The Crypto-Monetized Web: A Forward-Looking Thought Experiment

Attack scenarios

Conclusion
By David Sancho
In past decades, we have seen how the web has drastically evolved. From the static, read-only version of Web 1.0 (to which this page harks back design-wise), we have witnessed its transformation to its present mode as the dynamic, interactive, and content-creator-driven iteration that is Web 2.0.
This is evident in the popularity of sites and apps that allow creators to make content for the benefit of their followers. If they create popular content and amass enough followers, such content can be made in exchange for monetary value through advertisements and sponsorships.
Today, we see a glimpse of a possible iteration of the internet — one that combines the powers of blockchain technology, cryptocurrencies, and content creators. We have dubbed this iteration as the crypto-monetized web (CMW), a new conception of the web wherein each user account has a corresponding reputation in terms of cryptocurrency. Depending on a user’s social interactions, such as the sharing of ideas and content as well as the popularity and engagement such content drums up, their reputation score’s monetary value can go up or down.
Read more >>In this new web paradigm, users can also invest in content creators as if they were commodities being traded in the stock market. Investing early in an up-and-coming content creator helps raise that creator’s social value, and as their value continues to rise, so will the rewards that can be reaped by their supporters. In fact, there are already websites that work like this, serving as further proofs of concept.
A crypto-monetized version of the web can be complex, especially since it will involve cryptocurrencies, social interactions, and a threat landscape that will likely be different from one we are currently familiar with. In this forward-looking thought experiment, we analyze how the criminal landscape could change if this CMW ever materialized as an environment where every user account automatically has a dollar tag attached to it. In the following sections of this report where we elaborate on attack scenarios, we also discuss the possibility of malicious actors favoring some attack types and new attack methods in the future CMW landscape.
- 1
 The need for a new web and monetization strategies
The need for a new web and monetization strategies - 2
 The main features and concepts of the crypto-monetized web
The main features and concepts of the crypto-monetized web - 3
 How the CMW differs from non-fungible tokens (NFTs)
How the CMW differs from non-fungible tokens (NFTs) - 4
 Attack scenarios
Attack scenarios - 5
 What could be on the blockchain in the future?
What could be on the blockchain in the future? - 6
 Conclusion
Conclusion
Watch our video on the crypto-monetized web:
The need for a new web and monetization strategies
Blockchain technology powers and secures cryptocurrencies or decentralized and encrypted digital currencies. With the advent of both landscapes, many other related concepts that aim to create new services and ways to experience the internet have been put forward, one of which is the concept of the CMW.
Today’s world wide web needs strategies for the diversification of monetization. As a result, the possibility of the CMW becoming part of our virtual lives is high. Currently, the main method to monetize websites is through advertisements, which accounted for US$378.16 billion in worldwide spending in 2020 — an amount that is close to Israel’s GDP in the same year. However, it’s important to note that according to a 2020 HubSpot study, users have an adverse attitude toward ads, specifically toward pop-up and mobile ads. Hence, finding and adding a new method of online monetization makes sense for both businesses and content creators.
It’s important to bear in mind that the CMW idea is an addition to rather than a replacement for digital advertising, where content consumers can be shown ads until they buy into the user reputation idea. This means that for ads to be turned off for users, they must first invest money in a creator. Once they do this, one possibility is that they will receive more targeted ads, or at least ads that are closer to the area of interest that they invested in. Similarly, popular creators will continue to recommend and advertise products to their audience. This strategy has already proven to be quite successful: One report shares that 49% of consumers follow influencer recommendations.
The main features and concepts of the crypto-monetized web
The concept of the CMW is related to Web3 or Web 3.0, but they are not the same. Web3 is a more generic vision of a decentralized and more machine-readable or semantic web. Even though the CMW also focuses on decentralization, in its landscape, every user has a monetary value in cryptocurrency. Users can spend currency on creators, causing their reputation value to go up. Naturally, as a content creator’s coin value goes up, so does a user’s investment. This user’s online reputation thus effectively becomes a tradable good, similar to company stock.
One of the best examples of such an implementation is BitClout, a Twitter-like social platform that has implemented a reputation system. Figure 1 shows the profile of a user named “@elonmusk,” though there is no confirmation that this has been certified as the official BitClout account of Elon Musk himself.
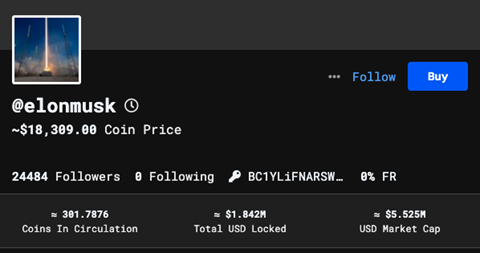
Figure 1. A Bitclout user profile taken on Jan. 18, 2022
It’s important to note that this user’s coin price is at 18,309 decentralized social tokens or DESO (formerly known as BitClout coins). If a different user wanted to invest in @elonmusk as a content creator, that user would need to buy DESO on a cryptocurrency exchange, and then spend them on @elonmusk’s coins by using the “buy” button as seen in Figure 1. This would immediately increase the content creator’s coin price. Future CMW implementations will likely make this process even easier. Although BitClout has already published a white paper that discusses the platform’s features, this implementation of the platform might still change should mainstream social media sites decide to buy into this web concept.
To be clear, a user need not invest in people or even get DESO coins to be on the BitClout platform; a user can use the platform without spending any money on it. However, if a user is a consumer of information, at some point they might want to reward the content creators that they follow and whose content they value. However, the desire to reward a creator for their content goes beyond having a personal preference for such content; users might also want to reward a content creator because they, as a user, understand that they too can profit by investing in good content creators. It’s also of interest to note that in a way, investing in a content creator can create the feeling of the investor being brought closer to their chosen content creator, in the same way that being retweeted by a popular influencer or becoming a patron of a preferred artist or writer gives one the feeling of being closer to them.
Content creators can also reward their top investors with certain perks, a way of sharing content that has already proven to be effective in patronage sites such as Patreon.
Now is a good time to outline how content creators make money on the current web paradigm. If content creators manage to grow audiences that are interested in the content that they’re posting on their social media platforms, they can make money by through any of the following means:

Creating and uploading videos on a YouTube channel. YouTube pays creators who are part of the YouTube Partner Program via ad revenue, YouTube premium fee, channel membership, YouTube Shorts fund eligibility and participation, Super Chat, and Super Stickers.

Creating content on a fan site. Patreon and OnlyFans are common choices for such sites. Instagram also debuted its own Subscriptions model in 2020, which aims to help “creators build sustainable businesses powered by the support of their communities.” Users who become patrons are usually able to unlock exclusive content, as well as get mentioned publicly on a content creator’s video or other forms of content.

Creating content on a pay-per-access website. This is like a private club where a creator builds a website and makes content available behind a paywall. One downside to this option is that it can be expensive and cumbersome to run.

Getting sponsorships. A sponsor usually pays a creator per mention of their goods or services. A sponsor can also give a creator a unique discount code that the creator can inform their audiences of and from which the creator can receive a sales percentage.

Driving traffic to a YouTube or Patreon account, or even a private site from other social media sites. Instagram and Tiktok are the two sites most often used for this option.
In the CMW paradigm, in addition to all of the aforementioned monetization plans, content creators also earn money by selling their own digital currency, albeit this drives their own coin price down. More importantly, this means that the system has a built-in incentive to encourage the creation of high-quality content.
It is also possible for a user to invest in a creator’s coins purely because of their potential to become more valuable, and not because the user agrees with that creator’s ideas or opinions. This type of user or speculator behavior is a reality that can happen in any economy. Barring this possibility, in general content creators and consumers receive specific benefits in this new web paradigm:
Content creators gain... | Content consumers gain... |
Closeness to their audience | A chance to invest in their favorite creators |
Monetization handled by the platform itself | An opportunity to give donations easily by upvoting content |
A predictable revenue stream | Possible perks from a content creator |
Motivation to deliver great content | A way to encourage great content |
It’s important to note how all these features can be similarly applied to patronage sites like Patreon. In fact, the CMW offers an embedded way to support creators within the platform itself, without any need for external systems.
Let’s try to illustrate features on both the current web and CMW paradigms with an example.
In the current web paradigm, Eric is a skateboarder from New York. He typically creates skateboarding tutorial videos in English, but he also shares videos of him doing impressive tricks for his followers to watch. One day, Eric wakes up to find his alerts going crazy from thousands of likes and shares of a video he posted on YouTube just before going to bed. The video has gone viral in Asia overnight, vastly outstripping Eric’s normal viewership. He has even started earning from ad revenues on his video and garnered more subscribers from Asia.
Let’s place the same story in the CMW paradigm. When Eric’s video went viral overnight, on top of earning ad revenue and garnering new subscribers, a large percentage of the Asian viewers who watched, liked, and shared his video chose to invest in him because he’s a potential rising star in the skateboarding world. This has a direct impact on Eric’s coin value. In such a scenario, content creators can therefore shift their concentration to creating an environment where a higher percentage of their content is a viral hit. Meanwhile, the platform itself will take care of collecting that value for them.
This scenario might soon become a reality, as there is already a groundswell of companies interested in shifting to this direction. The following is a list of websites that promise to deliver a similar experience as their current web functionalities, but with a decentralized reputation built into them:
Current Web | Crypto-Monetized Web |
Medium | |
Spotify | |
YouTube | |
Privi | |
NFT storage |
Some leverage common cryptocurrencies like Ethereum, while others have their own dedicated currencies such as BitClout’s DESO or Audius’ AUDIO. Indeed, there is already significant interest from early adopters of this emerging trend; according to Coinbase, as of Jan. 20, 2022, these coins have a market cap of US$448 and US$584 million, respectively.
The future might or might not be exactly like BitClout, but looking at how this platform operates is a good place to start understanding the concept of the CMW. In the same future, it’s also possible that a tech giant like Google, Facebook, or Twitter will acquire or license BitClout, or even start developing their own version of the CMW from scratch.
The CMW model is interesting because it could be a way for these social media sites to complement advertisement-based business models. A social media company could receive a small fee for each cryptocurrency transaction via the CMW model while also earning money from an advertisement-based model. Both models are compatible, and a social media company can decide to complement their advertising revenue with other reputation-based revenue streams.
How the CMW differs from non-fungible tokens (NFTs)
If you’re wondering how the CMW concept is related to non-fungible tokens (NFTs), the answer is quite simple: It’s not. NFTs are digital assets whose properties are stored as URLs and are reflected on a blockchain. These URLs typically store digital assets such as songs, images, and artwork, and their exact hash can be used to identify them uniquely on a blockchain to point to their current owner. The blockchain also stores the whole history of ownership for each hash.
In the terms of the CMW, reputation is a different kind of asset. Since it can’t be represented by a single hash, the blockchain stores each user’s BitClout or equivalent value. The blockchain could also be used to store other user information, such as a user’s number of posts, number of followers, and creator coin balances. In short, it’s not advisable to confuse the CMW with NFTs. The involvement of cryptocurrencies in both the CMW and NFTs can be confusing, but they are not related. Unlike NFTs, reputation tracks something that is not easily reproducible by somebody other than the owner.
From a business perspective, what the increased interest in NFTs is telling us is that reputation as a tradable asset will probably garner the same kind of interest, if not more. Undeniably, there has been a recent surge of interest in this area as well as in investing in cryptocurrency-backed services. It follows, therefore, that on paper, this is an encouraging sign for web reputation technology as a successful concept.
Attack scenarios
With new technology comes new challenges, and the CMW landscape is no exception. In this section, we classify attacks according to categories. Some of these attacks draw on features of the CMW paradigm, which makes mitigating abuses more difficult.
Identity theft
Profile hijacking is instantly monetizable. If an attacker phishes a creator’s account or somehow manages to steal access to it, they can just sell away all the creator’s coins and obtain real cryptocurrency, which can be immediately exchanged for real money on an exchange site. Demonetizing an account, therefore, is a real possibility.
In the same vein, an enterprising criminal can utilize a stolen account to sell nonexistent items and products or promote links to a hijacked audience. Although this is already a possibility in the current Web 2.0 framework, a more invested audience in the CMW would likely be even more receptive to selecting such links or buying special offers.
From a criminal perspective, creating fake accounts and blowing up their value with a small amount of money might justify the investment if those accounts can be sold later on for more money than was initially invested. Those fake accounts can then be used to promote other users and products. These accounts can also be sold in bulk.
Needless to say, a user’s cryptocurrency wallet is the most obvious threat that can leave the user without any coins. And although this concern applies in any cryptocurrency scenario other than the CMW paradigm, we nonetheless believe that it is necessary to mention it briefly.
Fake content creation
The phenomenon of fake news has been around for a while now, and it has been known to alter people’s opinions on different issues for the benefit of an attacker’s nefarious agenda. In a CMW scenario, having loyal followers invested in a content creator’s opinion can be a powerful way of spreading false information. Once an attacker either manages to hijack a content creator’s account or amasses enough followers organically, they can have a powerful platform for catapulting fake news.
In a similar way, attackers can spread links to loyal audiences that they can either hijack or grow organically. These links can then lead to pages that can increase the search engine ranking of domains and act as some sort of search engine optimization (SEO) tactic. The content creator can create SEO doorways and sell user-clicks to others. There are also multiple ways of earning money on pay-per-click schemes that an attacker can use in such a scenario.
In fact, any scam that relies on a user’s gullibility can be amplified when there is a high bond of trust between content creators and their respective followers. Any hijacked account can then use this to seed fake “prize” messages or any such scams, which is what happened when an attacker hijacked Elon Musk’s official Twitter account to scam people into thinking that any Bitcoin amount they send over to a professional-looking website would be doubled in value.
Pump-and-dump schemes
Although the danger in this kind of scheme might already be known, it’s recommended to include a discussion here to anticipate how pump-and-dump schemes might be carried out in the CMW. If we think of user reputation the same way that we think of stock value in that such reputation also fluctuates depending on a user’s content, pump-and-dump schemes are an absolute possibility for attackers. Since a pump-and-dump scheme involves the manipulation of stock prices in order to maximize profit, a stock influencer or a group of investors can promote a particular stock, of which they already own a large volume, to inflate its price. While the stock price is high, they will share their stocks, causing the stock price to drop rapidly and leaving new investors with a much lower stock price.
The following are three possible pump-and-dump scheme options that an attacker can choose from to earn money illicitly:
- Promoting users. This first option is a legitimate feature that can be abused. If an attacker has enough followers, they can promote any other account that they previously invested in at a low price. After several rounds of promotion, the attacker can cash out. Ideally, the attacker has taken over an account with a big following, which can then be used to promote a second fake account or perhaps a regular user. As mentioned previously, this is not something that can be prevented as it is a legitimate feature that attackers simply misuse for their advantage. Another opportunity for attackers to earn profit is to sell reputation-boosting services in which clients can be done through hijacked accounts.
- Botnet boosting reputation. This second option is similar to the first, except that an attacker needs a botnet or many users at their disposal. The attacker instructs these users to purchase coins from an account that the attacker has previously invested in at a low price, causing the price go up substantially. Once the promoted account’s price is high enough, the attacker cashes out. There are two possible results of this:
- The bot accounts are actually low-value accounts that have been either stolen or hijacked. If this is the case, the attack is viable only if the stolen or hijacked bot accounts hold enough coins to purchase the victim account’s coin. This coin value will also increase as more and more bots purchase the victim’s coin. Zero-value dummy accounts would therefore not work for this attack.
- The bot accounts are dummy accounts created by the attacker. In this case, the attacker needs to invest enough money in each account to be able to purchase their victim’s coins. This attack also needs to be mathematically calculated so that the amount of money invested in each of the bots is smaller than the benefit or return of investment (ROI) of selling the victim’s coins. Even if the total benefit or ROI is small, the attack might be repeated as many times as necessary to make a fortune. Obviously, the way to counteract this is to design a system where this cannot be done. For example, the math behind the reputation systems needs to be complex enough to disallow these kinds of scams. Additionally, setting up cash-out time limits or requiring a minimum number of posts before cashing out is allowed might prevent this attack. It’s worth mentioning that this kind of automated attack would need an API, which a system like BitClout has. Any other serious implementation would also provide one such API in a similar manner.
- Promote and advertise. This third option is a variation of the first one. The idea here is to use a substantial number of followers to advertise products and collect earnings from the advertisers. This can also be combined with the aforementioned pump-and-dump scheme in a way that promotes a user account to be pumped while at the same time profiting from the promoted links being sent to this audience. As a last option, the account with a big audience can be sold to some other crook to continue profiting.
Selling accounts
The hijacking and selling of accounts to other crooks is a possibility, albeit an unlikely one. Selling an account would only be feasible if all account-related data were in the blockchain. This is unlikely, because if that premise were true, the social media company would never be able to recover or reset hacked and stolen accounts. The more likely scenario would be to grow an account organically, creating an audience that is receptive to what one has to say, and then to sell that account to a company that can keep creating content centered mostly on the brand. For example, an actor creates a few cooking accounts and starts sharing recipes. If one of those accounts takes off and starts attracting users, that account can be sold to an interested food company. The food company who then bought the account will use it to keep sharing recipes that will regularly use the company’s product in order to promote it. This is a legitimate feature of this reputation technology, but it can also be used to monetize those accounts that start getting an interested audience.
Data breaches
In this alternative future where monetary reputation is tied to an account, data breaches can be especially concerning. Right now, a data breach that consists of usernames and passwords (or perhaps password hashes) is disastrous because the user can see their account taken over by somebody else without any blame on the user’s part. In a reputation-based social media web paradigm, an account lost in this manner can also cause the loss of the account’s reputation and therefore the loss of monetary value. For an attacker, a data breach can bring high rewards, so malicious actors have much more incentive to break password hashes coming from data breaches, buy data from new unreleased breaches, or attack companies to breach data. To be clear, this is more of a threat to platforms who hold customer data than to content creators or consumers.
Money laundering
As in any virtual economy whose elements can be bought and sold, buying reputation can be a great way to invest in cryptocurrency — regardless of whether such cryptocurrency comes from legitimate sources — as well as to invest in other people’s reputation, only to sell these later on for profit. Since origin and destination wallets can be different, the ability to trace these movements would also be difficult, which can be a way to launder cryptocurrency and evade being tracked by law enforcement.
In a similar way, criminals can make payments for illegal goods and services with reputation scores. Child exploitation or human trafficking rings, for instance, could establish their communities and support one another via user reputation. This is something that needs to be policed early on in the development phase of these social networks to prevent it from becoming endemic.
Ransom demands
Once it has been established that a user account has a corresponding dollar value and is therefore a prime target for attack, once it is hijacked, the demanded ransom becomes a viable option to regain access to the account. The reason for this is that even a two- or three-day downtime can have a direct effect on revenue as the account’s followers are expecting the consistent delivery of content — otherwise, they might start looking for similar content elsewhere. Of course, the ransom needs to be only a fraction of what the hijacked account’s dollar amount is. The beauty of the reputation system is that it already assigns a price tag on user accounts, so there is no need to estimate or make up a value for a ransom.
In the CMW scenario, the basic demand for a ransom can be made more sophisticated by a hacker demanding that the victim pay up within a limited number of hours for them to get their account back. Otherwise, the hacker can pose as the victim and make a damaging post, such as a racist comment or a controversial political statement that would effectively lower the victim’s reputational score. Such problematic posts can cause the victim to be canceled online, meaning a drop in reputation score that directly equates to a loss in coin value. One could argue that it is not in the attacker’s interest to lower the value of a hijacked asset, but if threatening to do so would place more duress on the victim to pay the ransom, thereby increasing the probability of profit, then the malicious actor might consider it worth the risk.
Unfortunately, there is always the possibility of a malicious actor demonetizing a hijacked account despite receiving the ransom, and there’s no risk-free method for determining an attacker’s moral compass.
What could be on the blockchain in the future?
Under this new web paradigm, some data will live on the blockchain. Since this future has not been realized yet, however, we can’t know what data will be stored there, making it difficult to assess potential risks. If we imagine an extreme possible future where large amounts of our data as users will be made public, the scenarios we create there would then be strikingly different from other more conservative futures where only our usernames and the amount of cryptocurrency we own are stored on the blockchain.
On the other extreme side of the spectrum, people’s user data might be associated with who they are as individuals, thereby serving as their very own “society score.” This is, of course, if we envision a future where one’s good deeds are checked against the government services a person requires.
In this societal model, for example, an individual who volunteers in a soup kitchen would earn more points, and this would increase their children’s chances of enrolling in their school of choice. This system is reminiscent of a “Black Mirror” episode titled “Nosedive.” It’s interesting to note, however, that this type of system already exists outside of British science fiction: A social credit system is already in place in countries like China.
In this extreme, having a societal score on the blockchain could mean that stealing crypto-wallets or impersonating other users can have a great impact on the victims. Lowering or threatening to lower a victim’s score can also negatively affect a user’s quality of life.
In a more conservative future where only social media reputation and cryptocurrency balances are kept on the blockchain, the possibilities of risk are diminished but not totally eliminated. An increase in the additional data stored on the blockchain can therefore, in turn, increase the risk a user faces. This is something that future developers of this concept will want to consider when they design their “reputation on the blockchain” systems.
Conclusion
In a future where each user’s reputation fluctuates like a stock market price with a dollar value attached to it, attackers can find ways to subvert the system or make better use of age-old attacks. Although it is possible to hypothesize more far-fetched attack scenarios, in our experience, attackers tend to walk the path of least resistance by developing already successful attacks into more advanced versions that can work best in the new environment.
Currently, we don’t know for sure if this CMW paradigm is going to be realized, but if it does, we need to be prepared to counteract the resulting threats — and perhaps even to design systems that would prevent some of them from happening at all.
Clearly, user accounts in the future can be worth more than they are now. Similarly, the ways in which stolen or hijacked user accounts can be monetized can also be significantly easier and faster. On top of that, spreading fake content can be made more effective when the audience is monetarily invested in listening to content creators whose accounts, unbeknownst to the audience, have been hijacked. As a result of these, data breaches can be more interesting and beneficial for attackers than they are today. Pump-and-dump schemes might also appear as a strong option that attackers would gravitate toward.
Indeed, life in the CMW is not a walk in the park. Complying with taxation and revenue agencies will likely be difficult and can be a source of pushback for the whole concept. The idea of making money from the web and making revenue in cryptocurrency — which later on can be converted into Bitcoin and then transferred to smaller crypto wallets — is likely a good argument for governments everywhere to vote against the CMW paradigm.
The past failed attempts of social media companies to create cryptocurrencies can attest to this. It’s also possible that there will also be opposition to the CMW idea due to pseudo-gambling concerns. Because earning money is a main feature of the CMW alongside allowing users to bet on other users' popularity, it can be considered a form of gambling that could be detrimental to younger people's mental health and wallets.
Nevertheless, even if this future never comes to pass, performing a thought-experiment exercise such as this one will always put network defenders in a position of strength. Ultimately, whenever a similar piece of technology arises, defenders will always need to start thinking about how it would influence an attacker’s perspectives. At the end of the day, we believe that the attacks we have seen so far are the ones that bad guys will try to repeat and assimilate into new scenarios and landscapes. The security industry will thus inevitably need to look at these attacks under a new light. This is exactly what we have done in this forward-looking thought experiment, and we will strive to continue doing this whenever something new threatens to alter the status quo — just as we believe this social reputation paradigm might very well do.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Artículos Relacionados
- Probing the Activities of Cloud-Based Cryptocurrency-Mining Groups
- TeamTNT Activities Probed: Credential Theft, Cryptocurrency Mining, and More
- Malicious Docker Hub Container Images Used for Cryptocurrency Mining
- Cryptocurrency Miner Uses Hacking Tool Haiduc and App Hider Xhide to Brute Force Machines and Servers
- Defending Systems Against Cryptocurrency Miner Malware
Artículos Recientes
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One