Ransomware 101: What, How, and Why
 view infographic: Ransomware 101
view infographic: Ransomware 101
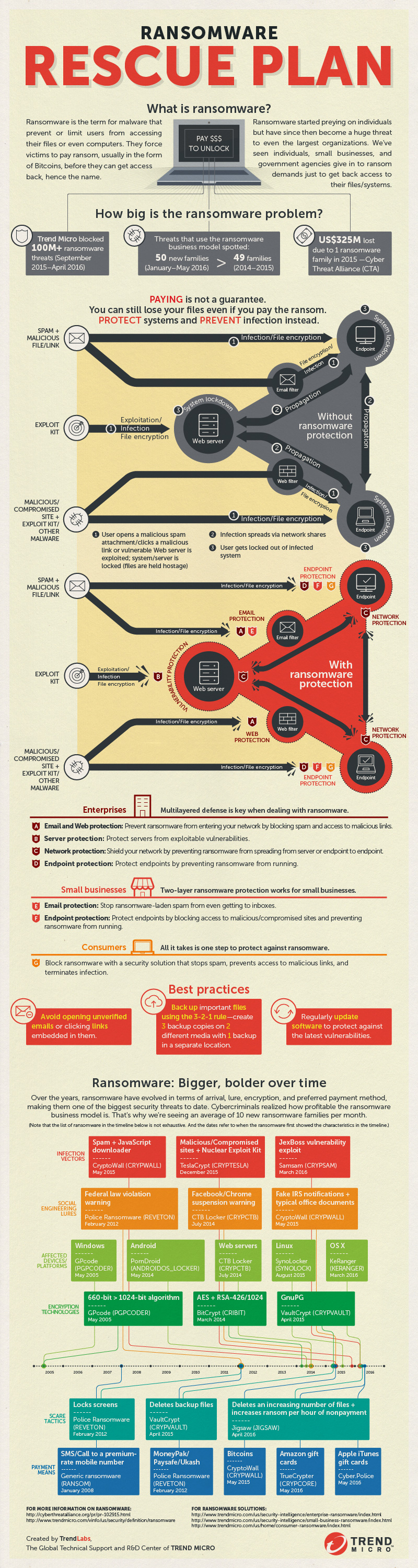
What makes ransomware so effective? One reason—fear. Just like any traditional extortion op, ransomware operations succeed because they capitalize on fear, which ultimately forces victims to do something irrational such as paying cybercriminals. Fear of losing your job because you lost important documents to ransomware can be crippling. Getting locked out of your system or never being able to open your files again is a scary thought. Possibly being indicted for potentially embarrassing browsing habits (such as watching adult or inappropriate videos) or unwanted public exposure can compel you to pay. And from what we’ve seen so far, fear-mongering works, as proven by the US$325 million paid by individuals and businesses worldwide to a single ransomware variant called CryptoWall in 2015.
Of course, the onus doesn’t completely fall on users. Ransomware has gone through some very drastic changes through the years. Every newly discovered variant seems to have improved, sporting more sophisticated routines that have made them more dangerous even to the informed. Ransomware has evolved a lot since its early days—when the malware type used federal law violation warnings (Police Ransomware/REVETON) as a scare tactic—to modern crypto-ransomware that can lock users out of their systems. Different ransomware families have also adopted a variety of new tactics to compel users to pay as soon as possible; Jigsaw, in particular, threatens to delete an increasing number of files after every hour of nonpayment.
Cybercriminals have also constantly improved ransomware’s hostage-taking tactics with the use of increasingly sophisticated encryption technologies. In 2013, ransomware strains led by CryptoLocker began encrypting files, holding them hostage until victims paid the ransom. It was proven to be an effective tactic, and other ransomware families followed suit. Since then, a number of businesses and large organizations around the world have been hit, as police departments, small businesses, schools, and hospitals joined the growing list of ransomware victims.
The threat is still growing. 50 new ransomware families have already been seen within the first five months of 2016 alone, which is more than the numbers seen in 2014 and 2015 combined.
[RELATED: Ransomware Rising: the Ransomware Numbers in 2016]
The ransomware threat is as real as it gets, but paying shouldn’t be an option, as paying the ransom does not guarantee that victims regain access to their locked files. Case in point, the Kansas Heart Hospital paid the ransom to regain access to their locked systems, but instead of getting a decrypt key, the hospital was extorted for more money.

Enterprises can employ a multilayered defense strategy to deal with ransomware.Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security prevent ransomware from reaching end users. At the endpoint level, Trend Micro Smart Protection Suites features behavior monitoring and application control, as well as vulnerability shielding to minimize the risk of getting infected by ransomware threats. Trend Micro Deep Discovery Inspector detects and blocks ransomware on networks, while Trend Micro Deep Security™ stops ransomware from reaching enterprise servers—whether physical, virtual, or in the cloud.
Two-layer ransomware protection, meanwhile, works for small and medium-sized businesses (SMBs) Trend Micro Worry-Free Services Advanced offers cloud-based email gateway security through Hosted Email Security. Its endpoint protection also features behavior monitoring and a real-time web reputation service that detects and blocks ransomware.
For home users, Trend Micro Security 10 provides robust protection against ransomware by blocking malicious websites, emails, and files associated with this threat.
Regardless of the user type, online best practices, such as avoiding opening unverified emails and links embedded in them, and regularly updating software and applications can reduce the risk of getting infected. Backing up files using the 3-2-1 rule can make mitigate the effects of file loss from a ransomware infection.
Finally, Trend Micro also offers free tools such as the Trend Micro Lock Screen Ransomware Tool, which is designed to detect and remove screen-locker ransomware. The Trend Micro Crypto-Ransomware File Decryptor Tool can decrypt files locked by certain variants of crypto-ransomware without paying the ransom or needing the decryption key.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- The State of Criminal AI: Market Consolidation and Operational Reality
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One