Next-Gen Payment Processing Tech: EMV Credit Cards
 In 1994, Europay, MasterCard, and VISA created the EMV consortium to develop new technologies to counteract payment card fraud. EMV, is the global standard for Integrated Circuit Cards (ICC), which is an open-standard set of specifications for smart card payments and acceptance devices. These specifications were designed to ensure interoperability between chip-based payment cards and terminals.
In 1994, Europay, MasterCard, and VISA created the EMV consortium to develop new technologies to counteract payment card fraud. EMV, is the global standard for Integrated Circuit Cards (ICC), which is an open-standard set of specifications for smart card payments and acceptance devices. These specifications were designed to ensure interoperability between chip-based payment cards and terminals.
EMV, or Chip-and-PIN cards, feature a chip that stores a cryptogram that allows banks to determine if the card or the transaction has been modified. The chip also stores a counter that gets incremented with each transaction to make sure that there are no duplicate or skipped counter values that indicate potential fraudulent activities.
After the Target data breach in December 2013, EMV credit cards were put in the security spotlight as many see it as the solution to prevent future credit card data breaches. The reality is that while EMV credit cards were developed to prevent counterfeiting, it cannot prevent PoS RAM Scraper attacks.
In the recent Home Depot data breach, credit cards used at Canadian Home Depot locations, which accepts EMV cards, were compromised using Point of Sale (PoS) RAM Scraper malware. While Home Depot’s Canadian stores have PoS EMV Chip-and-PIN card terminals that were considered to be less vulnerable, the incident proved that it.
How does it work?
EMV cards store encrypted Tracks 1 and 2 data on the chip. Meaning, it stores payment information securely rather than on a magnetic stripe, making it virtually impossible to copy or create fraudulent EMV cards. Similar to debit cards, cardholders need to input a PIN code for authentication before the transaction takes place.
The EMV chip-on-card makes it extremely difficult for criminals to manufacture counterfeit credit cards using stolen data, thus reducing counterfeit and lost or stolen card fraud. However, it still does have a weakness: if the EMV credit card’s Tracks 1 and 2 data are sent to the PoS system for processing, it will become susceptible to RAM scraper attacks because the decrypted data resides in RAM.
Where has EMV been adopted?
EMV cards are widely used in Canada, Mexico, South America, Europe, and Asia. In October 2015, the US is scheduled to switch to EMV cards, but unlike other regions that implemented Chip-and-PIN cards, the US opted to switch to Card-and-Signature cards, which may fall short on fraud control.
The primary reason why the US hasn’t opted for the Chip-and-Pin route is because banks don’t want to burden their customers by having them remember a four-digit code at the checkout. When the switch is implemented in October, merchants who don’t have the upgraded system will be responsible for the charges that occur if a compromised EMV card is used in a fraudulent transaction.
UK credit card fraud statistics show that after EMV cards were introduced in the country, losses related to card-not-present fraud dramatically increased in volume. This shows that criminals are using stolen credit card data for online purchases as opposed to manufacturing and using counterfeit cards.
What are its benefits?
While EMV technology does have its share of security challenges, it plays a crucial role in bolstering payment card security. PIN-based authentication can help address fraud involving cards that are lost and stolen, as EMV replaces the traditional magnetic stripe with embedded microprocessors that store cardholder data. The system also requires users to enter PINs (ideally one that ought to be known only to the cardholder) instead of signing their names to complete payments at PoS terminals. This payment technology offers better protection against counterfeit fraud—which could lead to data breaches.
Are there security risks with EMV?
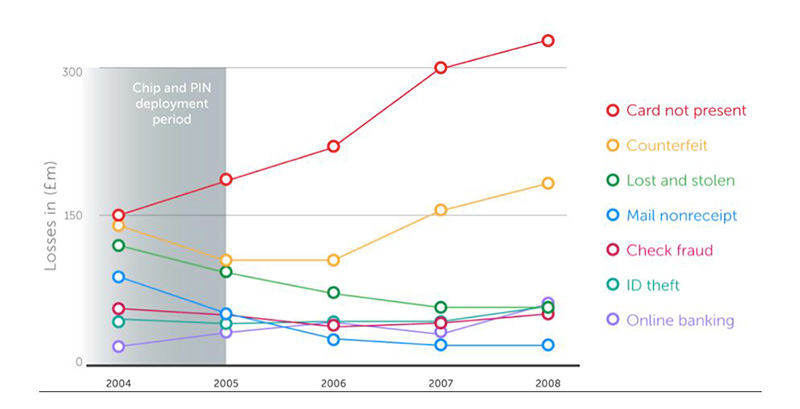 Fraud statistics on UK -issued credit cards. Source: "Chip and PIN is Broken"
Fraud statistics on UK -issued credit cards. Source: "Chip and PIN is Broken"
Researchers from the University of Cambridge showed that cybercriminals could cheaply construct special devices that intercept and modify communications between EMV credit cards and PoS terminals, fooling the latter into accepting fake successful PIN verifications. Even though this is a proof-of concept attack, it shows that there are flaws in the EMV protocol.
Another attack recently observed is the EMV ‘replay’ attack. The first known victim was a Canadian bank that had incorrectly implemented their EMV transaction handling code and wasn’t checking either the cryptogram or the counter values. Cybercriminals spoofed EMV transaction requests to this bank and got the fraudulent charges approved.
In a similar attack, cybercriminals in Brazil encoded non-EMV card transactions as EMV transactions and successfully passed them through Visa and MasterCards’ networks. In both these cases, the criminals were not breaking the EMV protocol, but were taking advantage of poor implementation and the trust model associated with EMV transactions. As EMV card usage becomes more widespread, cybercriminals are expected to discover more exploitable flaws.
[More: Next-Gen Payment Processing Technologies: What They Are, and How They Work]
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- Forecasting Future Outbreaks: A Behavioral and Predictive Approach to Proactive Cyber Risk Management
- Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report
- The Industrialization of Botnets: Automation and Scale as a New Threat Infrastructure
- From Holiday Snap to Custom Scam in 30 Minutes: How AI Turns Public Photos Into Targeted Attacks
- From LinkedIn to Tailored Attack in 30 Minutes: How AI Accelerates Target Profiling for Cybercrime

 Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report
Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One