In Transit, Interconnected, at Risk: Cybersecurity Risks of Connected Cars
 Download Cybersecurity for Connected Cars: Exploring Risks in 5G, Cloud, and Other Connected Technologies
Download Cybersecurity for Connected Cars: Exploring Risks in 5G, Cloud, and Other Connected Technologies
5G-enabled vehicle connectivity to networks, devices, and other vehicles
Connected Cars and 5G
With regard to 5G in connected cars, it's important to consider how 5G links a vehicle to its surroundings through cellular vehicle to everything (C-V2X). While C-V2X also functions for 4G-connected vehicles, in 5G C-V2X comes into maturity. C-V2X is intended to thoroughly make a 5G car a part of the environment around it, making it capable of reacting to events.
Here are some of the ways that C-V2X links vehicles to their environment:
Vehicle to Network (V2N)
V2N helps with disseminating information, such as high-traffic conditions, changes in weather, and events that affect public safety. Internally, the vehicle can benefit from more reliable connectivity, anti-theft measures, and fleet management.
Vehicle to Device (V2D)
Vehicle-pedestrian collisions can be avoided through V2D, as the location of pedestrians carrying personal devices or cellphones can be relayed to vehicles. Information gathered inside the car can also be leveraged by fleet managers for analytics.
Vehicle to Vehicle (V2V)
V2V helps prevent vehicle-to-vehicle collision as it enables securely navigating intersections. As connected vehicles approach an intersection, they communicate by exchanging certificates directly through public key infrastructure (PKI). It also helps with the day-to-day activities of connected car users, such as changing lanes or looking for parking spots.
Connected Cars and the Cloud
Our vision of a cloud-linked ecosystem for connected cars
We explored the idea of moving some of the electronic control units (ECU) to the cloud. Some advantages of doing this would be:
- Simplified E/E architecture, leaving fewer ECUs to manage in the car itself
- Massively expanded processing capabilities using cloud computing
- Enhanced road situational awareness, from local to up to 500 m radius
- Improved fuel, battery, emissions, and operational efficiency
- Distributed cloud servers plus full-coverage, low-latency network, makes attackable surfaces more resistant to malicious attacks
Still, there are also immediate risks with having a cloud-based car E/E architecture. Some of the mainstream cloud attacks that OEMs, suppliers, and drivers need to worry about include:
- Denial of service (DoS)
- Man-in-the-middle (MitM) attack
- Hijacking of services
- Latency issues
- Misconfiguration issues
- Cloud supply chain issues
Connected Cars and Fleet Management
Fleet management involves handling a unit (aka a fleet) of vehicles such as taxis, trucks, or even autonomous vehicles such as delivery drones. This can be done for connected cars as well. Handling vehicles in a fleet helps manage costs and improve safety. Inevitably, some cybercriminals will target these units via these following threats, among others:

Underground taxicab fraud
Hacker underground forums offer software for taxi fraud, such as simulators that fake vehicle activity. When this software is used in connected taxis, it can falsify data such as the driving and pickup history to make more money.

DDoS and MitM attacks
An attack on even a single connected car can be dangerous, so launching attacks on a fleet is potentially catastrophic to the safety of many drivers and passengers.
Connected Cars and
Traditional IT Attacks
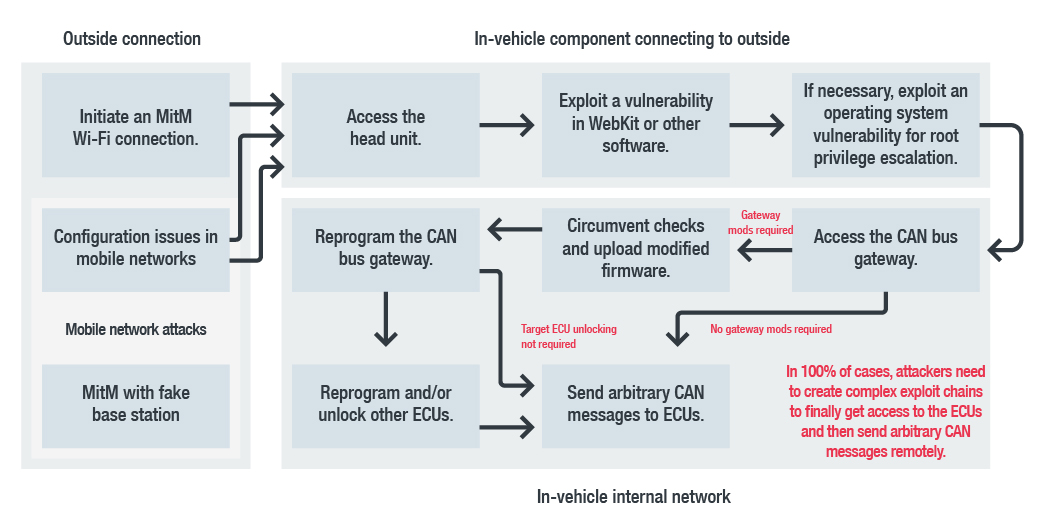
What usually happens in a traditional IT attack on a connected car? We analyzed four remote car-hacking case studies (Jeep Hack 2015, Tesla Hack 2016 and 2017, and BMW Hack 2018) and spotted a pattern followed by these attacks.
A generalized remote hacking attack chain based on the featured remote attack case studies
Some of our observations are:
- The initial attack vector is either via a mobile network or via a Wi-Fi network. In all four case studies, the hackers attempted some type of MitM attack using these channels.
- The attackers always targeted the head unit, which is the infotainment hub of the vehicle. Head units are found in all modern cars, with different degrees of functionality depending on whether the car is a basic or luxury vehicle. All new head units can talk to the gateway ECU, which makes them the go-to entry point into the vehicle’s bus network.
We detail the full analysis and the MITRE ATT&CK® matrix for each incident in our paper.
Like in most cybercriminal activities, attackers who attempt to launch attacks on connected cars will most probably be motivated by financial gain, and thus will go after various lucrative targets such as physical access to connected cars to steal driving services, goods inside a car, or the car itself. Attackers could also target data collected, generated, stored, and shared by cars, especially personally identifiable information (PII) that they could sell to interested parties. It is also possible that attackers would steal the network and processor resources of these cars, as well as the stored energy inside cars.
We expound on these cybersecurity risks and their effects in our paper, "Cybersecurity for Connected Cars: Exploring Risks in 5G, Cloud, and Other Connected Technologies."
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization




 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One