-
Overview
-
BEC
-
Credential Phishing
-
Malware
-
Phishing
-
Cloud App Security
Cloud computing has been experiencing rapid growth and is expected to expand further in the near future — some estimates predict that the global cloud computing market would grow to more than double its 2018 value in a few years. It’s no surprise that cloud-based business emails have seen a similar shift, especially as email accounts now serve as doors to a host of other file-hosting and collaboration tools.
However, as adoption rises, the threats to cloud platforms and services also grow in scale and complexity, and email services are prime targets. Their increasing use in enterprise environments has led to cybercriminals targeting users in a variety of ways: from traditional social engineering techniques to the use of more sophisticated malware types, and even to the potential abuse of emerging technologies in the field of artificial intelligence (AI).
In 2019, staple email-based threats such as business email compromise (BEC) and credential phishing remained prevalent, yet at the same time, the year saw threat actors employing new techniques and strategies in a bid to make their campaigns more effective.
[ Assess your security posture, including email security ]
An overview of the email threat landscape
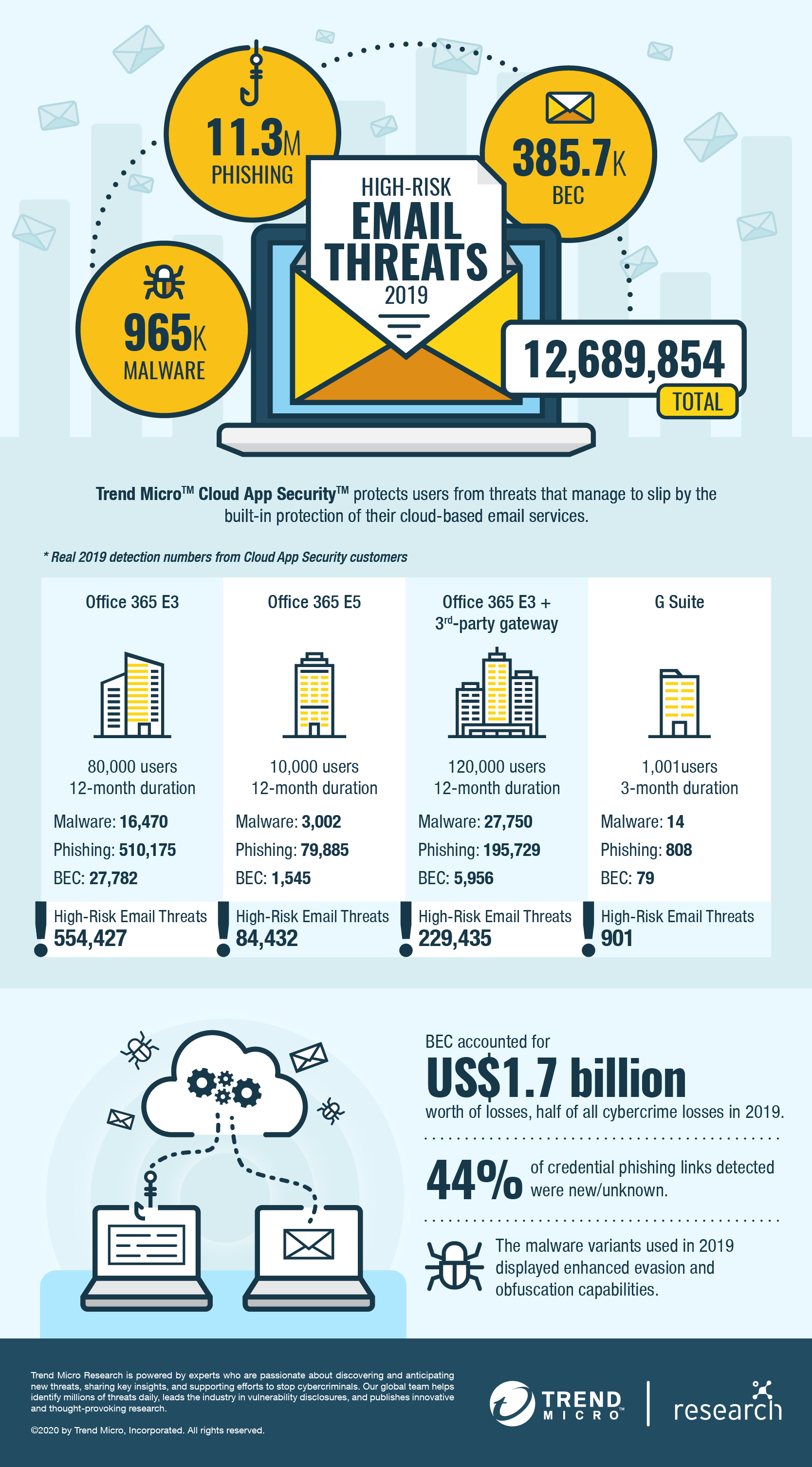
The Trend MicroTM Smart Protection NetworkTM infrastructure blocked over 47 billion email threats in 2019, an increase of 14% from the previous year. The Trend Micro Cloud App SecurityTM solution, an API-based solution that provides protection for various cloud-based applications and services, including Microsoft® Office 365TM ExchangeTM Online, OneDrive® for Business, SharePoint® Online, Gmail, and Google Drive, was able to detect and block 12.7 million high-risk email threats.
While the overall detections for malware dipped slightly in 2019, phishing and BEC saw significant leaps.
Email threats are not going away and are following the move to the cloud. Many organizations use cloud-based systems that have their own security implementation. Some rely on Microsoft Office 365 E3 and E5 threat protection services or Google’s built-in security, and others use third-party email gateways as well. Detections from Trend Micro Cloud App Security reveal how a massive number of threats still manage to slip past these filters and why a multilayered approach is necessary.
For one organization with approximately 80,000 Office 365 users, Trend Micro Cloud App Security detected over 550,000 high-risk email threats after they passed through Microsoft’s native email security filter. That means an average of nearly seven high-risk malicious emails per individual. Majority of the threats were phishing URLs, which is not unexpected given the size of the company. More worrying, however, is that over 27,000 BEC attempts were also detected. Given the nature of BEC scams, even one successful attack could result in significant financial losses for the organization.
It is but expected that larger organizations get the lion’s share of email threats, but this does not exempt smaller businesses from being beset by email-based attacks. For one organization with approximately 1,000 Gmail users, Trend Micro Cloud App Security detected over 900 high-risk email threats in a three-month period — nearly a 1:1 ratio of users to threats. Although they face fewer threats based on numbers alone, many small and medium-sized businesses (SMBs) are ill-equipped to handle threats due to a lack of skilled personnel or resources — oftentimes both.
BEC remains a big business for cybercriminals
BEC is big business: According to the FBI, BEC scams amounted to US$1.7 billion in exposed losses in 2019 — half of the year’s total losses due to cybercrime. It remains a major thorn in the side of organizations, as the number of BEC attempts detected by Trend Micro Cloud App Security rose significantly from just over 100,000 in 2018 to nearly 400,000 in 2019 — a 271% increase. Furthermore, the percentage of BEC attempts out of the total number of email threats detected tripled from the previous year.
An interesting shift can be seen in the significantly higher percentage of BEC detections that were caught by authorship analysis via AI and machine learning — from 7% in 2018 to 21% in 2019. Given that this stage follows behavior and intention analysis, it appears BEC operators are getting smarter and exploring beyond the usual social engineering tricks.
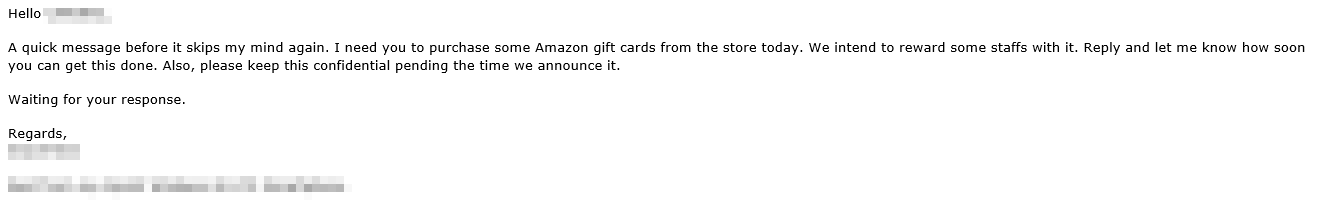
BEC scams have been on the rise in the past few years. Cybercriminals tend to rely on what’s worked before, and this was still true for 2019. Fake invoices requiring wire transfer payments sent via email remained a prominent BEC technique, while scams involving gift cards, which were already gaining steam in previous years, became one of the most popular methods for conducting BEC scams in the fourth quarter of 2019. Gift card scams eliminate the need for a middleman or for accounts that could potentially be shut down by banks and law enforcement, thus guaranteeing a virtually “hands-free” transaction for BEC scammers. The FBI also noted that some incidents were accompanied by wire transfer requests.
A gift card scam detected by Trend Micro Cloud App Security. Scams such as these are more informal, and thus more unlikely to be perceived as a threat.
Aside from the usual methods, BEC scammers have also started evolving their techniques. For example, one notable change is how the use of CEO fraud, in which cybercriminals impersonate an organization’s chief executive officer, is on the decline. In a 2019 report, the U.S. Treasury Department’s Financial Crimes Enforcement Network said CEO fraud accounted for only 12% of sampled incidents in 2018, down from 33% in 2017 — indicating that BEC threat actors are starting to look for newer, perhaps more accessible, targets.
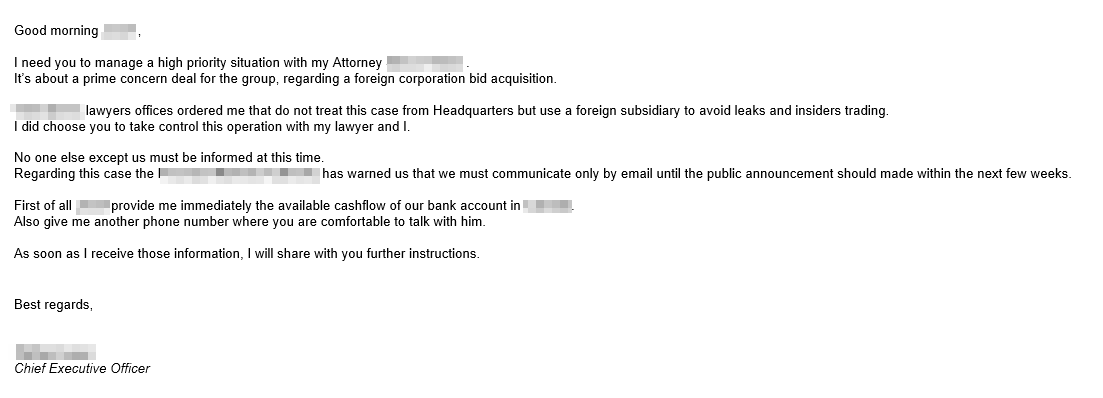
Cybercriminals are also expanding their social engineering tricks. Traditionally, BEC threat actors relied on fake invoices requiring wire transfer payments sent via email. Last year, the London Blue group started using email messages that notified the target organization of acquisition terms of an overseas vendor — with the caveat that 30% of the purchase price had to be wired. Another incident in December saw cybercriminals compromising the account of one of the employees of a Chinese venture capital firm. They then spoofed the domain of an Israeli startup company the victim organization had dealings with and eventually walked away with US$1 million originally meant for seed funding.
A sample of a BEC email using the acquisition scam detected by Trend Micro Cloud App Security. It seems to be a preliminary email, as no amount is mentioned yet.
Fraudsters have also taken aim at nonprofit organizations. Some prominent events from 2019 include the theft of US$2.3 million from the Manor Independent School District in Texas and an attack on an Ohio church that led to US$1.75 million in losses. Local governments were not spared either, as incidents in 2019 such as those in North Carolina and Georgia led to millions of dollars in losses in the U.S.
Credential phishing poses more unknown risks to established targets
In our 2017 and 2018 Trend Micro Cloud App Security reports, we noted that Microsoft Office 365 users were frequent targets of phishing — and 2019 was no exception. Data from the Trend Micro Smart Protection Network infrastructure shows that the number of unique Office 365-related phishing links blocked in 2019 jumped to more than double 2018’s total.
For one organization with 10,000 Office 365 users, phishing attacks were a major cause for concern. Cloud App Security managed to detect and block over 410,000 phishing attempts targeting the company, out of which over 100,000 were spam emails and over 300,000 were credential-phishing emails. Another organization that had 550 employees using Office 365 had over 2,600 phishing attempts detected and blocked. These emails were the ones that made it past the built-in filters of the email service, and the number of phishing attempts was even higher.
USERS
USERS
While Office 365 end users have always been frequent targets of phishing attacks, particularly credential phishing, threat actors are also now going after Office 365 administrator accounts. An attacker gaining control of an Office 365 user’s credentials could mean gaining complete access to an individual account. Taking over an administrator account, on the other hand, could result in gaining control over the organization’s Office 365 domain and all of its connected accounts.
Although there was an increase in the overall detections for credential-phishing attempts — a 35% increase from 2018 — the number of credential-phishing attempts involving unknown phishing links is quite striking. For 2018, this number stood at just over 9% of the total credential phishing detections. In 2019, unknown phishing links accounted for over 44% of credential phishing detections.
Perhaps the simplest possible reason for this increase is that threat actors have been busy updating their phishing websites to reflect a new set of links to avoid detection by antivirus software. It’s also possible that a number of new groups have begun launching campaigns with their own batch of URLs, hence the massive increase in the detection of unknown URLs.
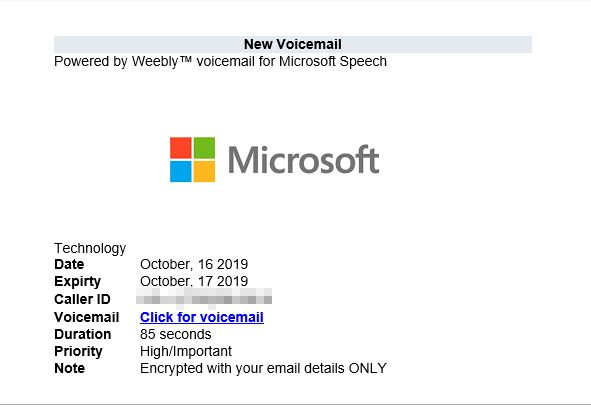
The techniques used in credential phishing have also become more devious — voice-themed and cloud-sharing abuse were notable ruses in 2019. For example, a phishing campaign in July used fake OneNote Online pages hosted on a SharePoint subdomain that linked to a bogus Microsoft login page.
An example of a fake voicemail notification caught by Trend Micro Cloud App Security
We detailed other credential phishing techniques in the first half of 2019 in our report, “The Rising Tide of Credential Phishing.“
Malware attacks use new delivery and evasion methods
The number of malware detections dipped in 2019 — to roughly 960,000 from over a million in 2018. But malware variants seen throughout the year weren’t lacking in capabilities.
On the surface, there seems nothing particularly special about a 2019 campaign launched by the Cloud Atlas/Inception group; like many other phishing campaigns, it took aim at high-value targets via phishing emails. What made these attempts notable was the malicious attachment it used: The Microsoft Office document contained malicious remote templates loaded from remote servers — an obfuscation technique meant to allow the document to evade both static and forensic analysis.
Furthermore, the templates executed a malicious HTML application, which then executed a malicious backdoor. Both the HTML application and the backdoor were polymorphic — they constantly modified their attributes to avoid detection. The final payload included a component designed to steal documents and send them to a command-and-control (C&C) server, and a password grabber from the compromised machine.
The use of ISO files to deliver malware became more common. In August, we found the LokiBot malware being delivered via spam emails containing malicious ISO attachments and using steganography to hide its tracks. In the same month, we reported on the cybercriminal group TA505, which also used ISO attachments to drop the remote access trojan (RAT) FlawedAmmyy.
Last year saw the proliferation of RATs in spam and phishing campaigns. In July, Trend Micro researchers found a phishing email delivering the Remcos RAT, a multifunctional tool with remote execution and data theft capabilities. It also used a number of obfuscation and anti-debugging techniques to evade detection. That same month, another campaign with multistage payloads — Imminent Monitor RAT and Proyecto RAT — targeted financial and government organizations in South America. The group behind the attack used a service that allowed the creation of throwaway email addresses for its C&C server. Another malicious spam campaign caught by Trend Micro honeypots involved a pair of AutoIT-compiled payloads — the trojan spy Negasteal (aka Agent Tesla) and the Ave Maria (aka Warzone) RAT.
Phishing attacks diversify in tools, techniques, and targets
Email-based attacks are becoming more multifaceted with each passing year. As awareness of social engineering increases, cybercriminals are adapting accordingly, implementing new methods to make their phishing attacks more effective — and subsequently more difficult to detect.
Instead of using a single URL, IP address, or domain for sending out emails, threat actors are now mixing it up by using both public and hosted cloud infrastructures to make their attacks look more legitimate. Another technique is the use of compromised email accounts to target unsuspecting employees in an organization, for example, by replying to ongoing email threads. This trend grew further in 2019, with reports that hijacked Office 365 accounts were used to send 1.5 million email threats in a single month alone.
In addition, the use of HTTPS in phishing websites increased to 58% in the first quarter of 2019, according to the Anti-Phishing Working Group. This uptick indicates that cybercriminals are pulling out all the stops to hide the fact that their websites are for malicious purposes from their intended victims.
The past year also saw phishing techniques with increasing complexity, perhaps best exemplified by Heatstroke, a phishing campaign that uses a multistage phishing attack involving multiple websites designed to fool the victim. The phishing kit itself uses an obfuscation method that shows text from folk stories when someone tries to view its source code on a browser — both to hide its tracks and to mock security researchers trying to analyze its code.
Heatstroke’s phishing page source code when viewed on a browser
An older scheme also saw a resurgence later in the year: the use of phishing lures leading to login pages that were designed to send a user’s digital token to an attacker, allowing them access to the victim’s O365 account even after credentials are updated.
The targets of phishing attacks also grew in scope. One campaign discovered by Trend Micro researchers involved the popular social media app Instagram. Popular Instagram personalities with followers ranging from 15,000 to 70,000 had their accounts stolen by cybercriminals, who used phishing emails that were made to look like a verification request from Instagram and that led the victims to a malicious website designed to steal their credentials.
These accounts were possibly targeted for financial extortion, with threat actors banking on the accounts' being valuable enough to the owners that they would be willing to pay a certain amount to retrieve access.
Protect your email and collaboration tools in the cloud with Trend Micro Cloud App Security
Email-based threats remained rampant in 2019. BEC has proved a lucrative venture for cybercriminals, a factor which, in addition to the variety in potential scams, is behind the significant increase in detected attempts. Moreover, the number of unknown links used for credential phishing shows that new campaigns are constantly being launched — either by new threat actors or by experienced cybercriminals refreshing old schemes. On the other hand, while malware detections were down slightly, 2019 proved to be a year in which more sophisticated techniques were employed to deliver malware.
A major takeaway that can be gleaned from the email threat landscape is that a single security gateway or service is no longer enough to protect organizations from email-based threats — especially with the move to cloud-based enterprise tools. Businesses, no matter the size, are at risk from a plethora of dangers that these kinds of threats pose.
Organizations should consider a comprehensive multilayered security solution such as Trend Micro Cloud App Security. It supplements the preexisting security features in email and collaboration platforms like Office 365 and G Suite by using machine learning to analyze and detect any suspicious content in the message body and attachments of an email.
Trend Micro Cloud App Security uses technologies such as sandbox malware analysis, document exploit detection, and file, email, and web reputation technologies to detect malware hidden in Office 365 or PDF documents. It provides data loss prevention (DLP) and advanced malware protection for Box, Dropbox, Google Drive, SharePoint Online, and OneDrive for Business, while also enabling consistent DLP policies across multiple cloud-based applications. It also offers seamless integration with an organization’s existing cloud setup, preserving full user and administrator functionality, providing direct cloud-to-cloud integration through vendor APIs, and minimizing the need for additional resources by assessing threat risks before sandbox malware analysis.
Trend Micro Cloud App Security stands on the cutting edge of email and software-as-a-service (SaaS) security, offering machine learning-powered features that combat two of the primary email-based threats: BEC and credential phishing. Writing Style DNA can help determine if an email is legitimate by using machine learning to check a user’s writing style based on past emails and then comparing suspicious emails against it. Computer vision, on the other hand, combines image analysis and machine learning to check branded elements, login forms, and other site content. It then pools this information with site reputation elements and optical character recognition (OCR) to check for fake and malicious sites — while reducing instances of false positives.
Even with the best security technology in place, the human element remains an important part of creating a rock-solid security implementation. Businesses need to ensure that their employees are educated on email threats and know how to recognize and react to these kinds of attacks. This includes examining messages for any grammatical errors and spelling mistakes, which are red flags that are often present in malicious emails. Users should also be vigilant when responding to or acting on an email, especially if it involves financial matters.
Organizations can avail of a free assessment test for email and endpoint security. It uses Trend Micro Cloud App Security to scan mailboxes for any potential threats.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Azure Control Plane Threat Detection With TrendAI Vision One™
- Forecasting Future Outbreaks: A Behavioral and Predictive Approach to Proactive Cyber Risk Management
- Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report
- The Industrialization of Botnets: Automation and Scale as a New Threat Infrastructure
- From Holiday Snap to Custom Scam in 30 Minutes: How AI Turns Public Photos Into Targeted Attacks

 Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report
Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report Azure Control Plane Threat Detection With TrendAI Vision One™
Azure Control Plane Threat Detection With TrendAI Vision One™ The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One