Next-Gen Payment Processing Architectures
 A rapidly increasing number of people make payments through mobile devices such as smartphones and tablets. They purchase apps, music, consumer goods, and a wide array of other products and services. Using traditional credit cards or even contactless cards, these payments are often at risk of attack.
A rapidly increasing number of people make payments through mobile devices such as smartphones and tablets. They purchase apps, music, consumer goods, and a wide array of other products and services. Using traditional credit cards or even contactless cards, these payments are often at risk of attack.
For example, the reality is that credit cards cannot prevent Point-of-Sale (PoS) terminal attacks. The chip-on-card makes it extremely difficult for criminals to manufacture counterfeit credit cards using stolen data thus reducing counterfeit and lost or stolen card fraud. But that doesn’t protect these cards from other types of attacks, particularly those that look to steal data during a transaction.
One common contactless attack is the relay attack. The attack chain consists of:
- A relay reader device called a mole, which is placed in close proximity to the card being attacked.
- A card emulator device called a proxy, which is used to communicate with the PoS terminal.
- A fast communication channel between the relay and the proxy.
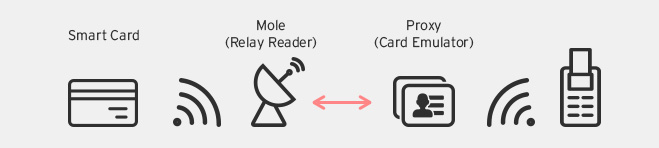 Relay attack against RFID payment cards
Relay attack against RFID payment cards
The mole emits radio frequency energy and powers the RFID chip on the card being attacked. The proxy interacts with the PoS terminal and forwards commands to the card via the mole. The mole captures the card’s responses and sends them back to the proxy, which then forwards it to the PoS terminal. Encryption does not protect against this type of attack because this is capturing an existing data transfer, with the mole and the proxy relaying data.
There are currently three primarily architectures that promote a next-generation solution to secure mobile payment. These are encryption plus tokenization, cloud-based PoS systems, and secure element systems.
Encryption Plus Tokenization
This payment architecture encrypts and tokenizes the credit card data, thus making credit card data theft virtually impossible for the cybercriminals.
The processing workflow is as follows:
- The customer swipes their credit card at the merchant’s PoS terminal to complete their purchase.
- The PoS terminal reads and encrypts the credit card data and transmits it for processing.
- The processor forwards the credit card data to the banks for authorization.
- The processor uses a tokenization algorithm to replace the actual credit card data with a token.
- The generated token and bank authorization status is send back to the merchant’s PoS system.
- The merchant’s PoS system stores the token instead of the actual credit card data in all places.
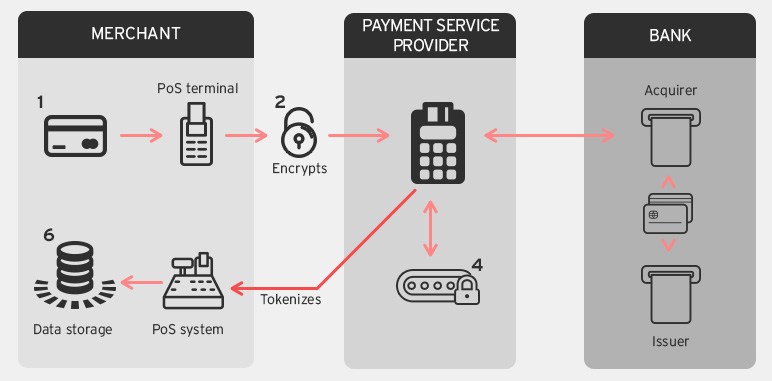 How encryption plus tokenization works
How encryption plus tokenization works
This system ensures that the actual credit card data is never present in device memory or in any other system on the merchant’s end. Stolen tokens cannot be used to create counterfeit credit cards and cannot be used in card-not-present transactions.
Cloud PoS Systems
With Software-as-a-Service (SaaS) becoming popular, there is an increasing shift towards cloud based PoS systems. Cloud PoS systems provide merchants with a low cost, feature rich, flexible, and secure payment transaction system.
There are a number of advantages to using cloud PoS that are convincing merchants to make the switch, including:
- There are no expensive setup costs involved. Merchants can install the payment applications on their own tablets, mobile phones, computers, etc. and start receiving payments.
- Most cloud PoS systems offers easy integration with existing e-commerce websites.
- Cloud PoS systems do secure transmission and storage of sensitive credit card data.
- Cloud PoS vendors guarantee system uptime and service availability.
- Data from multiple devices and locations are centrally stored and processed in the cloud. This simplifies data management and provides secure access to that data from any device, any place.
- Cloud PoS systems have an offline mode in the event of a network failure. The payment application will batch transactions and send them once the network connection is re-established.
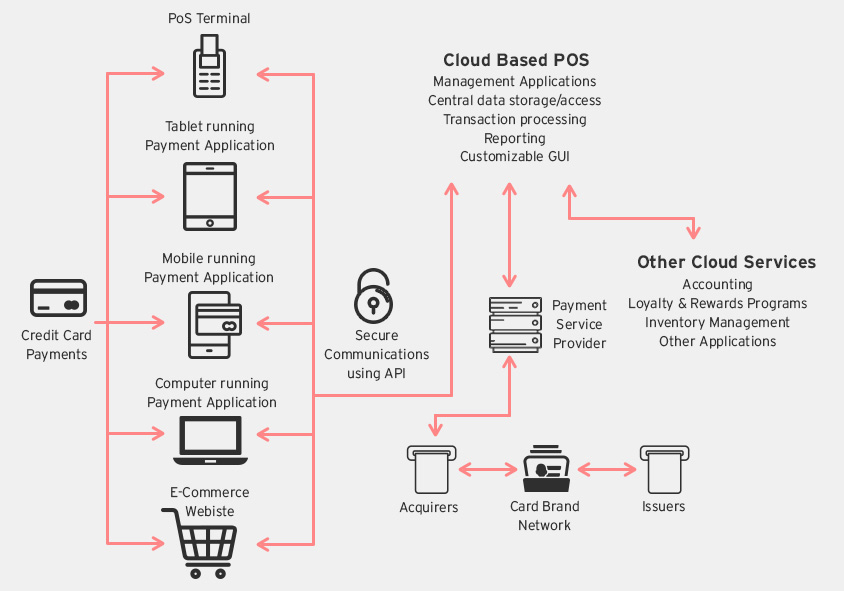 Cloud PoS Architecture
Cloud PoS ArchitectureSecure Element
This architectural solution uses a secure element to process credit card transactions.
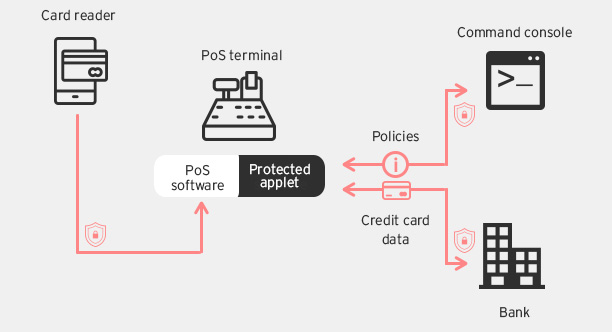
In this system, the credit card information is read by the PoS terminal and sent directly to a secure element, which Intel calls Protected Applet (PA), bypassing the PoS software. The PA manages all transaction processing requests with the banks and can be configured to share certain data with the PoS software. Moving all credit card processing actions to the secure element and completely bypassing the RAM ensures the sensitive data cannot be stolen by RAM Scraper malware. The secure element is designed to be tamper resistant and cannot be infected by malware.
These solutions represent the best prospects for secure payment transactions in the near future. While they are more secure than existing mobile payment methods, they have certain features that still have the potential for attacks.
[MORE: Next-Gen Payment Processing Technologies: What They Are, and How They Work]
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- Threat Attribution Framework: How TrendAI™ Applies Structure Over Speculation
- AI Skills as an Emerging Attack Surface in Critical Sectors: Enhanced Capabilities, New Risks
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One