Ransomware Recap: Petya Ransomware Outbreak Shakes Europe
 A Petya ransomware variant (detected by Trend Micro as RANSOM_PETYA.SMA) is spreading across Europe, successfully infecting—and affecting—a number of businesses, government departments, and utility providers. It's success can be attributed to its use of the PsExec tool and Windows Management Information Command-line as infection vectors, along with the EternalBlue exploit—previously used by the WannaCry ransomware and fileless ransomware UIWIX—as a second option. This presents a number of possibilities since the Microsoft tools can be used to carry out actions on other computers—if an infected device has administrator access, then the ransomware could spread to computers connected to the same network.
A Petya ransomware variant (detected by Trend Micro as RANSOM_PETYA.SMA) is spreading across Europe, successfully infecting—and affecting—a number of businesses, government departments, and utility providers. It's success can be attributed to its use of the PsExec tool and Windows Management Information Command-line as infection vectors, along with the EternalBlue exploit—previously used by the WannaCry ransomware and fileless ransomware UIWIX—as a second option. This presents a number of possibilities since the Microsoft tools can be used to carry out actions on other computers—if an infected device has administrator access, then the ransomware could spread to computers connected to the same network.
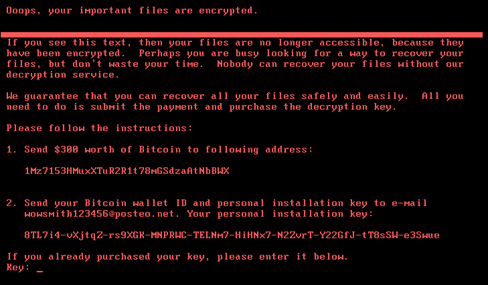
Figure 1. Petya ransom note
Users and organizations are advised to perform the following mitigation steps immediately in order to prevent and avoid infection:
- Apply Microsoft's security patch MS17-010
- Disable TCP port 445
- Restrict accounts with administrator group access
Mobile ransomware variants resurface
Apart from Petya, even mobile ransomware seems to be taking notes from WannaCry. Early this month, a new variant of SLocker (detected by Trend Micro as ANDROIDOS_SLOCKER.OPST) surfaced mimicking the WannaCry interface. SLocker is an older malware widely regarded as the precursor of Android mobile ransomware, but has been quite active these past few months. It is notable for being one of the few mobile families that actually encrypts files and is not simply a screenlocker.
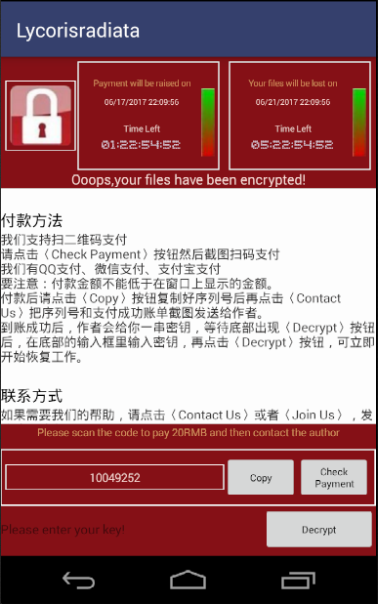
Figure 2. SLocker copying the WannaCry GUI
Luckily, this variant's distribution was limited and its life was cut short by the publishing of decryption tools soon after the detection and the arrest of its suspected author in China.
Koler (detected by Trend Micro as ANDROIDOS_LOCKER.AXBO) is another mobile ransomware that surfaced this week. This particular ransomware uses targeted ads and impersonates a popular porn app to get users to download it.
Once installation is in progress, the app asks users for permissions to finish installing—this just grants admin rights to the ransomware. It then installs an FBI screenlocker and tries to intimidate the victim with a law enforcement scare tactic.
Other ransomware developments
One more ransomware detected this week is RANSOM_CRYPAYSAVE, which is an MSIL-compiled variant that is still in-development. The authors ask for payment using PaySafeCard, which is a service that allows for more secure online payments, and is a much more convenient mode of payment than Bitcoin.
Another ransomware that tries to stand out is GPAA (detected by Trend Micro as RANSOM_GPAA) which capitalizes on the Cerber name by using a .cerber6 extension on affected files to scare victims. This ransomware poses as the Global Poverty Aid Agency (GPAA) and tries to ask victims for Bitcoin donations before reverting back to typical ransomware behavior and demanding payment in exchange for decryption.
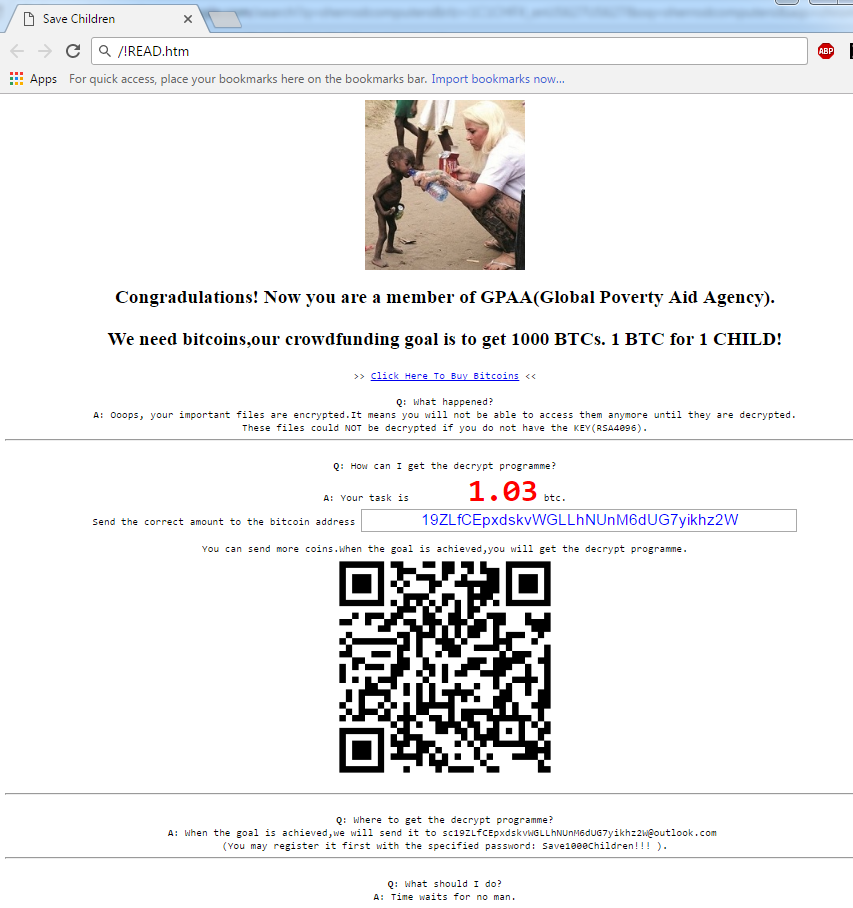
Figure 3. GPAA impersonating a charity
As this week surprises us with yet another major ransomware outbreak, users are reminded to always stay vigilant and be mindful of the patches sent out by vendors for their products. Comprehensive and effective solutions are also necessary to protect against this evolving and growing threat.
Ransomware Solutions
Enterprises can benefit from a multi-layered, step-by-step approach in order to best mitigate the risks brought by these threats. Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security prevents ransomware from ever reaching end users. At the endpoint level, Trend Micro Smart Protection Suites deliver several capabilities like high-fidelity machine learning, behavior monitoring and application control, and vulnerability shielding that minimizes the impact of this threat. Trend Micro Deep Discovery Inspector detects and blocks ransomware on networks, while Trend Micro Deep Security™ stops ransomware from reaching enterprise servers—whether physical, virtual, or in the cloud.
For small businesses, Trend Micro Worry-Free Services Advanced offers cloud-based email gateway security through Hosted Email Security. Its endpoint protection also delivers several capabilities such as behavior monitoring and real-time web reputation in order detect and block ransomware.
For home users, Trend Micro Security 10 provides strong protection against ransomware by blocking malicious websites, emails, and files associated with this threat.
Users can likewise take advantage of our free tools such as the Trend Micro Lock Screen Ransomware Tool, which is designed to detect and remove screen-locker ransomware; as well as Trend Micro Crypto-Ransomware File Decryptor Tool, which can decrypt certain variants of crypto-ransomware without paying the ransom or the use of the decryption key.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One