National Cyber Security Awareness Month: The Enterprise’s Safety Online Is Everyone’s Business
 View Infographic: Evolving risks, human links
View Infographic: Evolving risks, human links
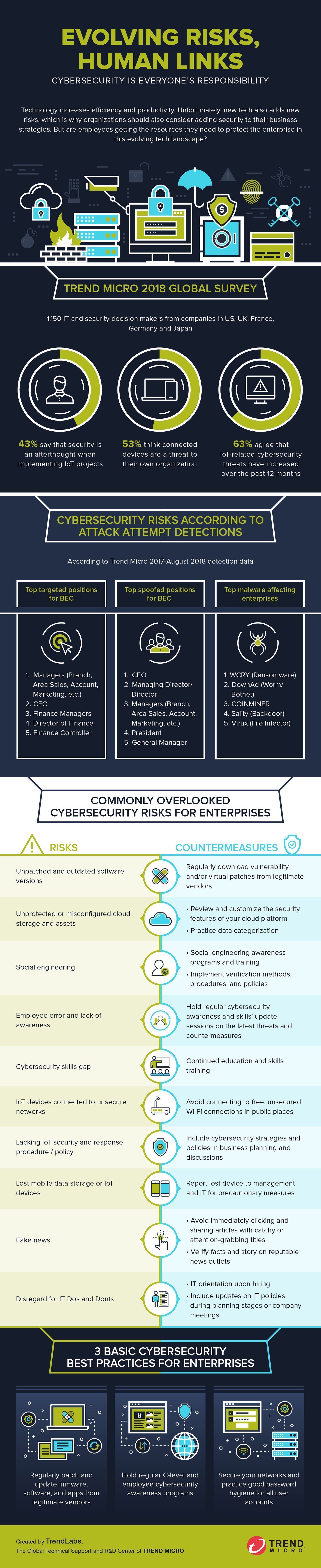
As innovations in technology progress, so do our expectations for efficiency and productivity. Unfortunately, cybercriminals also constantly improve the tools and methods they use to infiltrate organizations and get to valuable enterprise assets. The National Cyber Security Awareness Month emphasizes the importance of security awareness, and an appropriate time to remind enterprises that they should always consider security when planning and implementing any project or process.
Our 2018 Midterm Security Roundup discussed how threat actors combined familiar and new techniques to circumvent online protection measures by taking advantage of platforms available across internet of things (IoT) devices. Unfortunately, many organizations continue to use outdated software, citing how the costs of the downtime and modernizing security policies could result in losses and disruption. However, security is not all about patching and updating systems; everyone can help improve the organization's security. Here are several security measures across different levels that an organization can implement to improve security across different fronts.
Enterprise
Investments drive growth, and disruptions to business transactions and processes could result in economic losses. With the growing dependence on the internet to facilitate transactions and communication, securing industry assets and improving employee awareness can keep cybersecurity threats at bay.
- Continued education with constant verification and learning – Regardless of rank, people in the organization are the weakest links against social engineering tactics, but the latest technologies can provide an effective defense when paired with awareness and education. Artificial Intelligence (AI) and Machine Learning (ML) can be used as tools to detect and withstand Business Email Compromise (BEC) schemes and other social engineering attacks.
- Multiplied threat entry points with diversified innovations – Mobile technology certainly enabled a more connected world, but it also exposed users and enterprises to more threats. Restricting access to highly sensitive information to company-issued devices alone and implementing a properly configured BYOD network are just some ways to thwart attacks on personal devices.
- Use social media as a business multi-tool – Social media turned the tide on traditional practices for businesses and users. Its ubiquity has turned social media platforms into valuable tools to capture the interest and attention of target audiences, but it also exposes users and organizations to malicious campaigns and fake news. Familiarize yourself with the way your organization uses social media to reach customers to determine protective measures that you need to implement.
- Protect the supply chain from threats – Enterprises may be threat actors' main targets, but they can also target other groups connected to their target organization: suppliers, contractors, middlepersons, and service-providers are just as likely to be used for targeted attacks. Discuss security measures with partners, suppliers, and contractors to determine if your perimeter is sufficiently secured.
[Related: Linking the enterprise to social media security]
Employees
It is no longer uncommon for employees to bring personal devices to the office for convenience or to help them with their tasks. This may pose risks as an additional entry point for attackers when IoT devices are insecure or left openly connected to the internet with default manufacturer-provided credentials.
- Secure your automated assistants – IoT devices directly connected to the internet act as efficient tools for active professionals. However, attackers can exploit an unprotected or outdated device in a number of ways. Patch your firmware and software versions regularly from legitimate vendors to remove exploitable vulnerabilities.
- Become the first line of defense – For cybercriminals to successfully launch fraudulent BEC campaigns, they not only spoof an individual in position to commit fraud, but also trick a person into performing financial transactions via social engineering. Defend against these strategies by verifying requests, links, and email addresses with those contacts before acting.
- Add a layer of protection for your online accounts with 2FA – As our everyday routines become more connected to the internet, we have to pay more attention to the way we manage and secure our information online. Set up the 2-Factor Authentication feature of your online accounts to prevent identity theft and unauthorized access.
- Is your new device slowing down? Check for miners – The continued rise in value of cryptocurrencies have made cybercriminals more determined to mine more. Given the resources — and toll on hardware —required to mine them, crypto-miner malware degrades the performance of personal computers, mobiles, and, IoT devices, and can be designed to spread across different networks and systems. Scan your systems if you notice significantly degraded system performance for infection symptoms: process slowdowns, overheating hardware, or when the batteries are used up too fast.
[Related: Best practices: Securing your mobile device]
Network Admins
Network admins act as the organization's frontline interveners. Make sure that the centralized platforms and systems are updated, the network can support the traffic necessary for internal and external functions and services, and storage assets’ data and access to these are limited to the relevant personnel.
- Secure modernized systems that protect us – Modern automated and connected doors, alarms, and locks are now being used to protect enterprise and personal assets. Reconfiguring default settings can secure these mechanized security systems from common network attacks and hacking methods.
- Safeguard networks against walks-ins and drive-bys – A lot has been said and published about the dangers of leaving an open, unsecured, or misconfigured wireless networks. Surprisingly, businesses of all sizes fail to secure these. Establishments can prevent “break ins” by monitoring and reviewing device logs for suspicious activity, as well as raising company awareness on the dangers of using unsecured connections.
- Review, reinforce and update your BYOD policy – Prohibiting the use of personal mobile devices would almost be impossible for any business these days. But a single insecure device or unaware user is all an attacker needs to infiltrate a network. Maintaining a secure BYOD network in the workplace decreases the attack surface by separating the network used by personal devices from the one used for the organization's critical data and processes.
- Practice security by design – Virtualization and cloud technologies provide enterprises with a new level of agility and flexibility in responding to increasing output demands. However, it's not all about subscribing to upgraded hardware and services. Dynamic organizations will adapt by recognizing pain points (such as a lack of security skills) and addressing it with DevOps and Managed Detection and Response (MDR) services.
- Mold a forward-looking enterprise with hybrid cloud integration – The combination of physical servers, virtual machines, and cloud storage assets provide tools and platforms for enterprises with remote personnel to enable a more agile workforce. But threats have also evolved, mixing traditional, evolved, and newly designed tools and methods to target this new infrastructure. Securing these platforms entail an active principle of strategic and shared responsibilities.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One