Mobile Payment Systems: How Android Pay Works
Google Wallet, which was succeeded by Android Pay in September 2015, is the mobile payment app for Android users. Supported by Android KitKat and newer, Android Pay supports tap-and-pay transactions using the device's near field communications (NFC) feature. To make it work, users need to install the app and input the card number and other details necessary for payment verification, such as name and address. Users who have accounts with major credit or debit cards in the US can just take a snapshot of the card using their smartphone's camera and it automatically inputs the date of expiration.
How does Google Wallet/Android Pay work?
Google Wallet/Android Pay operates in two ways—card emulation with secure element (SE) and host-based card emulation. In card emulation with secure element, the device is placed on the NFC terminal and all the data read will be routed in SE, which is responsible for the communications with the NFC terminal. Once the transaction is done, the application can query the SE regarding the status and notify the user.
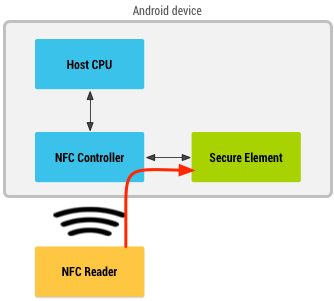 Card Emulation with a Secure Element (Source: developer.android.com)
Card Emulation with a Secure Element (Source: developer.android.com)
With host-based card emulation, the Android OS and the app is directly involved in the processing of payment transaction. Once the user brings the device up to the NFC terminal, the app performs the card emulation and handles communication with the terminal. All data is hosted in a cloud environment, which does the actual transaction processing before it brings back the status to the app.
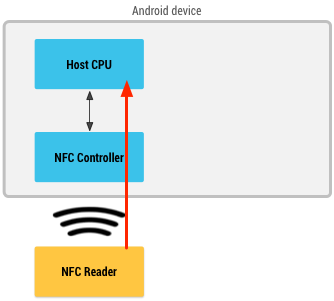 Host-based Card Emulation (Source: developer.android.com)
Host-based Card Emulation (Source: developer.android.com)
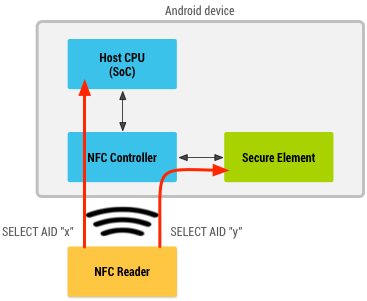
Device operating both SE and HCE (Source: developer.android.com)
What are its advantages?
Apart from the convenience it offers, given that it works together with major credit and debit companies and is supported by a lot of US retailers, Google Wallet/Android Pay hosts the data transmitted during transactions in a secure cloud environment. It does not store any of the user data on the device itself, which means that if the Android device is infected with information-stealing malware, the user information and credentials used by this app won’t necessarily be stolen by the cybercriminals.
What are its disadvantages?
It's no secret that the open source Android platform has suffered from a long list of vulnerabilities and exploits. And while Google pushes updates for these vulnerabilities, not all devices of different manufacturers can receive those patches due to mobile fragmentation. This can make those devices vulnerable to attacks.
There are also reports regarding Google Wallet Relay attack that requires the target card to be in close proximity with a reader device, besides needing to install relay software to work. In effect, it can potentially communicate the data transmitted over the network or have privilege access to it.
[MORE: Next-Gen Payment Processing Technologies: What They Are, and How They Work]
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- Forecasting Future Outbreaks: A Behavioral and Predictive Approach to Proactive Cyber Risk Management
- Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report
- The Industrialization of Botnets: Automation and Scale as a New Threat Infrastructure
- From Holiday Snap to Custom Scam in 30 Minutes: How AI Turns Public Photos Into Targeted Attacks
- From LinkedIn to Tailored Attack in 30 Minutes: How AI Accelerates Target Profiling for Cybercrime

 Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report
Fault Lines in the AI Ecosystem: TrendAI™ State of AI Security Report AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One