Activists have traditionally used physical signs and catchy slogans to promote their agenda, but many have since moved online to reach a significantly broader audience. Some of these online vandals subvert and deface websites to push a specific message, and others put forward political ideas in an act generally known as “hacktivism”. Our study shows samples of these web defacements that date as far back as 1998, most of which were triggered by specific political events, targeting a variety of different websites.
We saw powerful geopolitical events triggering these web defacements and how political beliefs and the defacers' religious inclination factor into the attacks. The defacers use different methods of hacking to compromise websites—from exploiting file inclusion vulnerabilities to simply stealing passwords from the administrator. We analyzed 13 million website defacements collected from five independent data sources to gain deeper insight into these actors and their methods.
Defacement Targets and Methods
The data we analyzed was aggregated from reports submitted to various defacement archives by the defacers themselves, along with shared initiatives, CERTs, and even data on the victims. It was collected over multiple countries, from 1998 to 2016. In terms of targets, this overview shows the different systems and servers that defacers targeted the most.
The major operating systems that defacers targeted
Unspecified nginx 757,306
The major web servers that defacers targeted
The metadata (which we cannot validate) the defacers voluntarily provided show that attackers leverage a wide range of vulnerabilities to compromise websites, listing over 30 different methods. Attackers typically compromised sites through common vulnerabilities such as local file inclusion, SQL injection and password guessing. Some other notable methods mentioned include server intrusion attacks, social engineering, URL poisoning, and the use of man-in-the-middle attacks to access credentials.
We also found that defacers voluntarily leave contact information on the defaced site, which is not typical of other cybercrimes. We found that they used email and Twitter as primary forms of advertisement, with 25% (email) and 8% (Twitter) of pages displaying at least one of these. In fact, 6% of the pages had multiple contact email addresses. It seemed like these hacking groups were promoting themselves along with their slogans and political messages.
The addition of streaming media left on websites is another interesting aspect of propaganda-driven attacks, usually in the form of visual aspects or songs playing in the background. We found that 32% of the defacements had embedded a URL referencing either a streaming service provider (like YouTube) or an audio file hosted on an external resource.
Conflicts Spark Anti-Israel Defacement Campaigns
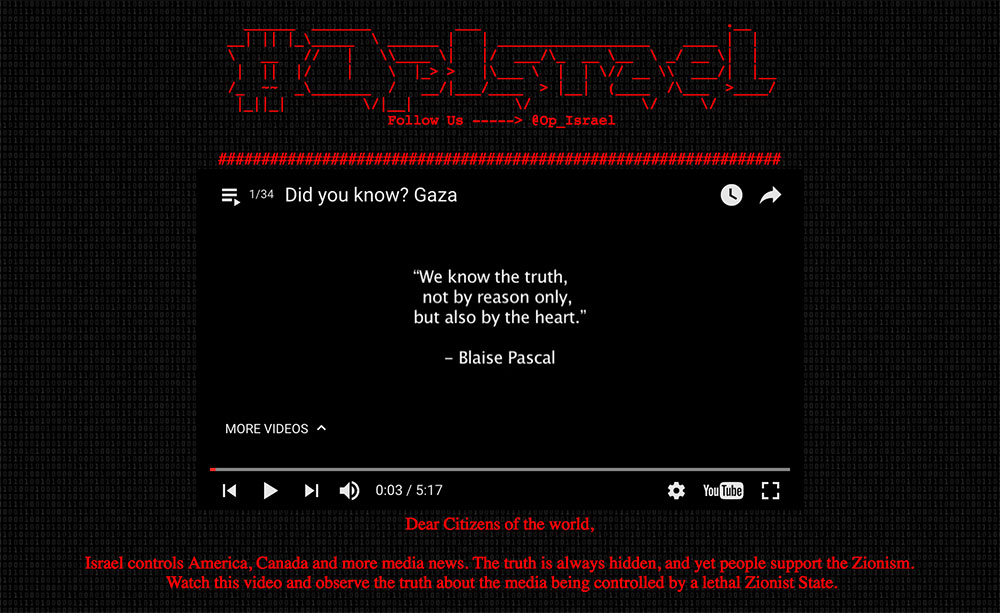
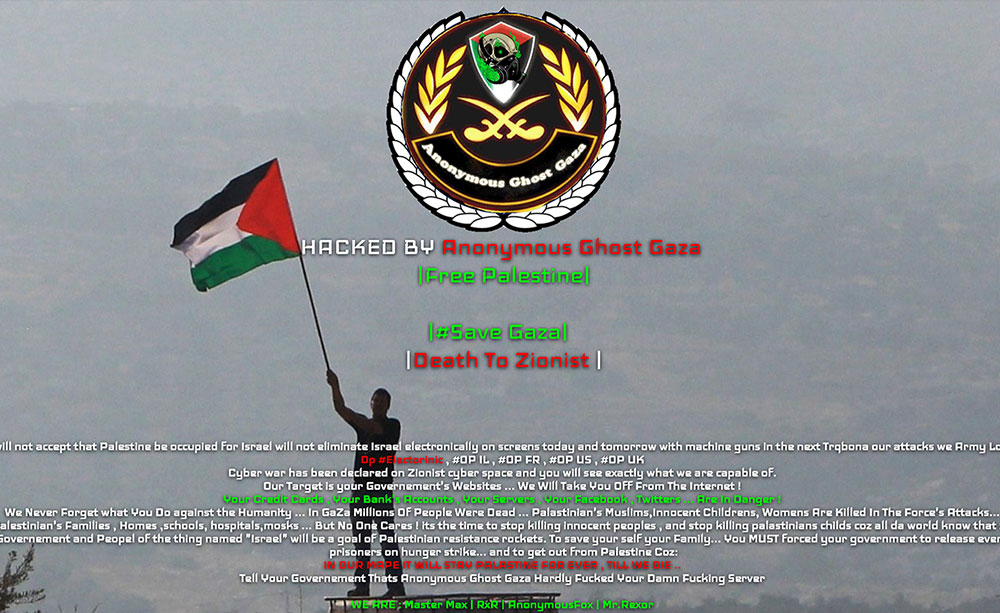
The long-standing conflict between Israel and Palestine fueled several anti-Israel defacement campaigns. #OpIsrael is the first (and longest) campaign, followed by the short but highly effective #OpSaveGaza. Last is #OpBader / #ElectronicBader / #BaderOperation, a loosely organized campaign involving multiple hacking groups.
Defacement page for #OpIsrael
Forceful language in the defacement campaign #Save Gaza
__________
Charlie Hebdo Aftermath Results in #OpFrance
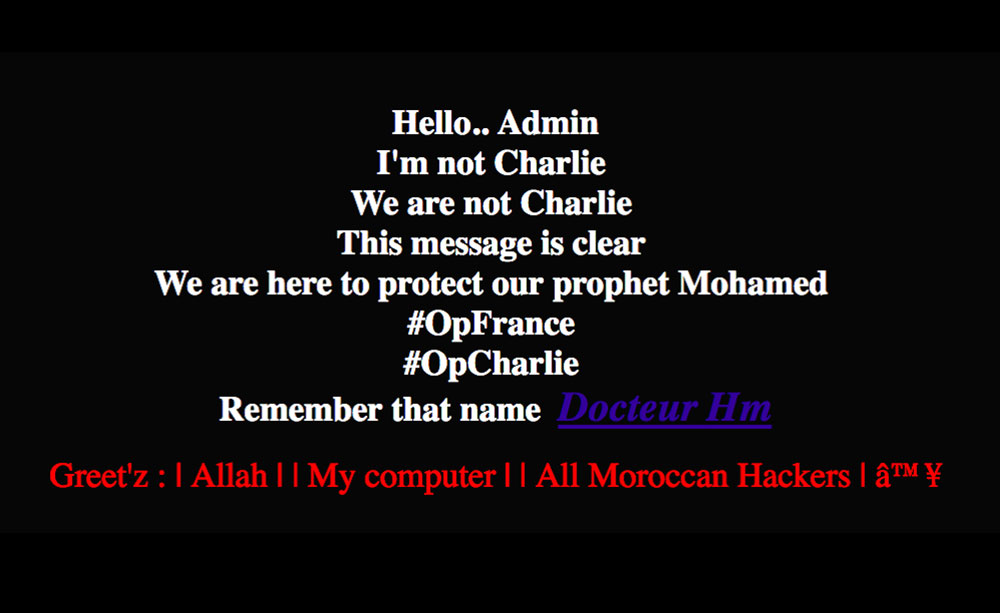
Groups from Muslim majority countries began targeting French websites with defacement campaigns in support of the attack on French satirical magazine Charlie Hebdo. The campaign was identified as #OpFrance, with smaller campaigns under it that include #OpCharlie #OPCHARLIEHEBDO, #AntiCharlieHebdo. One suspected member of the Middle East Cyber Army (alias "The Greatest") was arrested several months after the #OpFrance campaign that stretched from January to March.
Defacement pages for the #OpFrance campaign
Defaced page modified to support “The Greatest”, who was supposedly arrested in Bulgaria
__________
Indian Border Disputes Trigger Campaigns
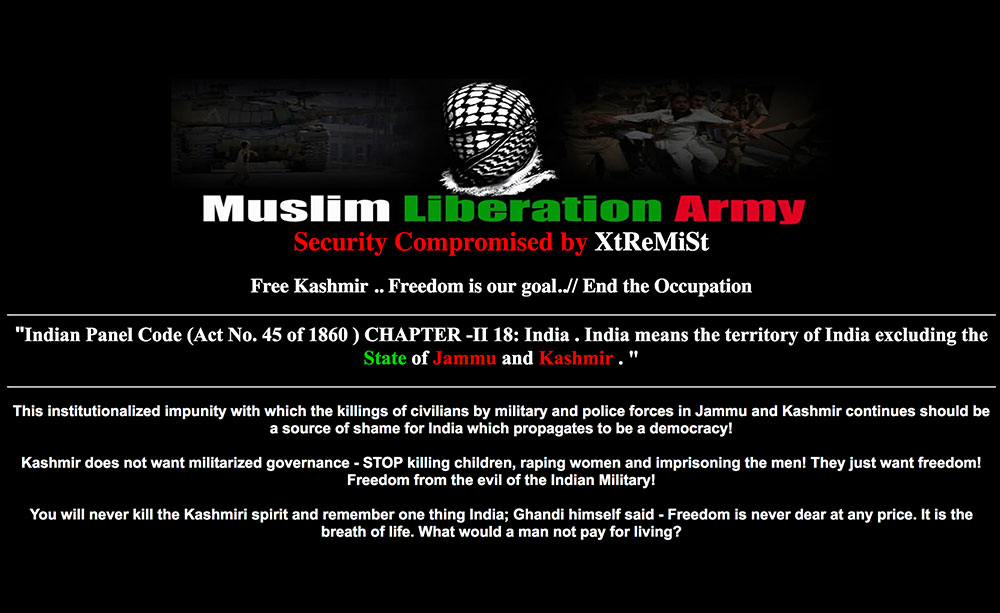
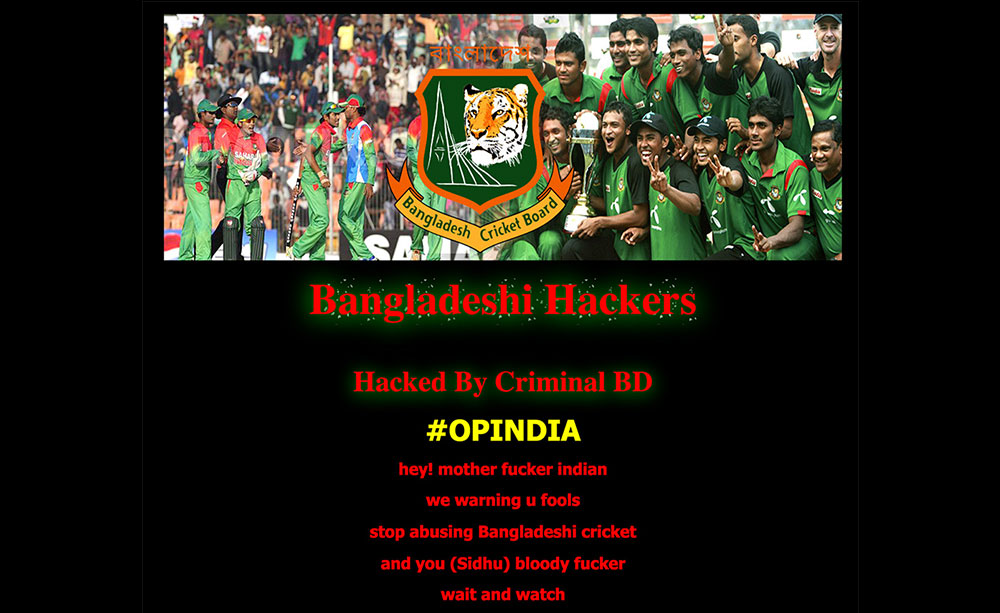
Like Israel, India has several unresolved territorial disputes, specifically with Pakistan regarding Kashmir, with Bangladesh about its borders, and with Nepal on amending the country’s constitution. These conflicts fueled a Free Kashmir campaign in 2011, a widespread #OpIndia campaign in March 2015, and #BackOffIndia defacements triggered by the Nepal conflict.
Free Kashmir campaign defacements; Pakistan is India's rival claimant
Defacement page for #OpIndia with an image of the Bangladesh cricket team featured
A campaign triggered by India’s involvement with Nepalese matters
__________
Military Actions prompt a #SaveSyria Campaign
In April 2016, the Syrian government launched airstrikes targeting residential areas despite an existing ceasefire agreement between both sides. This triggered a #SaveSyria campaign that exposed graphic images of wounded civilians in Aleppo. Most of the #SaveSyria defacements targeted Russian websites because many suspected that Russia was behind the airstrikes.
Defaced sites showing graphic images of Aleppo
__________
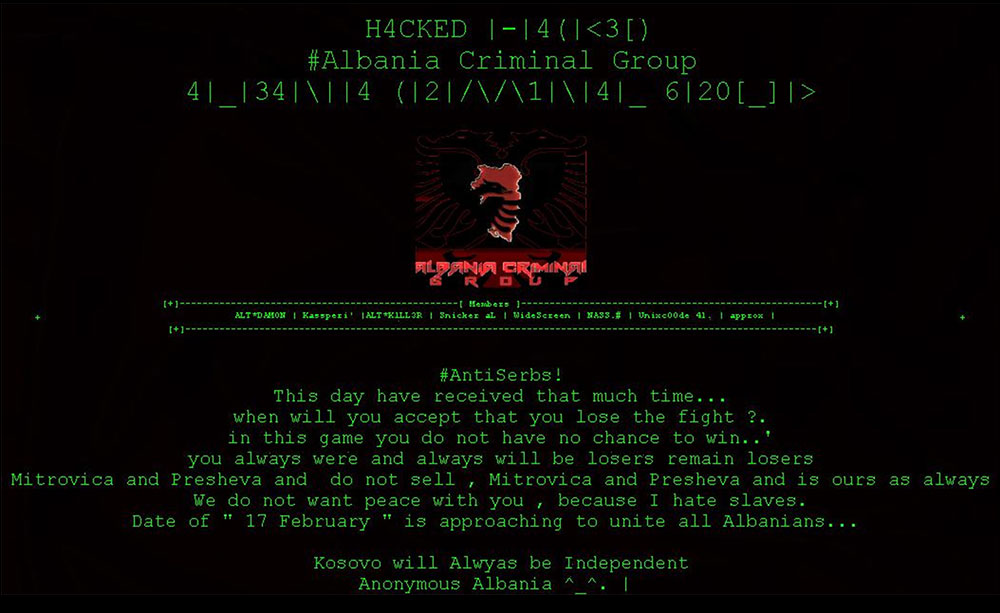
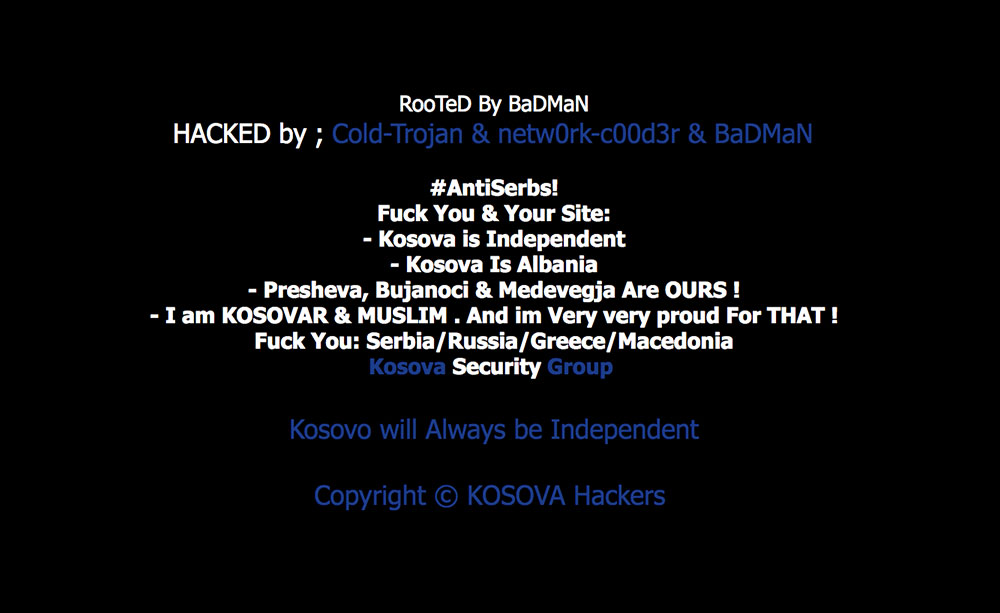
Campaigns Provoked by Kosovo Disputes
Kosovo is a disputed territory and partially recognized state that declared its independence from Serbia in 2008. However, some communities of Serbian descent in Northern Kosovo refused to acknowledge Kosovo's independence. In 2011, Kosovo Police clashed with ethnic Serbian rioters, triggering a series of defacement pages showing support for Kosovo independence.
Defacement pages supporting Kosovo
__________
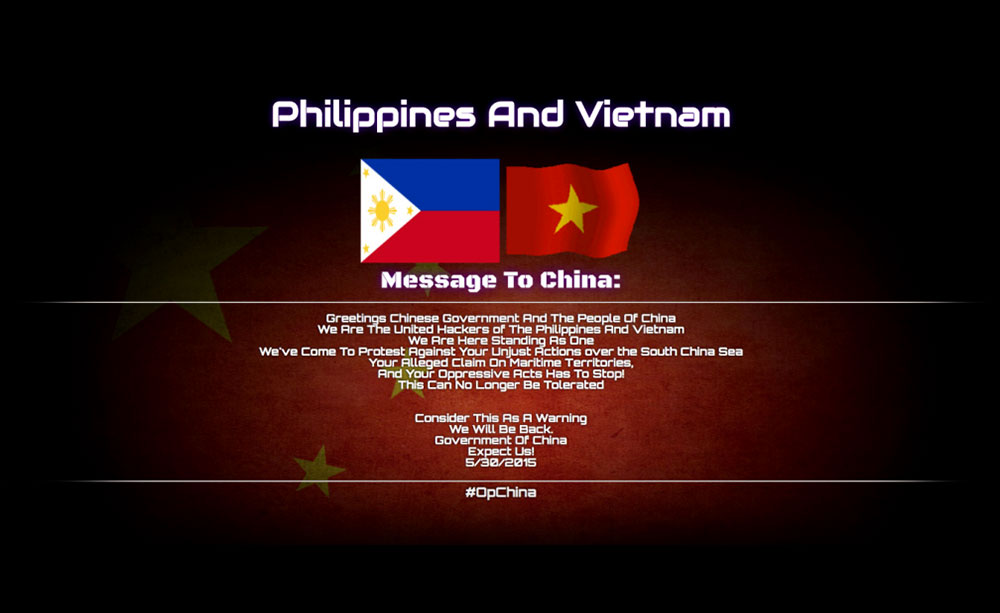
Disputes in the South China Sea
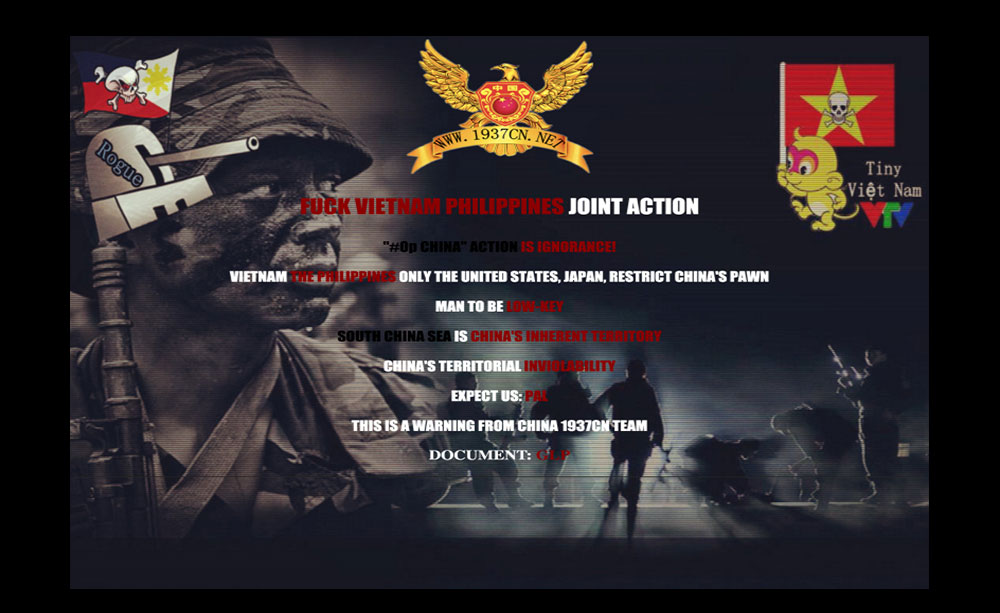
Six countries around the South China sea (China, Taiwan, Philippines, Vietnam, Malaysia and Brunei) are contesting several islands and features, rock outcrops, sandbars, and reefs in the region. The tension between China and Vietnam, as well as China and the Philippines has increased over the past few years. These territorial disputes fueled several defacement campaigns between the groups sympathetic to the opposing sides.
A joint message from Vietnamese and Filipino hackers, protesting Chinese actions
Retaliation from Chinese hackers
__________
How Defacement Communities Operate
Defacing groups can be defined as ‘loose affiliations’ since members can be active in more than one group. Sometimes individual hackers come together simply because they are reacting to the same event. These different groups can also come together to form bigger teams or collectives.
Operating much like other organizations, hacking groups use social media sites to coordinate and launch events and campaigns. They also set up team pages to advertise campaigns and actively recruit other hackers and hacking groups to participate.
Within these communities, those participating in a campaign also readily share tools, target lists, and defacement page templates. The goal is to make a widespread statement, so those involved actively give out materials.
Certain groups also set up team websites to host content and announcements, and use forums to facilitate discussions. These forums commonly have sections for tutorials, tools and kits. Apart from defacement materials, these groups share other attack techniques as well. For example, they post hacking tutorials on Github and tutorial videos on streaming sites.
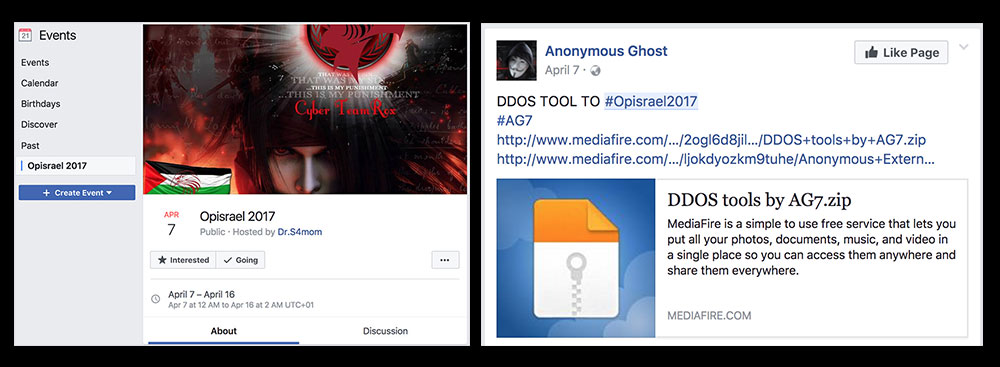
Social media tools used for defacement activities
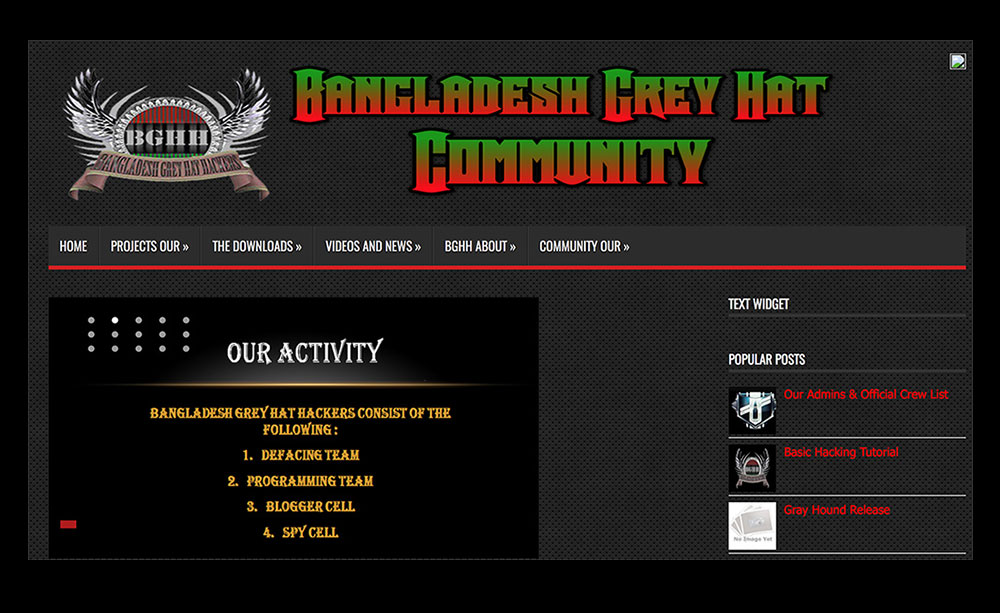
Example of a community site hosting forums, downloads, news and more
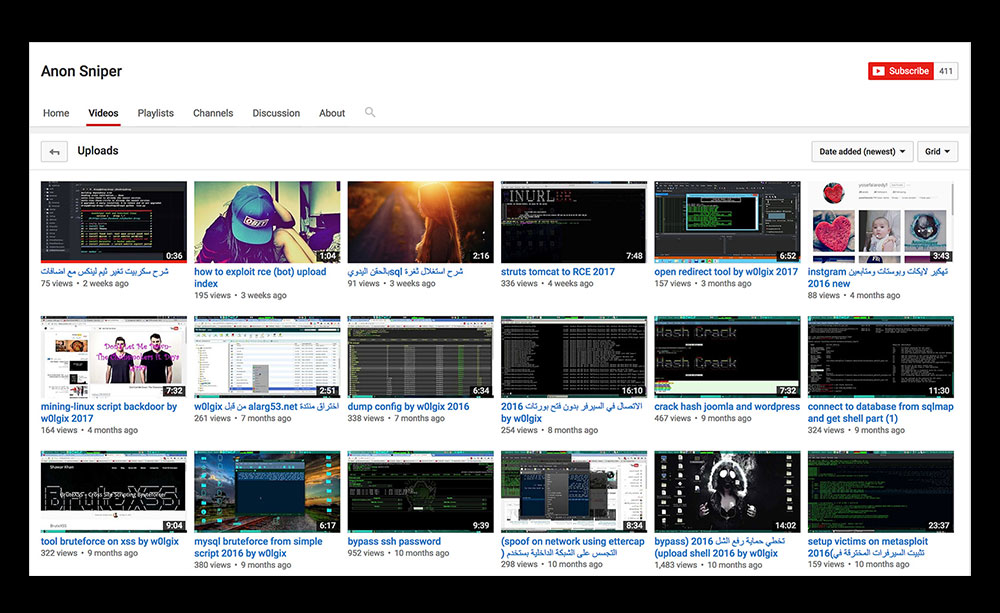
Tools and tutorials for different hacking activities shared by defacers
Defacers are also contributing to Exploit-DB, which is an open-source database for sharing exploit codes and security papers. Comparing our list of known defacers to authors on Exploit-DB, we found that 10% of them were contributors. As expected of hackers who compromise and deface sites, the majority of the exploits they shared were for web apps.
Types of exploits submitted by possible defacers
__________
Beyond Defacement
Conflict and specific events can trigger defacement activities, bringing together disparate hackers and hacking groups. These collectives can sustain campaigns for years, and actively share their tools and methods within closed groups. While some may begin with simple defacement, as we’ve seen in the communities they create, it can lead to exploring other activities and criminal behavior.
During the course of our study, we found that most defacements were relatively benign. However, the web servers the defacers compromise contain potentially sensitive data (PII, account credentials, transaction histories, etc.), which is quite valuable information. If these hackers decide they want to make a profit, they could easily capitalize on the access they have. Hackers are becoming increasingly involved in developing web shells (backdoors to maintain access to compromised web servers), and delving into doxing and leaking stolen data.
Apart from individuals, defacement groups could also easily monetize their successful web exploits. For example, they could redirect website visitors to a malicious page, or install malware on the site itself. Depending on the capabilities of the hacker, there are numerous possibilities. Enterprises and users should be aware that these defacements mean that hackers can access any vulnerable site, and that these security holes are serious issues that must be addressed.
__________
How can enterprises protect their sites?
Based on the major vulnerabilities defacers used, there are simple steps that can secure servers against these threats:
- Employ basic security policies and enforce them long-term: strong passwords, proper administration security policies, correct configuration.
- Use web application firewalls to filter, monitor, and block malicious traffic. Security is necessary at the web application level.
- Practice secure coding. Organizations must implement secure coding standards on all their sites.
- Use testing tools to ensure deployed codes are secure.
- Make patching systems and networks a part of standard policy. This prevents cybercriminals from exploiting vulnerabilities in unpatched/outdated software.
- Regularly scan web applications for vulnerabilities: Organizations need to check their web apps for vulnerabilities as these can lead to SQL injection and cross-site scripting attacks.
- Use multi-layered protection that secures vulnerable websites from the common attacks used by defacers. Solutions like Trend Micro™ Deep Security™ and Vulnerability Protection provides virtual patching that protects servers and endpoints from threats that may abuse vulnerabilities.
 View A Deep Dive into Web Defacement
View A Deep Dive into Web Defacement






 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One