Ransomware Spotlight: Trigona
Top affected countries and industries according to Trend data
This section cites Trend Micro™ Smart Protection Network™ (SPN) data on Trigona’s attempts to compromise organizations. Note that these detections pertain only to Trend customers and cover only a part of the Trigona victims.
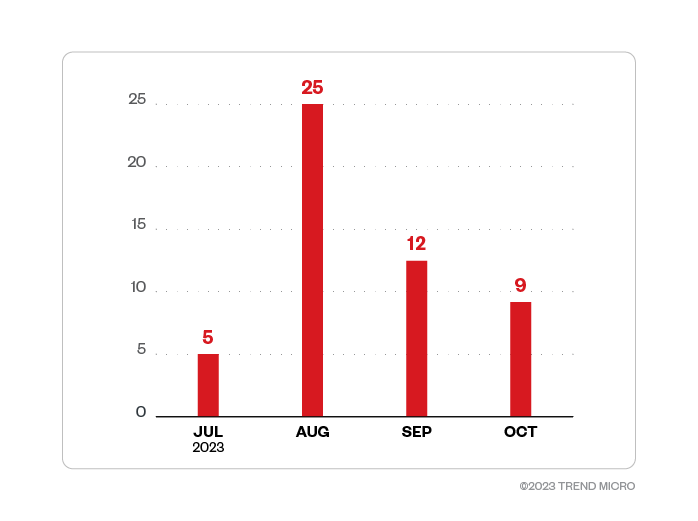
We first detected Trigona attack attempts on Trend customers in July 2023 and noted that the number of attempts peaked the following month. Attempted attacks then declined until the reported shutdown of the ransomware group’s leak site.
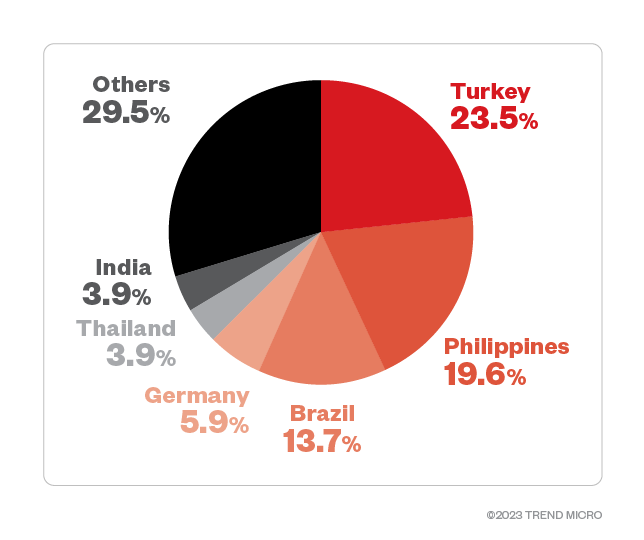
Turkey and the Philippines topped the Trigona attack detections at 23.5% and 19.6%, respectively, while Brazil followed closely at 13.7%. Germany and Thailand rounded up the top five countries targeted by Trigona during its time of activity.
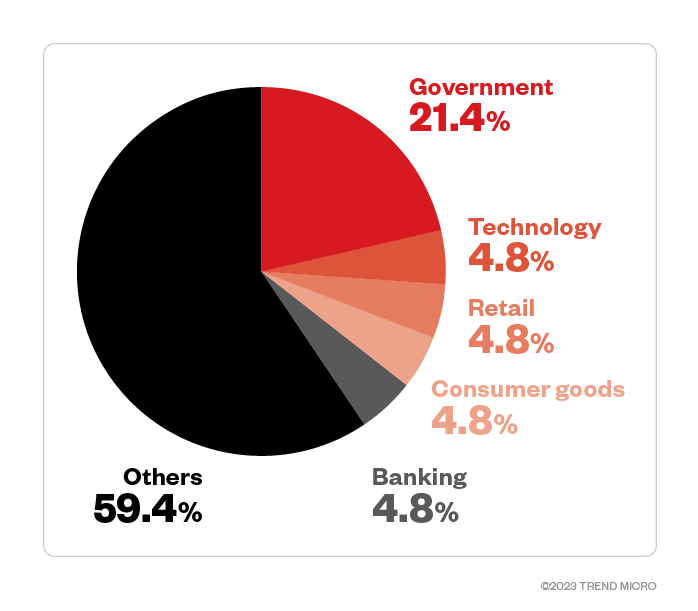
Industry data showed that threat actors behind Trigona targeted government organizations the most, with attack attempts making up 21.4% of total detections, according to feedback from Trend customers who detailed the industries in which they belong. Trigona also targeted enterprises in the technology, retail, fast-moving consumer goods, and banking industries.
Targeted regions and industries
according to Trigona ransomware’s leak site
This section looks at data based on attacks recorded on the leak site of the Trigona ransomware from April 2023 to October of the same year, when the leak site was taken down. The following data represents organizations that were successfully infiltrated by the Trigona ransomware and which refused to pay the ransom.
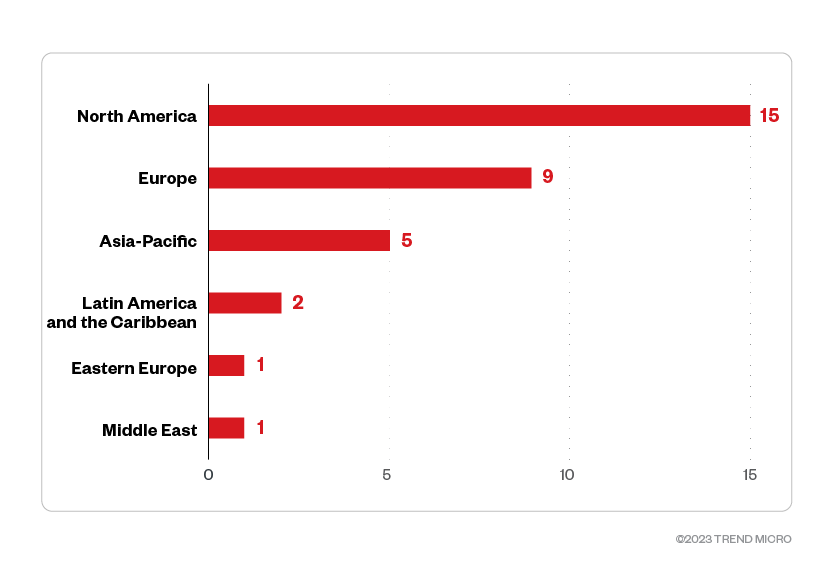
Based on a combination of Trend’s open-source intelligence (OSINT) research and investigation of the leak site, Trigona ransomware compromised a total of 33 organizations within the aforementioned period. Of these, 45.5% were organizations operating from North America, while 27.3% were from Europe. Enterprises in Asia-Pacific and Latin America and the Caribbean were also compromised.
Figure 4. The distribution by region of Trigona’s victim organizations
Sources: Trigona ransomware’s leak site and Trend Micro’s OSINT research
(April 2023 – October 2023)
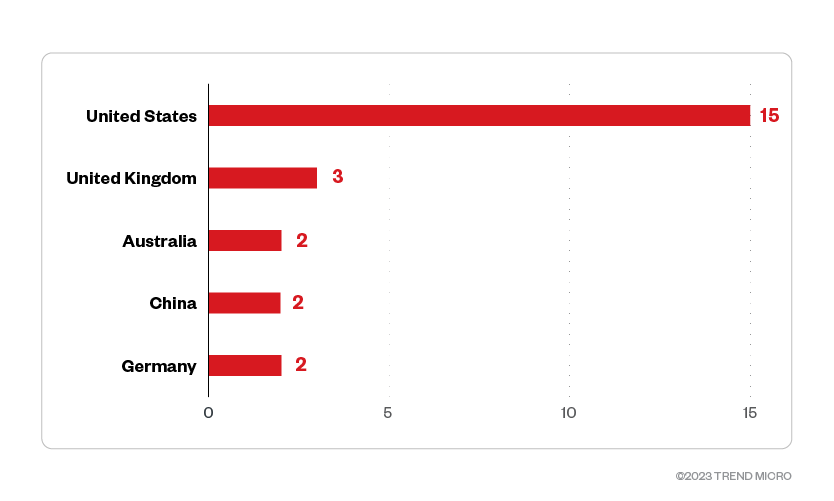
Based on the leak site data, out of the 13 countries targeted, the United States made up almost half of the victim organizations. Organizations from the United Kingdom made up 9.1%, while Australian organizations made up 6.1% of Trigona’s victims.
Figure 5. The top five countries targeted by the Trigona ransomware
Sources: Trigona ransomware’s leak site and Trend Micro’s OSINT research
(April 2023 – October 2023)
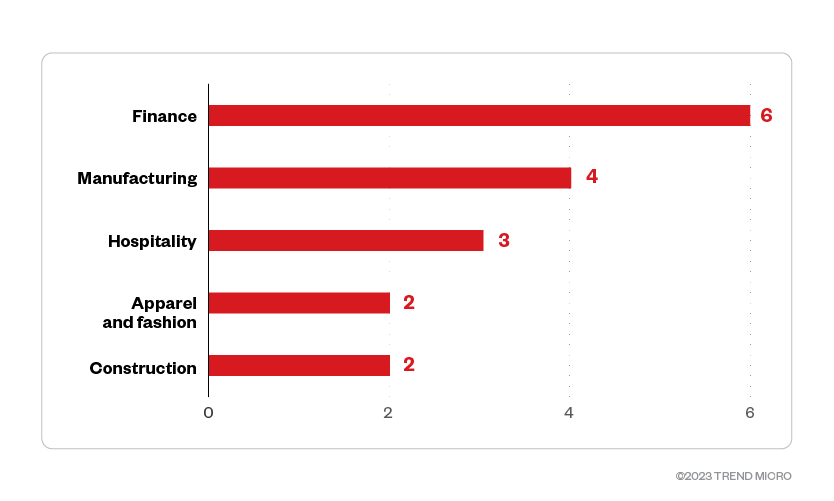
Threat actors behind the Trigona ransomware targeted enterprises in the finance industry the most, with 18.2% of its victim organizations classified under this trade.
Figure 6. The top five industries targeted by the Trigona ransomware
Sources: Trigona ransomware’s leak site and Trend Micro’s OSINT research
(April 2023 – October 2023)
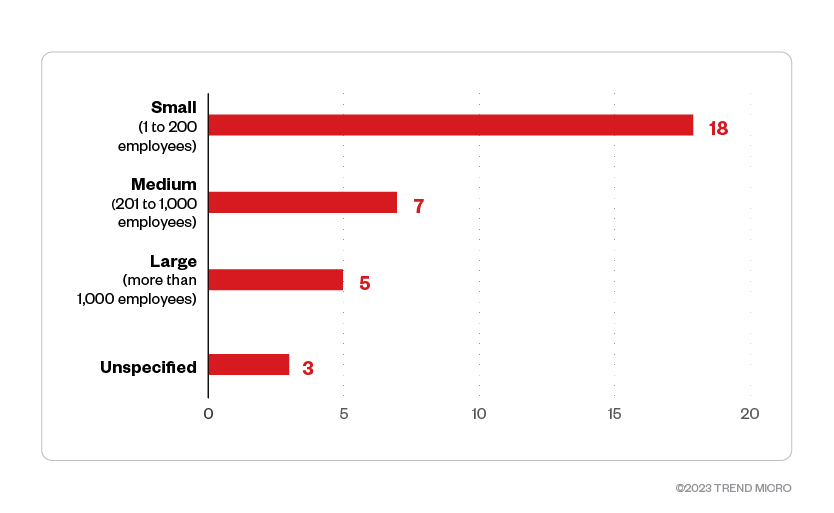
Trigona set its sights on small- and medium-sized businesses, which made up more than half of the group’s total victims from April to October 2023.
Figure 7. The distribution by organization size of the Trigona ransomware’s victims
Sources: Trigona ransomware’s leak site and Trend Micro’s OSINT research
(April 2023 – October 2023)
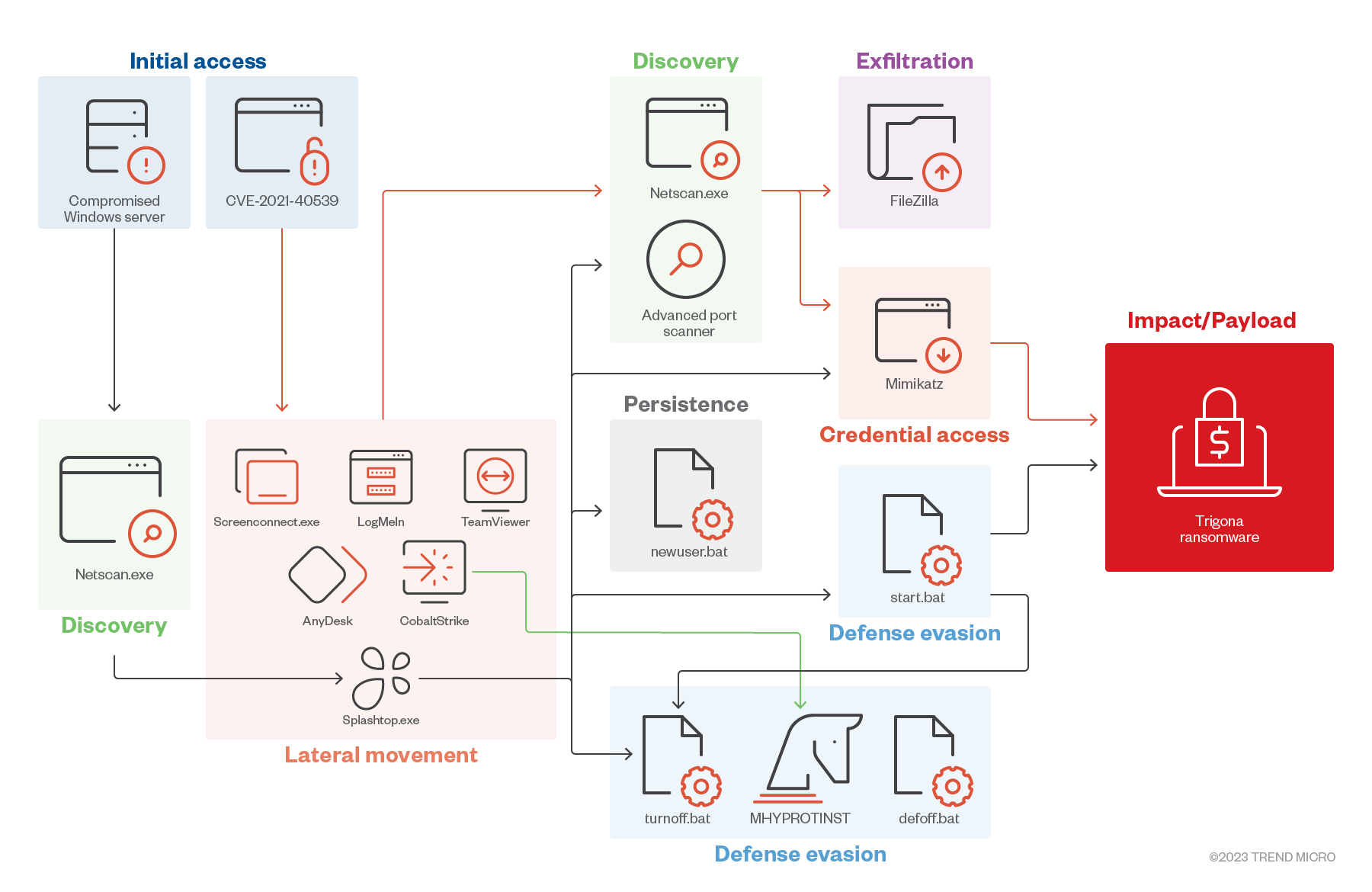
Infection chain and techniques
Initial Access
- Trigona threat actors were observed leveraging the vulnerability CVE-2021-40539.
- Trigona also targets compromised accounts by obtaining access from network access brokers.
Defense Evasion, Discovery
- Trigona drops turnoff.bat (detected as Trojan.BAT.TASKILL.AE) and defoff.bat (detected as Trojan.BAT.KILLAV.WLDP and Trojan.BAT.KILLAV.WLDX), which are used to terminate antivirus-related services and processes, including Trend-related service TMBMSRV.exe.
- Trigona also uses Network Scanner and Advanced Port Scanner to identify network connections.
Credential Access/Collection
- Trigona operators use Mimikatz to dump passwords and credentials on victim machines.
Lateral Movement
- Trigona operators use Splashtop, a legitimate remote access tool, to drop additional tools in a compromised machine.
- The threat actors also use other tools, such as LogMeIn, ScreenConnect, AnyDesk, and TeamViewer, for remote access.
- One of the samples we investigated showed that Trigona could utilize Cobalt Strike to drop MHYPROTINST (detected as Trojan.Win64.MHYPROTINST.A or Trojan.Win64.MHYPROTINST.B), which is used to terminate antivirus processes.
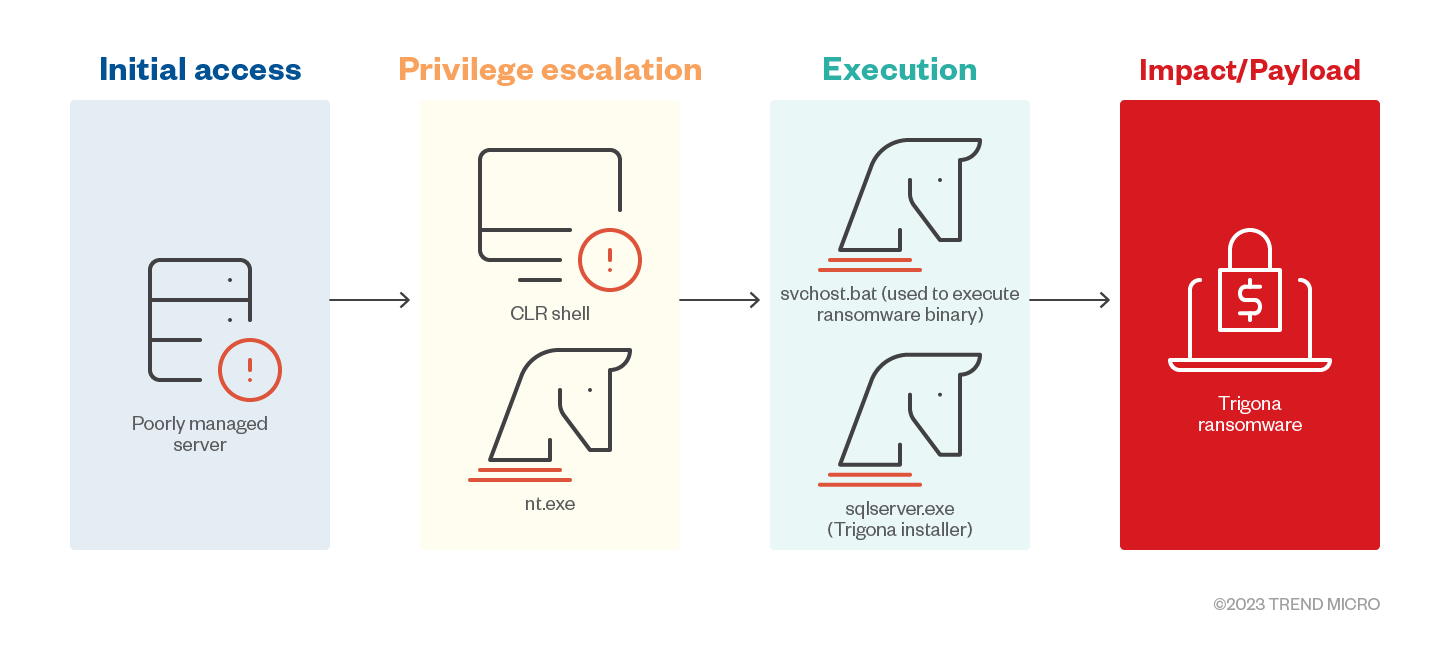
Privilege Escalation
- Trigona operators make use of Common Language Runtime (CLR) shell on attacks seen on MSSQL servers. The CLR shell tool is capable of multiple commands, one of which drops additional executables for privilege escalation (nt.exe).
Impact
- The Trigona ransomware encrypts data on victim machines using the Advanced Encryption Standard (AES) algorithm. It contains an encrypted configuration in its resource section that would be decrypted upon execution. However, it will only use certain strings within its configuration during execution. It also randomizes the file names of encrypted files and appends the extension “._locked”.
- Trigona also uses TDCP_rijndael to encrypt target files. It will only encrypt the first 0x80000 bytes (512 KB) of a file unless executed with the argument /full.
Additional information
Newer versions of the Trigona ransomware make use of additional command-line arguments. The following table summarizes the command-line arguments it accepts:
| /r | Encrypts files in random order |
| /full | Encrypts the whole content of a file; by default, only the first 0x80000 bytes/512 KB are encrypted |
| /erase | Deletes contents of a file |
| /!autorun | Prevents creating an autorun registry |
| /is_testing | Used for testing purposes; used with /test_cid and /test_vid |
| /test_cid | Used to input test CID |
| /test_vid | Used to input test VID |
| /p | Specifies path to encrypt |
| /path | Prevents encrypting local files |
| /!local | |
| /!lan | Prevents encrypting network shares |
| /shdwn | Turns off the machine after encryption |
| /autorun_only | Installs autorun, but does not trigger the encryption |
The Linux version of Trigona found in the wild shares similarities with its Windows counterpart. The Linux version of Trigona accepts the following command-line arguments:
| /erase | Deletes contents of a file |
| /is_testing | Used for testing purposes; used with /test_cid and /test_vid |
| /test_cid | Used to input test CID |
| /test_vid | Used to input test VID |
| /path | Specifies the path to encrypt |
| /shdwn | Turns off the machine after encryption |
The 64-bit versions of Trigona found in June 2023 contains the following additional command-line arguments:
| /sleep | Sets the ransomware to “sleep” or be dormant for a specified time before execution |
| /debug | Executes in debug mode; needs to be executed with /p |
| /log_f | Used for logging and specifying the log file |
| /fast | Most likely used to speed up encryption, but our analysis showed that this argument doesn’t work |
| /allow_system | Used to allow encrypting files in system directory |
MITRE tactics and techniques
| Initial Access | Persistence | Defense Evasion | Discovery | Impact |
|---|---|---|---|---|
T1190 - Exploit Public-Facing Application | T1547.001 - Boot or Logon Autostart Execution: Registry Run Keys/Startup Folder | T1140 - Deobfuscate/Decode Files or Information T1218.005 - System Binary Proxy Execution: Mshta T1036.005 - Masquerading: Match Legitimate Name or Location T1497.003 - Virtualization/Sandbox Evasion: Time-Based Evasion | T1083 - File and Directory Discovery T1135 - Network Share Discovery T1033 - System Owner/User Discovery | T1529 - System Shutdown/Reboot T1486 - Data Encrypted for Impact T1485 - Data Destruction |
Summary of malware, tools, and exploits used
| Initial Access | Defense Evasion | Discovery | Lateral Movement | Privilege Escalation | Impact |
|---|---|---|---|---|---|
|
|
|
|
|
|
|
| ||||
|
| ||||
|
| ||||
| |||||
|
Security recommendations
Despite reports that the Trigona ransomware’s leak site has been shut down, it is worth examining how threat actors behind the group conducted their operations. While relatively new, Trigona successfully facilitated various techniques and created versions to target specific operating systems within its one year of activity. The group, which gained a reputation for imposing intimidating time constraints within which victims were pressured to pay ransom, was also observed targeting data beyond the infected machine and into shared network drives. These behaviors suggest that the threat actors behind the group are quick to adapt, not to mention fierce in carrying out their schemes. Combined with Trigona’s assumed affiliation with CryLock and BlackCat, there is a possibility of the threat actors regrouping after the shutdown and respawning under a different name.
To protect systems against ransomware and other similar threats, organizations can implement security frameworks that allocate resources systematically to establish a strong defense strategy.
The following are some best practices that organizations can consider to help protect themselves from ransomware infections:
Audit and inventory
- Take an inventory of assets and data.
- Identify authorized and unauthorized devices and software.
- Make an audit of event and incident logs.
Configure and monitor
- Manage hardware and software configurations.
- Grant admin privileges and access only when necessary to an employee’s role.
- Monitor network ports, protocols, and services.
- Activate security configurations on network infrastructure devices such as firewalls and routers.
- Establish a software allowlist that executes only legitimate applications.
Patch and update
- Conduct regular vulnerability assessments.
- Perform patching or virtual patching for operating systems and applications.
- Update software and applications to their latest versions.
Protect and recover
- Implement data protection, backup, and recovery measures.
- Enable multifactor authentication (MFA).
Secure and defend
- Employ sandbox analysis to block malicious emails.
- Deploy the latest versions of security solutions to all layers of the system, including email, endpoint, web, and network.
- Detect early signs of an attack such as the presence of suspicious tools in the system.
- Use advanced detection technologies such as those powered by artificial intelligence (AI) and machine learning.
Train and test
- Regularly train and assess employees in security skills.
- Conduct red-team exercises and penetration tests.
A multilayered approach can help organizations guard possible entry points into the system (endpoint, email, web, and network). Security solutions that can detect malicious components and suspicious behavior can also help protect enterprises.
- Trend Micro Vision One™ provides multilayered protection and behavior detection, which helps block questionable behavior and tools early on before the ransomware can do irreversible damage to the system.
- Trend Micro Cloud One™ Workload Security protects systems against both known and unknown threats that exploit vulnerabilities. This protection is made possible through techniques such as virtual patching and machine learning.
- Trend Micro™ Deep Discovery™ Email Inspector employs custom sandboxing and advanced analysis techniques to effectively block malicious emails, including phishing emails that can serve as entry points for ransomware.
- Trend Micro Apex One™ offers next-level automated threat detection and response against advanced concerns such as fileless threats and ransomware, ensuring the protection of endpoints.
Indicators of compromise (IOCs)
The IOCs for the threat discussed in this article can be found here. Actual indicators might vary per attack.
Trend Micro Vision One Hunting Query
Trend Vision One customers can use the following hunting query to check if their network/system is possibly affected by Trigona ransomware:
fullPath:"*._locked" OR fullPath:"*available_for_trial*._locked" OR fullPath:"*\\how_to_decrypt.txt" OR malName:"*TRIGONA.*.note" OR malName:"*CRYLOCK.*.note" OR (processFilePath:"*\\mshta.exe" AND filefullpath:"*\\how_to_decrypt.hta") OR (objectRegistryKeyHandle:"*\\Run\\*" AND objectRegistryData:"*\\how_to_decrypt.hta")
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines


 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One