Database Passwords of Anchor CMS Users Inadvertently Exposed
A recent report has highlighted an issue with Anchor CMS, a lightweight blogging platform targeted towards users looking for a simple and easy system. Dutch researcher Tijme Gommers discovered that sites built using Anchor CMS may be inadvertently exposing their database passwords in public error logs.
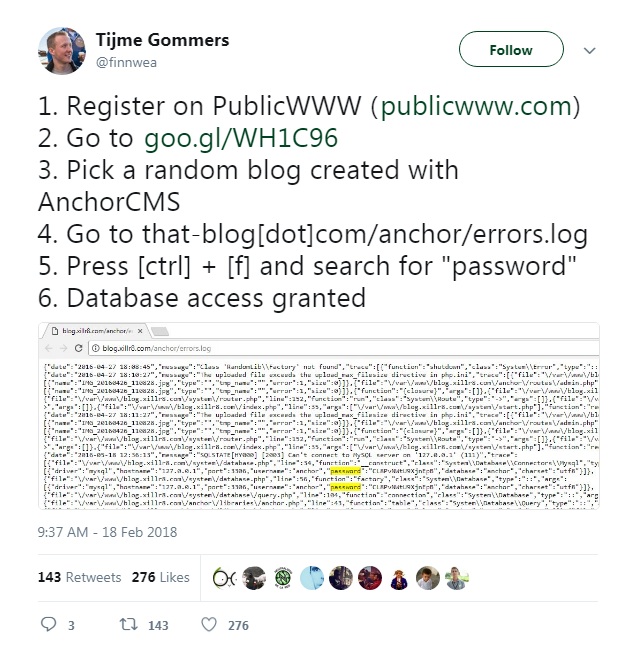 Figure 1. Gommers initial tweet showing the Anchor CMS vulnerability
Figure 1. Gommers initial tweet showing the Anchor CMS vulnerability
Based on Gommer's tweet, anyone can simply visit the site mentioned and download a copy of the site’s error log. Within that log, database passwords are searchable and exposed in cleartext. Users of AnchorCMS may not even have been aware of this issue since this particular file is not flagged by the service as notable or important. But any developer should always be aware of the security limitations and options available in the services they use, and evaluate what is needed before it becomes a serious concern.
The news report highlights the severity of the issue: when there are too many concurrent connections to the MySQL server, a common occurrence for most websites, an error is logged. In the file entry, the credentials included in the log are enough for a remote attacker to gain access to the server, as it contains the user name, database password, and IP.
A determined attacker will find it quite easy to gather the information needed to compromise a website by simply digging through the available error logs.
[READ: InfoSec Guide: Web Injections]
Finding the right solutions
The researcher does not plan on reporting this to the Anchor CMS team, and has said that this is more a DevOps issue. As a rule, webmasters should consider security from initial development onwards, and should control access as much as possible. For this particular issue, the best thing to do is to limit access to *.log files via htaccess for all content management systems.
[READ: How DevOps Can Be a Model for Effective Cyber Security]
However, this may also be addressed on the service side—Anchor CMS could stop gathering sensitive credentials in the errors log, block access to the log file, or implement other solutions that would ultimately prevent the exposure of this information.
Is this a compliance issue?
With the new regulations on managing data fast approaching, most enterprises should be careful about storing and handling sensitive data. Privacy is a very real concern. The EU General Data Protection Regulation (GDPR), which takes effect on May 25 of this year, has strict provisions about managing credentials and demands privacy by design. It specifies that entities should “hold and process only the data absolutely necessary for the completion of its duties (data minimisation), as well as limiting the access to personal data.”
It is a consideration all organizations—small and large—should take when handling any kind of data. Complying with this standard is not just a legal matter, but it will also create a more efficient and safer environment, ultimately giving services a competitive advantage and a better reputation with customers.
Aside from privacy and security by design, organizations can look into comprehensive solutions such as Trend Micro™ XGen™ security, which provides a cross-generational blend of threat defense techniques against a full range of threats for data centers, cloud environments, networks, and endpoints. It features high-fidelity machine learning to secure the gateway and endpoint data and applications, and protects physical, virtual, and cloud workloads.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One