Security 101: Defending Against Fileless Malware
by Simon Floreza, Donald Castillo, and Mark Manahan (Threats Analysts)
Fileless malware aren’t new, but they’re an increasingly prevalent threat. In fact, it was reported that 77 percent of successful cyberattacks against enterprises used fileless techniques. They aren’t as visible compared to traditional malware, employ a variety of techniques to stay persistent, and can adversely affect the integrity of the organization’s business process and the infrastructures that run them.
Here’s a closer look at how fileless threats works and what can be done to thwart them:
Launching malware via document exploits
Fileless threats can make its way through traditional means. These can come from malicious macro codes in the form of JavaScript or VisualBasic (VBA) scripts embedded within Office documents, PDFs, archives, or seemingly benign files. Once opened, these macros will run the scripts and often abuse legitimate tools like PowerShell to launch, download, and execute more code, scripts, or payloads. These scripts are typically executed by tools like PowerShell encoded and obfuscated, making it challenging for monitoring software to detect obvious keywords that trigger their execution.
These scripts can either abuse PowerShell to retrieve and run an executable on the system’s local storage/disk or run the code directly in memory. In the latter case, the attack isn’t entirely fileless, as it still relies on actual files and employs macros to gain an initial foothold on the system.
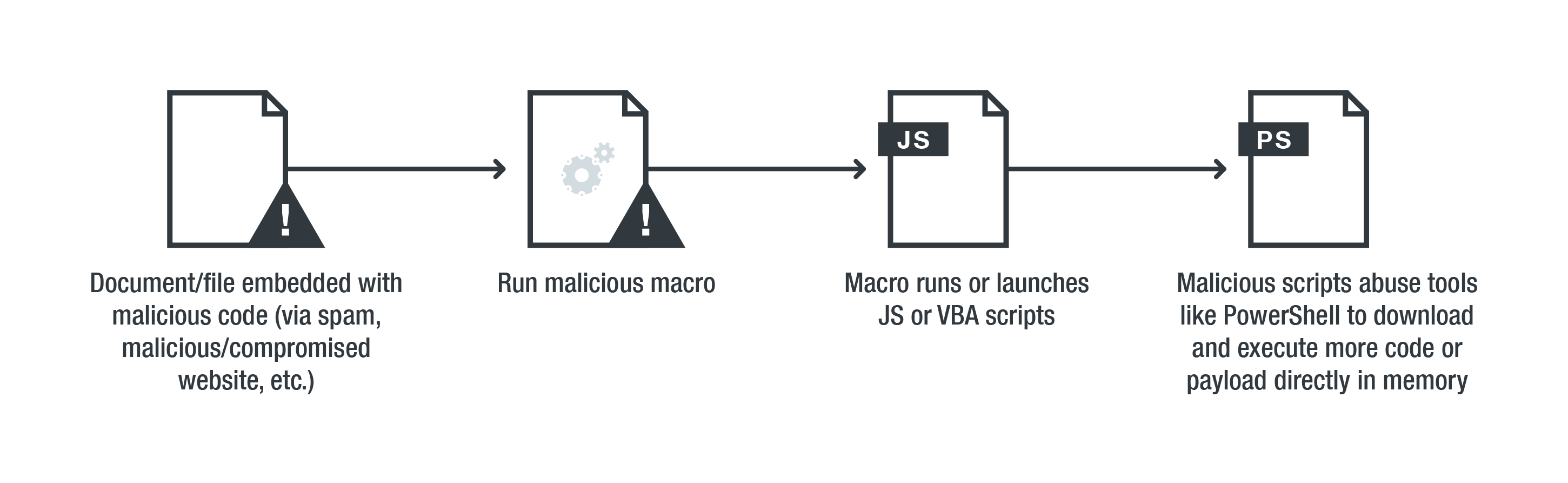
An infection chain of a fileless threat that uses document exploits
Users can reduce their exposure to these threats by practicing security hygiene and fostering a more cybersecurity-aware workplace. This includes being more cautious of unsolicited emails or files, especially those that prompt users to enable macros or scripts.
To protect against fileless threats that use spam emails as vectors, enterprises can take advantage of Trend Micro™ endpoint solutions such as Trend Micro Smart Protection Suites and Worry-Free™ Business Security. Both solutions protect users and businesses from threats by detecting malicious files and spammed messages, and blocks all related malicious URLs. The Trend Micro Deep Discovery™ solution has a layer for email inspection that can protect enterprises by detecting malicious attachments and URLs. Deep Discovery can detect the remote scripts even if it is not being downloaded in the physical endpoint.
Trend Micro™ Hosted Email Security is a no-maintenance cloud solution that delivers continuously updated protection to stop spam, malware, and advanced targeted attacks before they reach the network. Additionally, Trend Micro Anti-Spam Engine detects and blocks malicious files without using signatures. Hosted Email Security protects Microsoft Exchange, Microsoft Office 365, Google Apps, and other hosted and on-premises email solutions. Trend Micro™ Email Reputation Services™ detects the spam mail used by this threat upon arrival.
Delivering payloads via in-memory exploits
Fileless threats derive its moniker from loading and executing themselves directly from memory. This makes antivirus (AV) detection more difficult compared to other malware and malicious executables, which write to the system’s disks. Fileless malware employ various ways to execute from memory. Most use malicious code injection, often to a legitimate process to avoid detection. They also abuse legitimate system administration tools and application programming interfaces (APIs) such as PowerShell, PsExec, and Windows Management Instrumentation (WMI) to take over the legitimate process’ memory and privileges.
Reflective DLL injection is the most prevalent technique used by in-memory exploits. This involves malicious code loading a dynamic-link library (DLL) into a host process, thus eliminating the need for the DLL to be written to the disk.
EternalBlue is a real-life example of an in-memory exploit. EternalBlue takes advantage of a vulnerability in the Server Message Block 1 (SMB 1) protocol, which lets attackers read applications, access services, and write to the files. Attackers could then inject their code to the system’s local security authority subsystem service (lsass.exe), a legitimate and crucial system file that manages credentials, user logins, and access tokens. Attackers can use this as a springboard for further attacks, such as abusing penetration testing tools like Mimikatz to retrieve credentials from the memory.
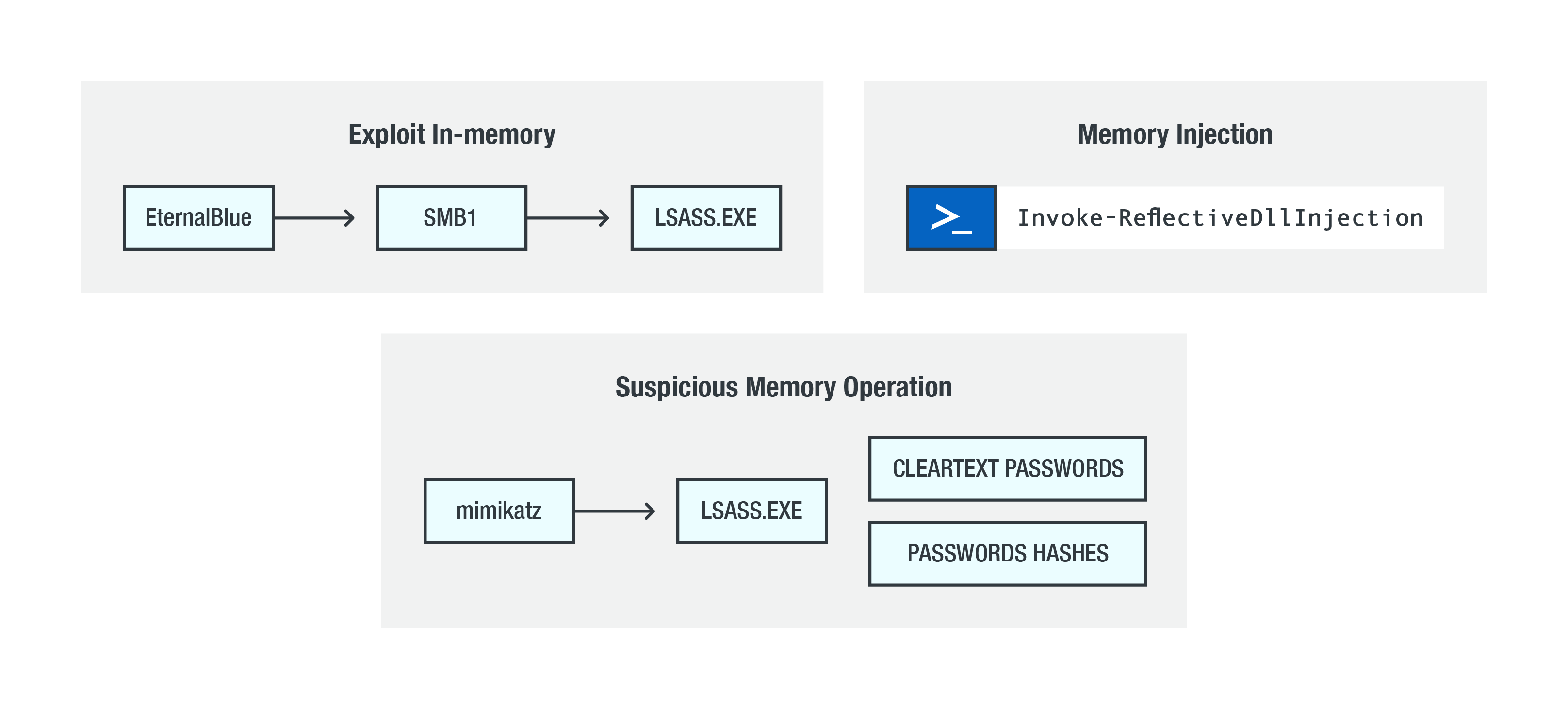 Overview of different in-memory exploit techniques
Overview of different in-memory exploit techniques
Fileless threats can also employ techniques like process hollowing, which the SOREBRECT ransomware uses. Like Petya/NotPetya, it abuses the PsExec tool to inject its code — or specifically, swap the original/legitimate process’ code (svchost.exe, which hosts instances of Windows services) with its own before resuming its execution. Other fileless threats use or load their malware from the system’s random-access memory (RAM), which stores data and code being currently used. While this could allow threats that use it to evade traditional AV detection, it is removed as soon as the computer is rebooted.
There’s no bulletproof way to detect and prevent attacks that use in-memory exploits. Defense in depth — or a multilayered approach to security — is important. Keep the system and its applications updated; secure the use of system administration tools; and deploy additional layers of security such as behavior monitoring, sandboxing, firewalls, and intrusion detection and prevention systems.
More importantly, proactively monitor the endpoints and networks. Fileless threats may not be as visible as other malware, but they can also leave telltale signs that IT and security teams could watch out for, such as suspicious network traffic (for C&C communication and data exfiltration). For example, Trend Micro’s custom sandbox integrated in Deep Discovery™ via Deep Discovery Analyzer, Deep Security™, and OfficeScan™ can intercept APIs and check for code strings meant to execute a malware’s evasion technique or routines.
Installing malware via script-based attacks
Fileless threats rely on scripts whose shellcodes or binaries are obfuscated, compiled, or embedded so that they don’t create files on the disk. This lets them interact or affect the system’s operating system or applications while making it difficult for traditional AV software to detect. Script-based attacks are also versatile, since they can be run from a file or directly on the command line (via PowerShell, WScript, JavaScript, VBScript, mshta, etc.). This flexibility is also what makes them more evasive. For example, a fileless threat can split how the scripts are invoked, or spread across different processes.
Script-based attacks use interpreted scripts (e.g., via PowerShell) to lead an arbitrary code execution. There are also malicious scripts designed to exploit vulnerabilities or design flaws in applications like Microsoft Office. Attackers, for instance, can remotely execute a script in memory to bypass endpoint-based security. This has been the technique of choice for many malware delivered filelessly, such as KOVTER, POWMET, and FAREIT.
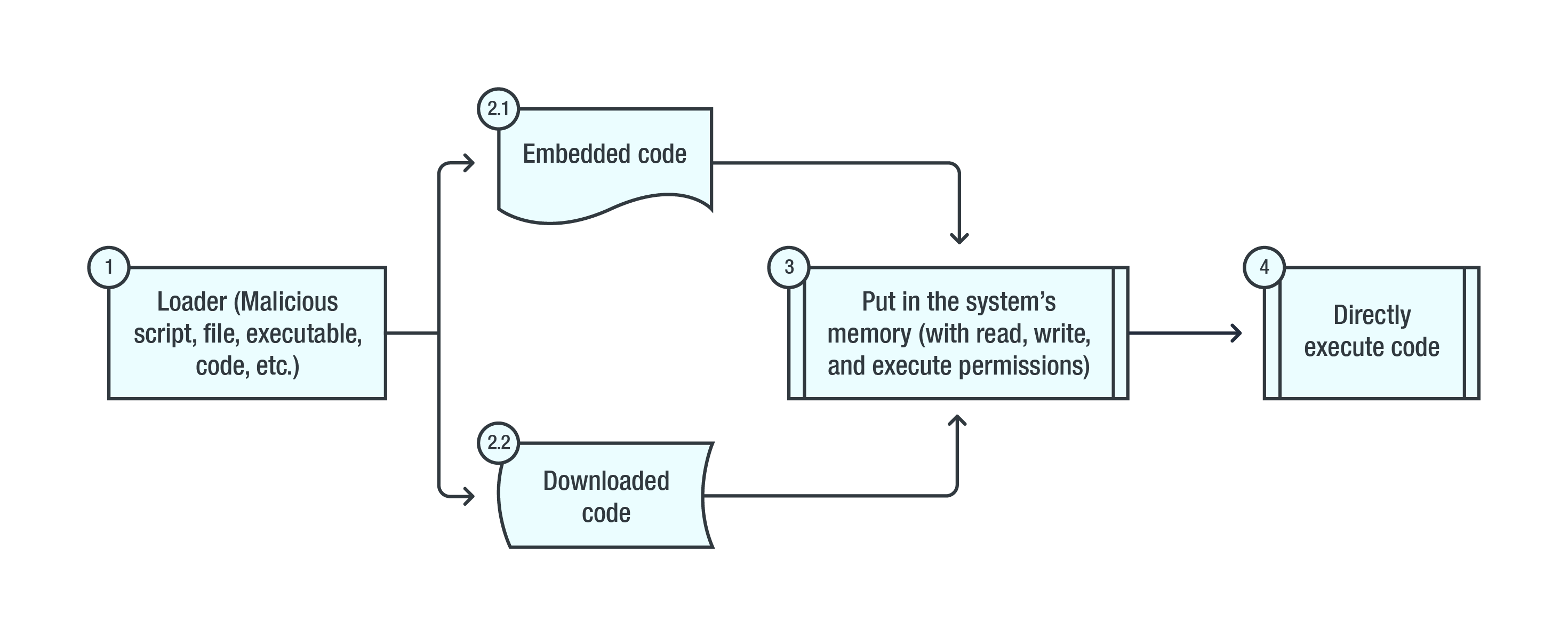 An infection chain of a script-based attack that abuses PowerShell
An infection chain of a script-based attack that abuses PowerShell
Many fileless threats particularly abuse PowerShell because of its flexibility and accessibility. It’s a built-in feature on many Windows operating systems, and, in the case of its open-source iteration (PowerShell Core), multiplatform. PowerShell is also capable of accessing APIs that execute important system and application functions as well as OS objects. And since it has no native executable on the disk, it can be abused to filelessly retrieve and deliver payloads or execute other malicious commands.
Users and especially businesses can reduce their exposure to script-based attacks by enforcing the principle of least privilege. Restrict, harden, and secure the use of system administration tools. For example, PowerShell itself has security mechanisms that can help further analyze anomalous behavior; it can also be configured to detect arguments/commands typically used by malware. Disable or delete outdated third-party plugins and components that may be used as entry points into the system.
Implementing behavior monitoring also helps by monitoring and blocking anomalous behaviors and routines associated with malware, like how a hijacked process would invoke Command Prompt to execute a PowerShell script. Trend Micro endpoint solutions such as Trend Micro™ Security, OfficeScan, and Worry-Free Business Security all include behavior monitoring to detect script-based, fileless malware. This helps organizations look out for malicious behavior and block the malware before the behavior is executed or performed. OfficeScan can also include a device control feature that can prevent removable media such as USB and optical drives from being accessed, preventing them to be vectors to fileless malware.
Installing malware by abusing IT and sysadmin tools
Fileless threats “live off the land,” or abuse features as well as system administration tools and utilities, mainly those built in into the system. A recent real-life example is how attackers use a combination of Windows management interface command (WMIC) and CertUtil — both of which are legitimate system utilities — to install an information stealer.
Profit- and cyberespionage-driven attacks also abuse command-line utilities like Microsoft Register Server (regsvr32) to load and execute malicious DLLs, or install modified versions of penetration testing tools (i.e., Cobalt Strike) to further compromise the system.
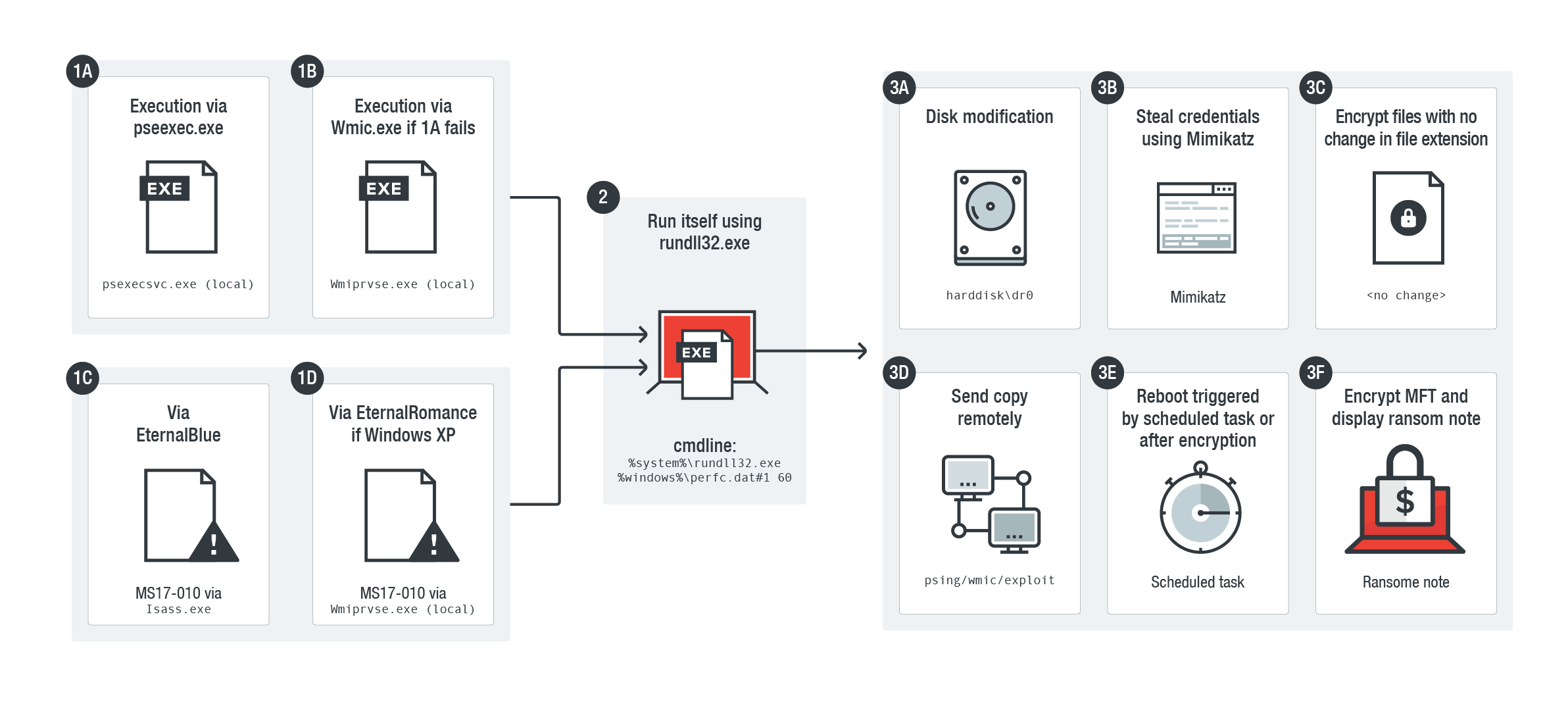
Infection of the Petya/NotPetya ransomware, which abuses various tools to encrypt files stored in an infected system and overwrite its disk
Abusing these tools provide fileless threats with jump-off points in their attack chains rather than using compiled executables. They can also misuse these tools to retrieve payloads, download, or launch additional malware, steal and exfiltrate data, retain persistence, and move laterally. And since these threats piggyback on legitimate tools, they can be difficult to detect. Some of the notably abused tools include command-line interfaces (PowerShell, Command Prompt, regsvr32, rundll32, WMIC, Bitsadmin, CertUtil, and msiexec), remote desktops, and third-party penetration testing tools like Cobalt Strike and Mimikatz.
Many applications have built-in command-line utilities to make them easier to update; developers and programmers are recommended to apply security by design. Enforce access policies and enable them only when needed. Secure the use of remote administration tools. Security mechanisms like application control helps by allowing only the execution of whitelisted applications or tools. For threats that abuse legitimate tools, behavior monitoring helps by thwarting malware-related routines.
Maintaining persistence with fileless techniques
Once malware gains a foothold in the endpoint, network, or server, it typically tries to remain there for as long as possible even after they are rebooted. Fileless threats use different and unique techniques to establish persistence, mainly by creating load points where the payloads can be restarted. These techniques also abuse built-in Windows tools and utilities.
A common persistence mechanism is to store malicious code or files in the system’s registry, which is mainly used in storing the configuration data and settings as well as file associations of applications. By storing malicious code in the registry keys, threats can be filelessly extracted, run, or executed when the system starts, or if certain files like shortcuts are clicked. A real-life example is the fileless version of the click fraud malware KOVTER. It creates registry entries containing malicious codes that will be decoded and injected by PowerShell into a spawned legitimate process.
Infection chain of a fileless cryptocurrency-mining malware that abuses PowerShell and WMI
Another technique for maintaining persistence is abusing tools like Windows Task Scheduler, which enables programs and scripted to be launched at a predetermined time. In a fileless malware’s case, scheduled tasks are created in order to trigger its execution. This technique is also used by other kinds of malware, such as certain kinds of information-stealing trojans and point-of-sale (PoS) malware to bypass traditional sandboxing. Additionally, attackers can set these scheduled tasks to recur and create registry entries to automatically reinfect the system.
More recently, attackers are abusing WMI to maintain persistence. WMI is used for managing devices and systems connected to a network. In cybercriminal hands, it can be used for lateral movement, code execution, and persistence. Typically, fileless threats will use WMI’s repository to store malicious scripts that are then invoked using WMI’s own functions. This include: WmiPrvSE (WMI Provider Host/Service), which provides management information; Scrcons (WMI Standard Event Consumer), a scripting application used to execute WMI scripts; and Wmic (WMI Command Line), a commandline utility used to allow objects to interact with WMI. Certain iterations of cryptocurrency-mining malware abuse WMI as its persistence mechanism.
Proactively monitoring endpoints and networks they are connected to helps reduce further exposure or reinfection. For example, system administrators as well as IT and security teams can use Microsoft’s Autoruns tool to examine registry keys and spot malicious entries. WMI’s own functions — specifically WMI event queries — can be used to detect and prevent its abuse. PowerShell has similar capabilities to harden systems or detect malware-related routines.
Trend Micro’s Smart Protection Suites deliver several capabilities like high-fidelity machine learning, web reputation services, behavior monitoring, and application control that minimize the impact of persistent, fileless threats. Trend Micro Endpoint Sensor, for instance, monitors events related to WMI to help quickly examine what processes or events are triggering malicious activity.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Artículos Recientes
- MCP Security: Network-Exposed Servers Are Backdoors to Your Private Data
- Email Threat Landscape Report: Evolving Threats in Email-Based Attacks
- Deepfake It ‘til You Make It: A Comprehensive View of the New AI Criminal Toolset
- Proactive Security: The Role of Exposure Management and Detection-Response Capability
- The Trend Micro Underground Series
 Email Threat Landscape Report: Evolving Threats in Email-Based Attacks
Email Threat Landscape Report: Evolving Threats in Email-Based Attacks AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™
AI in the Crosshairs: Understanding and Detecting Attacks on AWS AI Services with Trend Vision One™ Trend 2025 Cyber Risk Report
Trend 2025 Cyber Risk Report The Road to Agentic AI: Defining a New Paradigm for Technology and Cybersecurity
The Road to Agentic AI: Defining a New Paradigm for Technology and Cybersecurity