CoinVault Ransomware, Not the First to Give Away Freebie Decrypts
Free samples are again out of the mall and into your malware-ridden computers.
The freshly minted CoinVault threat of the cryptographic ransomware variant—those that encrypt your files and keep them hostage unless you pay up—offers an interesting twist to the typical ransomware setup: You get to decrypt one file for free.

CoinVault Revives Freebie Decrypts
However, this is not the first time that ransomware creators have given their victims the option to get one file back for free. One specific variant of the CryptoWall ransomware displays a button on screen which allows victims to decrypt one file for free.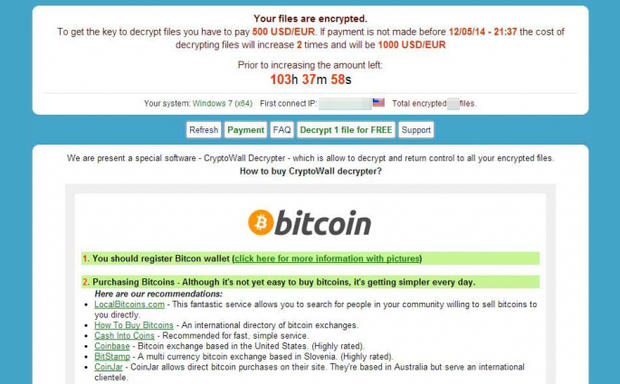
image source: TechRepublic.com
In addition, we have seen a number of interesting routines from ransomware variants since we started tracking them. TROJ_CRITOLOCK.A, for one, demands to be paid the ransom amount in bitcoins in order to retrieve a “private key” for decrypting users’ files. Meanwhile, Cryptobit, CrytoDefense, and CryptoWall variants instruct users in various ways on how to pay using the Tor browser so the bad guys are harder to track.
CoinVault uses a "freemium model" by offering its victims one freebie decrypt. By giving victims a taste of how easy it is to unlock the decrypted data, the chances of victims paying up increases as well. This makes this threat a tad more dangerous than the past cryptographic locker variants of its kind. Chances are those who would not believe the wallpaper display that warns of a CRILOCK Trojan, for instance, are unlikely to believe this one because of the freebie decrypt.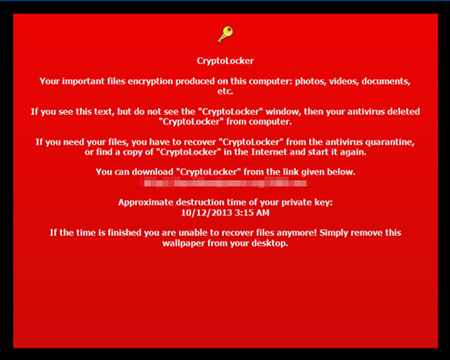
CoinVault can get inside your computers by getting automatically downloaded from malicious websites visited or an infected drive inserted. Once inside the system, it can gather information, encrypt files, and connect to certain websites.
We have outlined a series of steps on how victims affected by CoinVault can delete the threat from their systems in our threat encyclopedia: technical solution against CoinVault or TROJ_Cryptcoin.AK.
3-2-1 Backup Rule
Backing up ensures that you don't lose your data even if you become a victim of ransomware. Good backup obeys the 3-2-1 rule:
This is summarized as follows:
- At least three copies,
- In two different formats,
- with one of those copies off-site.
[Read: World Backup Day: The 3-2-1 Rule]
This rule relies on the concept of redundancy, and makes sure that a single event can’t destroy your copy as you have three stored in various places, that the risk of damage is reduced since you store them in different formats, and that one copy is safe in an alternate setting in case of a disastrous event like a fire or a break-in.
Update: More in-depth technical analysis on CoinVault, as well as the list of related hashes, is available at the Security Intelligence Blog.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One