New HC7 Ransomware Variant First to Accept Ethereum (ETH) as Ransom Payment
As Ethereum (ETH) continues to soar in its market price, cybercriminals are quick to jump in on new opportunities to make a profit. A new variant of the HC7 Planetary ransomware appears to be the first ransomware to accept the Ether cryptocurrency as ransom payment.
The HC7 Planetary variant is distributed via hacking into networks using remote desktop. Once the malicious actor hacks into the network, the ransomware is manually installed on all machines that can be accessed.
The ransomware, which is currently in the wild, encrypts files and appends them with a .PLANETARY extension. As seen in the ransom note below, the author demands US$700 per machine or $5,000 for all of the machines on the network.
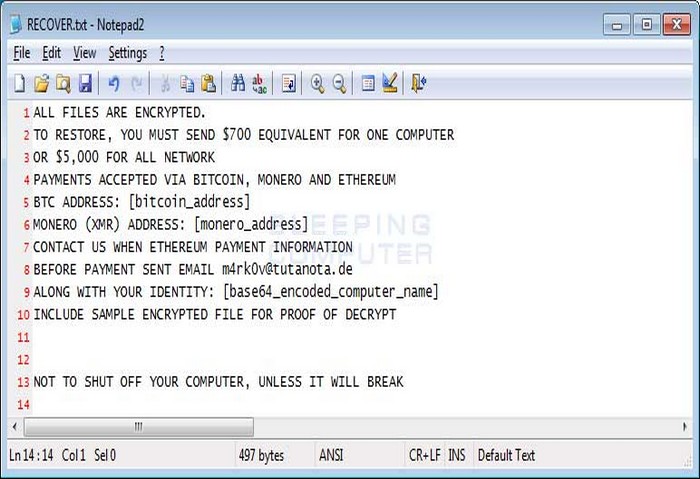 Figure 1. HC7 Planetary ransomware ransom note (via bleepingcomputer.com)
Figure 1. HC7 Planetary ransomware ransom note (via bleepingcomputer.com)
Notably, the ransomware lists Ethereum along with Bitcoin and Monero as an accepted cryptocurrency for payment. Ethereum is currently the second most valuable cryptocurrency after Bitcoin at over $1,200 per coin, and is projected to triple in value in 2018.
In December 2017, security researchers discussed how HC7-encrypted files can be decrypted by performing memory forensics on a victim's machine in order to retrieve the password used on the command line when the ransomware was installed. However, it is not clear if this method can be used to decrypt files hostaged by this new HC7 variant.
Users and enterprises can adopt these best practices to lower or eliminate the risk of ransomware infection.
Trend Micro Solutions
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One