Ransomware Spotlight: Royal
Top affected countries and industries
according to Trend Micro data
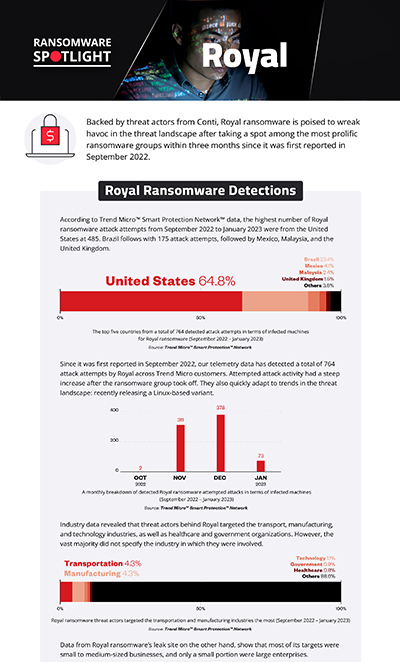
In this section, we examine Royal ransomware’s attempts to compromise organizations since it was first reported in 2022 based on Trend Micro™ Smart Protection Network™ country and regional data. It’s important to note that this data covers only Trend Micro customers and does not contain all victims of Royal.
Threat actors behind Royal focused their attention on the United States, with 485 target attack attempts detected, making up 63.5% of the total detections. Brazil follows with 175 registered attack attempts, followed by Mexico and Malaysia with 31 and 18 detections respectively, while there were only 11 attack attempts detected in the United Kingdom.
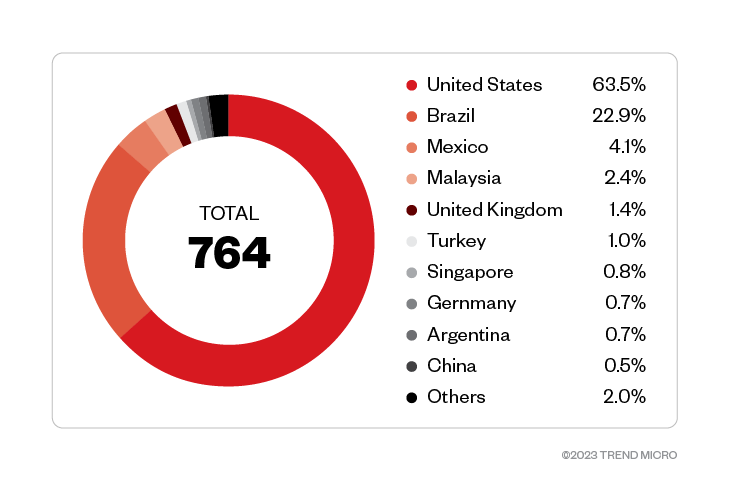
Among Trend Micro customers who disclosed what industry they are involved in, the transportation and manufacturing industries were targeted the most. The technology and education industries, as well as healthcare and government organizations were also targeted.
Figure 2. Trend Micro customer organizations belonging to the transportation and manufacturing industries experienced the most attack attempts from threat actors behind Royal. (September 2022 – January 2023) Source: Trend Micro™ Smart Protection Network™ ™
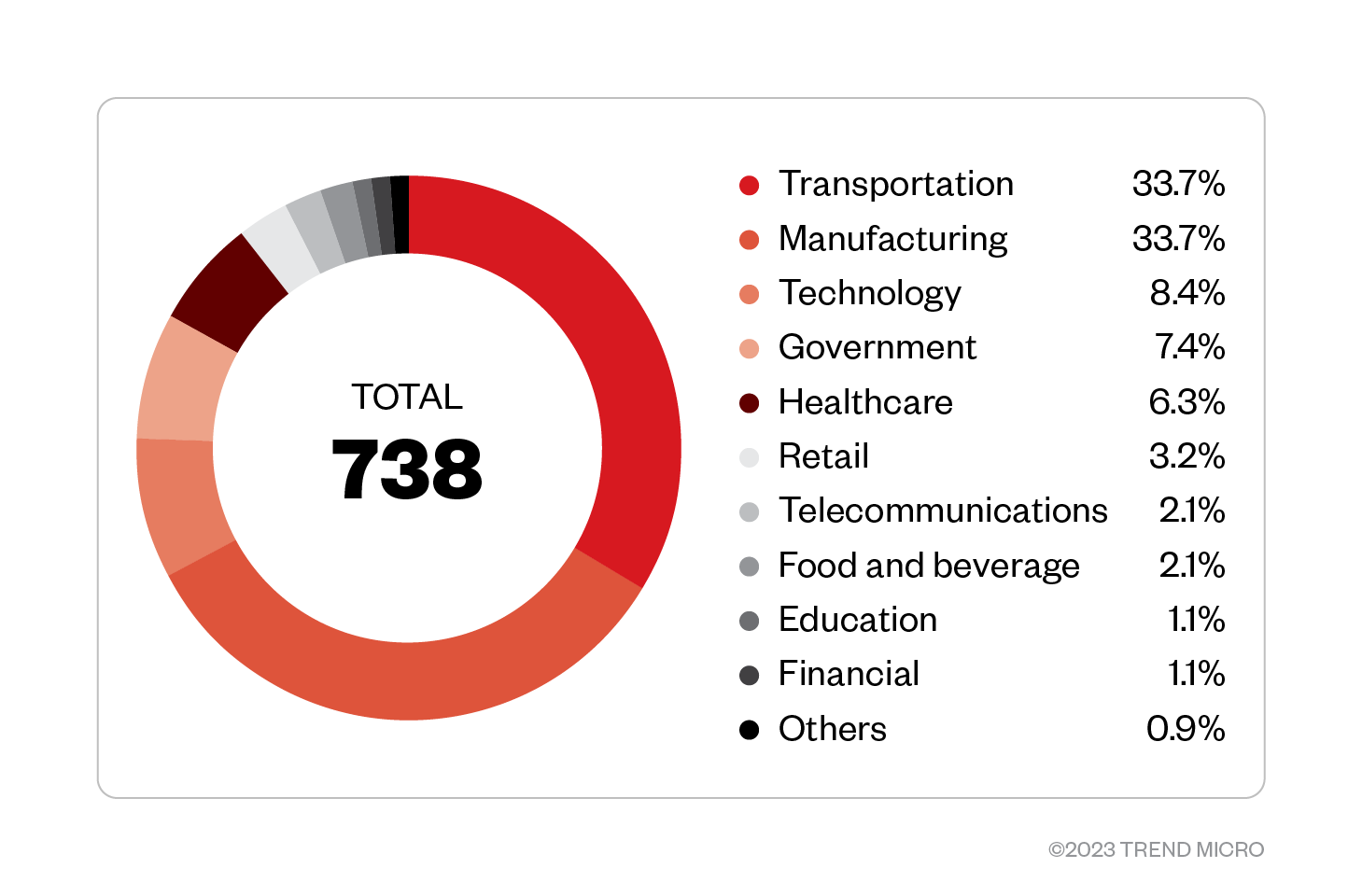
Since it was first reported in September 2022, our telemetry data has detected a total of 764 attack attempts by Royal across Trend Micro customers.
Figure 3. A monthly breakdown of detected Royal ransomware attempted attacks in terms of infected machines (September 2022 – January 2023) Source: Trend Micro™ Smart Protection Network™ ™
Targeted regions and industries
according to Royal ransomware’s leak site
This section looks at data based on attacks recorded on the leak site of Royal ransomware’s operators. The following data represents organizations successfully infiltrated by Royal ransomware, which have refused to pay the ransom demand as of writing.
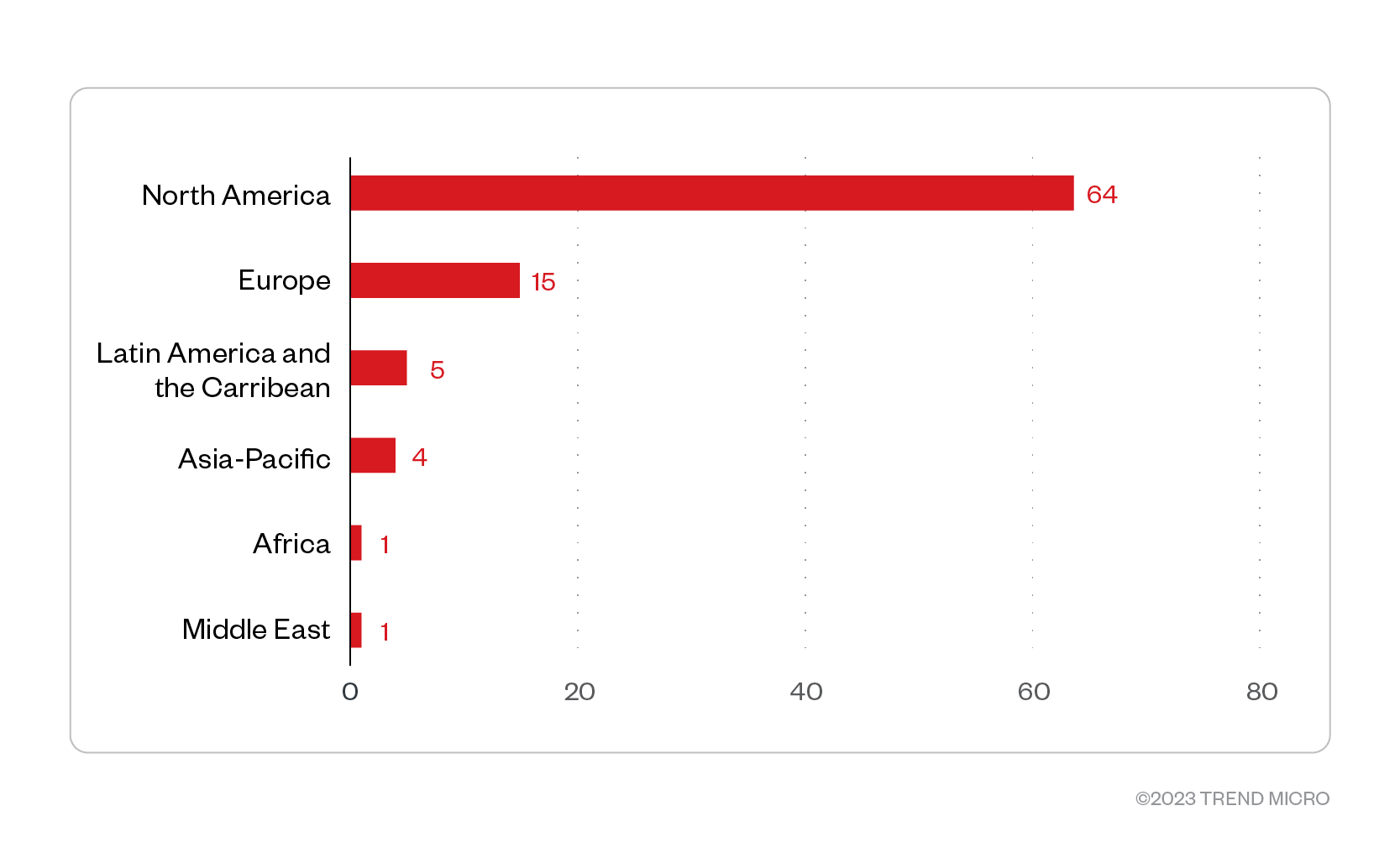
Based on a combination of Trend Micro’s open-source intelligence (OSINT) research and investigation of the leak site, Royal ransomware compromised a total of 90 organizations. Of these, 64 were organizations operating from North America, while 15 were from Europe. Enterprises in Latin America and the Caribbean, Asia-Pacific, Africa, and Middle East were also compromised.
Figure 4. The distribution by region of Royal ransomware’s victim organizations
Source: Royal ransomware’s leak site and Trend Micro’s OSINT research (November 2022 – January 2023)
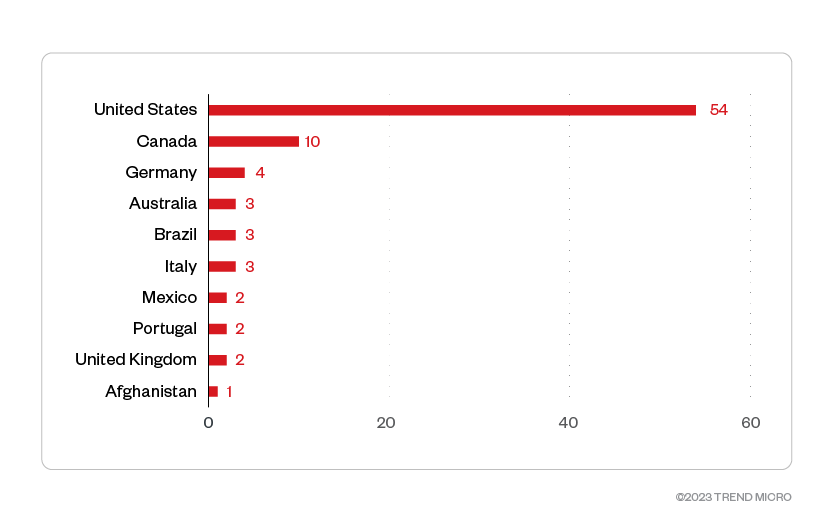
The United States had the most victim organizations with 54 compromised organizations, while 10 Canadian enterprises were also jeopardized. Germany, Australia, and Brazil round up the top five countries most targeted by threat actors behind Royal.
Figure 5. The top 10 countries most targeted by the Royal ransomware group
Source: Royal ransomware’s leak site and Trend Micro’s OSINT research (November 2022 – January 2023)
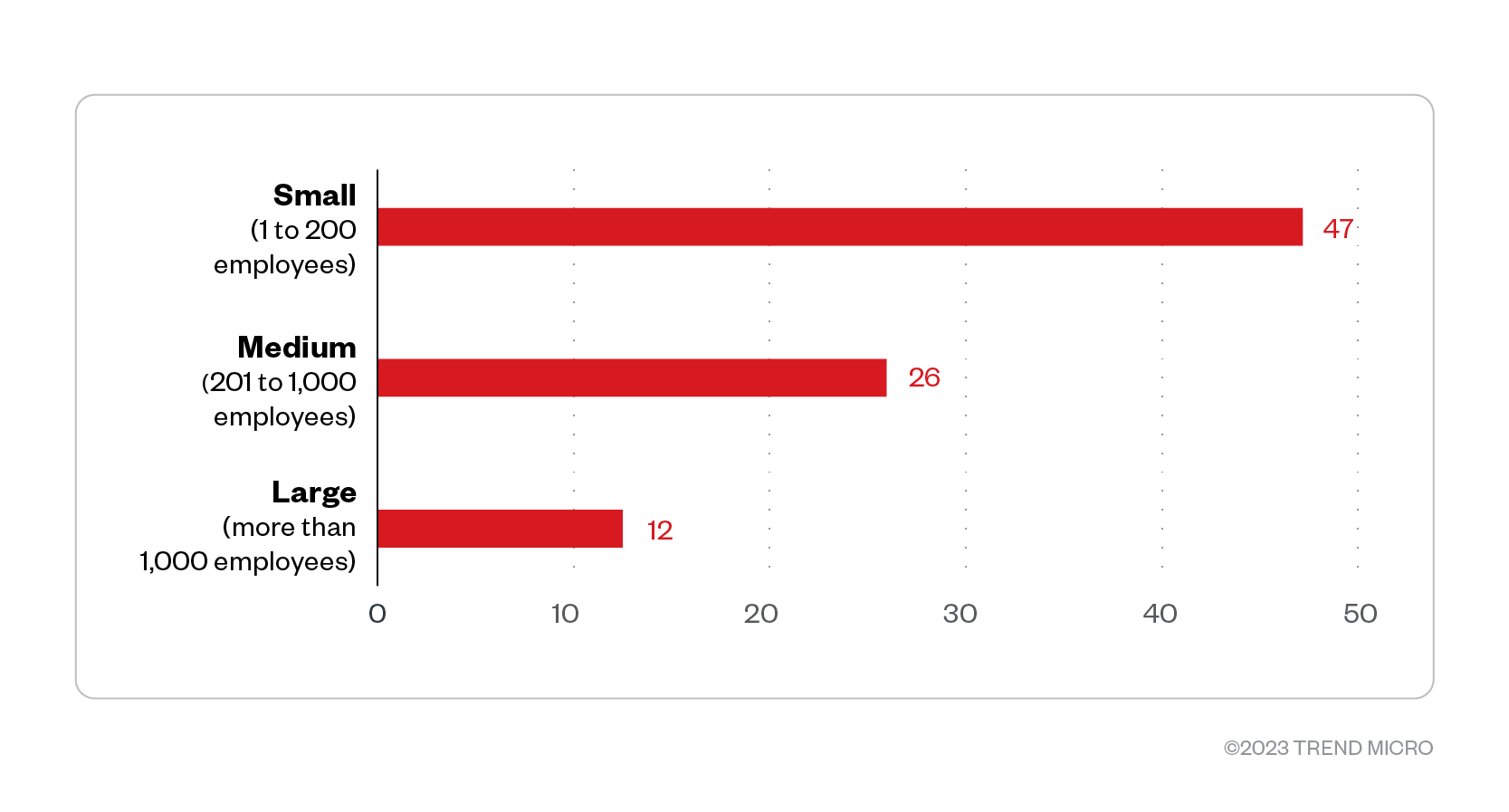
The majority of Royal ransomware victim organizations were small to medium-sized businesses, and only a small portion were large enterprises.
Figure 6. The distribution by organization size of Royal ransomware’s victim organizations
Source: Royal ransomware’s leak site and Trend Micro’s OSINT research (November 2022 – January 2023)
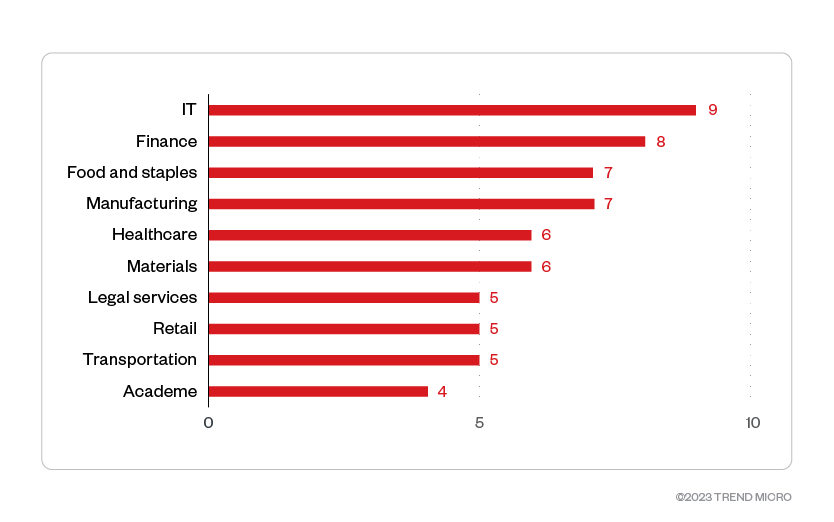
Among the identified sectors of Royal ransomware victim organizations, the IT, finance, materials, healthcare, and food and staples industries were its top targets.
Figure 7. The top 10 industries most targeted by Royal ransomware threat actors
Source: Royal ransomware’s leak site and Trend Micro’s OSINT research (November 2022 – January 2023)
Initial Access
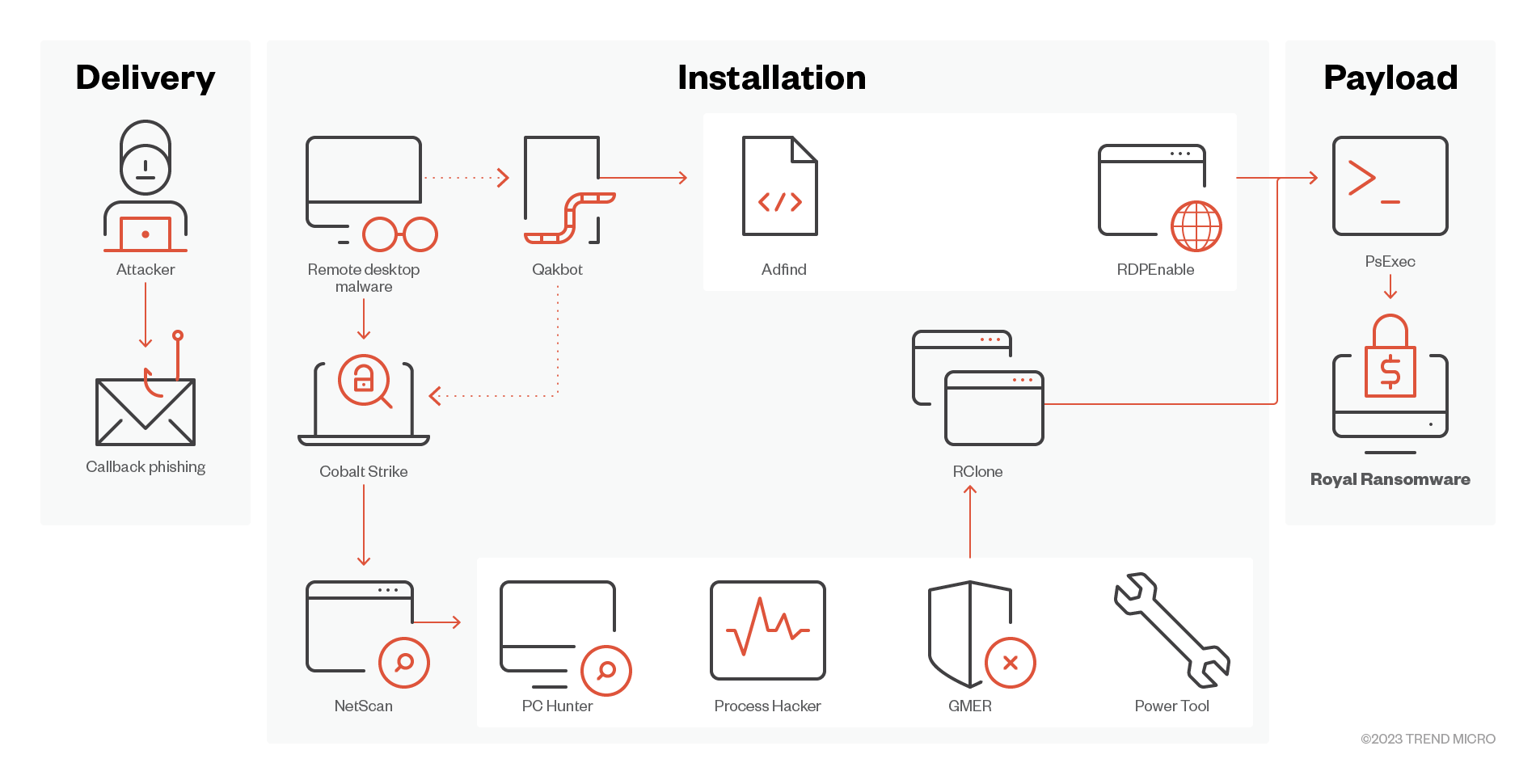
External reports mention that one of the arrival methods of Royal Ransomware is via the Callback Phishing scam where victims are tricked into installing remote desktop software. This method is similar to the techniques used by the Conti group.
- We have also recently observed Royal arriving from Batloader and IcedID malware.
Defense Evasion
- Upon successful installation of a remote software, attackers usually use tools like PCHunter, Process Hacker, GMER, or PowerTool to manually uninstall AV products installed on the target system.
Discovery
- Attackers also use tools like NetScan and AdFind along with windows net.exe and nltest.exe to gain information of the victims Active Directory and connected remote systems.
- We have also observed Royal ransomware actors using Advanced Port Scanner, a free network scanner, to find and open ports.
Lateral Movement and Command and Control
- Royal ransomware has also been observed to use Cobalt Strike and Qakbot to pivot on target machines and deploy other tools and payloads.
- Our observations from Royal ransomware activity also saw dual use agents, such as Connectwise, Splashtop, Atera, and Syncro, to connect to victim environments and execute malicious processes.
Exfiltration
- Rclone was found on the victim machines; the program is usually used to exfiltrate stolen information.
Impact
- Royal Ransomware requires an “-id” argument to execute; this is any 32-character-long argument. It also accepts a “path” argument for target encryption, and the “-ep” argument which indicates the encryption percentage for large files to encrypt.
- Encryption can be on local and network paths; the latest Royal ransomware variant has an option to choose either local, network or both.
- Shadow copies are also deleted using the vssadmin tool.
MITRE tactics and techniques
| Initial Access | Execution | Defense Evasion | Discovery | Exfiltration | Lateral Movement | Command and Control | Impact |
|---|---|---|---|---|---|---|---|
T1566 - Phishing | T1059 - Command and Scripting Interpreter | T1562.001 - Impair Defenses: Disable or Modify Tools T1112 - Modify Registry | T1069 - Permission Groups Discovery: Domain groups T1018 - Remote System Discovery | T1567 - Exfiltration Over Web Service | T1570 - Lateral Tool Transfer | T1095 - Non-Application Layer Protocol | T1490 - Inhibit System Recovery T1486 - Data Encrypted for Impact |
Summary of malware, tools, and exploits used
Security teams should take note of and observe the presence of the following malware and tools typically used in Royal ransomware attacks:
Tools
- PsExec
- NetScan
- AdFind
- CobaltStrike
- PCHunter
- Process Hacker
- GMER
- PowerTool
- RDPEnable
- RClone
- Connectwise
- Splashtop
- Atera
- Syncro
- Advanced Port Scanner
Malware
- Batloader
- IcedID
Recommendations
Backed by threat actors from Conti, Royal ransomware is poised to wreak havoc in the threat landscape after it became one of the most prolific ransomware groups within the three months since it was first reported. Combining new and old techniques and quick to evolve, Royal poses a high-stakes threat to enterprises. Organizations are recommended to stay vigilant against such threats.
To protect systems against Royal ransomware and other similar threats, organizations can implement security frameworks that allocate resources systematically to establish a strong defense strategy.
Here are some best practices that organizations can adopt to defend against Royal ransomware:
Audit and inventory
- Take an inventory of assets and data
- Identify authorized and unauthorized devices and software
- Audit event and incident logs
Configure and monitor
- Manage hardware and software configurations
- Grant admin privileges and access only when necessary to an employee’s role
- Monitor network ports, protocols, and services
- Activate security configurations on network infrastructure devices such as firewalls and routers
- Establish a software allowlist that only executes legitimate applications
Patch and update
- Conduct regular vulnerability assessments
- Perform patching or virtual patching for operating systems and applications
- Update software and applications to their latest versions
Protect and recover
- Implement data protection, backup, and recovery measures
- Enable multifactor authentication (MFA)
Secure and defend
- Employ sandbox analysis to block malicious emails
- Deploy the latest versions of security solutions to all layers of the system, including email, endpoint, web, and network
- Discover early signs of an attack, such as the presence of suspicious tools in the system
- Use advanced detection technologies such as those powered by AI and machine learning
Train and test
- Regularly train and assess employees’ security skills
- Conduct red-team exercises and penetration tests
A multilayered approach can help organizations guard possible entry points into their system (endpoint, email, web, and network). Security solutions can detect malicious components and suspicious behavior, which can in turn help protect enterprises.
- Trend Micro Vision One™ provides multilayered protection and behavior detection, which helps block questionable behavior and tools early on before ransomware can do irreversible damage to the system.
- Trend Micro Cloud One™ – Workload Security protects systems against both known and unknown threats that exploit vulnerabilities. This protection is made possible through techniques such as virtual patching and machine learning.
- Trend Micro™ Deep Discovery™ – Email Inspector employs custom sandboxing and advanced analysis techniques to effectively block malicious emails, including phishing emails that can serve as entry points for ransomware.
- Trend Micro Apex One™ offers next-level automated threat detection and response against advanced concerns such as fileless threats and ransomware, ensuring the protection of endpoints.
Indicators of Compromise (IOCs)
The IOCs for this article can be found here. Actual indicators might vary per attack.
Trend Micro Vision One Hunting Query
Trend Vision One customers can use the following hunting query to check if their network/system is possibly affected by Royal ransomware:
(processCmd:"?:*\\psexec.exe" AND objectFilePath:"*.exe*-id *") OR fullPath:"*.royal_?"
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines


 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One