Ransomware Recap: Satan Offered as Ransomware as a Service
 Ransomware continues to make headway in the threat landscape despite the use of techniques and routines that have become commonplace. Take for instance the fittingly named ransomware that emerged last week: Satan (detected by Trend Micro as RANSOM_NATAS.A). Peddled as a service to fellow cybercriminals, distributors of the ransomware get 70% of the ransom paid by the victim. Satan's service lets affiliates generate a custom executable file to be used in their campaign, which also includes the ransom price. Subscribers of the service can also set the price and time limit.
Ransomware continues to make headway in the threat landscape despite the use of techniques and routines that have become commonplace. Take for instance the fittingly named ransomware that emerged last week: Satan (detected by Trend Micro as RANSOM_NATAS.A). Peddled as a service to fellow cybercriminals, distributors of the ransomware get 70% of the ransom paid by the victim. Satan's service lets affiliates generate a custom executable file to be used in their campaign, which also includes the ransom price. Subscribers of the service can also set the price and time limit.This ransomware targets 131 file
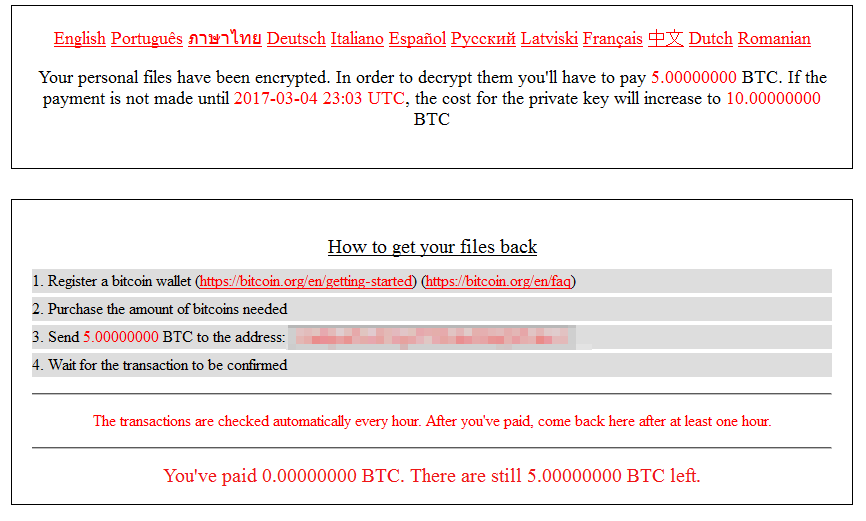
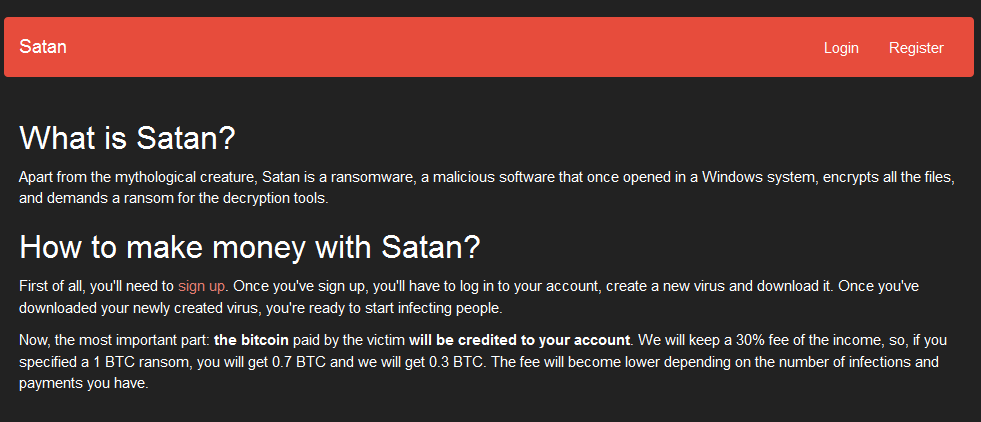
Ransomware Get Local Flavors
We’ve also noted how ransomware
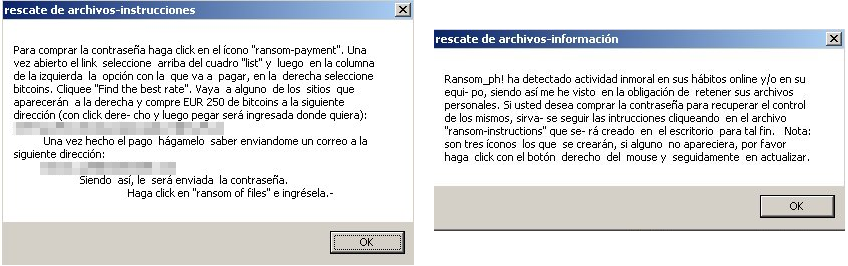
Another is Kaenlupuf, also named
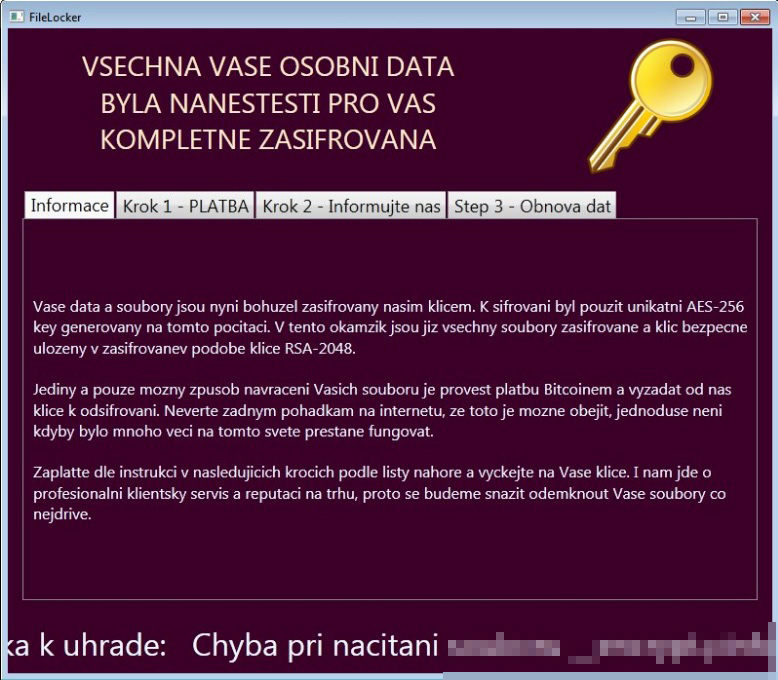
Slovak and Czech-speaking users were also targeted by Czech Ransomware (RANSOM_CZCRYPT.A). Czech Ransomware’s ransom note appears as a pop-up window
The AvastVirusinfo ransomware (Ransom_XORIST.MGW), also known as
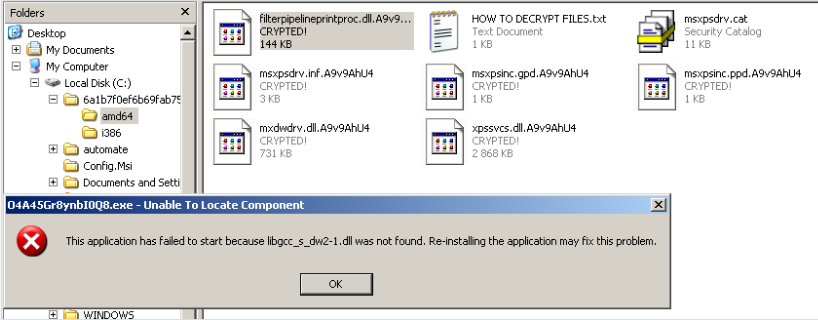
Ransomware based on open-source projects like EDA2 and Hidden Tear also emerged last week. This includes
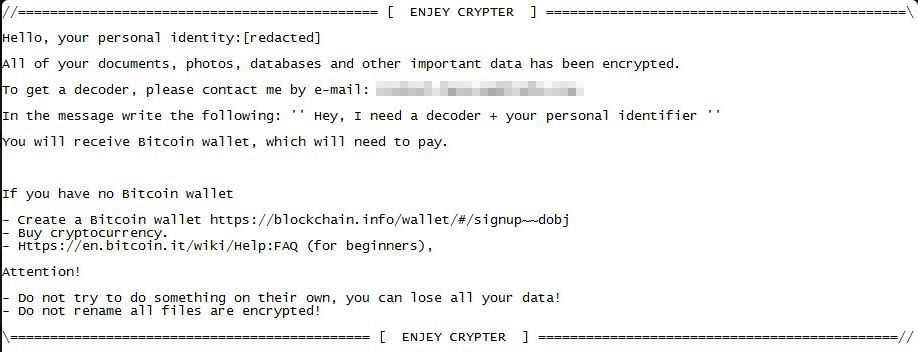
Ransomware Solutions:
Enterprises can benefit from a multi-layered, step-by-step approach in order to best mitigate the risks brought by these threats. Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security prevents ransomware from ever reaching end users. At the endpoint level, Trend Micro Smart Protection Suites deliver several capabilities like high-fidelity machine learning, behavior monitoring and application control, and vulnerability shielding that minimizes the impact of this threat. Trend Micro Deep Discovery Inspector detects and blocks ransomware on networks, while Trend Micro Deep Security™ stops ransomware from reaching enterprise servers–whether physical, virtual or in the cloud.
For small businesses, Trend Micro Worry-Free Services Advanced offers cloud-based email gateway security through Hosted Email Security. Its endpoint protection also delivers several capabilities such as behavior monitoring and real-time web reputation in order detect and block ransomware.
For home users, Trend Micro Security 10 provides strong protection against ransomware by blocking malicious websites, emails, and files associated with this threat.
Users can likewise take advantage of our free tools such as the Trend Micro Lock Screen Ransomware Tool, which is designed to detect and remove screen-locker ransomware; as well as Trend Micro Crypto-Ransomware File Decryptor Tool, which can decrypt certain variants of crypto-ransomware without paying the ransom or the use of the decryption key.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One