New Version of Disk-Wiping Shamoon/Disttrack Spotted: What You Need to Know
 We came across external reports that the notorious, disk-wiping worm Shamoon, also known as Disttrack, has reemerged with an updated version. We were also able to source several samples of this version of Shamoon that Trend Micro detects as Trojan.Win32.DISTTRACK.AA and Trojan.Win64.DISTTRACK.AA. While there are no obvious indications that this new version is currently in the wild, we are further analyzing the malware to verify its functions and capabilities given its destructive impact.
We came across external reports that the notorious, disk-wiping worm Shamoon, also known as Disttrack, has reemerged with an updated version. We were also able to source several samples of this version of Shamoon that Trend Micro detects as Trojan.Win32.DISTTRACK.AA and Trojan.Win64.DISTTRACK.AA. While there are no obvious indications that this new version is currently in the wild, we are further analyzing the malware to verify its functions and capabilities given its destructive impact.
Trend Micro’s XGen™ security already protects users and businesses from this disk-wiping worm using proactive techniques like behavioral analysis and high-fidelity machine learning. Here’s what users and organizations need to know about Shamoon’s latest iteration:
What is Shamoon/Disttrack?
The Shamoon or Disttrack worm is a wiper. It is known to overwrite files stored in the affected system and infects its master boot record (MBR). Its first iteration overwrites documents, pictures, videos, and music files, wipes the MBR, and replaces it with an image of a burning flag. The second version used an infamous image of a refugee.
This new version of Shamoon appears to have the same MBR-overwriting function. Unlike the previous versions that delete/replace files, this new iteration reportedly sports the capability to irreversibly encrypt files. It also seems to be missing components such as predefined credentials used for lateral movement within the network and command-and-control (C&C) communications. Our analysis is currently ongoing and will verify these as soon as updated information is available.
Is this new version of Shamoon/Disttrack in the wild?
A file containing Shamoon’s latest version was reportedly uploaded to VirusTotal from Italy. We found no indications that this new version of Shamoon is actively being distributed in the wild.
How does this new version of Shamoon/Disttrack work?
Our initial findings revealed that it resembles an old version of Shamoon but with some modifications. For example, it changed its service and file names from NtertSrv to MaintenaceSrv. This version of Shamoon affects 32- and 64-bit systems running Windows.
It still retains the capability to overwrite the infected system’s disk and could take the following names (dropped and executed in the system folder as %System%\{wiper name}):
- _tdibth.exe
- _wialx002.exe
- acpipmi2z.exe
- af0038bdax.exe
- arcx6u0.exe
- averfix2h826d_noaverir.exe
- hidirkbdmvs2.exe
- mdamx_5560.exe
- mdmgcs_8.exe
- mdmusrk1g5.exe
- megasasop.exe
- netbxndxlg2.exe
- prncaz90x.exe
- prngt6_4.exe
- prnlx00ctl.exe
- prnsv0_56.exe
- tsprint_ibv.exe
- vsmxraid.exe
- wiacnt7001.exe
Here's an overview of its attack chain:
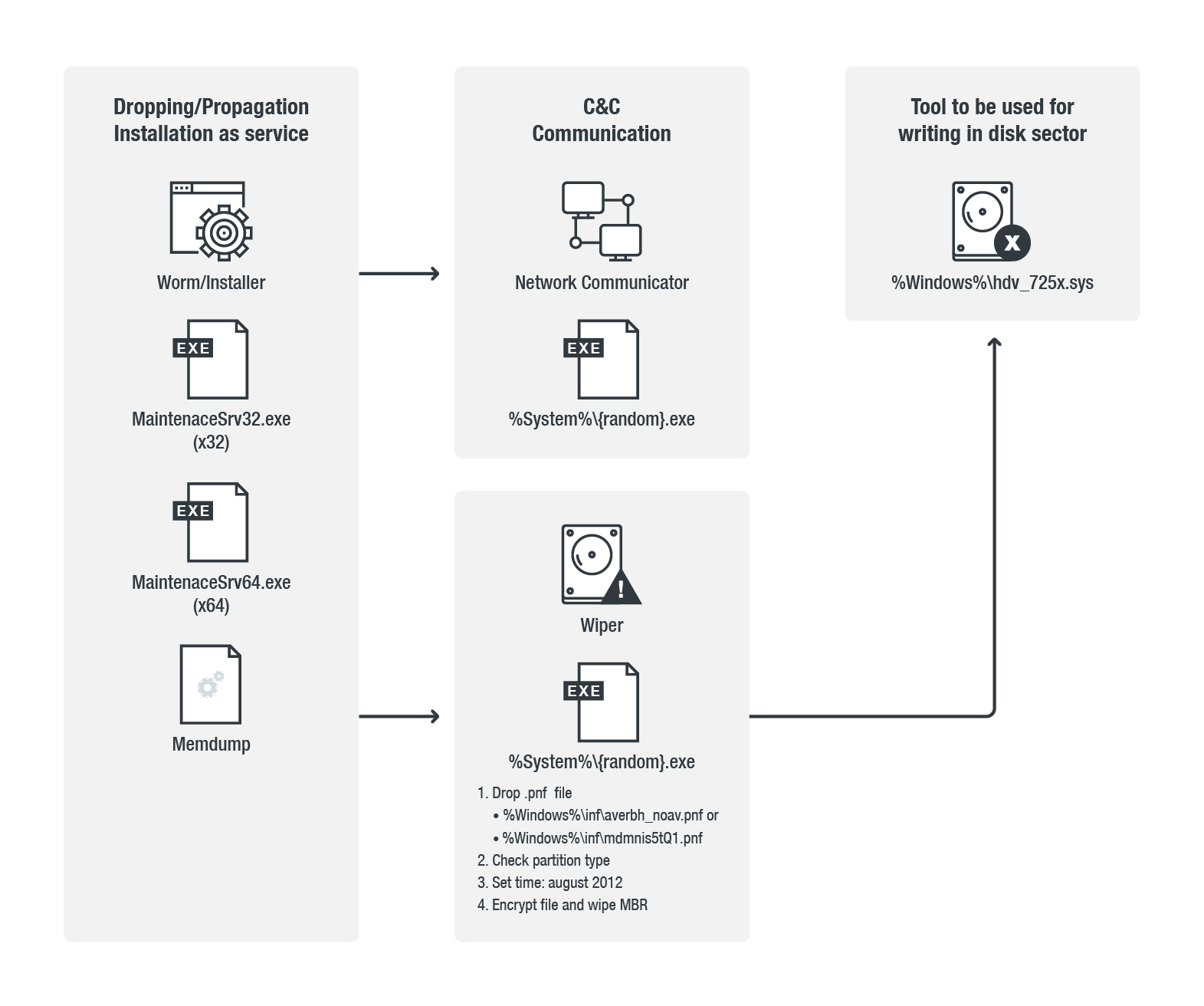
How does Shamoon/Disttrack propagate?
Shamoon spreads by dropping copies of itself in the system’s administrative shares. The Shamoon worm propagates in these shared network/administrative folders: ADMIN$, C$\WINDOWS, D$\WINDOWS, and E$\WINDOWS.
What makes Shamoon/Disttrack notable?
Shamoon was used in targeted attacks against high-profile organizations and enterprises in the Middle East, particularly those in Saudi Arabia. It’s also worth noting that Shamoon is also being discussed by hackers and members of the Middle Eastern and North African underground. It is also notorious for its sociopolitical statements that accompany the images it replaces the infected system’s MBR with.
Shamoon can render endpoints and servers connected to the targeted organization’s domain unbootable. When it resurfaced in December 2016, Shamoon added a technique that can bypass sandboxes by including a logic bomb in its code. It activates and drops its components at a certain date and time.
External news notes that the new version of Shamoon appears to have the same function. It is configured to activate on December 7, 2017 at 11:51 p.m., probably as a way to execute the malware immediately.
How do the three versions of Shamoon/Disttrack differ?
Here's an overview of how the three versions of Shamoon differ in terms of behavior:
| Behavior | Version 1* (2012) | Version 2 (2016) | Version 3* (2018) |
| Drops log file containing file path that it will overwrite | f1.inf, f2.inf, net{4 char random} | netimm173.pnf, usbvideo324.pnf | %Windows%\inf\averbh_noav.pnf or %Windows%\inf\mdmnis5tQ1.pnf (contains number of encrypted files only) |
| MBR wiping | Overwrite MBR and partition with 0x30000 bytes (uses damaged image) | Overwrite MBR and partition with 0x4e00 bytes (uses image of a refugee) |
|
| System time trigger | SetSystemTime (August 2012) — sets the date to this date | CheckSystemTime (starts November 17, 2016 – December 31, 2016) — use as trigger, not force | SetSystemTime (August 2012) — sets the date to this date |
| Installation, Copying of itself, and Autostart |
Service name: TrkSvr |
Service name: NtsSvr Display name: Microsoft Network Realtime Inspection Service Image path: %System%\ntssrvr32.exe %System%\ntssrvr64.exe |
Service name: MaintenaceSvr Display name: Maintenace Host Service Image Image path:
|
| Drop path, filename, and propagation are the same | %System%\{random file name}.exe (wiper) %System%\netinit.exe (version 1 and 2), %System%\{random file name}.exe (version 3) - Network %System%\Drivers\drdisk.sys, %Windows%\hdv_725x.sys (version 3) This worm drops copies of itself in the following shared folders: \\{IP address}\ADMIN$\system32\{random file name}.exe \\{IP address}\C$\WINDOWS\system32\{random file name}.exe \\{IP address}\D$\WINDOWS\system32\{random file name}.exe \\{IP address}\E$\WINDOWS\system32\{random file name}.exe |
||
What can be done to defend against Shamoon/Disttrack?
Users and especially businesses are recommended to enforce defense in depth in securing their online premises, which includes the following measures:
- Patch and update the system to prevent vulnerabilities from being exploited.
- Regularly back up important data to mitigate damage.
- Enforce the principle of least privilege: Disable outdated plugins or components; employ sandboxing, data categorization, and network segmentation to lessen further exposure to Shamoon’s disk-wiping and file-overwriting capabilities.
- Employ multilayered security mechanisms such as application control, which prevents unwanted or suspicious executables from running, and behavior monitoring, which blocks anomalous system modifications.
- Proactively monitor the network for any signs of lateral movement or malicious traffic by deploying firewalls, and intrusion prevention and detection systems.
Updated as of December 12, 2018, 1:42 a.m. PDT to include technical insights on the new version of Shamoon.
Updated as of December 12, 2018 6:05 p.m. PDT to include a visualization of Shamoon's attack chain.
Updated as of December 12, 2018 8:26 p.m. PDT to update the table (System time trigger and note on the first and third versions of Shamoon).
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One