What You Need To Know About Tax Scams
 View Infographic: What You Need To Know About Tax Scams
View Infographic: What You Need To Know About Tax Scams
April 15 marks the Internal Revenue Service’s (IRS) tax filing deadline for 2019. While many taxpayers are rushing to file their returns, cybercriminals are also preparing to cash in on the tax season. Fraudsters and cybercriminals use the tax season as a social engineering lure to deceive people into unwittingly handing out credentials, money, and personally identifiable information (PII).
[READ: What Do Hackers Do with Your Stolen Identity?]
Many cybercriminals also use the tax season to deliver threats like ransomware, spyware, and banking trojans. Others use fake IRS phone calls and online services to trick taxpayers into sending money to fraudster-owned accounts. In fact, fake IRS calls reportedly cost 12,000 victims US$63 million in losses in 2018.
Here’s what you need to know about tax scams and what you should look out for to avoid them.
[Trend Micro Research: Behind Tax Fraud: A Profile of IRS Scammers]
How IRS Tax Fraud Works
IRS tax scams typically begin with a spam email posing as the IRS. These spam emails can redirect unsuspecting users to phishing- and malware-ridden sites. They can also come with malicious attachments such as spyware, backdoor or banking malware, and remote access trojans impersonating legitimate files. These threats are designed to steal the unwitting user’s PII, which an attacker can then use to access the victim’s accounts or sell in underground marketplaces.
[BEST PRACTICES: Identifying and Mitigating Phishing Attacks]
These threats became so prevalent that, in 2004, the IRS came up with a list: the Dirty Dozen. Compiled annually, the Dirty Dozen list details the most common scams to help protect taxpayers. Here are the IRS’ Dirty Dozen for 2019:
- Phishing. Emails claiming to be from the IRS, typically promising recipients with sizeable tax refunds or threatening them with legal action. Variations of these schemes include hijacking a victim’s personal bank account, filing fraudulent tax returns, and then asking the taxpayer to refund the money by posing as a collection agency or the IRS. Other phishing schemes also target employee financial information (e.g. Form W-2 data).
- Phone Scams. Unsolicited phone calls claiming to be from the IRS intimidating victims with legal action to coerce victims into paying a fake tax bill. These scams also include the so-called “robocall,” a text-to-speech recorded voicemail that directs victims to contact a specific number.
- Identity Theft. Tax-related identity theft schemes entail scammers using stolen Social Security or Individual Taxpayer Identification numbers to claim tax returns or refunds. Other cybercriminals target businesses by illicitly filing corporate income tax returns using stolen identities.
- Return Preparer Fraud. This type of fraud involves tax professionals/preparers filing false income tax returns. This includes claiming inflated or excessive credits, expenses, deductions, and exemptions, sometimes without the taxpayer’s knowledge.
- Inflated Refund Claims. Scammers lure taxpayers by promising fictitious and overstated credits, rebates, or benefits. Some fraudsters use fake forms (e.g., W-2 or Form 1099) that improperly report taxable income.
- Falsifying Income to Claim Credits. Like inflating refunds, this kind of fraud involves reporting made-up income to increase refundable tax credits. Variations of this fraud include scammers conning taxpayers into signing fake forms in order to claim a refund.
- Falsely Padding Deductions on Returns. This entails exaggerating deductions such as charitable donations, medical and business expenses, as well as falsely claiming tax benefits.
- Fake Charities. Fraudsters set up fake charities then deceive unsuspecting taxpayers into making donations or giving out their PII, luring them with tax incentives.
- Excessive Claims for Business Credits. These entail improperly claiming expenses for activities that are not qualified or eligible for a research credit. The IRS also saw fraudulent tax return preparers ensnaring taxpayers into inflating refunds by claiming a fuel tax credit, which is restricted to the use of off-highway vehicles.
- Offshore Tax Avoidance. This encompasses hiding income in offshore accounts to evade taxes.
- Frivolous Tax Arguments. This scheme uses dubious and exorbitant legal claims to avoid paying taxes. The IRS provides a list of some of the most common frivolous arguments used.
- Abusive Tax Shelters. These schemes attempt to hide ownership of income and assets by abusing trust arrangements, captive insurance companies, and conservation easements to avoid tax, reduce insurance costs, and claim deductions.
[RELATED NEWS: Stolen W-2 Forms Leaves Stanford University Employees Vulnerable to Fraud]
Examples of tax-related email scams:
Many of the socially engineered, tax-related spam emails we saw affected victims in countries such as the U.S., Australia, New Zealand, and the U.K. the most. Here are some of samples of tax fraud emails:
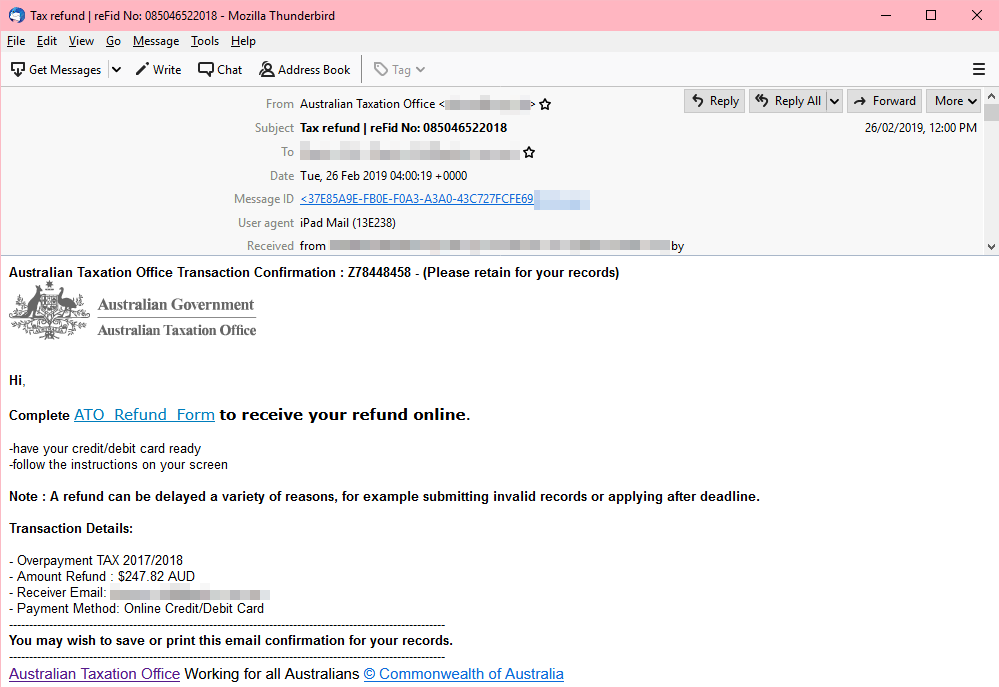
ATO Refund Email and Fake Tax Certificate
This socially engineered spam email pretends to be a refund notification from the Australian Tax Office (ATO), saying that the recipient is eligible for a hefty refund. It instructs the user to open the attached archive and extract the files in their system to get the refund.
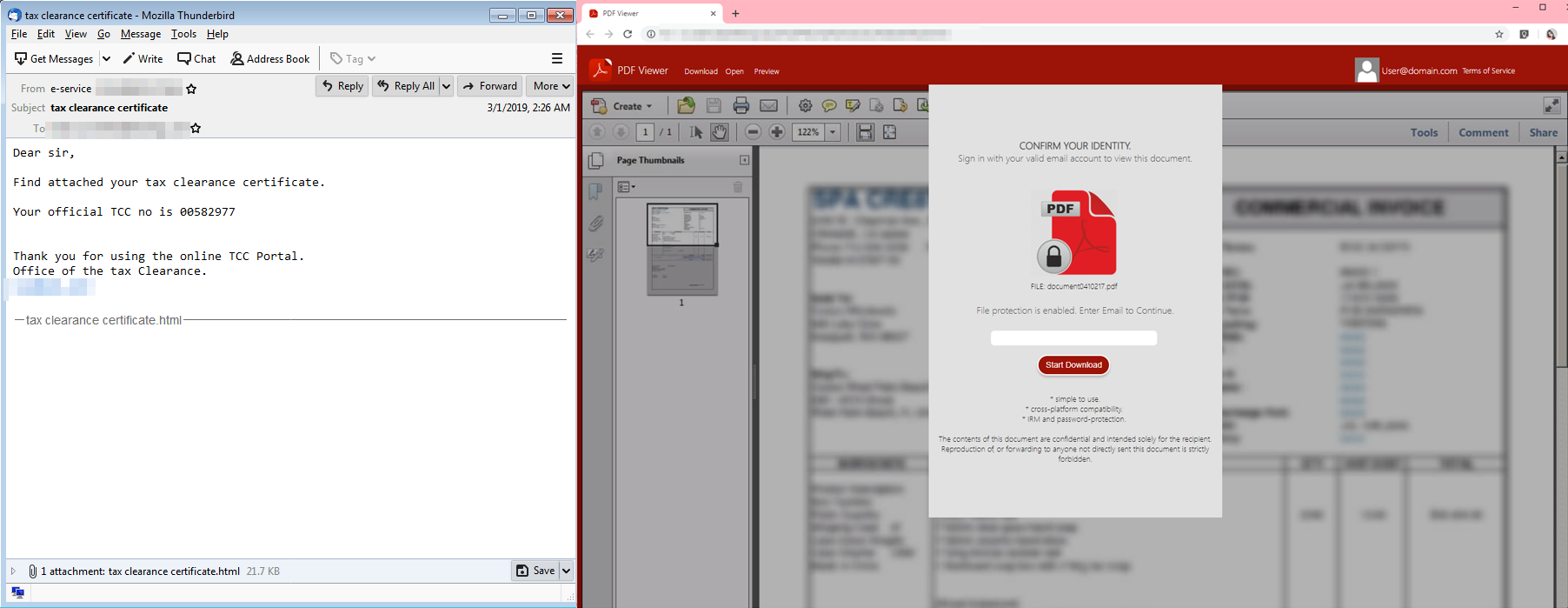
This phishing email, pretending to be from the IRS, urges the recipient to open the HTML file attachment. Upon opening the file, it displays a fake Adobe Reader log-in prompt and tricks the user into entering their credentials in order to download the supposed tax clearance certificate.
[READ: Post-Tax Season Spam Campaign Delivers URSNIF to North American Taxpayers]
IRS Tax Exemption Notification
The keywords used in this phishing email sample uses “Tax Exemption Notification” as the email subject. To appear legitimate, the email body contains an image banner of the IRS. The message tells the recipient that he is exempted from reporting and is eligible for other financial benefits. The sender pretends to assist the recipient, but in reality, the cybercriminal behind this scam is phishing for information by urging the user to give out sensitive information by completing the fake W-8BEN form in the attached PDF file.
[Interactive: How Much Personal Information is Worth in the Cybercriminal Underground]
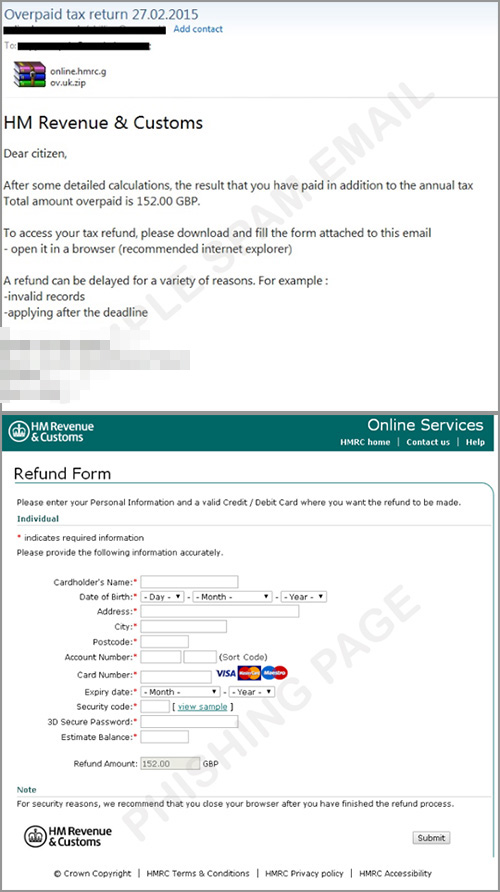
Refund from HMRC
This tax-related scam appears to come from HM Revenue and Customs, a British government institution. It tricks users into opening the message by using the subject “tax refund.” This email invites users to download the attached form, which then loads a phishing page that captures information.
[Security 101: Business Email Compromise and Tax-Related Threats]
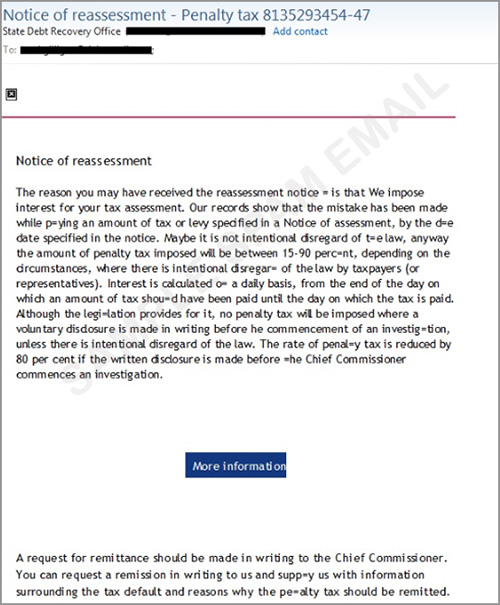
Scare Tactic Leads to Ransomware
Ransomware operators also take advantage of taxpayers in Australia and New Zealand by sending spam emails using “penalty tax” in its subject heading. The “More Information” button takes users to a landing page while a file-encrypting malware is downloaded to the victim’s system. The IRS regularly issues scam alerts so taxpayers can avoid them.
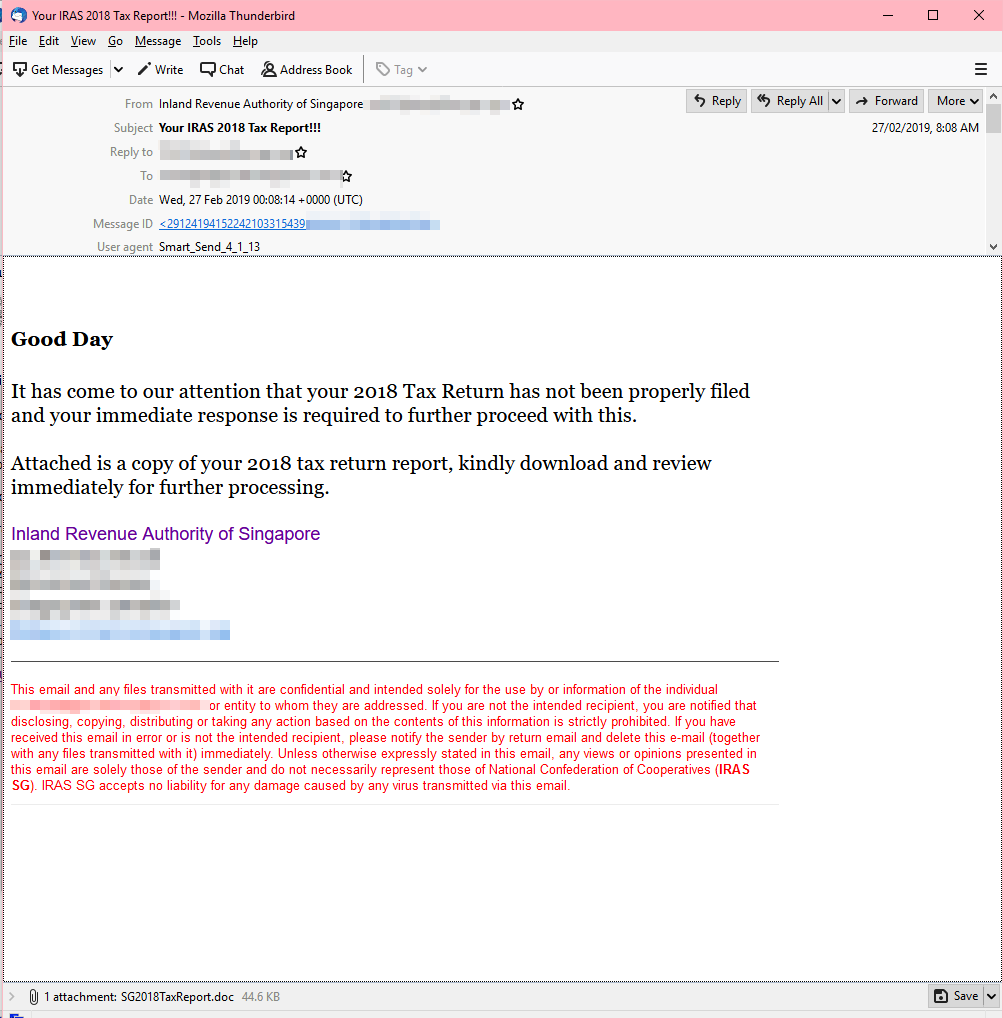
This spam email pretends to be from the Inland Revenue Authority of Singapore (IRAS), notifying that the user’s tax return wasn’t properly filed. It prods the taxpayer to download and open an attachment disguised as a tax return report. The file has malicious macro code that delivers a trojan downloader.
[READ: Why Scammers Want Your Tax Returns — and How to Stop Them]
How to avoid tax scams
Taxpayers and businesses should exercise caution. Never open links or attachments that come from unexpected or suspicious senders, especially when they claim to be from officials or agents of government organizations. Unsolicited email from an IRS-related component such as Electronic Federal Tax Payment System (EFTPS) should be immediately reported to the IRS via phishing@irs.gov.
It also helps to stay abreast of the latest security threats and use the latest security technologies such as Trend Micro™ Security, Smart Protection Suites, and Worry-Free™ Business Security, which can effectively block access to malicious sites and spam email as well as detect malware. Businesses can also take advantage of Trend Micro’s Phish Insight, which provides free interactive and educational resources to reinforce the workplace’s posture against phishing.
[Avoiding Phishing Scams: How Phishing Leads to Hacked Accounts and Identity Theft]
To help taxpayers avoid IRS scams, here are the things that the IRS will never do:
- Call and demand immediate payment or call about taxes owed without first having sent a bill.
- Initiate contact by email to request personal or financial information.
- Demand tax payment without giving you the opportunity to question or verify the owed amount.
- Ask you to give out credit and debit card information over the phone or email.
- Require you to use a specific payment method, such as a prepaid debit card, to pay your taxes.
- Threaten to bring law enforcement to have you arrested for not paying.
Read more about tax scams in our infographic, “Tax Scams: How They Work and How to Avoid Them.”
Trend Micro Solutions
The Trend Micro™ Security, Smart Protection Suites, and Worry-Free™ Business Security solutions provide comprehensive multi-device protection against threats by identifying and blocking malware and malicious links on websites and in social networks, emails, and instant messages to shielding privacy and guard against identity theft. These solutions are powered by Trend Micro XGen™ security, which provides a cross-generational blend of threat defense techniques against a full range of threats for data centers, cloud environments, networks, and endpoints.

Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Artículos Recientes
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines


 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One