Attack Uses Fake Google Docs Application to Access Gmail Accounts
![]() Users who have received a legitimate-looking Google Docs link in their Gmail accounts may be potential victims of a sophisticated phishing attack that has been making the rounds recently. The scam is highly effective due to its perpetrator’s use of a third party application which is cleverly disguised as the Google Docs app—making it more difficult to detect than typical phishing scams.
Users who have received a legitimate-looking Google Docs link in their Gmail accounts may be potential victims of a sophisticated phishing attack that has been making the rounds recently. The scam is highly effective due to its perpetrator’s use of a third party application which is cleverly disguised as the Google Docs app—making it more difficult to detect than typical phishing scams.
The initial email arrives on a user’s Gmail account from a known contact who wants to share a document. This email contains a link to the real Google account authentication webpage, complete with a list of accounts owned by the user. The page will then prompt the user to choose an account and will also request permissions for an application with the misleading “Google Docs” name. However, giving permissions to this application will allow the scam’s perpetrators access to the user’s inbox and contact list, providing them the ability to read and send emails. The malicious application will then copy the victim’s contact list and send a duplicate of itself to all the names in the list. This method of replication allows it to spread quickly in a short amount of time.
Unlike a true phishing attack, the “Google Docs” application does not request for the user’s password. It relies on Open Authentication (OAuth) abuse—such as the one seen in the recent Pawn Storm attacks, to log into a user’s online accounts and gather information.
Google managed to get wind of this scam from a Reddit thread and managed to address the problem within an hour by taking down the malicious application. The company also issued the following statement via their official Twitter account: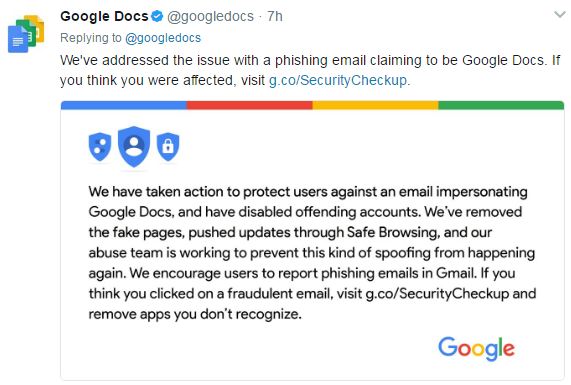
The company encourages all users who suspect they could have been affected by the phishing attack to visit https://myaccount.google.com/permissions page to check for all previous access to their accounts by third party applications.
The key takeaway with this incident is that cyber criminals can often use a company’s own tools to make their attack attempts look as legitimate as possible. And while no malware is currently being detected with this campaign, the potential for a fast-spreading and widespread attack can clearly be seen. To mitigate this, users have to be extremely careful with any files or links they receive--even if it was sent by someone they know. While Google is currently working on a solution that would prevent these types of attacks from happening in the future, it would be prudent in the meantime for users not to click on any kind of Google Docs link before verifying.
Trend Micro Solutions:
Trend Micro offers a broad range of email and collaboration security solutions to protect users from threats delivered through cloud-based platforms. Cloud App Security is a cloud-based protection service that secures email and cloud file sharing in Office 365, Dropbox, and Google Drive by finding unknown malware hidden inside office files.
Trend Micro™ Deep Discovery™ Email Inspector detects and blocks ransomware spear phishing emails through advanced analysis techniques for known and unknown attacks.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- The State of Criminal AI: Market Consolidation and Operational Reality
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One