Malicious Spam Campaign Targets South Korean Users
 Trend Micro researchers detected a malicious spam campaign primarily targeting South Korean users. It utilizes attachments compressed through ALZip, an archive and compression tool widely used in South Korea. When decompressed, the attachment is revealed to contain two executable (.EXE) files that carry the information stealer TrojanSpy.Win32.INFOSTEALER.THBOCBO, and Ransom.Win32.NEMTY.THBOCBO, a ransomware variant.
Trend Micro researchers detected a malicious spam campaign primarily targeting South Korean users. It utilizes attachments compressed through ALZip, an archive and compression tool widely used in South Korea. When decompressed, the attachment is revealed to contain two executable (.EXE) files that carry the information stealer TrojanSpy.Win32.INFOSTEALER.THBOCBO, and Ransom.Win32.NEMTY.THBOCBO, a ransomware variant.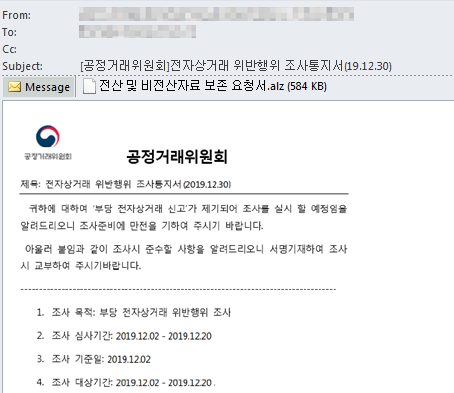
Figure 1. A sample of an email used in the spam campaign
Attached malware: ransomware and information stealer
Ransom.Win32.NEMTY.THBOCBO is a variant from the Nemty ransomware family. Like many other ransomware types, it encrypts files in fixed, removable, and network drives.TrojanSpy.Win32.INFOSTEALER.THBOCBO steals the following data, which will then be sent to its command-and-control (C&C) server:
- Computer name
- CPU count
- Date
- Display language
- Display resolution
- Globally Unique Identifier (GUID)
- Installed programs
- Internet protocol (IP)
- Internet service provider (ISP)
- Keyboard language
- Location
- Machine ID
- Operating system
- Outlook credentials
- Passwords
- Path
- Processor
- Random access memory (RAM)
- Running processes
- Time zone
- User name
- Version
- Video card
- Work directory
The ransom note
The ransom note informs victims that their files have been encrypted, and that victims can get a decryption tool after paying the ransom. The note then includes instructions on how to initiate the decryption process, giving the victims a three-month deadline. It should be noted that there isn’t any indication that the cybercriminals will indeed decrypt the files.
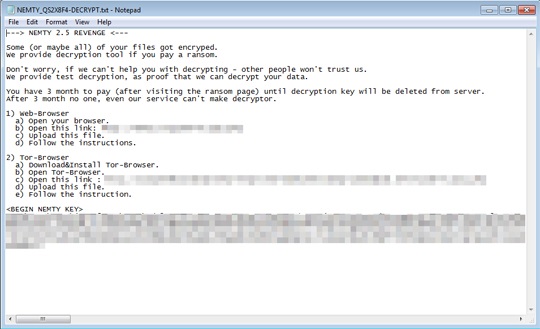
Figure 2. Ransom note used in the spam campaign
Security against malicious spam campaigns
Many cybercriminals are adept at concealing intent through socially-engineered facades. These include targeting users in a specific country and sending fake emails that supposedly came from reputable local institutions, a tactic that has been used in recent spam campaigns like the Emotet spam campaign targeting Japanese users. Threat actors take advantage of the fact that even cautious users tend to let their guard down upon seeing that the emails come from establishments (especially local ones) that they recognize and trust.
Being misled by these emails can lead to the compromise of the systems of not just a single user, but possibly the whole enterprise as well. To avoid such threats, users are advised to do the following:
- Avoid downloading attachments and clicking links in emails from unfamiliar sources.
- Confirm if the emails indeed came from a particular institution by verifying the contact details from their official website.
- Learn how to identify and avoid email threats.
To strengthen a system’s defense against ransomware, install the latest patches to address vulnerabilities that can be exploited. Users can also install Trend Micro Smart Protection Suites, especially those for email and collaboration:
- Trend Micro™ Deep Discovery Email Inspector™
- Trend Micro™ Email Security
- Trend Micro™ InterScan Messaging Security
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- The State of Criminal AI: Market Consolidation and Operational Reality
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One