Beyond the Bells and Whistles: A Look at Mobile OS Updates
The third quarter of 2013 marked a “first” for Google, as Android™ captured an 81% share of the mobile market. IDC reported that this is the first time Android surpassed the 80% market share mark. The report also stated that 211.6 million smartphones were shipped in the quarter, marking a 39.9% growth from the same quarter of last year.
These numbers proved that the move to mobile continues. CCS Insight, in fact, predicted that 6.6 billion mobile phones will be in use by 2017. But are you keeping the additional mobile devices you’re buying safe?
It’s all too easy to become sidetracked by the fancy features and add-ons that come with the latest platform update rollouts. Keep in mind that as the mobile threat volumecontinues to surge, security should become your top priority.
Two major OS updates were released this year—iOS 7 and Android KitKat. Just like we did with previous versions when they were released, let’s take a look at some of the new security features the new OS versions offer and what these mean for you.
iOS 7Boasting of undergoing “the biggest change” to the platform since the introduction of the iPhone, much of the press coverage focused on how iOS’s user interface (UI) design drastically changed. But while the OS’s look changed, has it made Apple device users feel safer?
Some law enforcement agencies seem to think so. Amid the rise in iPhone theft, law enforcers are hopeful that certain iOS 7 security features can help users protect their devices and data. Find My iPhone, an app that can locate, send a message to, and erase stored data in a missing device, for example, now requires the password for the associated Apple ID before it can be deactivated via a feature called “Activation Lock.” This may help deter strangers from immediately disabling the feature.
iOS 7 now also requires authentication for many features or processes. The only way you can only erase tracking or monitoring apps is by entering an authentication passcode that’s different from your Apple ID password. Reset—a feature bad guys often abused—can now only be accessed with your Apple ID password.
We already know that apps get more information or access than they need to work. To address this, iOS 7 has made app management more precise by allowing you to designate which apps can access the camera, cellular data, etc.
Data encryption has also improved with iOS 7. It now automatically encrypts data in both iOS and third-party apps, requiring only your passcode for activation. It also improved its virtual private network (VPN) support, allowing you to set which apps can only connect over VPN when launched. Each app’s VPN tunnel is specific to that app so your personal data and Web activity will not be combined with the app data. Unfortunately, this VPN feature is only accessible if the app allows per-app VPN.
Apple also added other features to iOS 7 that should reap big rewards for security. Personal Hotspot passwords—vulnerable to brute-force attacks in the past—are now more secure with the use of pseudorandom, 12-character, alphanumeric passwords. Apple also included a “Trust/Don’t Trust” option for connecting iOS devices to computers for the first time. This can prevent malicious or infected computers from accessing data on a connected device. Even better, the “Don’t Trust” option still allows charging. You can also block text messages, calls, and iMessages® on iOS 7, which can prevent smishing and vishing attacks.
The new Touch ID™ feature introduced in iPhone 5S may not be a software update but it’s still a feature worth mentioning. Touch ID allows you to unlock your phone using a fingerprint scan in the place of your passcode for quicker access. Unfortunately, it has already been proven vulnerable, which can become troublesome since Touch IDcan also be used to make iTunes®, iBooks®, and App Store
SMpurchases.
What This Means for iOS UsersMost of the new iOS 7 features certainly help deal with iPhone theft and unauthorized account access. Additional measures also mean taking extra steps or exerting extra effort though. Restarting your Apple device, for example, now requires entering your Apple ID and password courtesy of Activation Lock. But given that security is the pay-off, taking extra steps is well worth the effort.
Entering your Apple ID and password even when doing just basic tasks like unlocking your device means these have become more valuable than before. Unfortunately, too, there’s a(n underground) market for that. The previous spike in Apple phishing sites showed how interested cybercriminals were in Apple IDs; they’ll be even more now, so keep your Apple ID and password secret.
Android KitKatAfter months of speculation and guessing, Google finally revealed that its latest Android OS version would be called “KitKat.” Android underwent some changes in security.
A major change to the platform is the implementation of security-enhanced Linux (SELinux). SELinux was made available on Jelly Bean though only in permissive mode, which meant you could monitor your device for suspicious activities but won’t be able to address them. In KitKat, SELinux is now available in “enforcing mode.” This means it can stop mobile threats from gaining root access to your device via buffer overflow and privilege escalation attacks.
Google also added an optional feature called “device-mapper-verity” (dm-verity).” It can help you check if changes or updates were made to the OS by unauthorized users. This feature can help protect your device from rootkits, which often have higher access privileges and so may go undetected by security software.
Google also improved how Android handled digital certificates. Bad guys often create fake certificates and pass off fake sites for legitimate ones. Now, you will be notified every time you visit a site that uses a suspicious certificate. KitKat also boasts of certificate pinning, which detects SSL/TLS communications that use fake certificates.
Google also introduced per-user VPN, a plus for shared devices. This means you can use a VPN that’s different from your co-users’. We have seen reports though that the VPN feature only works for the first user; the rest will have to make do without VPN access.
Android KitKat is relatively lightweight. It can run using as little as 512MB of RAM, which means even older devices can run it. This could be seen as a deliberate move by Google, as 26.3% of Android users still run Gingerbread.
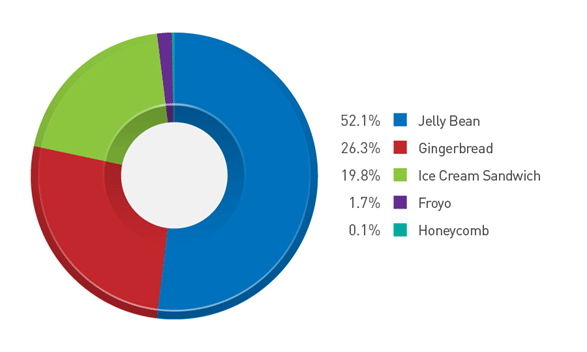
Figure 1: Android versions in use as of November 1, 2013
Some still won’t be able to get KitKat though. Given the Android fragmentation problem, some hardware developers may decide to not make the update available to their users.
What This Means for Android UsersWhile Google has exerted considerable effort to beef up Android’s security, some of KitKat’s features may still not be enough to protect you from threats. Dm-verity, for example, while powerful is optional. Not everyone may understand how it works and so may choose not to use it. The existing fragmentation issue also means Android users will not get the same level of protection across the board.
No matter how many new security features Google introduces, your device’s security still largely rests on your hands. Every Android device needs a security solution to detect and block threats, including dangerous sites like a fake mobile Facebook page that asks for log-in credentials and credit card information.
Fake apps were common threats for Android users, especially as the number of malicious and high-risk apps has reached the 1-million mark without any sign of slowing down anytime soon. Fake apps are often found in third-party app stores, which may not be strictly monitored compared with Google Play™.
You can also avoid downloading fake apps to a certain degree by avoiding third-party app stores; download only from official app stores. Pay attention to even the tiniest details; a lot of fake apps will try to pass themselves off as the real thing. Check for misspellings in publishing (e.g., developer’s name) details though using a security solution is still better if you just don’t have the time to nitpick.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One