Ransomware Recap: A Tale of Two “Lockers”
 One of the aspects of ransomware that makes them so effective is the psychological angle: encrypting files in a computer or device plays on the victims' fears – specifically, would they lose their files if they did not pay?
One of the aspects of ransomware that makes them so effective is the psychological angle: encrypting files in a computer or device plays on the victims' fears – specifically, would they lose their files if they did not pay?
A new mobile ransomware called LeakerLocker (Detected by Trend Micro as ANDROIDOS_LEAKERLOCKER.HRX) takes this psychological fear one step further. It does not threaten to encrypt or delete files. Instead, it gathers personal information and threatens to expose this info to the user's contact list.
LeakerLocker arrives on an Android device via Google Play. Three applications (which have since been taken down by Google) in particular were found carrying the mobile ransomware: Wallpapers Blur HD, Booster & Cleaner Pro, and Calls Recorder.
Figure 1: Calls Recorder app
Analysis of the Calls Recorder app shows that LeakerLocker will begin to gather personal information from the device as soon as it's downloaded. The type of data gathered includes contacts, phone calls and photographs, which it then threatens to expose, as seen from the ransom note taken from another application carrying the ransomware: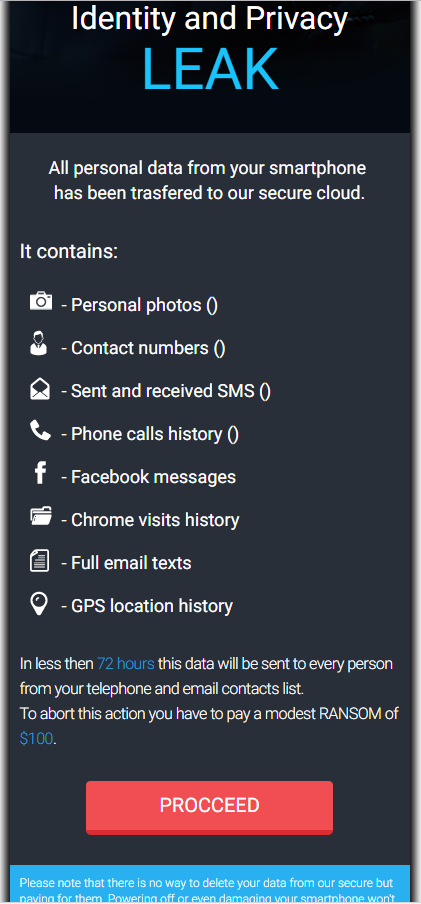
Figure 2: LeakerLocker ransom screen
Analysis of the LeakerLocker code reveals that it isn't capable of actually exposing the information, but the simple threat of having potentially sensitive information exposed could be enough to scare a victim into paying the ransom.
In addition to LeakerLocker, here are the other notable ransomware news from this week:
SLocker
While the world has had enough of Petya and its variants, it seems that cybercriminals are still trying to ride the ransomware’s popularity. In July, the veteran ransomware known as SLockerwas found copying Petya's Graphical User Interface (GUI). Recently, SLocker popped up again with a new variant (Detected by Trend Micro as ANDROIDOS_SLOCKER.OPSCB) combining the use of the China-based social networking website QQ with its screen locking and file encrypting capabilities.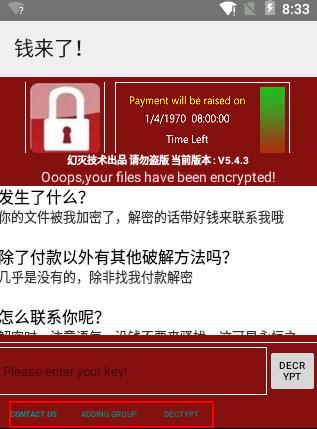
Figure 3: SLocker ransom note
This variant features a few changes since its first iteration, particularly in how it was created. Notably, it uses the Android integrated development environment (AIDE), which makes it easier for potential attackers to create their own SLocker variants. It does come with a few kinks, and is rather incompetent when it comes to actually encrypting files – including unnecessary file types like temp, cache, and system logs.
However, it combines file encryption with screen locking features, making it doubly troublesome for its targets.
Cerber
While the Cerber ransomware has gone through so many evolutions that it is hardly surprising to see new variants popping up, ransomware with cryptocurrency-stealing features are quite unusual. That relatively uncommon feature is what makes this new Cerber variant (Detected by Trend Micro as RANSOM_HPCERBER.SMALY5A) quite notable.
Figure 4: Email containing the Cerber ransomware
The new variant specifically steals cryptocurrencies by targeting three kinds of wallets—Bitcoin’s Core wallet and two third-party wallets from Electrum and Multibit—while trying to retrieve password information via files and internet browsers. In addition, Cerber will also delete the actual wallet files once the information is stolen.
While this behavior in itself is unlikely to cause wide scale concerns due to the relatively small number of Bitcoin users, it's still a significant threat. It's also a sign that ransomware developers are starting to look for more ways to profit, regardless if the victim chooses to avoid paying the ransom.
Demon
Although the Demon ransomware (Detected by Trend Micro as RANSOM_DEMON family) is relatively unremarkable in terms of payload—it doesn't actually encrypt any files—it’s notable because of its unusual ransom note, which is similar to WannaCry’s: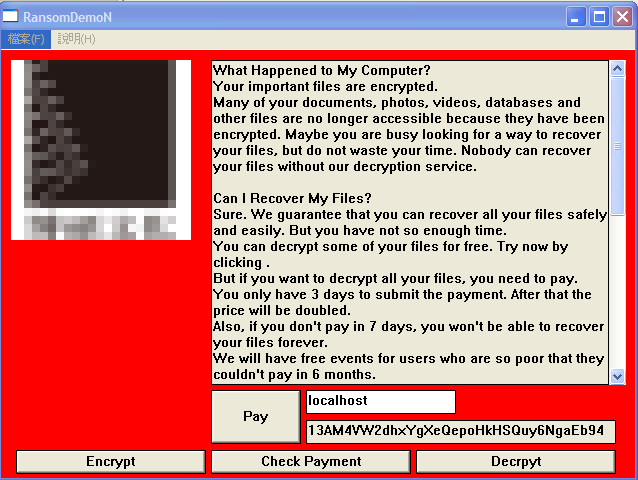
Figure 5: Demon ransom note
Perhaps even stranger is the “encrypt” button located at the bottom left portion of the ransom note. Why this button exists is not clear, as obviously, no user will want to encrypt their own files. The Chinese characters found in the upper left portion of the note (blurred in the above photograph) is actually the logo of an online bookstore, which adds to the amateurish quality of this ransomware.
It all points to an unsophisticated attempt at tricking users through bluffing without having routines that do any damage.
Mobile ransomware highlight this week’s recap. Plenty of users are still unaware that ransomware can also infect mobile devices. Users should always double check any application they download, even if they come from reliable sources such as Google Play. Reading app reviews can help users distinguish legitimate applications from suspicious and potentially malicious ones.
Ransomware Solutions
End users and enterprises can also benefit from multilayered mobile security solutions such as Trend Micro™ Mobile Security for Android™ (available on Google Play), and Trend Micro™ Mobile Security for Apple devices (available on the App Store). Trend Micro™ Mobile Security for Enterprise provide device, compliance and application management, data protection, and configuration provisioning, as well as protect devices from attacks that leverage vulnerabilities, preventing unauthorized access to apps, as well as detecting and blocking malware and fraudulent websites
Enterprises can also benefit from a multi-layered, step-by-step approach in order to best mitigate the risks brought by these threats. Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security prevent ransomware from ever reaching end users. At the endpoint level, Trend Micro Smart Protection Suites deliver several capabilities like high-fidelity machine learning, behavior monitoring and application control, and vulnerability shielding that minimizes the impact of this threat. Trend Micro Deep Discovery Inspector detects and blocks ransomware on networks, while Trend Micro Deep Security™ stops ransomware from reaching enterprise servers–whether physical, virtual or in the cloud.
For small businesses, Trend Micro Worry-Free Services Advanced offers cloud-based email gateway security through Hosted Email Security. Its endpoint protection also delivers several capabilities such as behavior monitoring and real-time web reputation in order detect and block ransomware.
For home users, Trend Micro Security 10 provides strong protection against ransomware by blocking malicious websites, emails, and files associated with this threat. Users can likewise take advantage of our free tools such as the Trend Micro Lock Screen Ransomware Tool, which is designed to detect and remove screen-locker ransomware; as well as Trend Micro Crypto-Ransomware File Decryptor Tool, which can decrypt certain variants of crypto-ransomware without paying the ransom or the use of the decryption key.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One