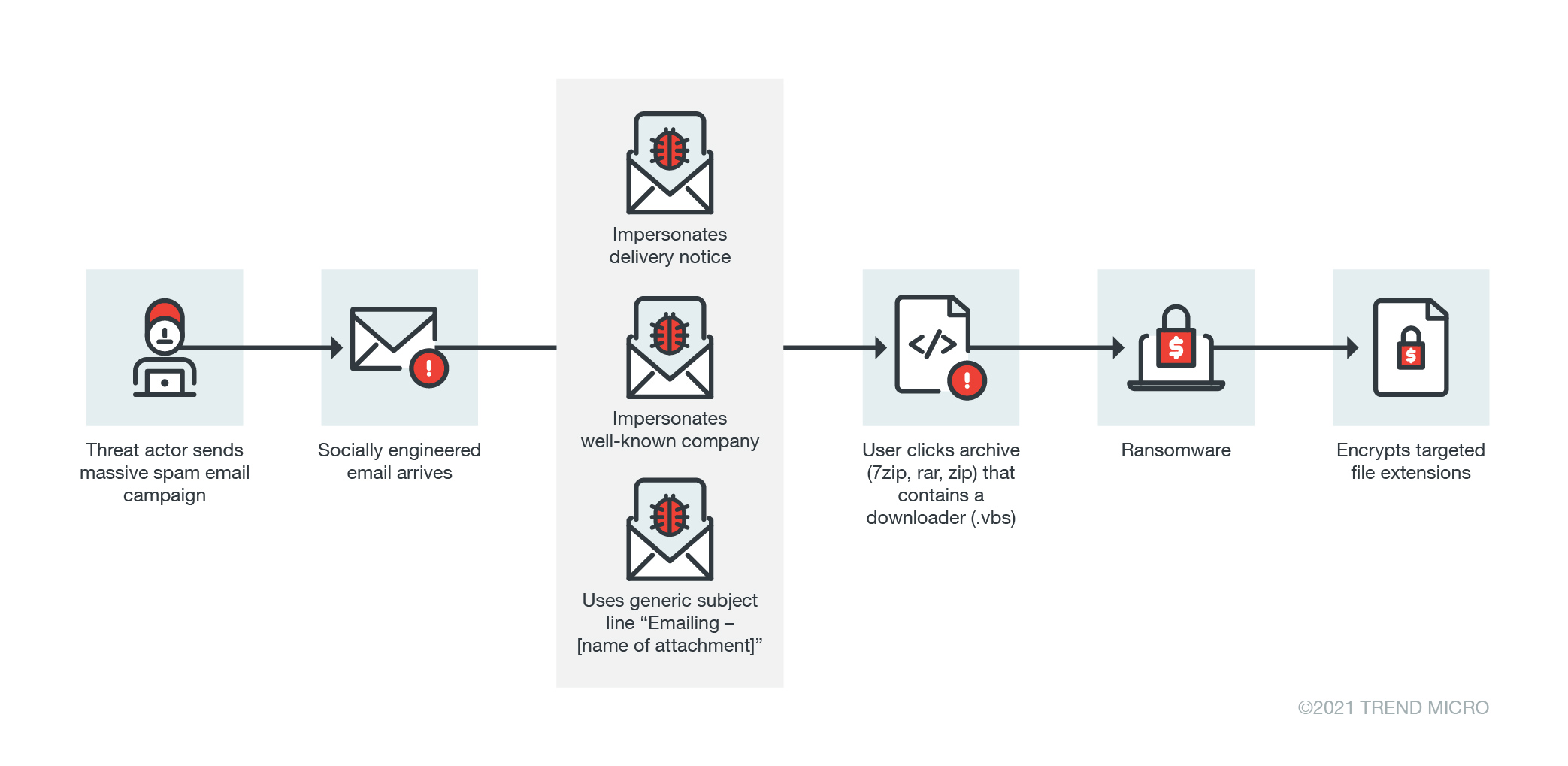
Email phishing is the most common method ransomware distributors use. These malicious actors have become experts at getting unsuspecting users to click on links to websites that host malware, or download dangerous files to start the infection process. Here are some methods attackers use to infect vulnerable home setups:
- Attackers can target work email accounts, remote desktop tools (i.e., Microsoft Remote Desktop or RDP), and cloud-based storage/networks, etc. to deliver the full ransomware payload. This can happen through phishing emails, or they may scan for specific tools and then try to guess the password (known as a brute-force attack). One new Mac ransomware, called EvilQuest, has a keylogger that can capture passwords as you type them in, allowing the ransomware operators to steal data and use it to spread their malware when you log into a corporate portal.
- Attackers can use malware that targets your VPN or remote desktop software. Phishing is again a popular way to do this, or they may hide it in popular software on torrent sites or apps uploaded to app stores.
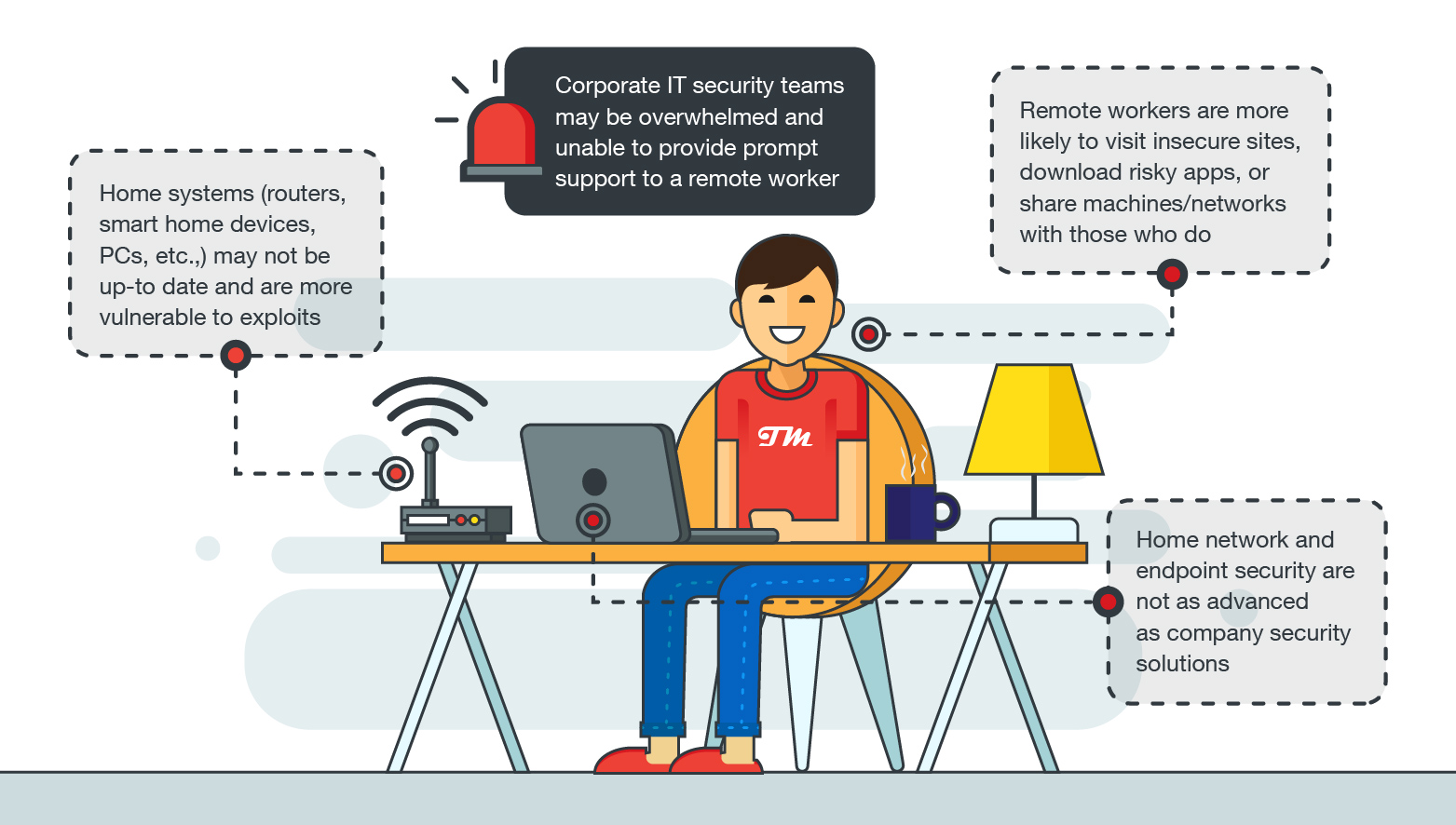
- Attackers can target smart home devices and routers via vulnerabilities, and default or simple passwords. Threat actors target these devices to use employees’ home networks as a stepping-stone into corporate networks.
How Can You Prevent Ransomware?
Remote workers can take some relatively straightforward steps to help mitigate the cascading risks posed by new ransomware families.Avoid giving out personal information
Some malicious actors take publicly available information and use it to gain access to more valuable private information, or use it to send and deploy malware on your device. The information is usually taken from social media sites and public profiles. Be mindful of the kind of information you share online — make sure that you only provide private information when absolutely necessary.
Strengthen your password hygiene
Home workers should employ password best practices for their email and other accounts: use eight or more characters and symbols; avoid repetition, sequences, or patterns; and do not reuse passwords. Since some online corporate tools and portals may also have defaults that attackers can brute-force, it is best to regularly change passwords and implement multi-factor authentication. Using a password manager is a good way to store multiple passwords and login IDs in one secure location.
Windows users should activate Show File Extensions
Show File Extensions is a native Windows functionality that shows users what types of files are being opened. Sometimes malicious actors use filenames that look like two extensions, for example “photo.avi.exe.” Users should use this Windows feature to check what they are opening and avoid any suspicious looking files.
Only open trusted email attachments
Ransomware commonly spreads through spam email with malicious attachments, and many distributors already know the most effective subject titles to grab a user’s attention. They also usually send malicious payloads in common file types: jpegs, Word docs, Excel sheets, and other attachments that most offices use regularly. Users should be wary of email attachments from unfamiliar senders, especially from outside their organization. Some ransomware actors also use uncommon files in their spam mail, and rely on the users to simply click without looking. Avoid opening suspicious file extensions (like .EXE, .VBS or .SCR). Some users can even configure their webmail servers to block those attachments.
Disable the internet connection if the computer exhibits suspicious behavior
Ransomware typically needs to connect with a command and control (C&C) server to complete its encryption routine. Without access to the internet, the ransomware will sit idle on an infected device. If a user manages to catch the ransomware during the early stages of the attack, they can disable internet access and mitigate any damage.
Take advantage of all the tools and security features at your disposal
Many devices and software already have integrated and constantly updated security features. Update your home router firmware, as well as operating systems and software on PCs, mobile devices, and browsers to the latest versions. This includes any virtual tools and VPNs from your company. All devices should also run up-to-date network and endpoint security solutions from a reputable vendor (this should include anti-intrusion, anti-web threat, anti-spam, anti-phishing, and of course, anti-ransomware features). Trend Micro Maximum Security provides ample protection for end-devices: PCs, mobile, and Mac. It can block web threats like ransomware and helps you avoid malicious phishing emails.
The Risks of Ransomware
Remote workers' systems infected by ransomware will likely lose most of their data if they have no back-ups, and will be unable to use their machine until someone from the company’s IT team can remove the malware. In a worst-case scenario, the malware will use their machine as launching points and spread within their company’s network. Recently, ransomware distributors have not only been denying their victims access to files, but are also using double extortion techniques wherein they steal data and threaten to expose the data if victims fail to pay the ransom.
If a ransomware attack is successful, recovery costs are steep. Aside from the loss of valuable data, stalled operations from inaccessible machines greatly affect a company’s bottom line. Not to mention that devices may need to be reinstalled or replaced if they are damaged from the attack. One of the most infamous examples of this is the incident involving shipping giant Maersk. The company had to deal with a reported US$300 million in business interruption and recovery losses.
The risks of ransomware are severe for both remote workers and enterprises. However, the best way to manage and mitigate the threat is to be vigilant about spotting suspicious behavior online and follow the best practices outlined above. As more organizations and employees turn to remote work setups, securing their working environment should be the new normal.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One