Frequently Asked Questions: The Petya Ransomware Outbreak
 On June 27, several organizations in Europe reported ransomware infecting their systems, modifying their master boot records (MBR) and encrypting their systems’ files. The culprit: a variant of the Petya ransomware that Trend Micro detects as RANSOM_PETYA.SMA.
On June 27, several organizations in Europe reported ransomware infecting their systems, modifying their master boot records (MBR) and encrypting their systems’ files. The culprit: a variant of the Petya ransomware that Trend Micro detects as RANSOM_PETYA.SMA.
The ransomware is spreading rapidly, affecting organizations, businesses, and end users, turning into an outbreak reminiscent of the one caused by WannaCry. Some questions remain: Do they work the same? Do they both have kill switches? Do they similarly use the EternalBlue vulnerability to infect systems?
[From the Security Intelligence Blog: A technical overview of our ongoing analysis of Petya]
Is it a wiper or ransomware?
It’s both, actually. This threat manifests mainly as a ransomware given its tell-tale red flags: encryption and modification capabilities, ransom notes, and other related code artifacts.
On the other hand, this threat can also overwrite the affected system’s hard disk—and the modifications include wiping the disk. Another example of ransomware that modifies MBRs is HDDCryptor, the family that was used in an attack against the San Francisco Municipal Transport Agency.
[READ: A technical analysis of EternalBlue (MS17-010) exploit]
Is the ransomware really Petya?
Petya is an old, existing ransomware that first emerged in 2016. It’s known to overwrite the system’s Master Boot Record (MBR), locking users out of their machines with a blue screen of death (BSoD). In Petya’s case, the BSoD screen is used to show the ransom note. Known to be peddled as ransomware as a service (RaaS) in underground marketplaces, it has undergone several alterations and rehashes since it was first discovered—PetrWrap and GoldenEye, to name a few—and even joined forces with another ransomware family, Mischa. During this time, the Petya-Mischa ransomware combo featured a modular approach—Petya overwrote the MBR while Mischa encrypted the files.
This version of Petya combines these two capabilities: after successfully infecting the system, Petya modifies the victim system's MBR, after which the files are encrypted.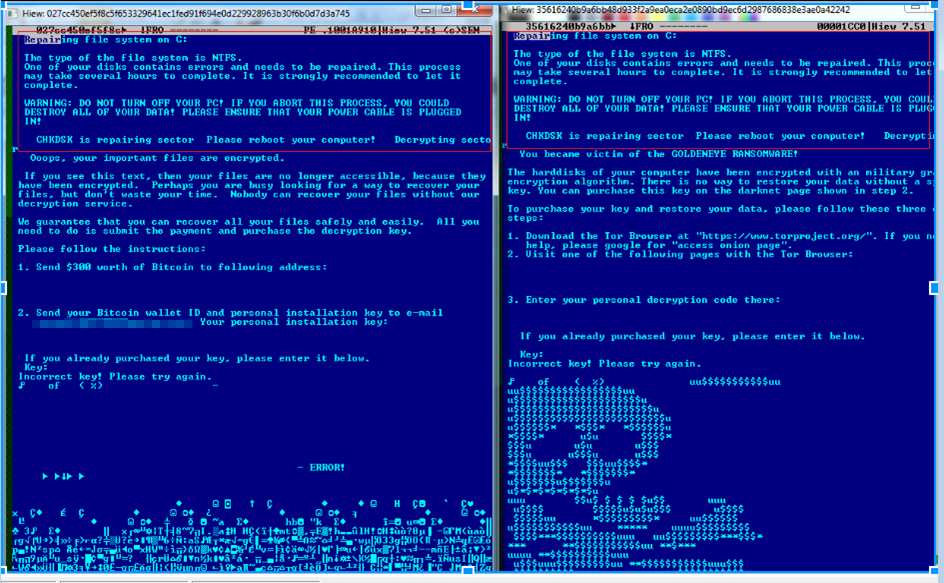
Differences in Petya (left, based on current sample) and GoldenEye’s (right) ransom notes shown after system reboot
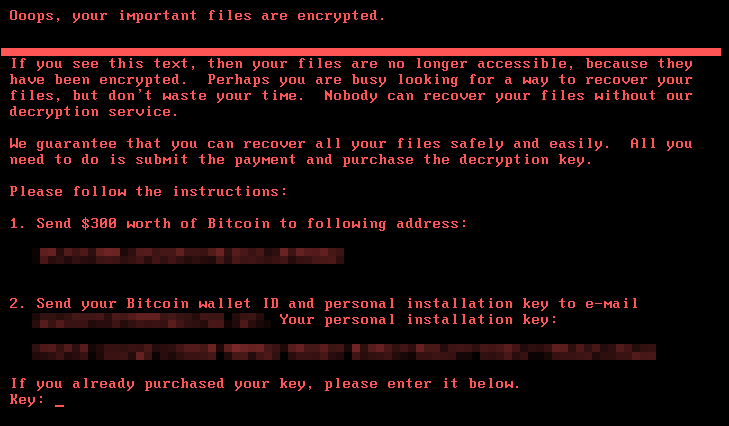
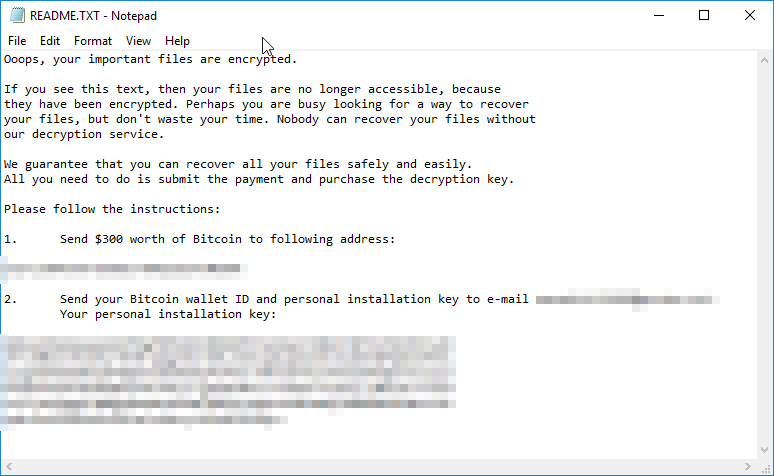
Ransom notes of Petya’s latest iteration
[READ: How GoldenEye ransomware targeted German businesses and end users]
Do Petya and WannaCry both use EternalBlue?
Yes. Both WannaCry and Petya exploit EternalBlue (MS17-010), a vulnerability in Windows’ Server Message Block, to infect endpoints and encrypt their files.
However, this Petya variant has other attack vectors that can be run independently from each other. Petya uses a modified version of PsExec, a legitimate system administration utility, to install the ransomware. If unsuccessful, it abuses Windows Management Instrumentation Command-line (WMIC), another legitimate scripting interface, to execute the ransomware in the machine. Petya is also coded to exploit the EternalRomance vulnerability, an SMB security flaw in Windows XP and Windows 2003 servers.
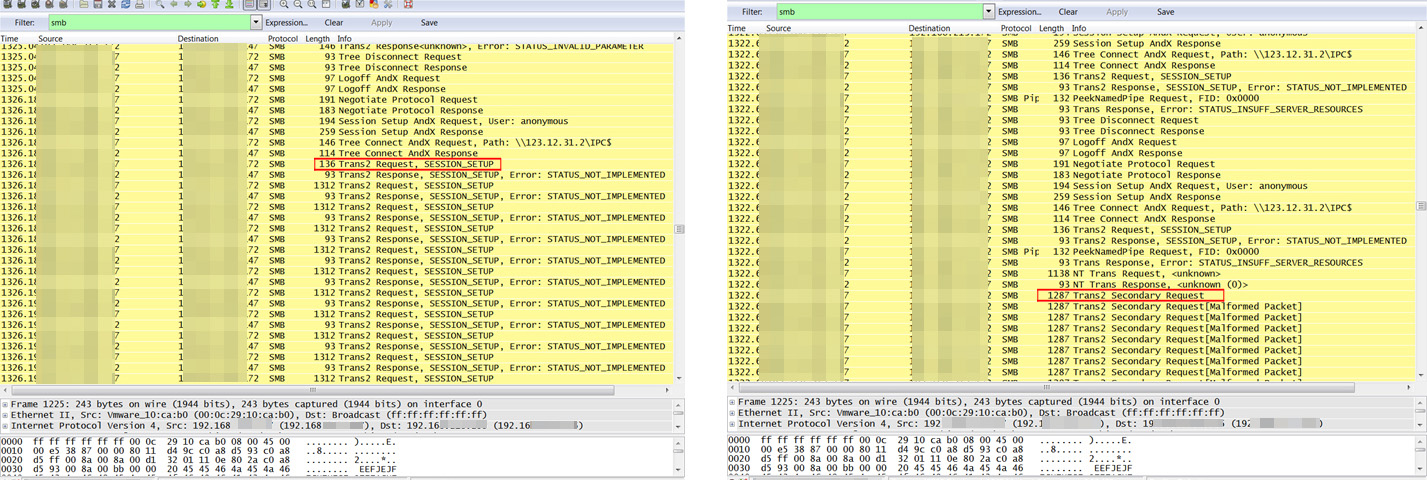
Petya checking for EternalBlue (left, highlighted), and Petya successfully exploiting the vulnerability (left)
[READ: A closer look at WannaCry ransomware’s kill switch and how it can help IT/sysadmins]
Does Petya really have a kill switch?
Again, it’s both yes and no. WannaCry’s kill switch involved a domain that prevents the ransomware from executing when checked/triggered. This played a vital role in mitigating its pervasive impact.
Petya doesn’t have a kill switch per se, but in order to proceed with its encryption routine, it will search for a specific file in the infected system, which is actually spawned by Petya. Note though that Petya checks for its current filename in the Windows folder. This means that the filename being checked by Petya may change. Petya’s encryption uses a modified PsExec embedded in the ransomware renamed as DLLHOST.DAT.
[READ: Take a closer look at SOREBRECT, another ransomware that abuses PsExec]
What does PsExec have to do with this?
Petya’s attack chain involves using PsExec, a Windows command-line utility that lets system administrators execute commands or run executable files on remote systems. Note that for this version of Petya, it abuses two components/executables—PSEXEC.exe, renamed within the ransomware as dllhost.exe, is used to access the remote machine, while PSEXESVC.exe will be executed in the system once a connection/request from PSEXEC.exe is established.
Petya takes steps to evade traditional security solutions and abuses legitimate tools to succeed. The Petya sample we analyzed is a dynamic-link library (DLL) loaded by another legitimate executable, rundll32.exe, which normally runs and loads code in DLLs containing the routines/features of a number of programs or applications.
So why does PsExec matter? Along with rundll32, this executable is legitimate and thus, often whitelisted. PsExec is a system administration tool, while rundll32 maintains the features of programs; unfortunately their very nature is also what makes them viable for cybercriminals to abuse.
[READ: Lessons learned from WannaCry ransomware that users and IT/system administrators can apply]
Is the affected MBR or hard disk recoverable?
It’s complicated. There’s a very narrow window of opportunity: if perfc.dat is directly executed without admin rights, the MBR won’t be overwritten. Given Petya’s attack vectors, however, system user rights will be inherited, which means more often than not it may still be overwritten. And even if the MBR is recovered, the files stored on them will still be encrypted.
Petya also encrypts the system’s Master Table File ($MFT), a database containing metadata that provides attributes about files and directories in an NTFS volume. More importantly, the ransomware deletes the encryption key used to scramble $MFT, making it impossible to be decrypted.
[READ: Learn more about the HDDCryptor ransomware that can also overwrite MBRs]
How does Petya spread?
This version of Petya employs remote code execution to propagate within the local network using PSEXEC.exe (renamed as DLLHOST.DAT). This Petya variant can also propagate by exploiting EternalBlue.
Petya will drop a copy of itself in the affected machine by using DLLHOST.DAT with certain parameters and enumerated credentials. If unsuccessful, Petya will use WMIC.exe to execute the ransomware.
Petya has a customized version of Mimikatz, a penetration testing tool, embedded within the ransomware that extracts usernames and passwords from the affected system. These stolen credentials are also used to spread Petya to other machines within the local network.
[READ: Best practices for securing and using system administration utilities like PowerShell]
What can I do to mitigate this threat?
Petya’s use of multilayered attack vectors also requires a defense-in-depth approach. Some of the best practices and countermeasures IT/system administrators and information security professionals can adopt are:
- Update your systems with the latest patches, or consider using virtual patching in their absence
- Apply the principle of least privilege for all workstations
- Restrict and secure the use of system administration tools such as PowerShell and PsExec
- Disable tools and protocols on systems that don’t require it (i.e., TCP port 445)
- Regularly back up important data
- Proactively monitor networks for any suspicious activities or anomalies
- Employ behavior monitoring mechanisms that can prevent unusual modifications (i.e., encryption) to systems
- Deploy network segmentation and data categorization to mitigate further damage that can be incurred from an attack
- Secure the email gateway and employ URL categorization (to block malicious websites) to reduce attack surface
Addendum: Updated on June 29, 2017, 6:09 AM PDT to include additional details on EternalRomance, $MFT encryption, and disk modification capability.
Trend Micro Ransomware Solutions
Enterprises should use a multi-layered approach to mitigate the risks brought about by threats like ransomware.
At the endpoint level, Trend Micro Smart Protection Suites deliver several capabilities like high fidelity machine learning, behavior monitoring and application control, and vulnerability shielding that minimize the impact of this threat. Trend Micro Deep Discovery Inspector detects and blocks ransomware on networks, while Trend Micro Deep Security™ stops ransomware from reaching enterprise servers–regardless if they’re physical, virtual, or in the cloud.
For small businesses, Trend Micro Worry-Free Services Advanced offers cloud-based email gateway security through Hosted Email Security. Its endpoint protection also delivers several capabilities such as behavior monitoring and real-time web reputation in order detect and block ransomware.
For home users, Trend Micro Security 10 provides strong protection against ransomware by blocking malicious websites, emails, and files associated with this threat.
Find more in-depth information on Trend Micro detections and solutions for this threat in this Petya ransomware technical support page. Technical details about this version of Petya can be found in our TrendLabs Security Intelligence blog post.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One