Threat Actors Deliver Courier-Themed Spam Campaign with Attached ACE Files

Insights and Analysis by Miguel Ang
Trend Micro researchers detected a new courier service themed malicious spam campaign that uses ACE files (detected by Trend Micro as Trojan.Win32.GULOADER.A) as attachments. The samples were gathered from our honeypot.
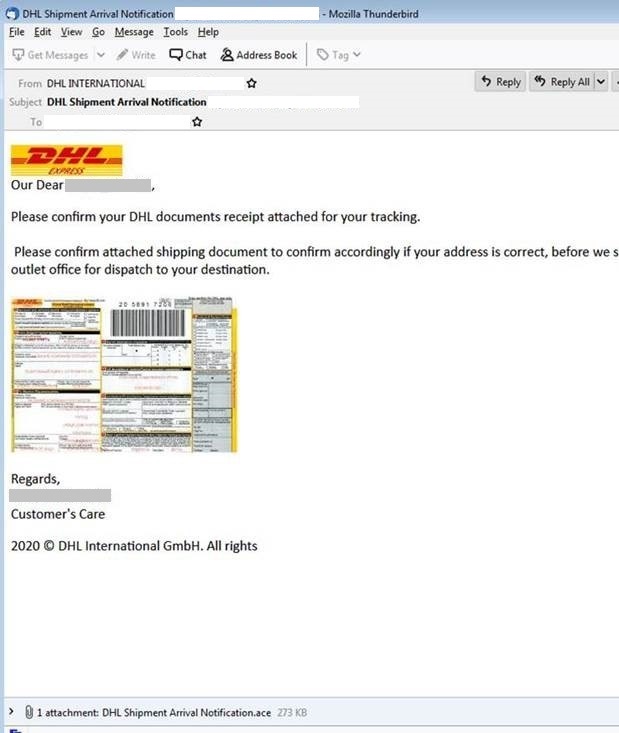
Figure 1. Sample DHL-themed spam email
The ACE file contains a zip file and an executable payload, which acts as a downloader upon extraction and execution.
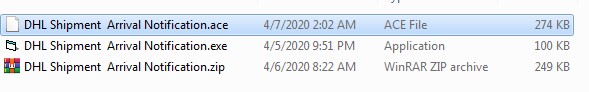
Figure 2. Attachment Contents
The zip is password protected and contains another executable.
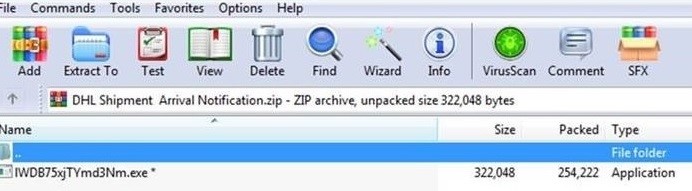
Figure 3. DHL themed spam
The binary is a downloader that will access a link to download its payload, set up a startup registry, and execute the payload using a VBS script. The indicated link does not download a file. However, the setup still makes future compromise possible.
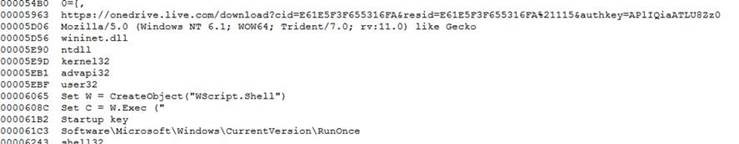
Figure 4. Binary file from the malicious attachment
We have been receiving other spam samples with the same payload. ACE is a data compression archive produced by WinACE. It can be opened using tools such as WinACE or BitZipper.
Delivery services themed campaigns are not new; earlier campaigns we detected delivered backdoor, Emotet, trojans, and other malware types. Other payloads made it possible to intercept text messages.
Thwarting spam campaigns
-
Do not download attachments or click links from unverified sources.
-
If the email comes from a seemingly familiar source, verify via the company’s phone number or other contact details if they indeed sent the email.
-
If the company sent legitimate emails before, check the new sender’s email address. If it is an entirely different source or the email address is spoofed, the email is most likely spam.
-
Take advantage of security solutions for spam and other email-based threats such as phishing and business email compromise (BEC).
Indicators of Compromise
| Filename | SHA-256 | Trend Micro Pattern Detection |
| DHL Shipment Arrival Notification.exe | accfdbd1af174d1134015daa4bc39ee1 b5c8b88df4ecee8ea0c9cda660bb18c7 |
Trojan.Win32.GULOADER.A |
| DHL Shipment Arrival Notification.ace | 1e6db9987ba9662be6f49c006b042766 f85027266427d6e3b3c62faac310542d |
Trojan.Win32.GULOADER.A |
| DHL Shipment Arrival Notification.zip |
eaa6bbbfd75eab17c2808b0c2dd4a5d5 a5ee473cc7cd5e93ce4302c4f830202d |
N/A |
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One