Ransomware Spotlight: Akira
Top affected industries and countries
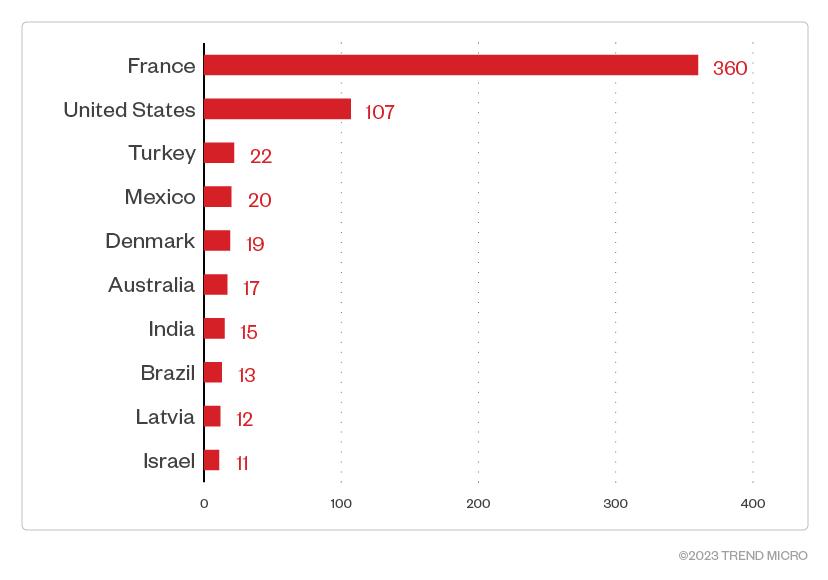
Because Akira is new and highly targeted, the number of attacks is not as substantial as other more established and widely used ransomware families. Our Trend Micro™ Smart Protection Network™ telemetry points to France as having been most hit by Akira from May 1, 2023, to Aug. 31, 2023, with 53.1% of all detections. The United States and Turkey take the second and third spots, respectively, with 107 and 22 detections.
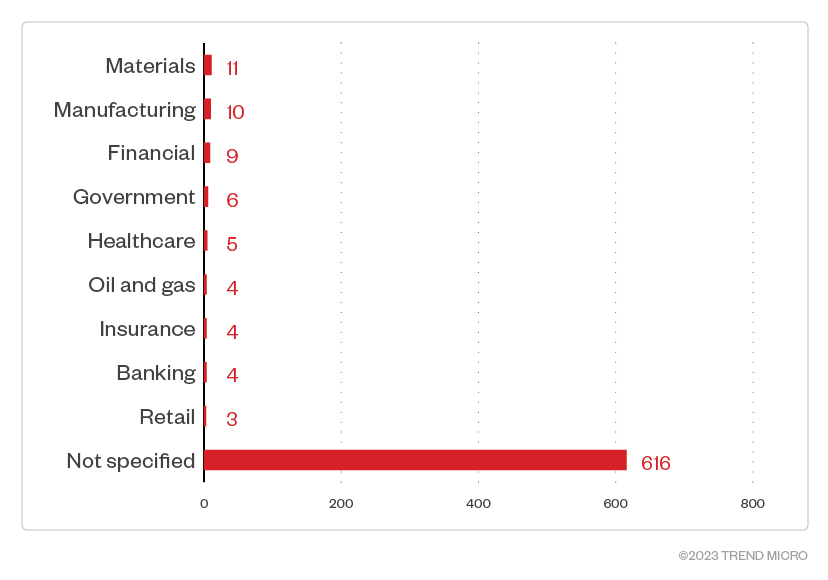
Based on our data, most of Akira’s victims belong to unspecified industries. Based on reports, approximately 80% of Akira’s victims are small to medium-sized businesses (SMBs). The materials, manufacturing, and financial sectors made the top five list in the three-month span.
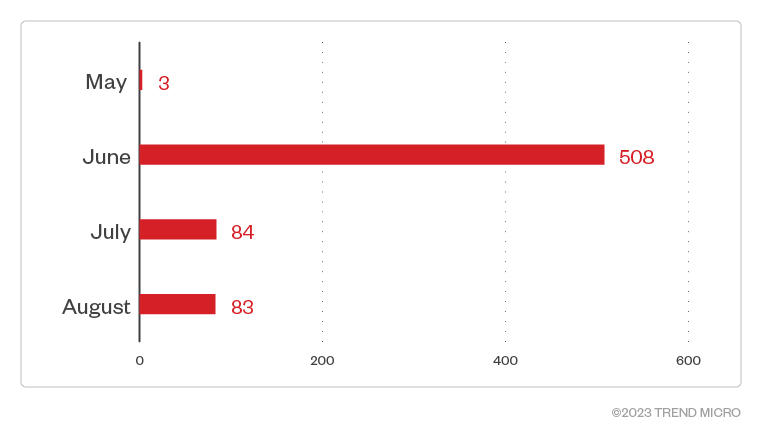
Akira’s monthly detections showed a surge in June 2023 with 508 attack attempts, which is significantly higher than the other months in our analysis period. Our lowest detections were for May 2023, with only three attack attempts for the entire month.
Targeted regions and industries
according to Akira's ransomware leak site
We now focus on Akira ransomware operators’ leak site data, which provides details on organizations that have been targeted by Akira actors.
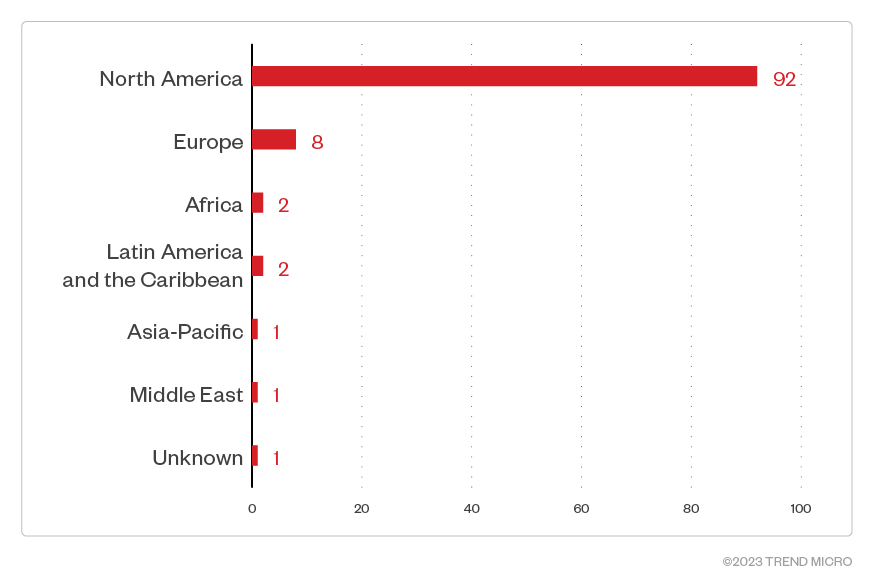
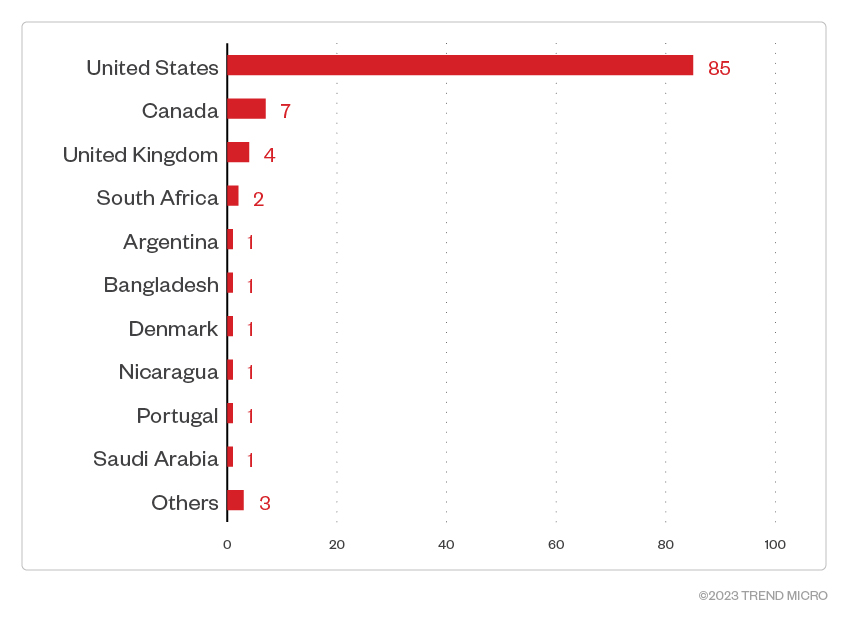
This data, which is a consolidation of Trend Micro’s open-source intelligence (OSINT) research and investigation of the leak site, shows that Akira ransomware actors compromised 107 organizations between April 1 to August 31, 2023. Most of Akira victims — specifically, 85.9% of them — were businesses based in North America.
Figure 4. The distribution by region of Akira ransomware’s victim organizations
Sources: Akira ransomware’s leak site and Trend Micro’s OSINT research (April 2023 – August 2023)
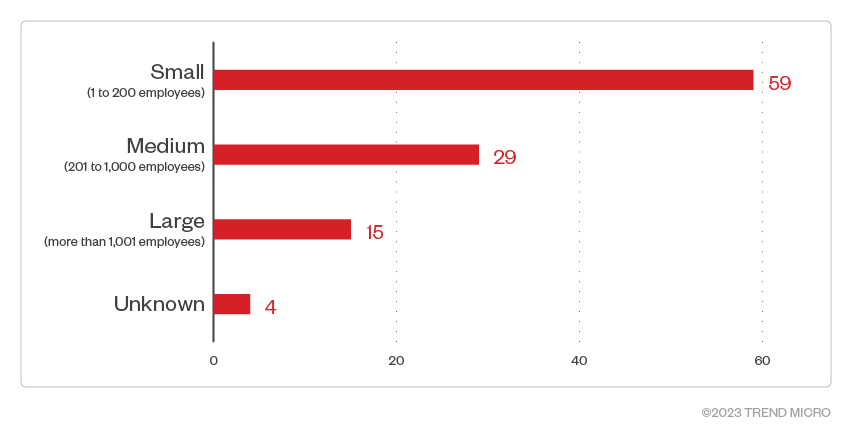
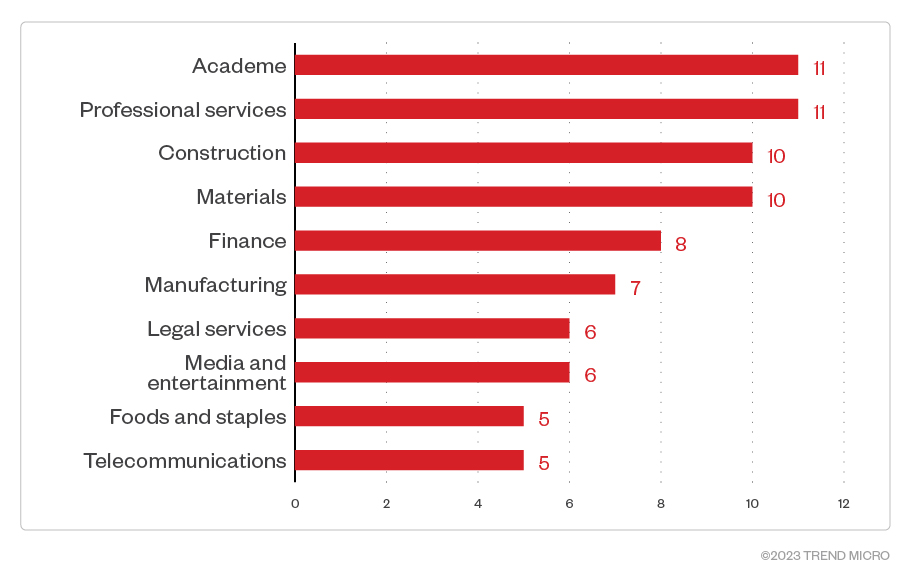
We’ve found that most of Akira’s victims were small-sized businesses, with 1 to 200 employees, at 59 victims. Meanwhile, midsized businesses and large enterprises took the second and third slots, respectively. Interestingly, based on leak site data, the most targeted sectors are the academe and professional services, followed closely by construction and materials.
Figure 6. The distribution by organization size of Akira ransomware’s victim organizations
Sources: Akira ransomware’s leak site and Trend Micro’s OSINT research (April 2023 – August 2023)
Infection chain and techniques
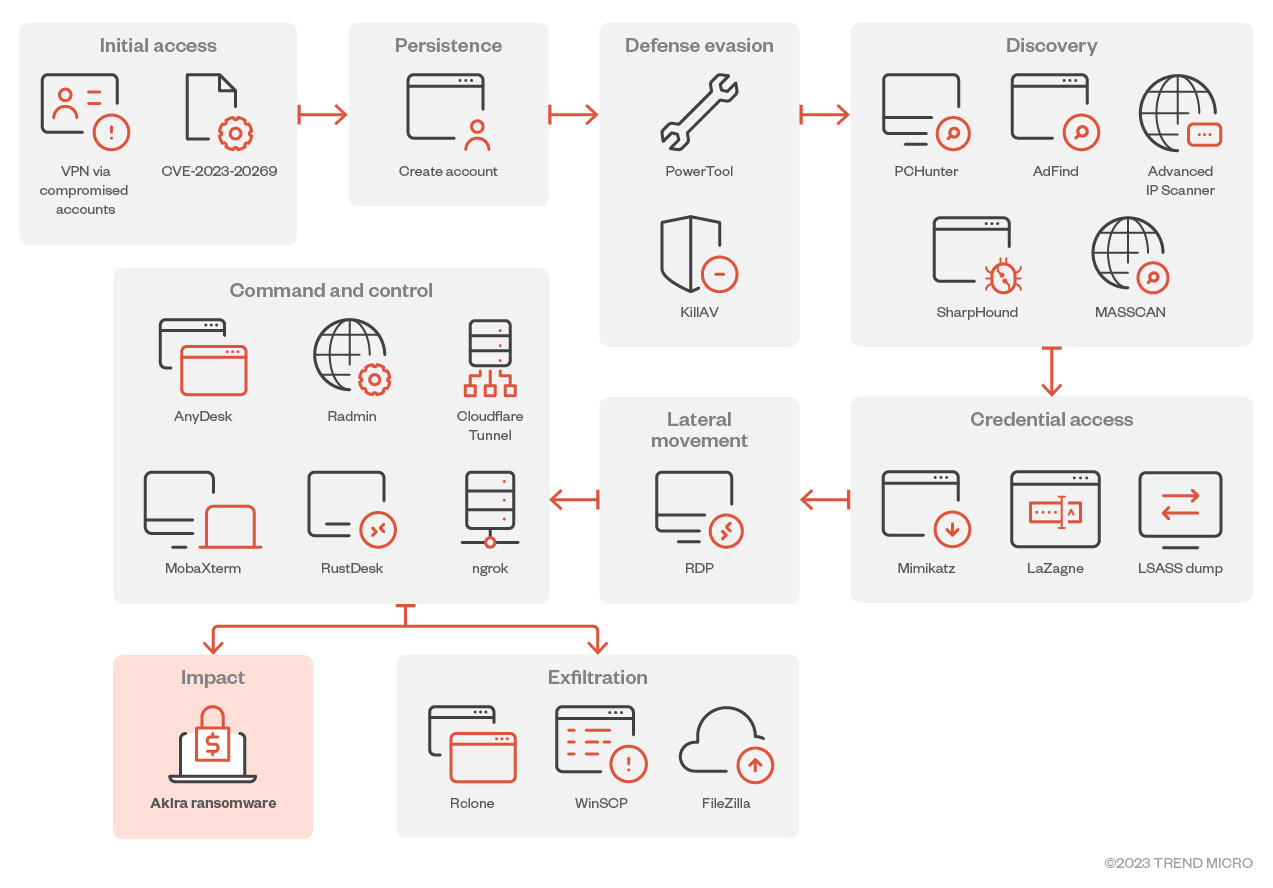
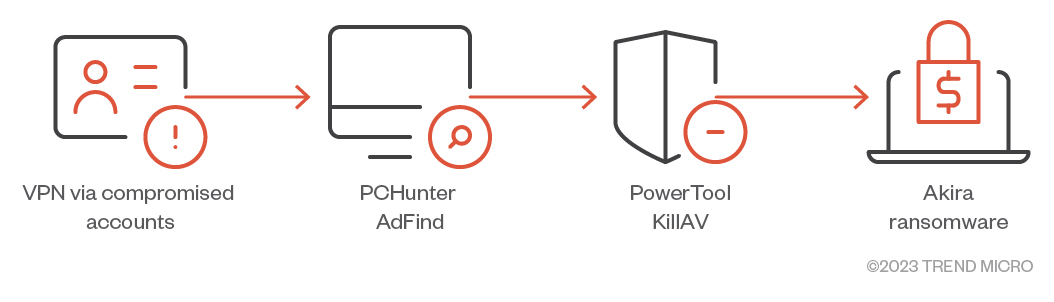
The Akira ransomware typically gains access to victim environments by using valid credentials that were possibly obtained from their affiliates or other attacks. It has been observed using third-party tools such as PCHunter, AdFind, PowerTool, Terminator, Advanced IP Scanner, Windows Remote Desktop Protocol (RDP), AnyDesk, Radmin, WinRAR, and Cloudflare’s tunneling tool. Figure 8 shows Akira’s infection chain.
Figure 8. The typical Akira ransomware infection chain
Figure 9. The Akira ransomware infection chain based on an infection case we’ve analyzed
Initial Access
Akira ransomware actors are known to use compromised VPN credentials to gain initial access. They’ve also been observed targeting vulnerable Cisco VPNs by exploiting CVE-2023-20269, a zero-day vulnerability that affects Cisco ASA and FTD.
Persistence
Akira operators have been observed creating a new domain account on the compromised system to establish persistence.
Defense evasion
For its defense evasion, Akira ransomware actors have been observed using PowerTool or a KillAV tool that abuses the Zemana AntiMalware driver to terminate AV-related processes.
Discovery
The actors behind the Akira ransomware have been observed using the following to gain knowledge on the victim's system and its connected network:
- PCHunter and SharpHound to gather system information
- AdFind alongside the net Windows command and nltest to obtain domain information
- Advanced IP Scanner and MASSCAN to discover other remote systems
Credential Access
Akira ransomware operators use Mimikatz, LaZagne, or a specific command line to gather credentials.
Lateral Movement
Akira actors use Windows RDP to move laterally within the victim's network.
Command and control
Akira ransomware operators have been observed using the third-party tool and web service RClone to exfiltrate stolen information. Moreover, they have also been observed using either FileZilla or WinSCP to exfiltrate stolen information via File Transfer Protocol (FTP).
- AnyDesk
- Radmin
- Cloudflare Tunnel
- MobaXterm
- RustDesk
- Ngrok
Exfiltration
Akira ransomware operators have been observed using the third-party tool and web service RClone to exfiltrate stolen information. Moreover, they have also been observed using either FileZilla or WinSCP to exfiltrate stolen information via File Transfer Protocol (FTP).
Impact
Akira ransomware encrypts targeted systems using a hybrid encryption algorithm that combines Chacha20 and RSA. Additionally, the Akira ransomware binary, like most modern ransomware binaries, has a feature that allows it to inhibit system recovery by deleting shadow copies from the affected system.
Other technical details
- It avoids encrypting the following directories:
- winnt
- tmp
- temp
- thumb
- $Recycle.Bin
- $RECYCLE.BIN
- System Volume Information
- Boot
- Windows
- Trend Micro
- ProgramData
- It avoids encrypting files with the following extensions:
- .exe
- .dll
- .lnk
- .sys
- .msi
- .akira
- It encrypts the whole file, regardless of size, if the file extension is any of the following:
- .4dd
- .4dl
- .accdb
- .accdc
- .accde
- .accdr
- .accdt
- .accft
- .adb
- .ade
- .adf
- .adp
- .arc
- .ora
- .alf
- .ask
- .btr
- .bdf
- .cat
- .cdb
- .ckp
- .cma
- .cpd
- .dacpac
- .dad
- .dadiagrams
- .daschema
- .db
- .db-shm
- .db-wal
- .db3
- .dbc
- .dbf
- .dbs
- .dbt
- .dbv
- .dbx
- .dcb
- .dct
- .dcx
- ddl
- .dlis
- .dp1
- .dqy
- .dsk
- .dsn
- .dtsx
- .dxl
- .eco
- .ecx
- .edb
- .epim
- .exb
- .fcd
- .fdb
- .fic
- .fmp
- .fmp12
- .fmpsl
- .fol
- .fol
- .fp4
- .fp5
- .fp7
- .fpt
- .frm
- .gdb
- .grdb
- .gwi
- .hdb
- .his
- .ib
- .idb
- .ihx
- .itdb
- .itw
- .jet
- .jtx
- .kdb
- .kexi
- .kexic
- .kexis
- .lgc
- .lwx
- .maf
- .maq
- .mar
- .mas
- .mav
- .mdb
- .mdf
- .mpd
- .mrg
- .mud
- .mwb
- .myd
- .ndf
- .nnt
- .nrmlib
- .ns2
- .ns3
- .ns4
- .nsf
- .nv
- .nv2
- .nwdb
- .nyf
- .odb
- .oqy
- .orx
- .owc
- .p96
- .p97
- .pan
- .pdb
- .pdm
- .pnz
- .qry
- .qvd
- .rbf
- .rctd
- .rod
- .rodx
- .rpd
- .rsd
- .sas7bdat
- .sbf
- .scx
- .sdb
- .sdc
- .sdf
- .sis
- .spq
- .sql
- .sqlite
- .sqlite3
- .sqlitedb
- .te
- .temx
- .tmd
- .tps
- .trc
- .trm
- .udb
- .udl
- .usr
- .v12
- .vis
- .vpd
- .vvv
- .wdb
- .wmdb
- .wrk
- .xdb
- .xld
- .xmlff
- .abcddb
- .abs
- .abx
- .accdw
- .adn
- .db2
- .fm5
- .hjt
- .icg
- .icr
- kdb
- .lut
- .maw
- .mdn
- .mdt
- It avoids encrypting files with the following extensions:
- .PLAY
- .exe
- .msi
- .dll
- .lnk
- .sys
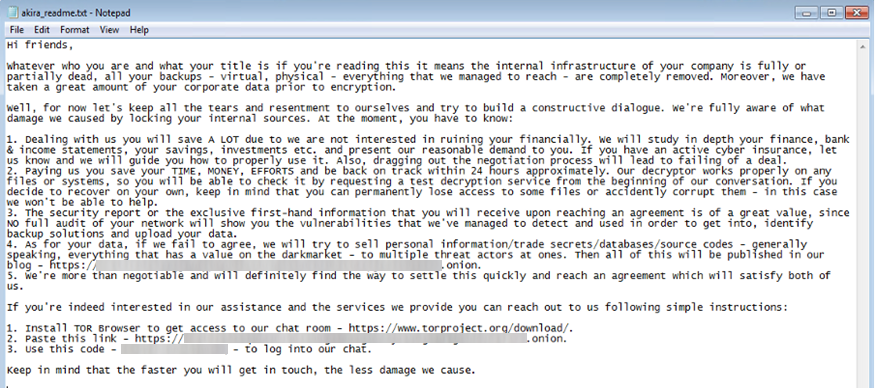
- It drops a ransom note:
akira_readme.txt
- It encrypts files using Chacha20 and encrypts the key using RSA encryption.
- Key generation:
- A ChaCha20 key and nonce are generated using CryptGenRandom
- Key encryption:
- It uses the embedded RSA public key to encrypt the generated Chacha20 key
- File encryption
- Files are encrypted using ChaCha20 encryption.
- The Akira ransomware supports three encryption modes depending on the file type and size:
- Full encryption
- Partial encryption
- Spot encryption
- Key generation:
- It appends this extension to encrypted files:
- .akira
- Hacktools
- PowerTool
- ADFind
MITRE tactics and techniques
| Initial Access | Persistence | Execution | Defense Evasion | Credential Access | Discovery | Command and Control | Lateral Movement | Exfiltration | Impact |
|---|---|---|---|---|---|---|---|---|---|
T1078 - Valid Accounts T1190 - Exploit Public-Facing Application | T1136.002 - Create Account: Domain Account | T1059 - Command and Scripting Interpreters | T1562.001 - Impair Defenses: Disable or Modify Tools | T1003.001 - OS Credential Dumping: LSASS Memory | T1082 - System Information Discovery T1069.002 - Permission Groups Discovery: Domain Groups T1018 - Remote System Discovery | T1219 - Remote Access Software | T1570 - Lateral Tool Transfer | T1567.002 - Exfiltration Over Web Service: Exfiltration to Cloud Storage T1048.003 - Exfiltration Over Alternative Protocol: Exfiltration Over Unencrypted Non-C2 Protocol | T1490 - Inhibit System Recovery T1486 - Data Encrypted for Impact |
Summary of malware, tools, and exploits used
| Initial Access | Defense Evasion | Discovery | Credential Access | Command and Control | Lateral Movement | Exfiltration |
|---|---|---|---|---|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
| |
|
|
|
| |||
|
| |||||
|
| |||||
|
Security recommendations
As experienced ransomware actors develop increasingly sophisticated ransomware families, organizations need to proactively protect themselves from evolving threats. As ransomware threats evolve and exploit vulnerabilities to target businesses around the world, organizations need to improve their security posture to avoid financial and reputational harm.
Here are some security best practices that can help organizations protect their mission-critical data from ransomware attacks:
Audit and inventory
- Take an inventory of assets and data.
- Identify authorized and unauthorized devices and software.
- Make an audit of event and incident logs.
Configure and monitor
- Manage hardware and software configurations.
- Grant admin privileges and access only when necessary to an employee’s role.
- Monitor network ports, protocols, and services.
- Activate security configurations on network infrastructure devices such as firewalls and routers.
- Establish a software allowlist that executes only legitimate applications.
Patch and update
- Conduct regular vulnerability assessments.
- Perform patching or virtual patching for operating systems and applications.
- Update software and applications to their latest versions.
Protect and recover
- Implement data protection, backup, and recovery measures.
- Enable multifactor authentication (MFA).
Secure and defend
- Employ sandbox analysis to block malicious emails.
- Deploy the latest versions of security solutions to all layers of the system, including email, endpoint, web, and network.
- Detect early signs of an attack such as the presence of suspicious tools in the system.
- Use advanced detection technologies such as those powered by artificial intelligence (AI) and machine learning.
Train and test
- Regularly train and assess employees in security skills.
- Conduct red-team exercises and penetration tests.
A multilayered approach can help organizations guard possible entry points into the system (endpoint, email, web, and network). Security solutions that can detect malicious components and suspicious behavior can also help protect enterprises.
- Trend Micro Vision One™ provides multilayered protection and behavior detection, which helps block questionable behavior and tools early on before the ransomware can do irreversible damage to the system.
- Trend Micro Cloud One™ Workload Security protects systems against both known and unknown threats that exploit vulnerabilities. This protection is made possible through techniques such as virtual patching and machine learning.
- Trend Micro™ Deep Discovery™ Email Inspector employs custom sandboxing and advanced analysis techniques to effectively block malicious emails, including phishing emails that can serve as entry points for ransomware.
- Trend Micro Apex One™ offers next-level automated threat detection and response against advanced concerns such as fileless threats and ransomware, ensuring the protection of endpoints.
Indicators of compromise (IOCs)
The IOCs for this article can be found here. Actual indicators might vary per attack.
Trend Micro Vision One Hunting Query
Trend Vision One customers can use the following hunting query to check if their network/system is possibly affected by Akira ransomware:
fullPath:(*.akira* OR *akira_readme.txt*)
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering



 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One