The IIoT Threat Landscape: Securing Connected Industries
March 18, 2020
The Industrial Internet of Things (IIoT) provides bridges of connectedness that enable seamless IT and OT convergence. However, threat actors can cross these bridges to compromise systems. As the use of IoT extends beyond the home and goes into the vast industrial landscape, the scale of threats likewise grows.
With that being said, some components of the industrial system may not be totally prepared for the shift. Industrial devices meant to thrive in isolated environments are being exposed and pushed outside the limits of what they were originally designed for, and they may not have enough security to safeguard against these new threats.
We delve into smart factories, smart cities, connected cars, and other smart environments to examine the prevalent threats against the IIoT landscape.
Smart Factories
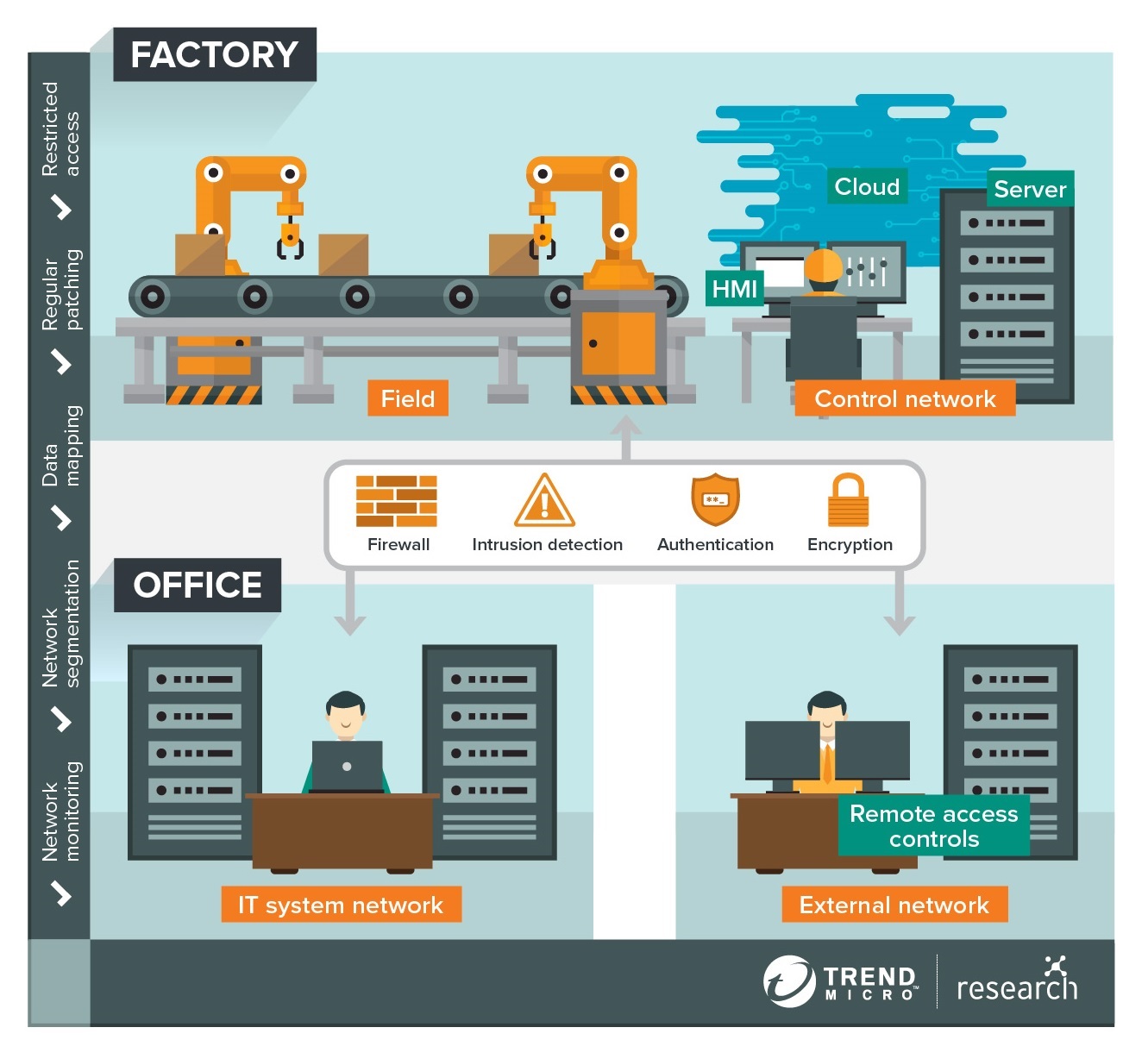
Figure 1. Smart Factory Architecture
Smart factories are exposed to compromise as there may be struggles for OT systems to keep up with IT. Some of these may be attributed to misconfigured settings and outdated components in endpoints and legacy software, the patches and updates of which may not be readily available or are already unsupported altogether. Patching such essential components of the system may halt production lines.
Industrial Control Systems (ICS) that were designed for isolated environments may not have cybersecurity measures that are apt for increased exposure. Also, vulnerabilities in communication protocols such as Modbus and Profinet lack the availability to authenticate users and detect unusual behavior. The integration of systems from different vendors, who have varying levels of security capabilities, could also expose the organization to IIoT threats.
These may lead to risks like IP leakage that could enable the theft of confidential data or trade secrets, industrial espionage, and production sabotage that may lead to physical accidents. And, as observed firsthand through a Trend Micro smart factory honeypot, vulnerable smart factories can attract threat actors who can deliver a variety of threats such as cryptocurrency miners, ransomware attacks, reconnaissance activities, and system shutdowns.
There are several recommendations to avoid such threats. One is to maintain legacy software by patching in tranches, if possible, to prevent system overload or operational disruption. Another is to assess the security risks of each device to see which parts of the system need to be prioritized in terms of security. This includes applying network segmentation and the principle of least privilege. Auditing the connections between IT and OT devices should be done to eliminate unnecessary — or potentially risky — connections. Security settings should also be configured, and additional authentication methods should be enabled.
Trend Micro TippingPoint Threat Protection System protects against known, unknown, and undisclosed vulnerabilities. IoT device makers can also integrate Trend Micro IoT Security with IoT devices, mobile apps, web apps, and IoT gateways. For detection of targeted attacks, ransomware, and advance threats, the Trend Micro Deep Discovery Inspector is recommended.
Smart Cities

Figure 2. Smart City Environment
Smart cities, which include energy, environment, connectivity, and governance, presents its own set of security challenges. One example of a challenge lies in the limitations of the devices’ form factor or complexity: Many smart devices are designed to be lightweight, with only enough computing power for their functions. This makes encrypting them a challenge. Updating and patching firmware may also prove to be difficult.
The devices’ lack of security exposes them to new threats. Cyber assets (e.g., devices and services) that are exposed and visible to the public can be used to gather intelligence, especially from governments. Threat actors can also conduct surveillance attacks through public IP security cameras.
There’s also the threat of ransomware and other blackmail attacks that hostage data and devices, which can be used to manipulate and interrupt operations. Such attacks could also affect the delivery of public utilities, such as power.
To mitigate risks in smart cities, enterprises should follow recommendations such as regularly employing patches and updates for the entire system, including firmware. Data should also be secured by configuring access according to the principle of least privilege and encrypting communication channels. A manual override should be allowed so personnel can mitigate the threat without having to rely on a network or internet connection. Administrators should also ensure that the system can still work without an internet connection, even if it’s just enough to continue basic services.
Trend Micro IoT Security gives IoT device makers solutions for securing their systems. Trend Micro Deep Security protects systems in multiple environments. Trend Micro IoT Security for Surveillance Cameras secures IP cameras from cyber threats.
Connected Cars

Figure 3. Intelligent Transport System
With the continued market growth of connected cars, it’s not difficult to see why cybercriminals consider these as attractive targets. Attackers can get in through unpatched vulnerabilities (both make- or brand-specific, and vendor-neutral flaws) and security gaps in protocols, such as the CAN bus, that can allow hacks on internet-connected car systems. Such attacks can disable crucial components of the vehicle (e.g., airbag, parking sensors, active safety systems) and compromise even physical security mechanisms. Vulnerabilities in third-party devices (like alarms) and apps (such as voice-enabled assistants) also pose risks.
Outside of such vehicles, the entire Intelligent Transport Systems (ITS) ecosystem and its components (such as roadway reporting, traffic flow control, and payment applications systems)are also exposed to threats, from malware, network, and distributed denial of service (DDoS) attacks, to man-in-the-middle (MiTM) and privilege escalation attacks.
How can connected cars, then, drive safely in this potentially threat-filled environment? To prevent such hazards, gaps in the network, hardware, software, and firmware should be checked to ensure that these are patched and updated. Other best practices, such as applying network segmentation and prioritizing the security of highly sensitive data, can also help protect sensitive information against hacks.
Trend Micro IoT Security for Automotive accelerates critical-modules protection against cyberattacks on connected vehicles. Trend Micro CAN Bus Anomaly Detection detects abnormal CAN bus network traffic and behavior through machine learning. Trend Micro Deep Security provides overall security for physical, virtual, and cloud environments.
Other Smart Environments
Other smart environments are not spared from threats. Cybercriminals go after personal data such as credit card details in the retail industry, or use ransomware attacks and other blackmail schemes against the utilities sector to interrupt services. In healthcare, threat actors aim to steal information such as confidential medical records, from hospital information systems, connected medical devices, and legacy systems.
Conclusion
The interconnectedness provided by IIoT enables faster and more efficient processes, but it can also expose industries to threats. No part of any system should be left exposed to such threats, since threat actors can do a lot of damage from even a single unsecured entry point.
Enterprises should audit systems to determine which components are vulnerable and which ones need more security. They should also ensure that security settings are properly configured to reduce risks. Other best practices, such as installing the latest patches and updates, and applying network segmentation and the principle of least privilege, should be implemented. Installing security solutions specifically configured for the IIoT environment can also help safeguard these systems.
HIDE
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Recent Posts
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One