Estimating Future Risk Outbreaks at Scale in Real-World Deployments
By Marco Balduzzi, Roel Reyes, Jessica Balaquit, Ryan Flores, and Benjamin Zigh
To protect organizations against cyberattacks, the industry has introduced several security solutions over the years, with endpoint detection and response (EDR) playing a central role in defending against outbreaks. This involves detecting the presence of malicious software on an endpoint, such as upon download, and triggering a detection and response process. While these solutions, especially when combined in unified extended detection and response (XDR) platforms, provide a comprehensive strategy against cyberattacks, there remains the shortfall that they employ a reactive approach. Anti-malware, anti-spam, web application firewalls, intrusion detection systems, and similar security protocols all operate by waiting for evidence of an attack (i.e., detected by a signature) before triggering an alert or initiating remediation.
While this is effective in most cases, the evolution of cyberattacks and cybercrime demands that organizations also strategically plan its defense: A proactive approach anticipates potential outbreaks and stays ahead of future attacks.
To overcome these limitations, we researched and developed a novel solution that leverages behavioral user data to estimate the risk of future incidents. Using a combination of AI techniques, we pinpointed machines that had been at risk of specific malware class outbreaks.
Our work was presented on Nov. 6, 2025, by our team at APWG’s eCrime Conference in San Diego, California, USA, and published as an IEEE publication titled “Beaver: Estimating Future Risks at Scale in Real-World Deployments.” A copy of the paper can be downloaded here.
In our research, we build upon our previous study and introduce a system that estimates the risk of future malware outbreaks. Our system not only forecasts potential outbreaks within the next 30 days but also provides a breakdown of the risk probabilities by malware class. Additionally, it offers explainable reasoning behind these predictions.
We analyzed 10.7 million endpoints across 217 countries and 822 organizations over a period of one month (January 2025). The majority of these machines were situated in very large enterprises consisting of networks used for business purposes, including regular desktop computers for day-to-day office tasks, high-end machines for specialized operations, and servers. Cumulative results were drawn to derive key threat information to foster product innovation and competitive advantage.
The results of our research provide insights such as that visiting gambling websites poses users twice the risk of coinminers and that ransomware becomes a major threat for users who download a large variety of software applications. Additionally, we discuss in our research the behaviors that put organizations at risk and the categories of endpoints that are most vulnerable to specific classes of malware.
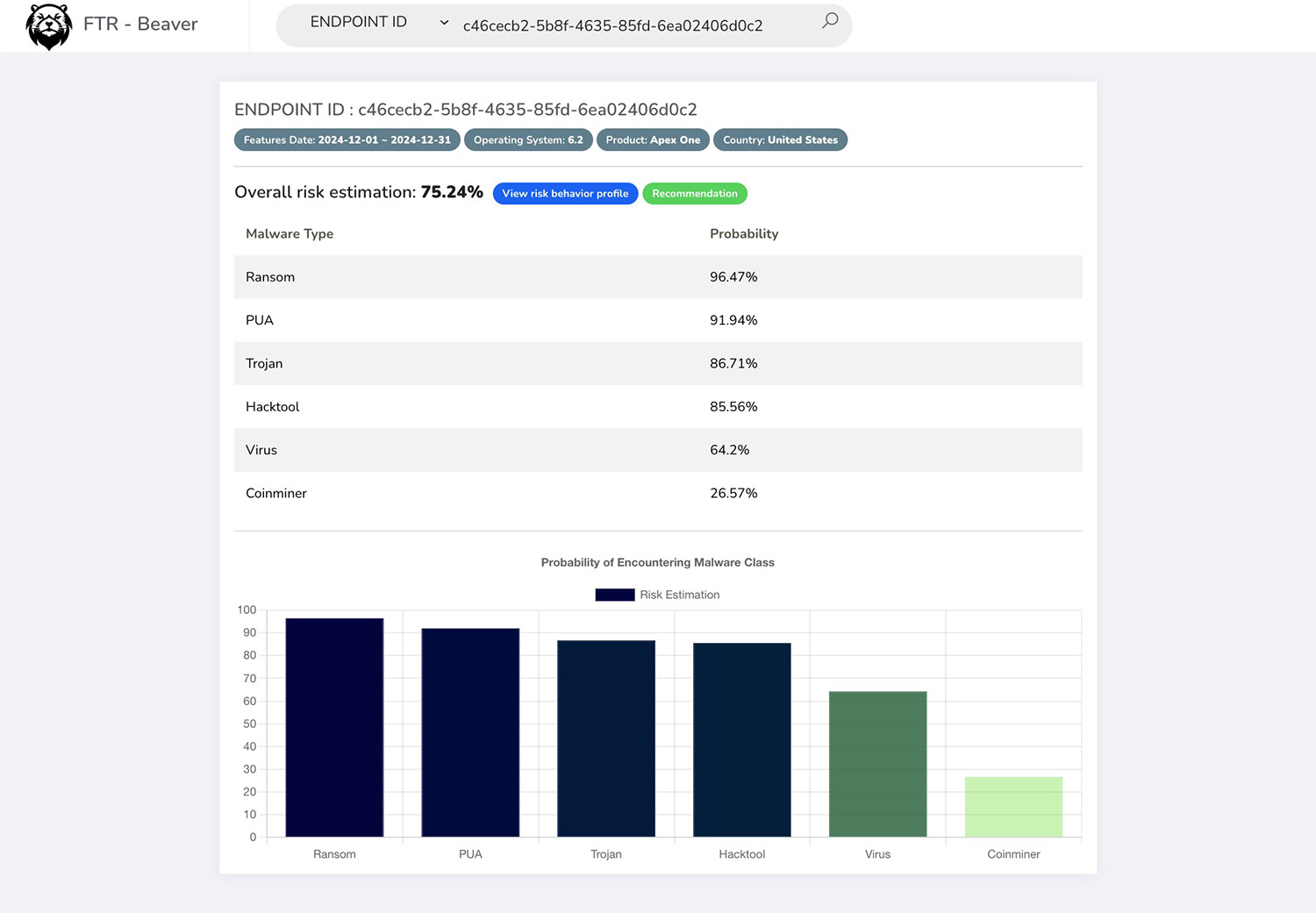
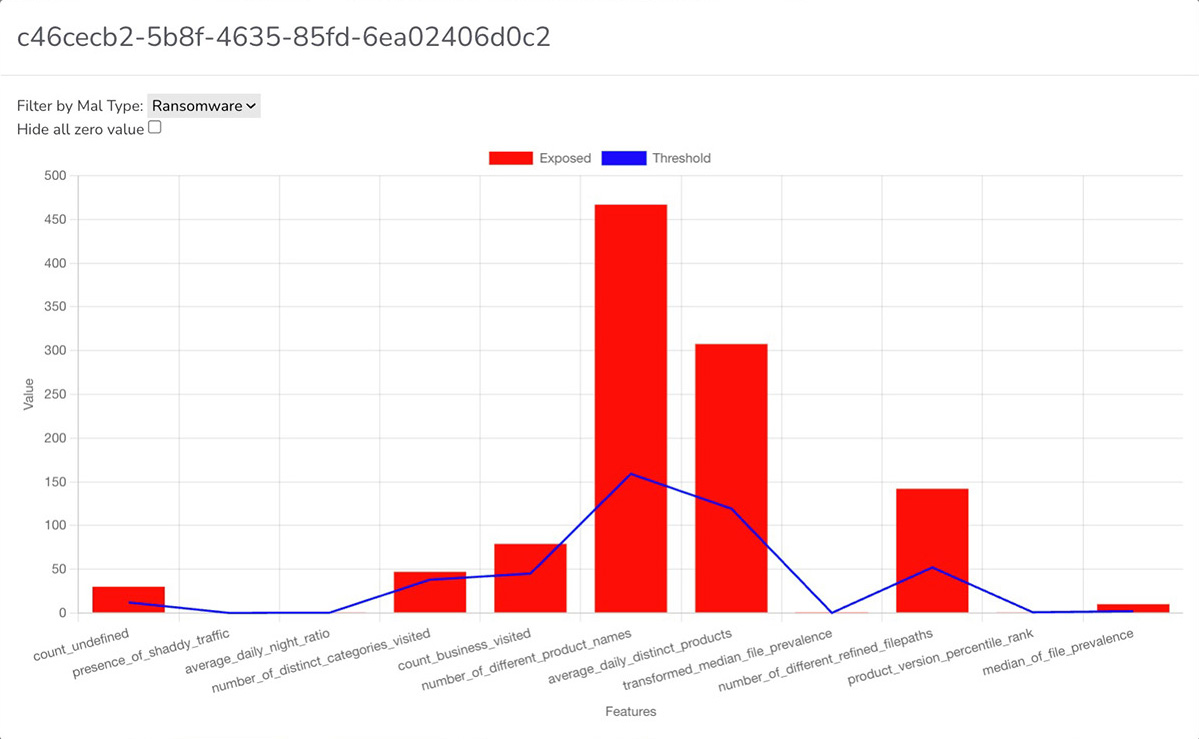
Figure 1. A screenshot from our solution that shows an example of a risk estimation for endpoint c46cecb2-5b8f-4635-85fd-6ea02406d0c2, and contributing features for malware class “ransomware”
This work represents a key foundation for predicting the risk of future cyberattack incidents, which is the main principle of Trend Micro’s Cyber Risk Exposure Management (CREM). We will soon release a more comprehensive paper on this subject, including major details on this area of research that we are actively exploring in our organization.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Artículos Recientes
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering


 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One