TrueCrypter Ransomware Now Accepting Amazon Gift Cards
During the last week of April 2016, a crypto-ransomware variant was spotted giving victims an alternative mode of payment besides the usual Bitcoin option. Reported by bleepingcomputer, TrueCrypter demands ransom in the form of Amazon gift cards or Bitcoins.
TrueCrypter uses several encryption methods such as AES, Caesar, and RSA to encrypt a victim’s files and demands .2 - .5 Bitcoins worth $94.36 to $235.89, or $115 USD in Amazon gift cards. The UI of TrueCrypter is fairly simple and straightforward. It also changes the wallpaper to a ransom note. However, users have to wait 24 - 48 hours for the files to be decrypted after payment because the threat actor has to process the payment manually.
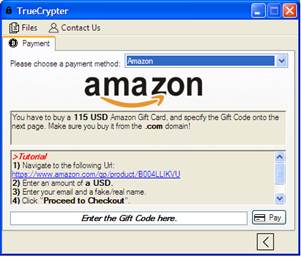
The sample acquired by Trend Micro was buggy and did not encrypt any file, even though it had anti-emulation and anti-debugging techniques written into it. While these broken codes were seen as a sign that the program may have been written by an amateur, it can also be assumed that the version of TrueCrypter found may still be in the testing stage.
As for the odd payment choice of Amazon gift cards, the transaction involving a gift card is a first in crypto-ransomware, but not in the world of cybercrime in general. In the cybercriminal underground, gift cards are one of the many wares that can be bought and sold. Among other commodities that can be bought and sold include other pre-paid gift cards, private accounts for services such as Uber and Netflix, credit card data, and debit card data.
The case of TrueCrypter proves that crypto-ransomware is slowly evolving. Right now, it could be accommodating new modes of payment. Tomorrow, we might see something nastier. That’s why users should know what ransomware is and how protect yourself from it.
[More: Ransomware: What It Is and How You Can Protect Yourself]
Infection vectors of crypto-ransomware varies a great deal. Trend Micro Security can block dangerous websites, including harmful links found in websites, social networks, emails and instant messages, and safeguards against viruses, phishing, and other online threats.
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
последний
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026
The AI-fication of Cyberthreats: Trend Micro Security Predictions for 2026 Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One