Ransomware Recap: qKG, a WannaCry Copycat, and more Hidden Tear-based Ransomware
qKG
qKG (detected by Trend Micro as RANSOM_CRYPTOQKG.A) is a ransomware variant that is notable for being implemented entirely via Visual Basic for Applications (VBA) macros—one of the few file-encrypters to do so.
Analysis of qKG samples shows that when a user enables the macros, the malicious macro is added to the normal.dot template of Microsoft Word. This means that, when a fresh MS Word document is opened, the modified normal.dot template with the malicious code gets loaded and executed instead.
For uninfected documents, normal operations will seemingly occur at first. However, qkG will encrypt the file’s contents once the file is closed. It will then show a message with an email and Bitcoin address, as well as the encrypted content.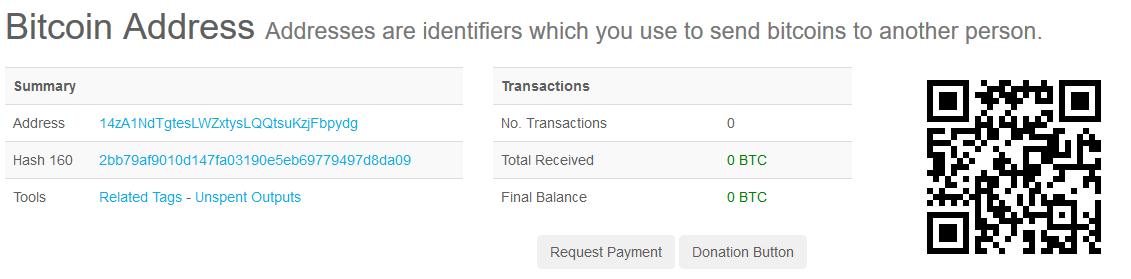
Figure 1: A screenshot of qKG’s transactions as of November 17, 2017
The initial qkG samples reveal that it is still a proof of concept (PoC) rather than an actual active malware.
Scarab
A ransomware called Scarab (detected by Trend Micro as RANSOM_SCARAB.C), which was first spotted in the wild back in June, was found being used in a new spam campaign that uses the Necurs botnet.
The attack involves an email typically coming from a printer brand, with an attachment that seems to be a scanned image.
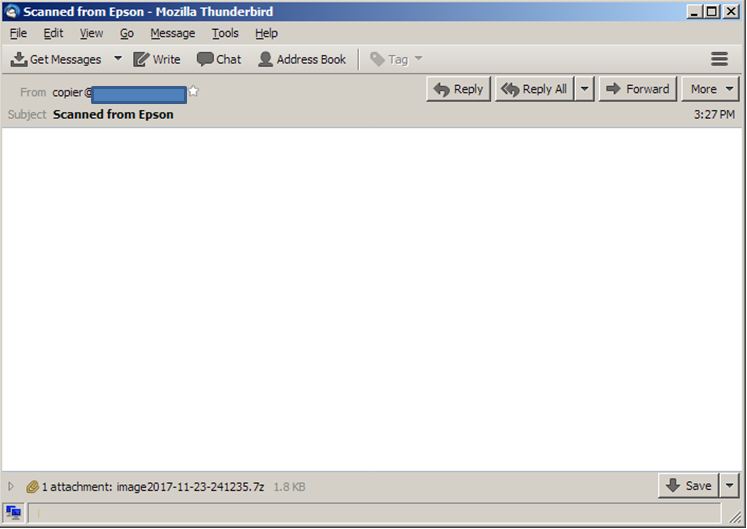
Figure 2: Sample email used in the Scarab ransomware campaign
However, this attachment is actually a 7-Zip archive containing a Visual Basic script. When clicked, the script will download and run an EXE file, which is the actual ransomware.
Once Scarab is executed, it will encrypt files without changing the original file names. However, it will append each file's name with the .scarab extension. It then drops a ransom note named labeled as "IF YOU WANT TO GET ALL YOUR FILES BACK, PLEASE READ THIS.TXT" on the user’s system. The actual ransom amount is not stated, but the ransom note mentions that the amount varies depending on how soon the user contacts the attacker.
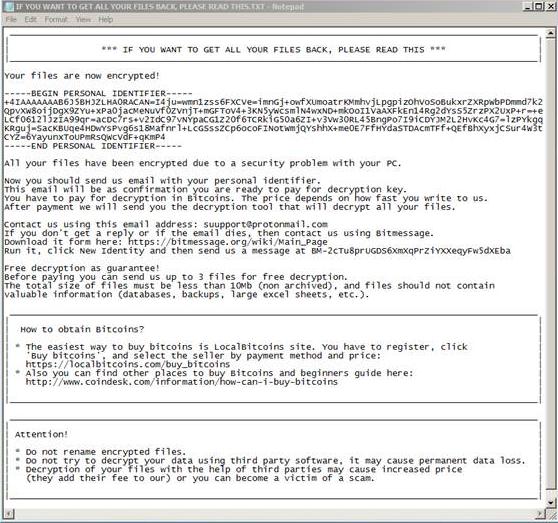
Figure 2: Scarab ransom note
WannaDie
Since the emergence of WannaCry as one of the year's most notable ransomware, there have been no shortage of “copycat” ransomware trying to profit from its infamy.
WannaDie (Detected by Trend Micro as RANSOM_WNDIE.A) is a recent Russia-based ransomware that spreads via spam emails containing a malicious file labeled wndi.exe. Once the executable is clicked, the malware is dropped into the victim’s system, encrypting files with the .wndi affix using AES encryption.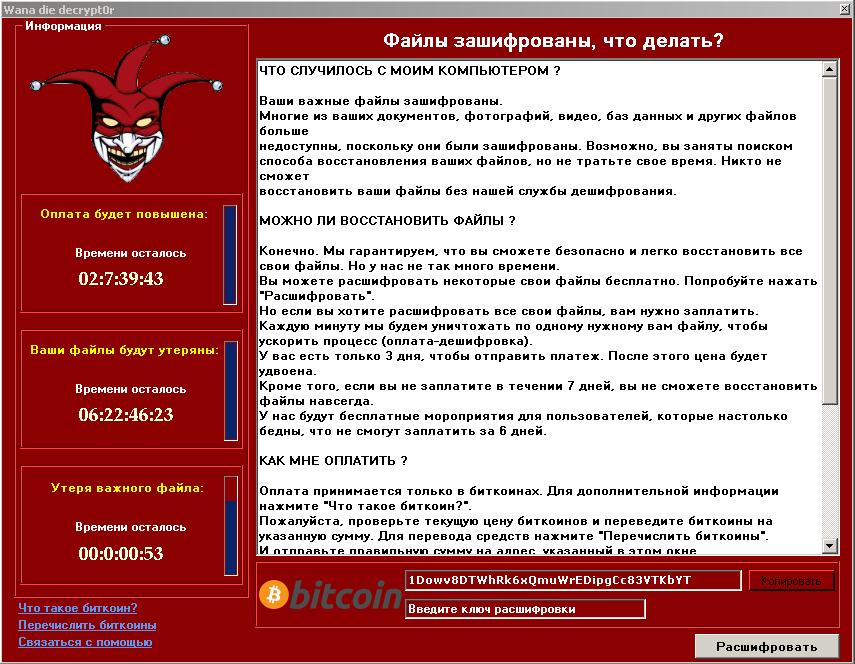
Figure 2: WannaDie’s ransom note
WannaDie’s ransom note looks like a modified version of WannaCry. The text itself is simply copied from WannaCry’s ransom note, translated in Russian.
Katafrack
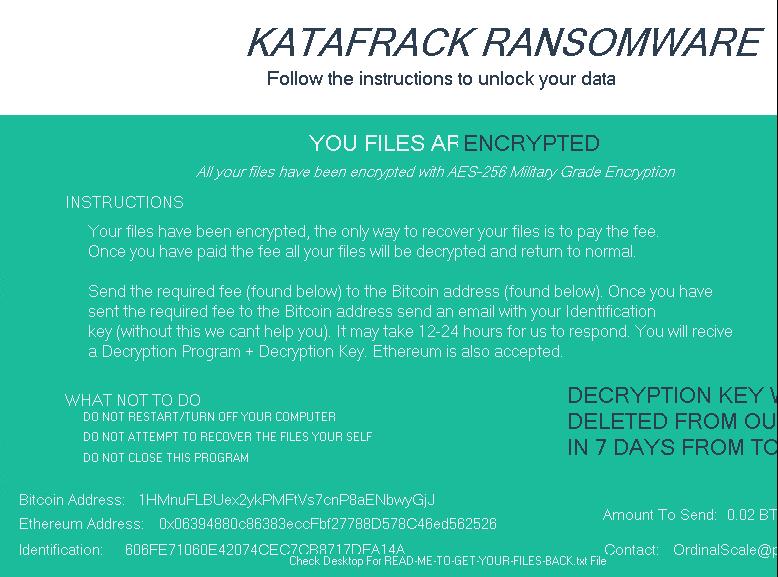
Katafrack (Detected by TREND MICRO as RANSOM_KATAFRACK.A) is another in a long line of ransomware variants based on Hidden Tear, created using Hidden Tear’s ransomware builder.
Like many other ransomware variants, Katafrack is distributed via spam emails as well as macro-enabled text files. Once it enters a user’s system, it will apply a personal cipher to the user’s data to ensure that decryption will need to be performed first.
It will drop a ransom note, as well as lock the user’s screen using the image below:
Trend Micro Ransomware Solutions
Enterprises can benefit from a multi-layered, step-by-step approach in order to best mitigate the risks brought by these threats. Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security prevent ransomware from ever reaching end users.
At the endpoint level, Trend Micro Smart Protection Suites deliver several capabilities like high-fidelity machine learning, behavior monitoring and application control, and vulnerability shielding that minimize the impact of this threat. Trend Micro Deep Discovery Inspector detects and blocks ransomware on networks, while Trend Micro Deep Security™ stops ransomware from reaching enterprise servers–whether physical, virtual or in the cloud.
In addition, Trend Micro XGen™ security provides a cross-generational blend of threat defense techniques against a full range of threats for data centers, cloud environments, networks, and endpoints. Smart, optimized, and connected, XGen™ powers Trend Micro’s suite of security solutions: Hybrid Cloud Security, User Protection, and Network Defense.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- The State of Criminal AI: Market Consolidation and Operational Reality
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One