Ransomware Spotlight: TargetCompany
Top affected countries and industries
according to Trend Micro data
In this section, we examine the TargetCompany ransomware’s attempts to compromise organizations since it was first reported in 2021, based on Trend Micro™ Smart Protection Network™ country, regional, and industry data. Note that this data covers only Trend customers and does not contain all victims of TargetCompany.
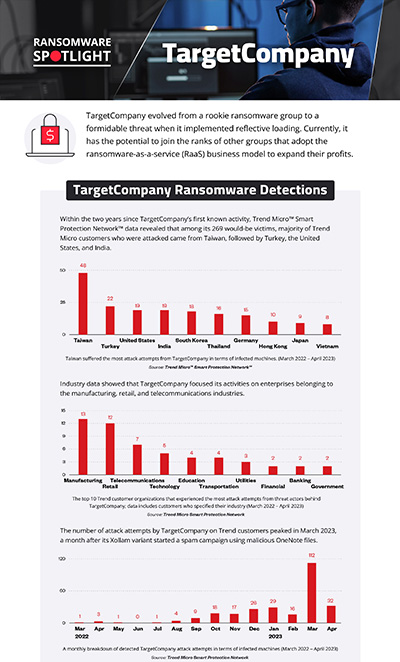
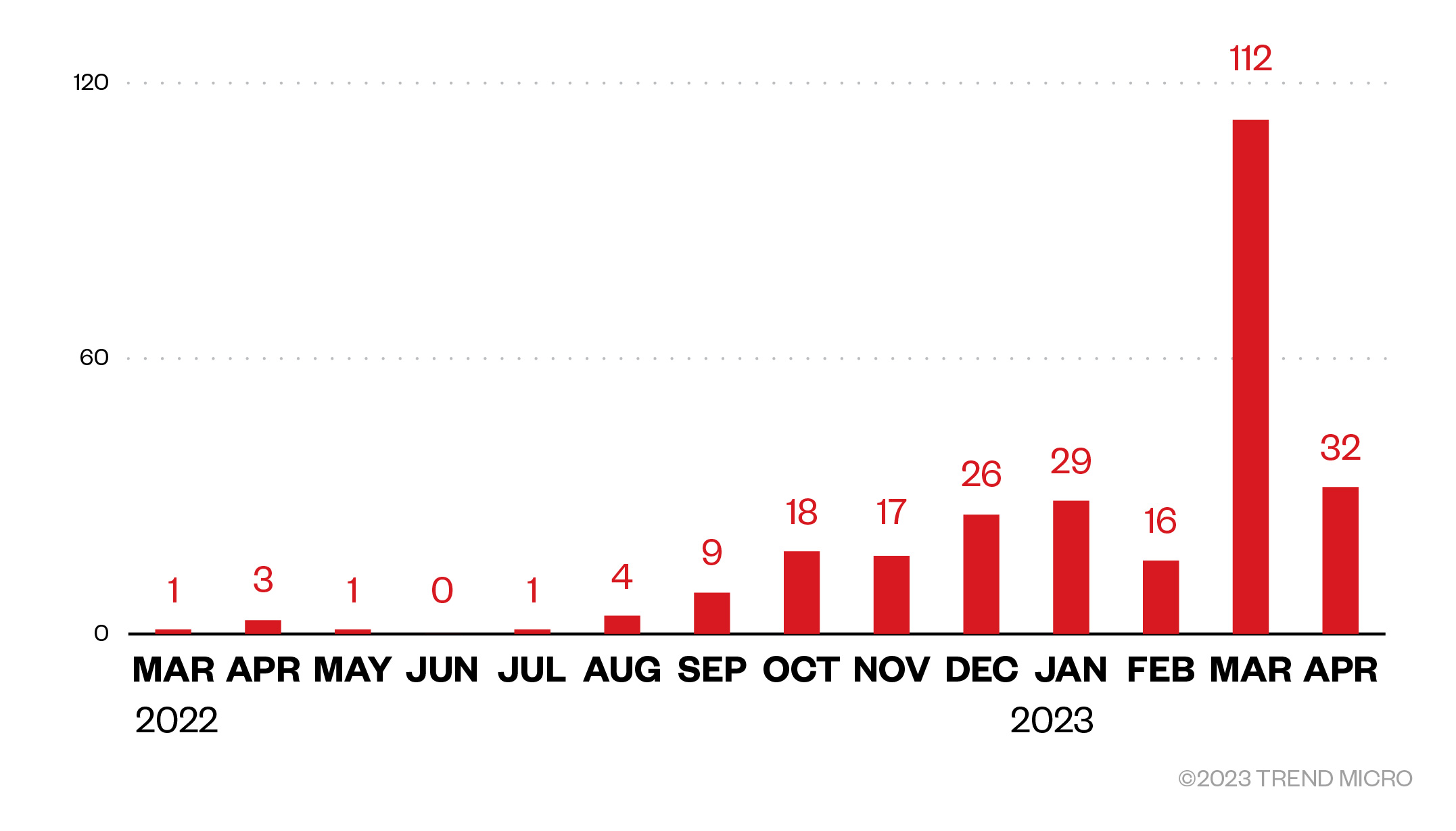
Our telemetry data detected attempted attacks from the TargetCompany group on Trend customers as early as March 2022. By April 2023, our detections total 269 attempted attacks.
TargetCompany has been observed to avoid attacking enterprises from Kazakhstan, Russia, Qatar, and Ukraine, although the group claims that its attack behaviors and patterns are not politically motivated.
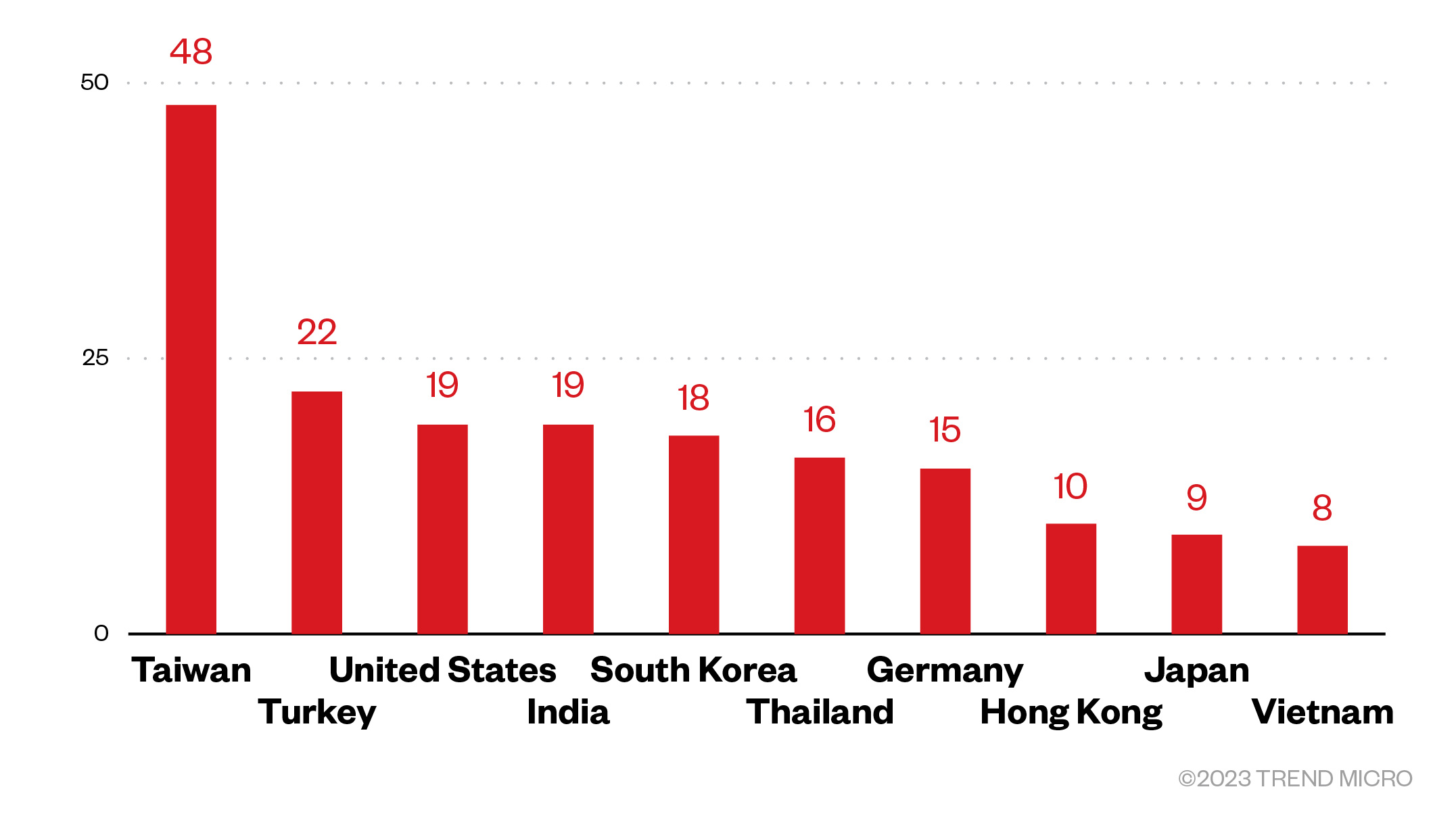
Our telemetry data showed that many of the top 10 countries targeted by TargetCompany are Asian countries. Of the 269 Trend customers targeted, 250 disclosed their locations.
Figure 3. The top 10 countries from a total of 250 detected attack attempts in terms of infected machines for the TargetCompany ransomware (March 2022 – April 2023)
Source: Trend Micro Smart Protection Network
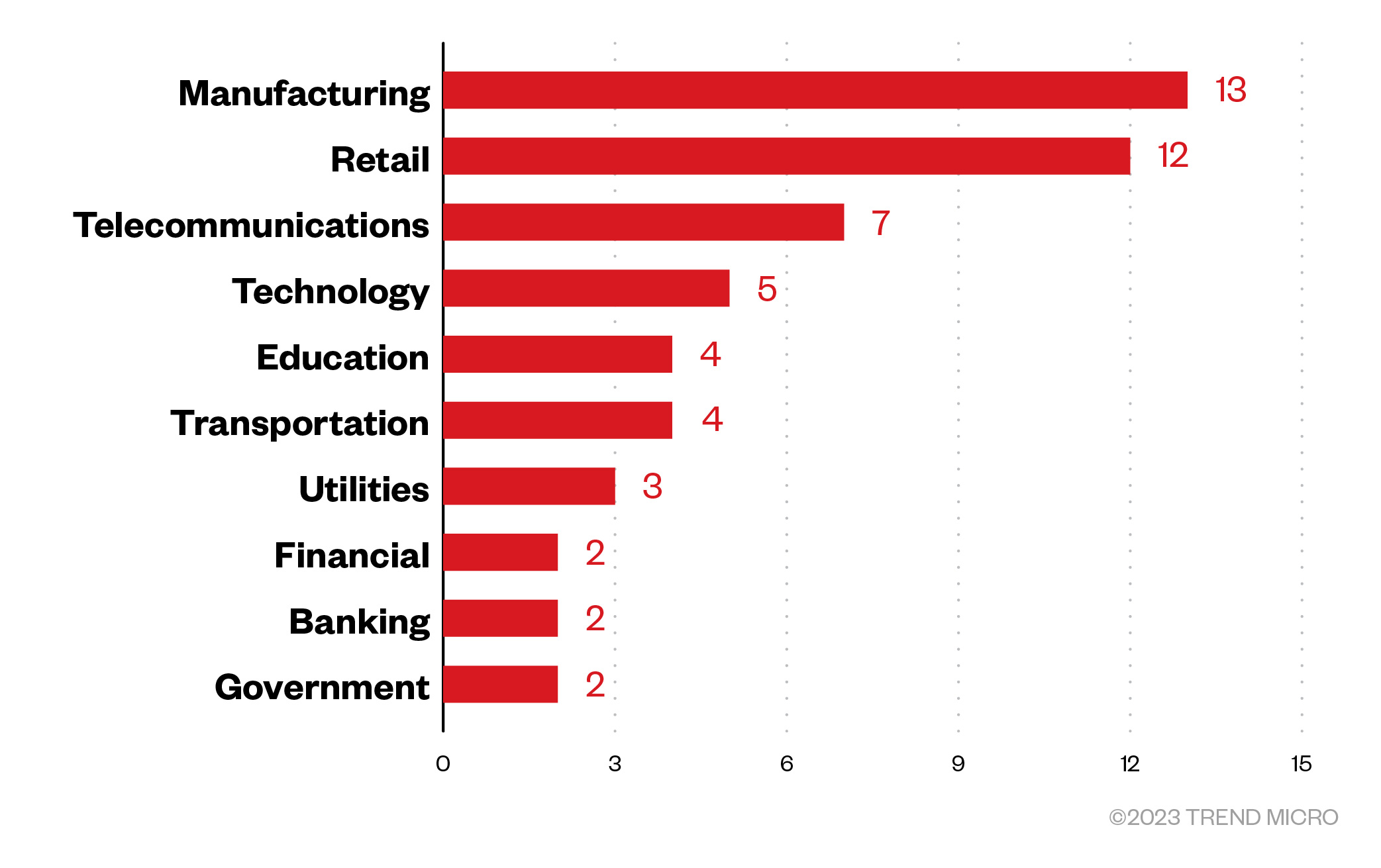
Data from customers who specified their industries showed that the ransomware group targeted enterprises in the manufacturing, retail, and telecommunications industries.
Figure 4. The top 10 Trend customer organizations that experienced the most attack attempts from threat actors behind TargetCompany. Data includes customers who specified their industry. (March 2022 – April 2023)
Source: Trend Micro Smart Protection Network
Targeted regions and industries
according to TargetCompany ransomware’s leak site
This section looks at data based on attacks recorded on the leak site of the operators behind the TargetCompany ransomware. Based on a combination of Trend's open-source intelligence (OSINT) research and investigations of the leak site, TargetCompany revealed 20 successfully infiltrated victims who refused to pay the ransom demand as of this writing. It is important to note that this figure might differ from the actual damage, especially since the leak site was only launched in November 2022, over a year since the ransomware group’s activities were first detected.
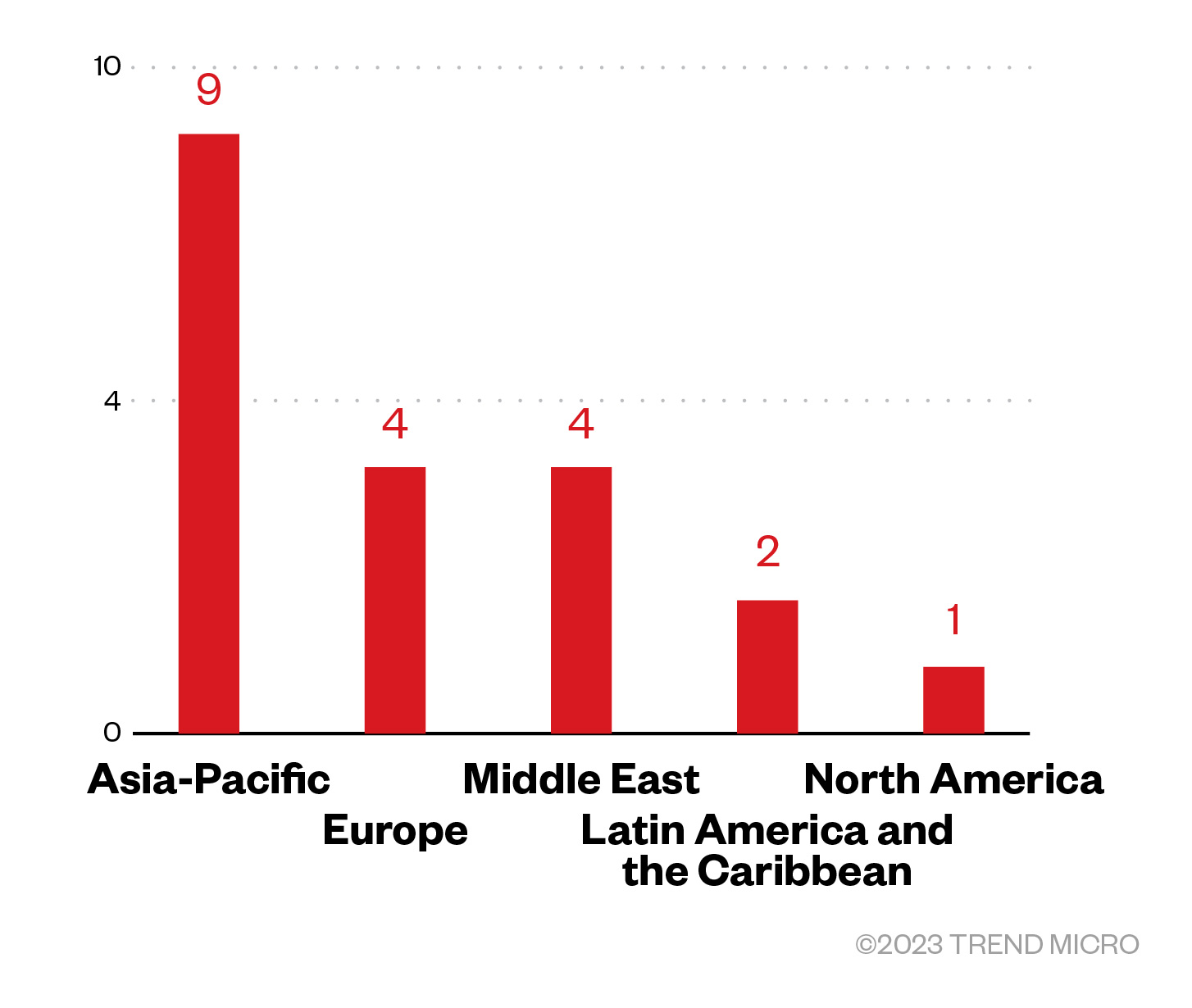
Of the total number of revealed victims in the leak site data, TargetCompany set their eyes mostly on enterprises from the Asia-Pacific region, followed by Europe and Middle East.
Figure 5. The distribution by region of Royal ransomware’s victim organizations
Sources: TargetCompany’s leak site and Trend's OSINT research
(November 2022 – May 2023)
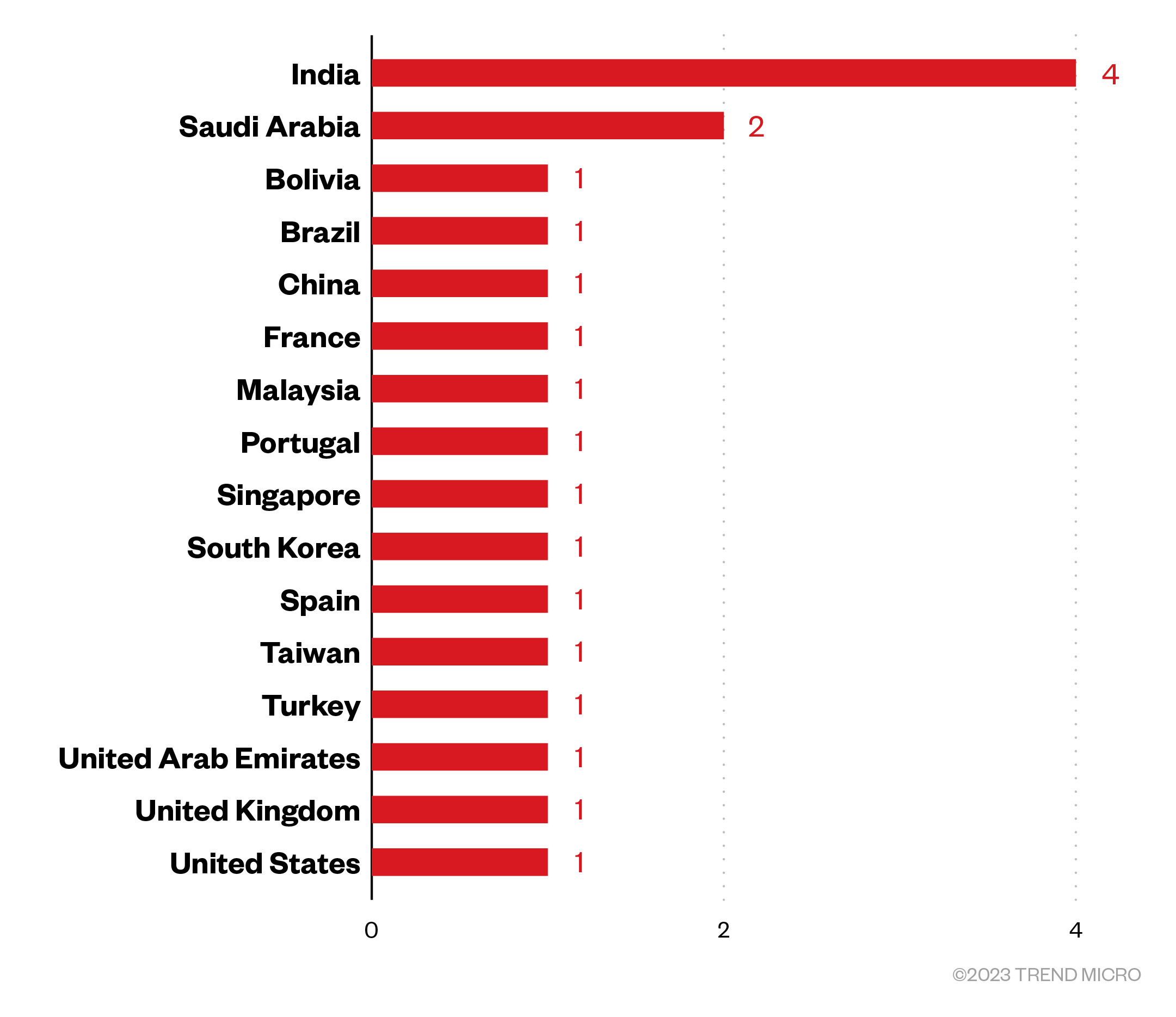
Threat actors behind the ransomware group launched attacks on organizations mostly in India, followed by Saudi Arabia, with the gang declaring only one victim from each of the other countries specified.
Figure 6. The countries and number of attacks executed by the TargetCompany ransomware group
Sources: TargetCompany’s leak site and Trend’s OSINT research
(November 2022 – May 2023)
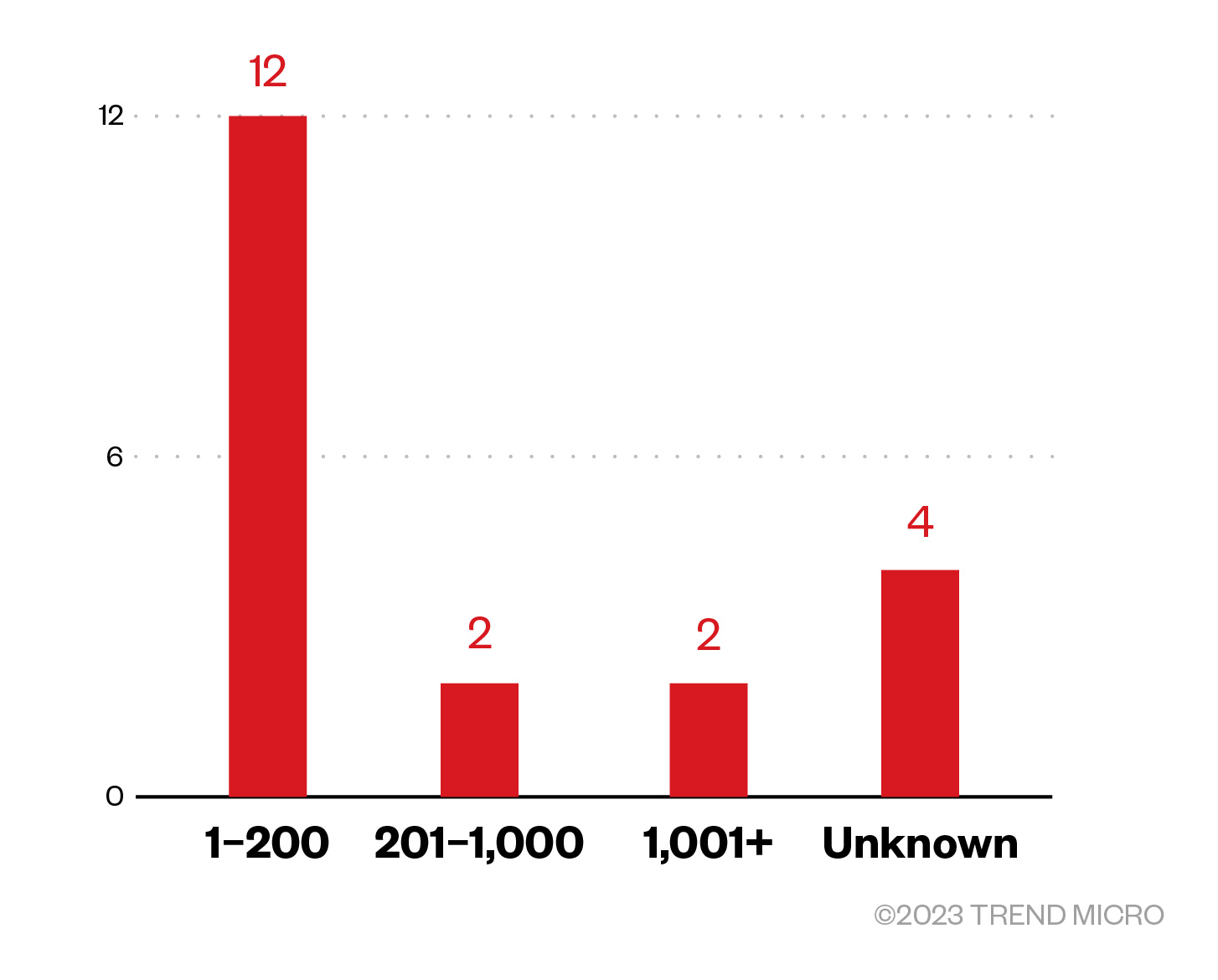
Majority of TargetCompany’s victim organizations were small businesses. However, a number of victims did not have their sizes specified.
Figure 7. The distribution by organization size of TargetCompany's victim organizations
Sources: TargetCompany’s leak site and Trend’s OSINT research
(November 2022 – May 2023)
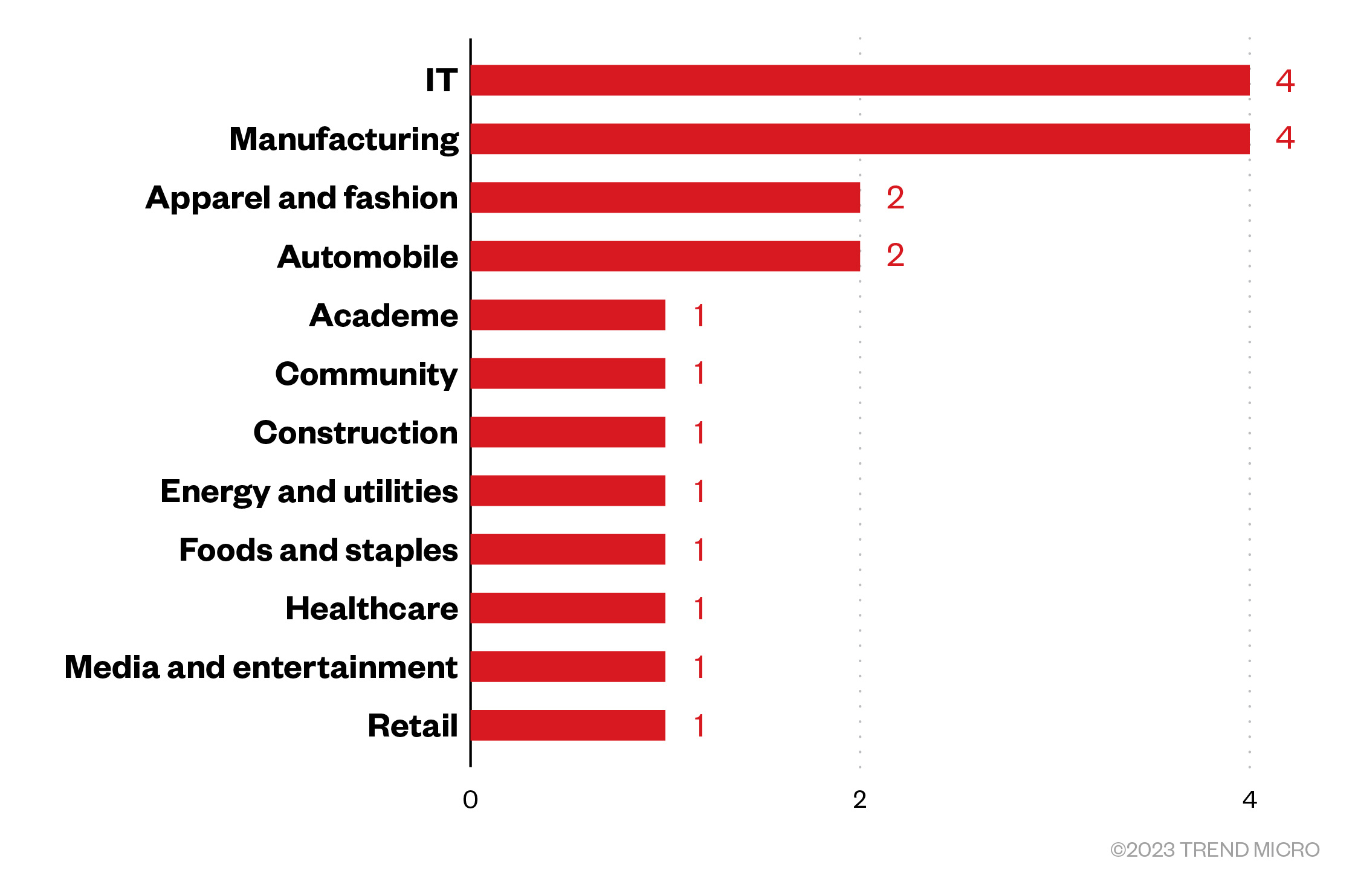
Finally, among the victims identified in TargetCompany’s leak site, the gang mostly victimized enterprises from the IT, manufacturing, apparel and fashion, and automobile industries.
Figure 8. A breakdown of the industries that suffered TargetCompany ransomware attacks
Sources: TargetCompany’s leak site and Trend’s OSINT research
(November 2022 – May 2023)
Initial Access
- TargetCompany has been observed to use CVE-2019-1069 and CVE-2020-0618, remote code execution (RCE) vulnerabilities that allow attackers to execute arbitrary code.
- The group possibly also leverages remote execution via the xp_cmdshell feature in Microsoft SQL Server.
- The latest variant of TargetCompany ransomware, Xollam, executed a spam campaign that proved to be successful in delivering malware using OneNote malicious files as an initial access technique to gain access to its victim’s system.
Execution
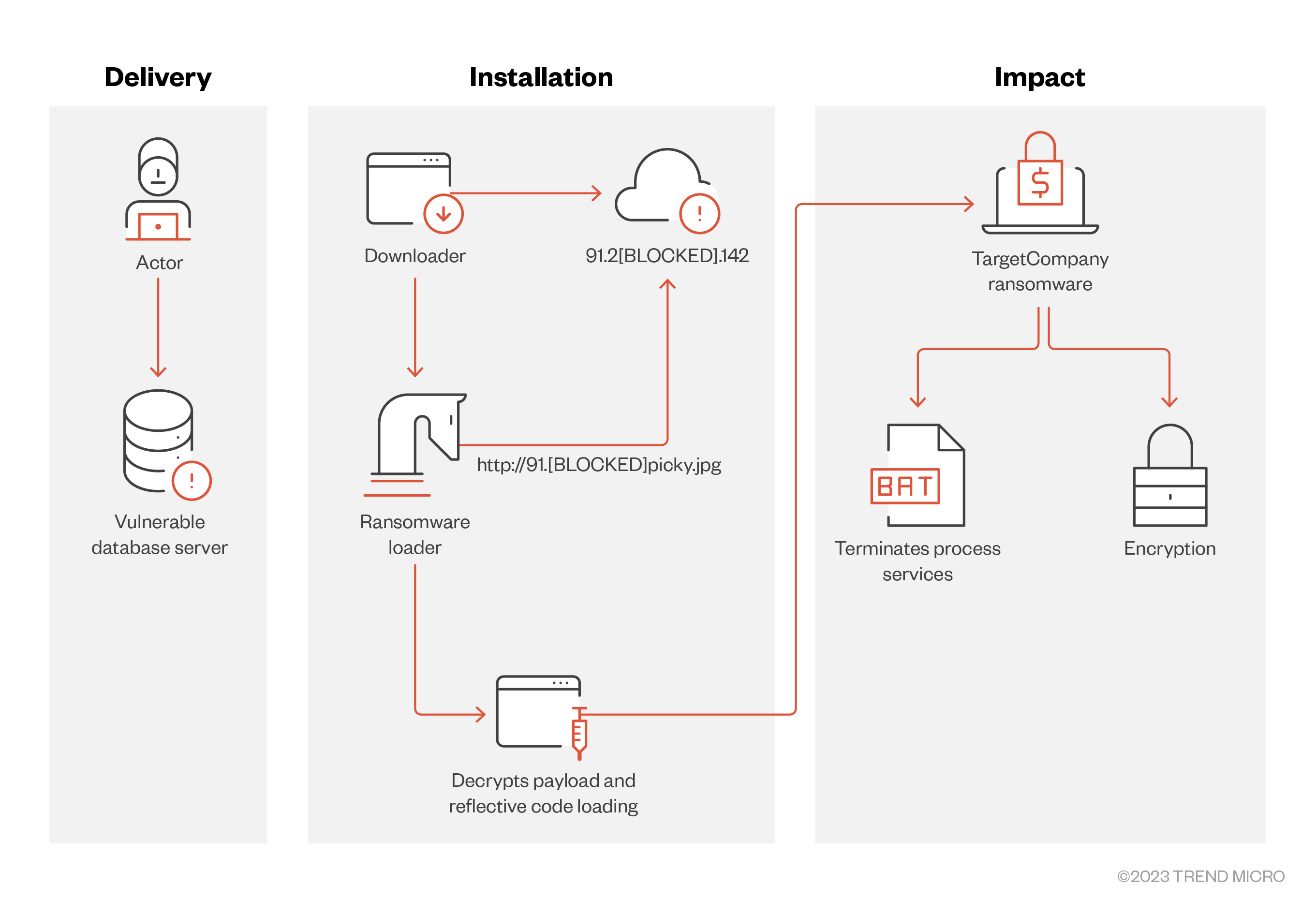
TargetCompany threat actors execute the following commands that create a PowerShell script. This script downloads a malicious file from the TargetCompany C&C server to execute on the target system via WMIC.
Figure 10. The command TargetCompany executes to create a PowerShell script that downloads its payload from its C&C server
- Payloads of early versions of the ransomware from June 2021 were dependent on the link downloaded by the PowerShell script and could either be TargetComp ransomware, the Remcos backdoor, the Negasteal malware, or the Snake Keylogger malware.
- In January 2022, the group incorporated reflective loading, wherein the PowerShell script downloaded a .NET downloader that retrieved an encrypted payload from the group’s C&C server. The payload is decrypted through XOR or inversion and is executed in memory.
Defense Evasion
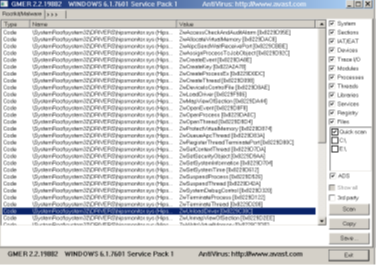
- Upon successfully gaining access to the victim’s system, attackers use tools such as GMER and Advance Process Termination to manually uninstall antivirus products on the target system.
- We also observed the presence of YDArk.exe (PCHunter64) for performing rootkit behaviors.
- We also observed TargetCompany dropping KILLAV to terminate security-related processes and services.
- The ransomware also drops a batch file named killer.bat that terminates various services and applications, including GPS-related services.
Discovery
- The TargetCompany ransomware uses network scan to collect network connection information in the system.
- We also observed the use of Mimikatz to gather credential information stored in the affected machine.
Lateral Movement
- TargetCompany threat actors use RCE via remote desktop to move laterally within the network of their victims.
Command and Control
- Throughout its evolution, TargetCompany has been consistent in accessing a C&C server to download and deliver its ransomware payload and other components. In our investigation, we discovered that the Mallox C&C server was an open directory that enabled us to easily access its content and examine it. However, the group eventually switched to using an Nginx web server, which prevents threat researchers from visiting its site.This also makes it more challenging to download the group’s payload and analyze its binaries.
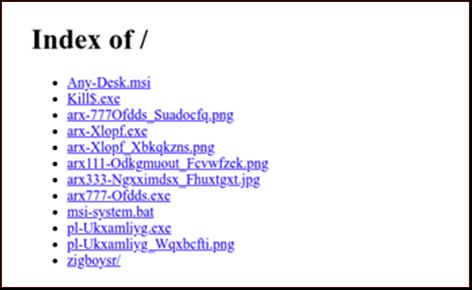
Figure 11. The text displayed on the Nginx web server that the TargetCompany ransomware group switched to from its initial open directory
Impact
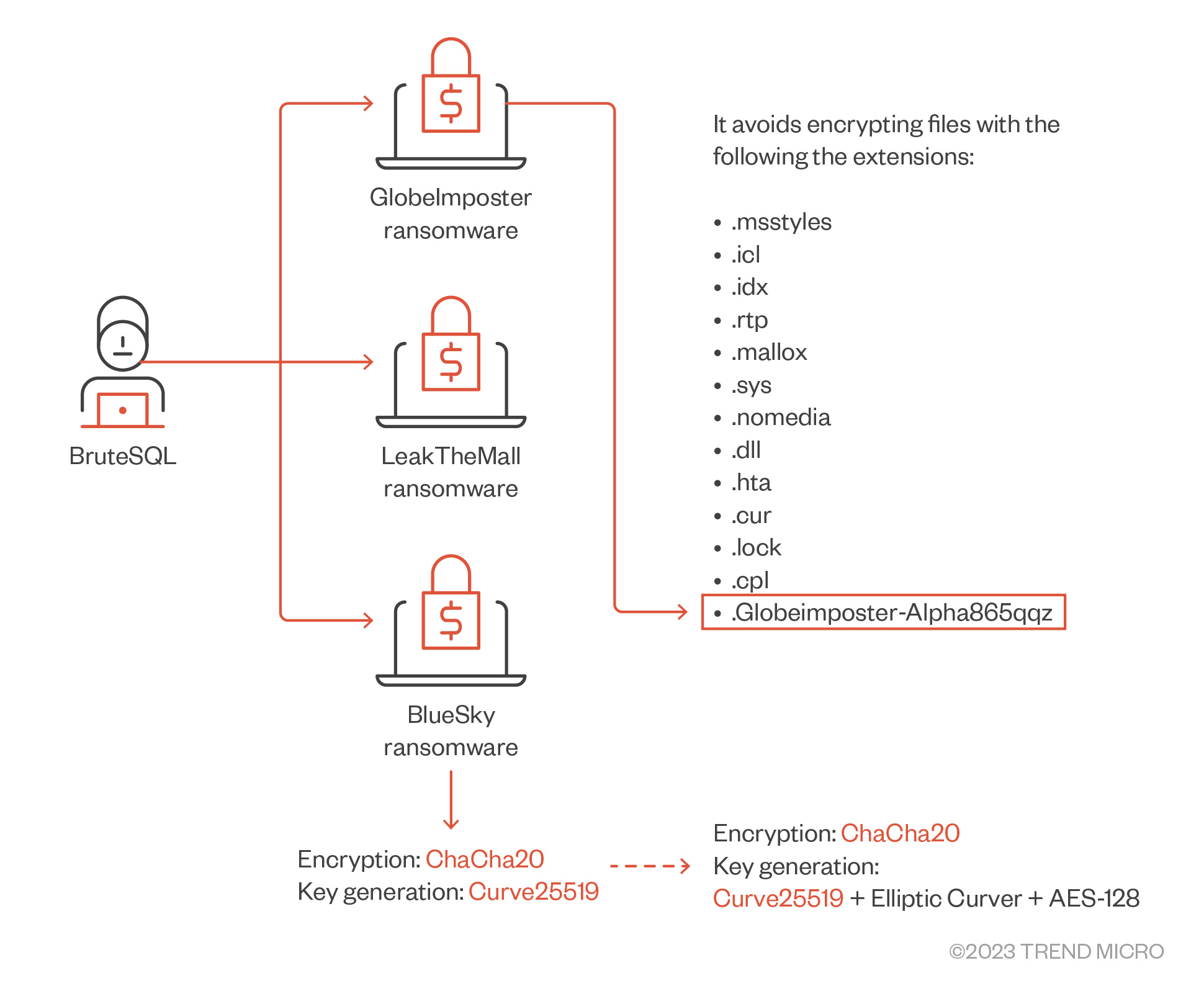
- The ransomware then encrypts the victim's files using the ChaCha20 encryption algorithm and generates the encryption keys using a combination of Curve25519, an example of elliptic curve cryptography, and AES-128.
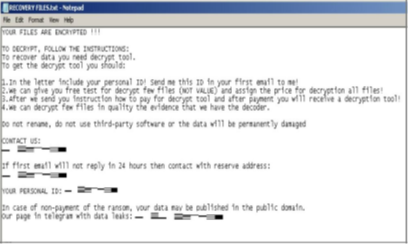
- The ransomware adds the following file extension to its encryptions (“.mallox,” “.exploit,” “.avast,” “.consultransom,” “.devicZz”) and drops HOW TO RECOVER !!.TXT"/"FILE RECOVERY.txt as its ransom note.
MITRE tactics and techniques
| Initial Access | Execution | Persistence | Defense Evasion | Discovery | Credential Access | Command and Control | Lateral Movement | Impact |
|---|---|---|---|---|---|---|---|---|
T1190 - Exploit Public-Facing Application | T1059.001 - Command and Scripting Interpreter: PowerShell T1047 - Windows Management Instrumentation T1059.003 - Command and Scripting Interpreter: Windows Command Shell | T1547.001 - Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder T1574.010 - Hijack Execution Flow: Services File Permissions Weakness T1543.003 - Windows Service | T1222.001 - Windows File and Directory Permissions Modification T1036.005 - Masquerading: Match Legitimate Name or Location T1127.001 - Trusted Developer Utilities Proxy Execution: MSBuild T1218 - System Binary Proxy Execution T1070.004 - Indicator Removal on Host T1562.001 - Impair Defenses: Disable or Modify Tools T1112 - Modify Registry T1620 - Reflective Code Loading T1070.004 - Indicator Removal: File Deletion | T1567 - Exfiltration Over Web Service T1082 - System Language Discovery T1049 - System Network Connections Discovery | T1003.001 - OS Credential Dumping: LSASS Memory | T1071.001 - Application Layer Protocol: | T1570 - Lateral Tool Transfer | T1489 - Service Stop T1486 - Data Encrypted T1490 - Inhibit System Recovery |
Summary of malware, tools, and exploits used
| Initial Access | Remcos backdoor |
| Discovery | Network scan |
| Collection | MIMIKATZ |
| Execution | Trojan.BAT.TARGETCOMP* |
| Defense Evasion | GMER |
| Advance Process Termination | |
| YDArk |
Recommendations
TargetCompany evolved from a rookie ransomware group to a formidable threat when it implemented reflective loading and might be joining the ranks of groups who adopt the RaaS business model to expand their profits. Our investigation of its tactics, techniques, and procedures (TTPs) reveals indications that the threat actors behind it share connections with other groups. There is enough indication that the TargetCompany ransomware continues to be an active threat in the landscape, which calls for sustained vigilance on the part of enterprises.
To protect systems against the TargetCompany ransomware and other similar threats, organizations can implement security frameworks that allocate resources systematically to establish a strong defense strategy.
Here are some best practices that organizations can adopt to defend themselves against the TargetCompany ransomware:
Audit and inventory
- Take an inventory of assets and data.
- Identify authorized and unauthorized devices and types of software.
- Audit event and incident logs.
Configure and monitor
- Manage hardware and software configurations.
- Grant admin privileges and access only when necessary to an employee’s role.
- Monitor network ports, protocols, and services.
- Activate security configurations on network infrastructure devices such as firewalls and routers.
- Establish a software allowlist that only executes legitimate applications.
Patch and update
- Conduct regular vulnerability assessments.
- Perform patching or virtual patching for operating systems and applications.
- Update software and applications to their latest versions.
Protect and recover
- Implement data protection, backup, and recovery measures.
- Enable multifactor authentication (MFA).
Secure and defend
- Employ sandbox analysis to block malicious emails.
- Deploy the latest versions of security solutions to all layers of the system, including email, endpoint, web, and network.
- Discover early signs of an attack, such as the presence of suspicious tools in the system.
- Use advanced detection technologies such as those powered by AI and machine learning.
Train and test
- Regularly train and assess employees’ security skills.
- Conduct red-team exercises and penetration tests.
A multilayered approach can help organizations guard possible entry points into their system (endpoint, email, web, and network). Security solutions can detect malicious components and suspicious behavior, which can in turn help protect enterprises.
- Trend Vision One™ provides multilayered protection and behavior detection, which helps block questionable behavior and tools early on before ransomware can do irreversible damage to the system.
- Trend Cloud One™ – Workload Security protects systems against both known and unknown threats that exploit vulnerabilities. This protection is made possible through techniques such as virtual patching and machine learning.
- Trend Micro™ Deep Discovery™ Email Inspector employs custom sandboxing and advanced analysis techniques to effectively block malicious emails, including phishing emails that can serve as entry points for ransomware.
- Trend Micro Apex One™ offers next-level automated threat detection and response against advanced concerns such as fileless threats and ransomware, ensuring the protection of endpoints.
Indicators of Compromise (IOCs)
The IOCs for this article can be found here. Actual indicators might vary per attack.
Trend Micro Vision One Hunting Query
Trend Vision One customers can use the following hunting query to check if their network/system is possibly affected by TargetCompany ransomware:
((processCmd:"?:*\\cmd.exe" AND objectFilePath:"*.update.ps1*") AND (objectFilePath:"*.update.ps1 & WMIC processs call create*")) OR ((processCmd:"?:*bat.exe" AND objectFilePath:"*-win -enc*")) OR (fullPath:”(*.XOLLAM OR *.MALLOX OR *.FARGO OR *.MALLAB)”)
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines



 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One