Protecting Yourself from Bad Rabbit Ransomware
Bad Rabbit is a new ransomware currently spreading across Eastern Europe. News reports are saying that it is targeting mainly media organizations in Russia and infrastructure and transportation services in the Ukraine. Initial analysis shows that it bears some similarities to Petya, which was a ransomware caused widespread damage in June. BadRabbit uses an exploit that targets Server Message Block (SMB) vulnerabilities.
Here’s what we know:
I’m a Trend Micro customer, am I protected?
- Yes, Trend Micro products with XGen™ security proactively detect this ransomware as TROJ.Win32.TRX.XXPE002FF019 without the need for a pattern update.
How does it infect users?
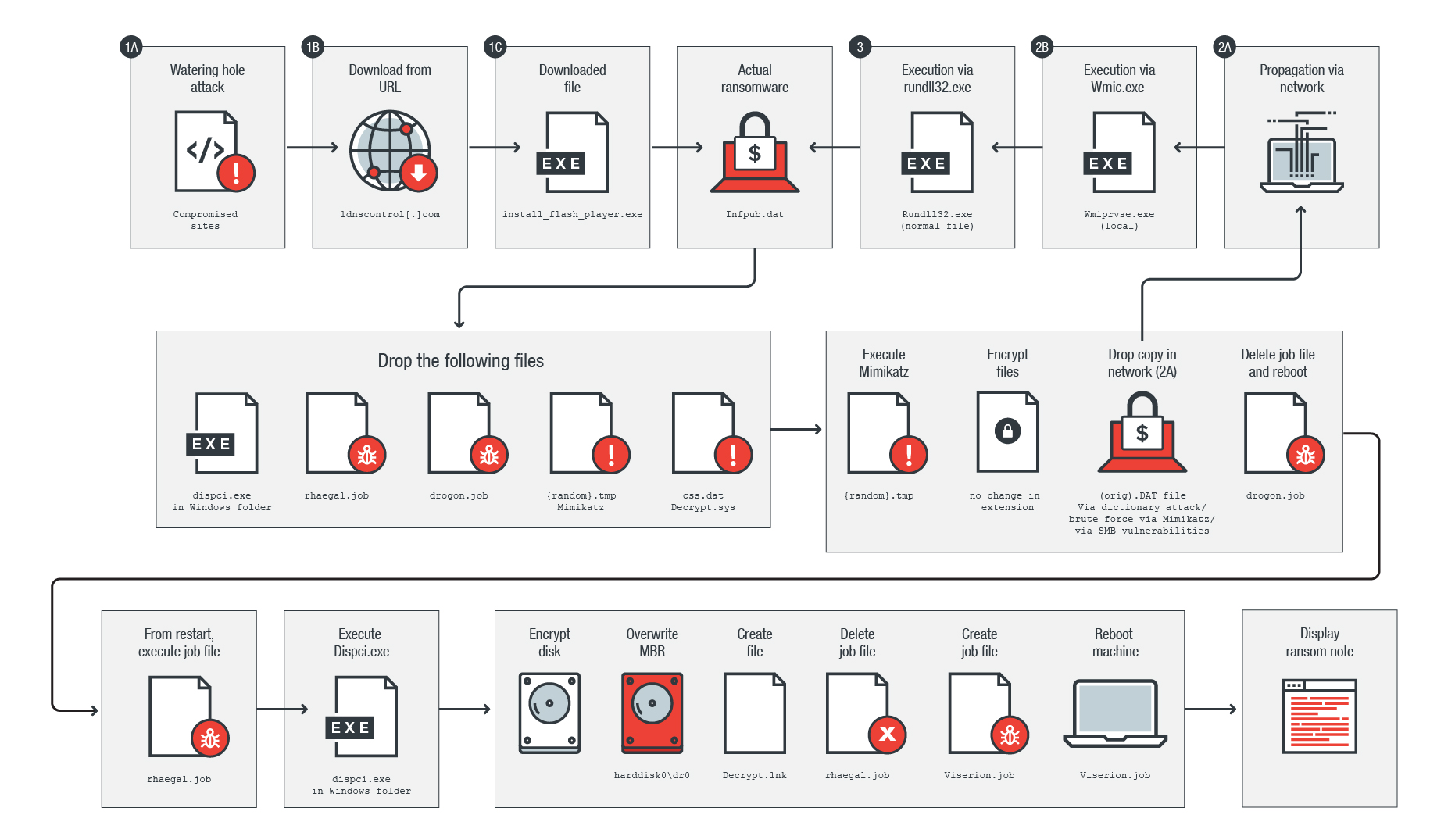
- Bad Rabbit uses a typical watering hole attack. With several compromised sites it attempts to convince users to install a fake Flash installer. If clicked, the installer drops malicious files.
How does it work?
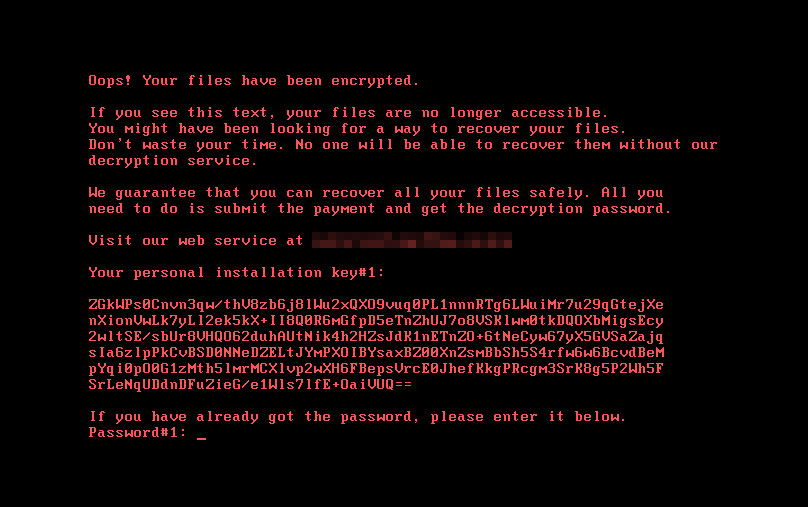
- The fake Flash installer drops several files that will encrypt files and shut down the victim’s machine.
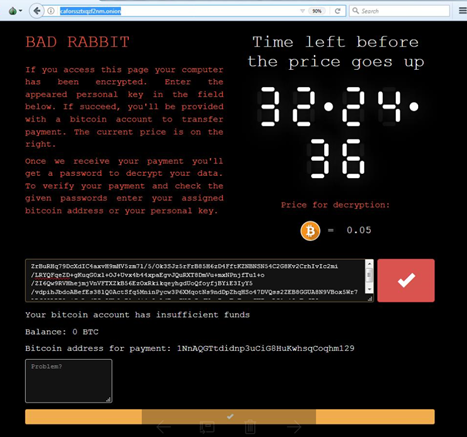
- The ransomware then modifies the system’s master boot record (MBR), displays a ransom note, and finally reboots the infected system again.
- Three of the malicious files are named after dragons from the popular TV series Game of Thrones (rhaegal.job, drogon.job, viserion_23.job).
- It uses a dictionary attack to harvest credentials from the infected computer and tries to access computers from the same network and spread laterally.
- Bad Rabbit also attempts to brute force any administrative shares it finds; if successful it drops a copy of itself into these shares.
- If these bruteforce attacks fails, it uses an exploit targeting the Eternal Romance SMB vulnerability resolved in MS17-010. These vulnerabilities were patched in March of this year.
- Keep your systems updated and patched. Cybercriminals often take advantage of known exploits, but patches from vendors come out regularly and can protect users from many attacks.
- Habitually back up files. Ransomware distributors gain leverage by encrypting files and threatening you with data loss. If you have backups of the affected files, the cybercriminal loses this leverage.
- Educate yourself on ransomware best practices for end users and businesses.
- Use multilayered security solutions that protect the points of entry attackers use to infect most users—namely websites and email.
Enterprises can benefit from a multi-layered, step-by-step approach in order to best mitigate the risks brought by these threats. Email and web gateway solutions such as Trend Micro™ Deep Discovery™ Email Inspector and InterScan™ Web Security prevent ransomware from ever reaching end users. At the endpoint level, Trend Micro Smart Protection Suites deliver several capabilities like high-fidelity machine learning, behavior monitoring and application control, and vulnerability shielding that minimize the impact of this threat. Trend Micro Deep Discovery Inspector detects and blocks ransomware on networks, while Trend Micro Deep Security™ stops ransomware from reaching enterprise servers–whether physical, virtual or in the cloud. Trend Micro XGen™ security provides a cross-generational blend of threat defense techniques against a full range of threats for data centers, cloud environments, networks, and endpoints. Smart, optimized, and connected, XGen™ powers Trend Micro’s suite of security solutions: Hybrid Cloud Security, User Protection, and Network Defense.
Detailed solutions for Bad Rabbit ransomware can be found on our dedicated site.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One