 Download Worm War: The Botnet Battle for IoT Territory
Download Worm War: The Botnet Battle for IoT Territory
Strength in numbers is the main principle behind botnets, networks of devices that have been infected and turned into bots to be used in performing attacks and other malicious activities. With the dawn of the internet of things (IoT), botnet developers have found a new domain to conquer, but there they must compete with one another to grow their bot armies. This so-called worm war is being waged unbeknown to the users who stand to lose control of their devices no matter which cybercriminal ends up winning each battle.
Users must understand the arsenal used in building botnets and turning common IoT devices such as routers into bots. In our research paper “Worm War: The Botnet Battle for IoT Territory,” we take an in-depth look at the world of IoT botnets. In this article, we give a preview of the main capabilities of botnet malware using the three bot source codebases we have identified to have paved the way for many botnet malware variants and formed the basis of the ongoing turf war.
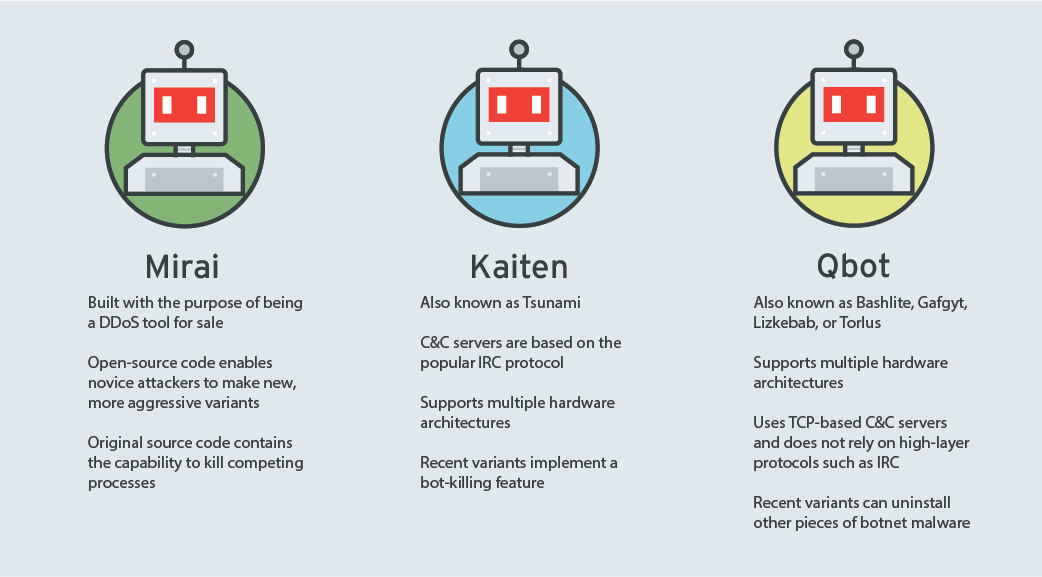
Kaiten
Also known as Tsunami, Kaiten is the oldest of the three. Its communication with its command-and-control (C&C) servers is based on the IRC (Internet Relay Chat) protocol, whereby infected devices receive commands from an IRC channel. Kaiten’s script also allows it to work on multiple hardware architectures, making it a relatively versatile tool for cybercriminals. In addition, recent variants of Kaiten can kill competing malware, allowing it to fully monopolize a device.
Qbot
Also known as Bashlite, Gafgyt, Lizkebab, and Torlus, Qbot is also a relatively old malware family, but it remains significant for botnet developers. What is most notable about Qbot is that its source code is made up of only a few files. It is difficult to use for beginner botnet developers, as evidenced by many tutorials and guides for using the malware in cybercriminal forums. Like Kaiten’s, Qbot’s source code can support multiple architectures, but the malware’s communication with its C&C servers is based on TCP (Transmission Control Protocol) instead of IRC. Recent Qbot variants also have the capability of killing rival malware.
Mirai
Mirai is the most recent of the three, but it has become a popular botnet malware family, having spawned numerous variants. It was created with the goal of becoming a distributed denial-of-service (DDoS) tool for sale. After its source code was made public, Mirai became a game changer for IoT malware. When it first entered the arena of botnet malware, it quickly made a name for itself through the attack on Dyn, a Domain Name System (DNS) hosting provider, that resulted in the disruption of widely used websites and services.
Botnet battle tactics
Kaiten, Qbot, and Mirai demonstrate the capabilities that allow botnet malware to compete for dominance over connected devices. To grow a botnet and maintain its size, botnet malware families and variants need to be able to infect as many devices as possible while defeating other usurpers. Botnet malware can search for vulnerable devices and use well-known tactics such as brute force to take control of a device. To solidify the takeover, botnet malware kills competing malware that might already be present in the device and new malware that might aim to steal its control.
The three bot source codebases under discussion have these capabilities. And since they are open-source, they allow malicious actors to continue to populate the threat landscape with competing variants.
A summary of the three main IoT bot source codebases
Defense against IoT botnets
Botnets can be grown into powerful armies of devices as demonstrated by the infamous Mirai attacks in 2016 that took down major websites (including Netflix, Twitter, and Reddit) and the well-known security blog Krebs on Security. On a smaller scale, for individual users, botnets monopolize IoT devices and resources that are meant to make their lives more convenient and their jobs easier. These devices have taken on more significance especially in a time where work-from-home arrangements have become the new norm for organizations.
The best defense strategy against warring botnets is to narrow their battlefield and deny cybercriminals the resources that would make their botnets powerful. Users can do their part by ensuring their IoT devices are secure. They can begin by following these steps:
- Manage vulnerabilities and apply patches as soon as possible. Vulnerabilities are the main way malware infects devices. Applying patches as soon as they are released can limit the chances for potential exploits.
- Apply secure configuration. Users must ensure that they are using the most secure configuration for their devices to narrow openings for compromise.
- Use strong, hard-to-guess passwords. Botnet malware takes advantage of weak and common passwords to take over devices. Users can circumvent this tactic by changing default passwords and using strong passwords.
Read more about the three highlighted botnet malware families, the cybercriminal underground activity surrounding botnets, and other defensive strategies to keep connected devices safe in our research paper “Worm War: The Botnet Battle for IoT Territory.”
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One