Modified TeamViewer Tool Drops Trojan Spyware on Victims

On January 20, a security researcher going by FewAtoms spotted a malicious URL in the wild. The URL is an open directory that leads would-be victims to a malicious self-extracting archive. Upon further analysis of the archive, we found that it is trojan spyware (detected by Trend Micro as TROJANSPY.WIN32.TEAMFOSTEALER.THOABAAI) that gathers and steals data disguised as TeamViewer. If successfully downloaded and executed on a victim’s device, the trojan spy creates the folder %User Temp%\PmIgYzA and drops the following files:
- %User Temp%\PmIgYzA\FZhIG.ico
- %User Temp%\PmIgYzA\config.bin
- %User Temp%\PmIgYzA\0.0
- %User Temp%\PmIgYzA\TV.dll (malicious payload)
- %User Startup%\Gateway Layer 1.3957.lnk (shortcut link to dropped TeamViewer.exe)
- %User Temp%\PmIgYzA\TeamViewer.exe
- %User Temp%\PmIgYzA\TeamViewer_Resource_fr.dll
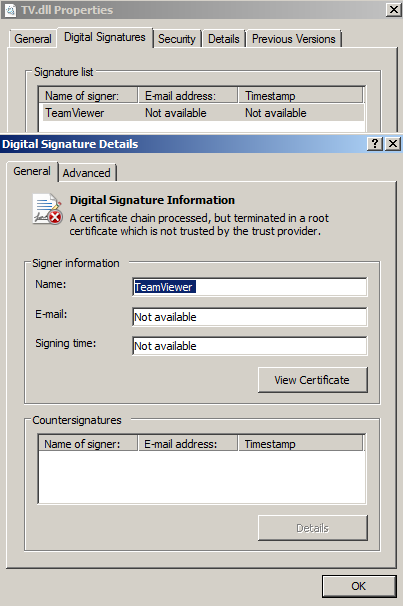
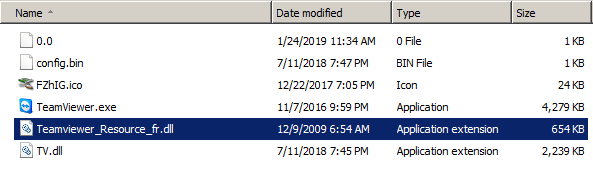
Figure 1. Files dropped by the Trojan spyware
After arriving on the victim’s system, the malware executes the TeamViewer.exe file, which loads the malicious DLL %User Temp%\PmIgYzA\TV.dll. The trojan spyware then gathers user and device data (listed below) and connects to the website hxxp://intersys32[.]com to send and receive this information.
- Operating System
- OS Architecture
- Computer Name
- User Name
- RAM size
- Presence of AV Products
- Administrator Privilege
Digging into the site revealed other malware connected to that particular URL, such as the trojan CoinSteal and another information stealer and malware dropper called Fareit. This could hint at a bigger operational campaign of trojan spyware.
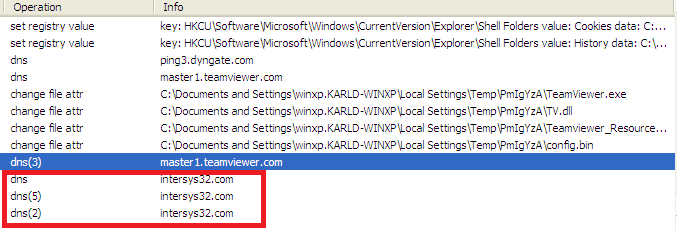
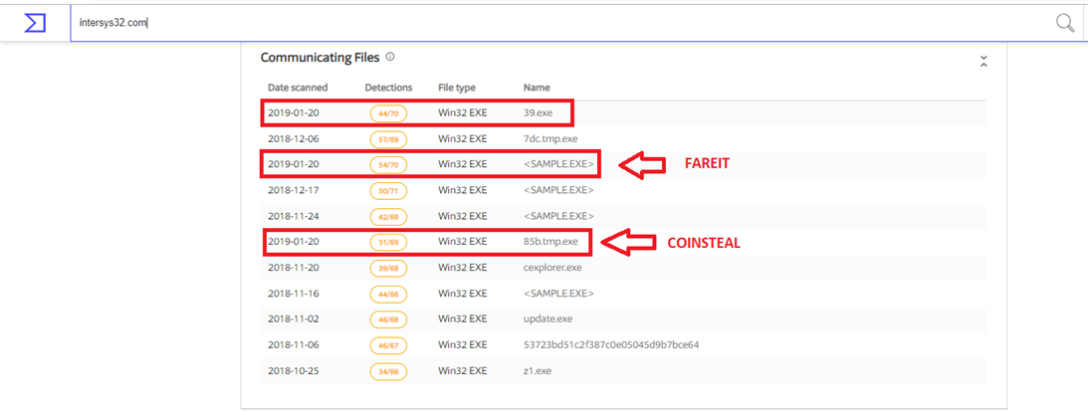
Prevention and Solution
This type of TeamViewer misuse is not new. Malware developers have been known to use the tool to deliver backdoors and keyloggers in a similar way as far back as 2016. We saw that the tool was trojanized by adding a malicious DLL to a legitimate version to be loaded onto a victim’s device. In 2017, a published report also showed how TeamViewer was being used to control an infected machine, not merely as a malware loader.
Given the possibilities of abuse and the recent schemes to deliver malware disguised as legitimate software, users should secure their endpoints with multilayered protection.
The following Trend Micro products can protect users from this threat:
Trend Micro™ Security, Smart Protection Suites
The malware described in this article is not the official TeamViewer software. It is a modified, pirated version of the software. It is strongly recommended to download the software only from the official TeamViewer website. Obtaining software from a reputable source is the best way to protect against threats like the trojan spyware described here. TeamViewer recommends to always use the latest version of its software in order to benefit from the latest security precautions.
Indicators of Compromise
SHA
b2ab87d5408a19b0d65d49b74c0f3d879ac55c3e57117e4117ff500394e2ad17
Malicious URLs:
hxxp://rosalos[.ug]/xxx/
hxxp://intersys32[.]com
With additional insights from Raphael Centeno and Patrick Roderno
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One