Agent Smith Malware Infecting Android Apps, Devices for Adware
 Agent Smith (detected by Trend Micro as AndroidOS_InfectionAds.HRXA), a new kind of mobile malware, has been found infecting Android devices by exploiting the vulnerabilities found within the operating system (OS) to replace installed apps with malicious versions without the user knowing. According to Check Point researchers, the malware displays fraudulent ads on the victims’ phones, though it can be used for more malicious purposes such as for stealing banking information, or to monitor targeted users. The highest number of infected devices have been observed in India, Saudi Arabia, Pakistan, Bangladesh, United Kingdom, United States, and Australia.
Agent Smith (detected by Trend Micro as AndroidOS_InfectionAds.HRXA), a new kind of mobile malware, has been found infecting Android devices by exploiting the vulnerabilities found within the operating system (OS) to replace installed apps with malicious versions without the user knowing. According to Check Point researchers, the malware displays fraudulent ads on the victims’ phones, though it can be used for more malicious purposes such as for stealing banking information, or to monitor targeted users. The highest number of infected devices have been observed in India, Saudi Arabia, Pakistan, Bangladesh, United Kingdom, United States, and Australia.
The researchers found an increase in the abuse of the Janus vulnerability (designated as CVE-2017-13156) before April 2019. They also observed popular tools, gaming, beauty filter, and adult content apps on Play Store dropping the Agent Smith malware, which executes subsequent malicious app updates disguised as official Google patches. The malicious Android Package (APK) version extracts the installed app list, references it to its prey list sent from the command and control server (C&C), and extracts the base APK to replace with the malicious advertisement modules and APK, which it installs as fake updates.
[Related: Android Security: Click fraud apps drove 100% malware increase in Google Play for 2018]
The attackers differentiated this malware’s routine from previous mobile malware campaigns by finding more loopholes and considering more sophisticated infection chains given Android's new security measures. According to the researchers, the three-stage infection includes Janus, Bundle, and Man-in-the-Disk, building a botnet of devices and making this “the first campaign seen that ingrates and weaponized all these loopholes.” With this groundwork planned and laid out, the attackers may have been preparing for an even bigger attack campaign as it tried to increase Play Store penetration rate. The researchers have already notified Google, which has confirmed the removal of the said malicious apps.
[Read: Android malware campaigns SimBad adware and Operation Sheep reportedly installed 250 million times]
In the first quarter of 2019, Trend Micro detected the malicious apps internally and separately identified the malware as AndroidOS_HiddenAds.HRXA and AndroidOS_Janus.ISO. At the time, these sporadic detections did not show related characteristics until infection reports around the world began to increase and the sandbox started unpacking to drop Android Dalvik Executable (DEX) files with AndroidOS_Janus.ISO flagged. Further analysis revealed that almost 900 apps in popular third-party Android stores such as 9Apps had embedded malicious modules, and a small number of malicious apps had a total of more than 11,000 downloads. These barely functioning apps typically have the APK self-sign signatures on their certificate content.
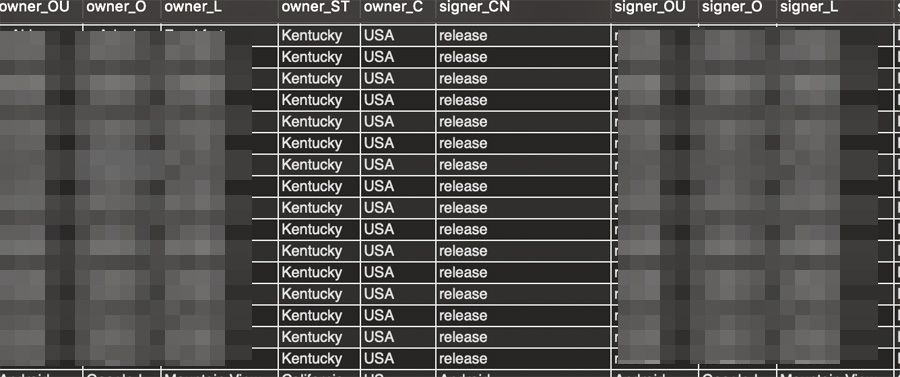
Figure 1. Signer and owner listed in the certificate content of Agent Smith-infected apps are exactly the same.
All of the apps' malicious versions occupied more OS space and contained android.support,multidex.MultiDexApplication, allowing the attacker to use the automatic tool to repackage its codes to malicious ones. Trend Micro has notified Google of this; Google already removed the remaining apps at the time of publishing.
Users are advised to check their devices and uninstall suspected apps or recently installed apps if they suspect infection. App developers, system developers, and mobile solutions providers are also reminded to monitor their respective products, and to patch and distribute updates in time to make sure vulnerabilities are fixed accordingly. Users and enterprises can consider using a multilayered mobile security solution to prevent adware and other potentially unwanted applications (PUAs) installation attempts in their devices.
With additional insights by Lorin Wu.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One