Ransomware Recap: Nov. 21- Dec. 2, 2016
 When it comes to ransomware sightings in the past two weeks, one of the most talked about incidents involve an identified ransomware attack reportedly impacting more than 2,000 of the almost 9,000 machines connected to the San Francisco Municipal Transportation Agency (SFMTA) network. This, in turn, has caused a system disruption that forced the agency to allow passengers to ride for free. It was later shared that the metro subway station's ticketing machines and fare gates were turned off to avoid inconveniencing the public.
When it comes to ransomware sightings in the past two weeks, one of the most talked about incidents involve an identified ransomware attack reportedly impacting more than 2,000 of the almost 9,000 machines connected to the San Francisco Municipal Transportation Agency (SFMTA) network. This, in turn, has caused a system disruption that forced the agency to allow passengers to ride for free. It was later shared that the metro subway station's ticketing machines and fare gates were turned off to avoid inconveniencing the public.
SFMTA representative Kristen Holland, in a statement released on November 28, shared that approximately 900 machines were primarily affected by the attack, contrary to earlier reports, and highlighted that no data was accessed from any of the agency’s servers. The statement was contrary to the attackers' threat that 30gb-worth of data was exfiltrated and will be sold in the Deep Web should the ransom demand of 100 bitcoins, or US$ 73,000, be left unpaid. Further, the cybercriminals behind the attack offered to decrypt one machine for 1 bitcoin, in an attempt to convince the SFMTA to pay the ransom.
SFMTA joins the lineup of organizations whose operations have been disrupted by a successful ransomware attack. In a blog entry, Trend Micro researchers confirmed that the ransomware involved was an iteration or evolved variant of HDDCryptor, a ransomare family that was discovered in September 2016. Samples of the ransomware have been analyzed, revealing subtle updates since its initial sighting.
As with other versions of HDDCryptor, the attack on SFMTA was done using tools necessary to enable full disk encryption, including data from shared network drives. Based on their analysis of the incident, Stephen Hilt and Fernando Merces believe that this particular attack is more targeted compared to those that involve exploit kits or automated installers. Instead, admin credentials may have been used to schedule a job that would operate on all the affected devices.
A closer look at the ransomware showed how the developers of the malware are constantly improving their codes by adding features like anti-sandbox and anti-debugging features, string encoding, and simple resource encryption to circumvent AV detection technologies. It is also interesting to note that no researcher has been able to attribute HDDCryptor executables to any known phishing campaigns. This means that the actors behind the attack may have had prior access to the SFMTA systems, allowing them to manually execute the ransomware.
Apart from HDDCryptor, other earlier discovered ransomware families continue to make its presence felt. In our last recap, Cerber’s reign as one of the more prominent ransomware families of late was highlighted with the continuous emergence of updates that add evolved capabilities and improved attack tactics.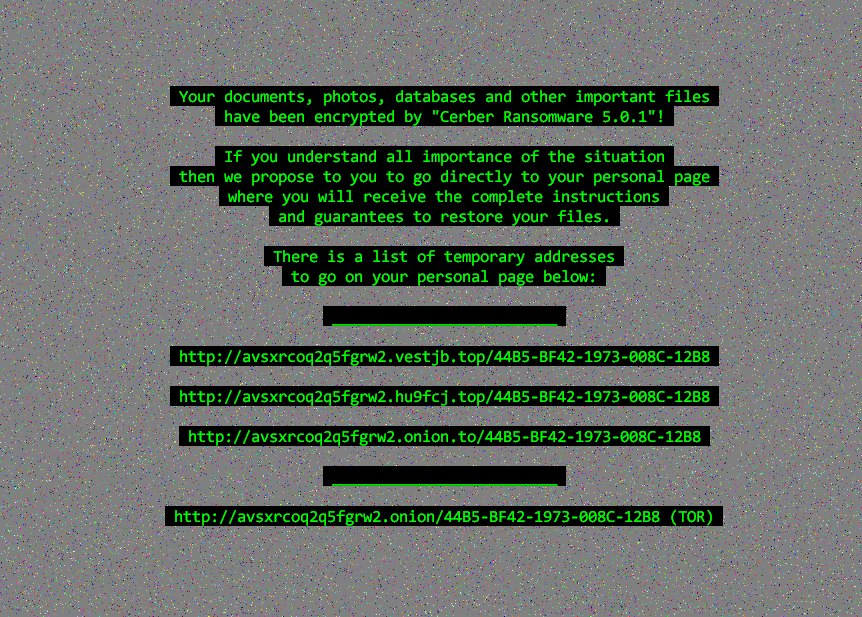
Over the past two weeks, Cerber's surge continues with the release of yet another variant, version 5.0, shortly followed by an updated version, 5.0.1 (detected by Trend Micro as RANSOM_CERBER.AUSJB). These updates reportedly incorporated minor changes to its code to make its main routine shorter than it previous versions. It also checks information of the targeted machine, like available memory and used disk space, before communicating with its servers. Previous versions simply flagged this type of information.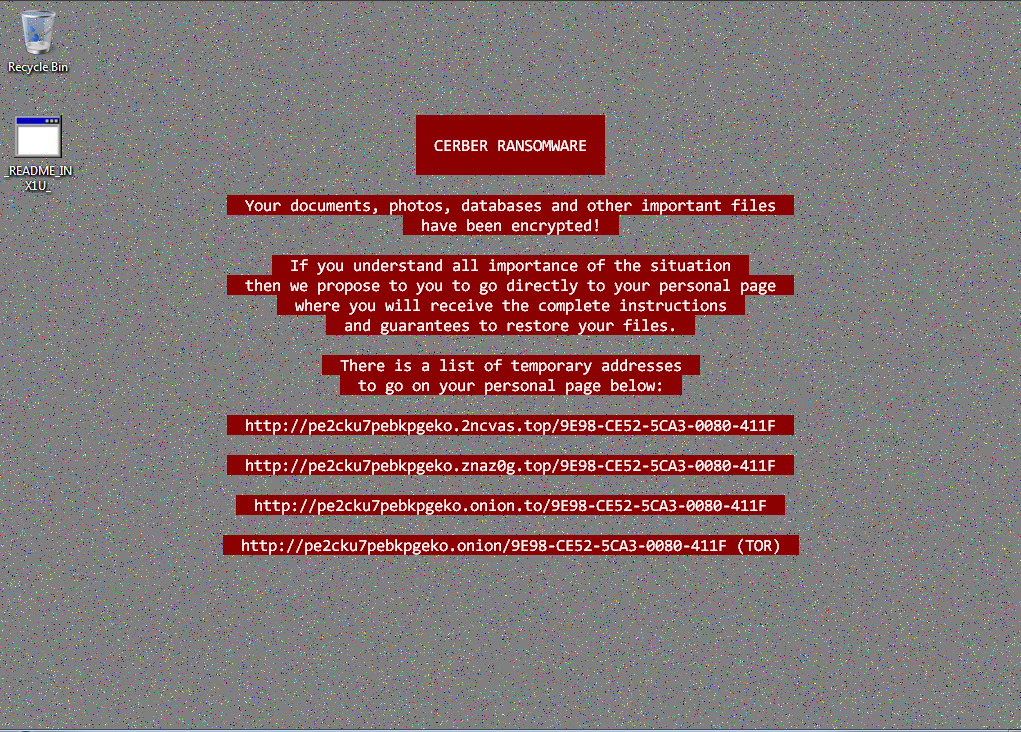
Not long after, December opened with a new version of Cerber (detected by Trend Micro as RANSOM_CERBER.AUSKM). Unlike previous versions, it shows a tweaked version of the ransom note, without indicating its version number. Interestingly, upon successful encryption, it adds four randomly-generated alpha-numeric characters to the extension name to the encrypted file. It also is reminiscent of the first sightings of Cerber, with the inclusion of an audio message announcing compromise. It demands a ransom of almost $500 for a decryption key.
Here are other notable ransomware stories in the past two weeks:
Locky
Over the past two weeks, a Locky variant (detected by Trend Micro as RANSOM_LOCKY.AJ) was seen adding a .aesir extension to the filenames of encrypted files. The attack uses a spam email campaign that involves messages masquerading as a complaint from the would-be victim’s ISP, notifying that spam has been coming from his/her machine. This then contains a zip attachment that contains a JS file that, when opened, will download and execute the Locky ransomware. Other samples observed by Trend Micro researchers involve traditional tactics of spam emails containing a fake invoice or spoofed order dispatch notification from legitimate brands.
Shortly after its discovery, samples of another Locky variant (detected by Trend Micro as RANSOM_LOCKY.Z) surfaced, this time using a .zzzzz extension appended to the filenames of its encrypted files. With routines similar to previously-seen Locky variants, this has been observed to originate from spam emails under the guise of false order receipts supposedly made by the victim. Upon execution and successful encryption, the ransom note gives specific instructions on how to settle the ransom.
HOLLYCRYPT
Another variant based on open-source ransomware Hidden Tear surfaced around the end of November. Called Hollycrypt (detected by Trend Micro as RANSOM_HIDDENTEARHOLLY.A), the ransomware hides under the guise of a Facebook Automation Tool, which will then lead to the download of a malicious PDF file. Upon successful encryption, it appends the .Hollycrypt extension to the file name of its encrypted file. Interestingly, the ransom note asks for money in the form of bitcoins or Vodka. After which, the said “antidote” will then be sent via email.
CRYPTOWIRE and LOMIX
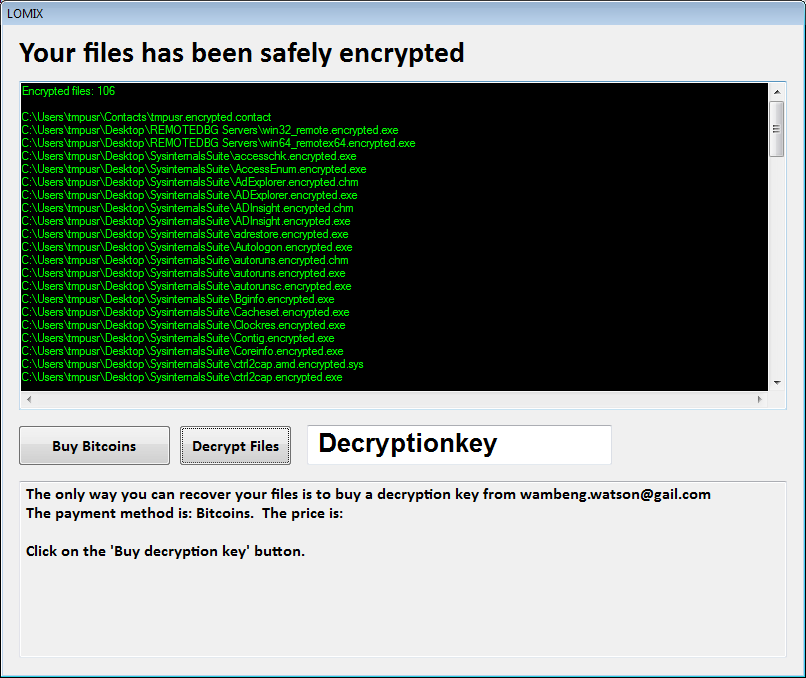
Cryptowire (detected by Trend Micro as RANSOM_CRYPTOWIRE) emerged at the tail-end of November, inserting the .encrypted string to the encrypted file. This means that an image file named image.jpg, when encrypted, becomes image.encrypted.jpg. Once encryption gets fully carried out, this particular variant leaves a locked screen that details a ransom of 0.29 bitcoin, or over $200. Not long after, LoMix, a variant of CryptoWire, emerged, featuring similar routines. This variant demands a ransom of over 0.60 bitcoins, or an amount reaching $500.
VINDOWSLOCKER
After its encryption routine, it appends a .vindows extension to the file name of the encrypted file. A ransom note will then be displayed, showing a contact number that leads the victim to dedicated operators. When the bait has been taken and the owner of the infected system contacts the given number, the operators will then perform a remote desktop session. According to reports, the operators will swiftly paste a shortened URL hosted on JotForm onto the address bar to mine the target’s personal data.
The entry of the new ransomware families and updates of variants released in the past mean one thing—ransomware works for cybercriminals. In order to defend against ransomware, a multi-layered approach is key to shutting out the malware from all possible gateways. IT admins in organizations should empower the workforce with necessary education to keep employees abreast of attack tactics. On the other hand, when infected, a solid back-up of important files can mitigate damages brought by a successful ransomware infection.
Ransomware solutions:
Trend Micro offers different solutions to protect enterprises, small businesses, and home users to help minimize the risk of getting infected by ransomware:
Enterprises can benefit from a multi-layered, step-by-step approach in order to best mitigate the risks brought by these threats. Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security prevents ransomware from ever reaching end users. At the endpoint level, Trend Micro Smart Protection Suites deliver several capabilities like high-fidelity machine learning, behavior monitoring and application control, and vulnerability shielding that minimizes the impact of this threat. Trend Micro Deep Discovery Inspector detects and blocks ransomware on networks, while Trend Micro Deep Security™ stops ransomware from reaching enterprise servers–whether physical, virtual or in the cloud.
For small businesses, Trend Micro Worry-Free Services Advanced offers cloud-based email gateway security through Hosted Email Security. Its endpoint protection also delivers several capabilities such as behavior monitoring and real-time web reputation in order detect and block ransomware.
For home users, Trend Micro Security 10 provides strong protection against ransomware by blocking malicious websites, emails, and files associated with this threat.
Users can likewise take advantage of our free tools such as the Trend Micro Lock Screen Ransomware Tool, which is designed to detect and remove screen-locker ransomware; as well as Trend Micro Crypto-Ransomware File Decryptor Tool, which can decrypt certain variants of crypto-ransomware without paying the ransom or the use of the decryption key.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One