The Sprawling Reach of Complex Threats
Complex and persistent threats riddled the cybersecurity landscape of 2019. Ransomware attacks found a niche in high-profile targets, while phishing scams came up with novel subterfuges. Vulnerabilities in a widely used software protocol were thrown into sharp relief, while threats to third-party services and tools highlighted the importance of security at all nodes of a supply chain.
Our annual security roundup examines these and other important security issues that emerged in the past year, and provides insights to help enterprises navigate across an increasingly precarious threat landscape.
Ransomware
High-profile targets
Aside from the perennially plagued healthcare sector, the government and the education sectors notably bore the brunt of ransomware operators’ more targeted approach. In the U.S., in particular, ransomware hit such high-profile victims as cities in California, Georgia, Michigan, Maryland, and Florida, and public school districts in Louisiana whose disruptions led to a state of emergency.
A likely contributor to this trend was the willingness of many organizations to pay ransoms so as to speed up the recovery of their data and systems. This inclination might have even been bolstered by their insurance coverage for ransomware attacks. For example, a county in Indiana, after its operations were paralyzed by ransomware, agreed to pay a six-figure ransom, over three-quarters of which was covered by the county’s insurance provider.

The ransom amounts demanded by the attackers, paid by the victim organization, and covered by the insurance provider in the case of LaPorte County, Indiana
Sly capabilities
It seemed that threat actors had found a firmer footing in selective targeting than in creating new forms of ransomware. While there was an increase from the previous year, albeit slight, in our detections of ransomware-related threats last year, the number of new ransomware families in 2019 was fewer than half of the corresponding number in 2018.
Despite their relatively low number, however, the new ransomware families included several that exhibited notable characteristics beyond the usual data encryption.
Year-on-year comparison of the number of detections of ransomware-related threats
Year-on-year comparison of the number of detections of new ransomware families
MAZE
Can automatically copy all affected files to operator-controlled servers
SNATCH
Can force Windows machines to reboot into safe mode so as to bypass security software and avoid detection
ZEPPELIN
Can terminate various processes and has target-customized ransom notes
Notable ransomware families that emerged in 2019
Messaging Threats
Phishing scams
The widespread use by enterprises of Microsoft Office 365, which crossed the 200 million monthly active users mark last year, continued to motivate scammers to launch phishing campaigns that spoofed the software suite, particularly its email component, Outlook. This was reflected in the number of unique Office 365-related URLs that we blocked, which doubled from the previous year.
However, the growing number of enterprise users switching to Slack and other newer messaging platforms as alternatives to email might have contributed to the drop in our detections of overall phishing-related URLs.

Year-on-year comparison of blocked unique Office 365-related phishing URLs
Year-on-year comparison of the number of instances of blocked access to non-unique phishing URLs (e.g., three instances of blocked access to the same URL counted as three)
With enterprises increasingly becoming wary of phishing threats, which traditionally arrive via email, scammers continued to come up with new ways of deceiving victims into giving up their sensitive information.
Abusing the SingleFile web extension
Identical copies of legitimate login pages created using the extension dupe victims into entering their credentials.
Compromising one-time passwords (OTPs)
A bogus online banking page tricks victims into entering their credentials and OTPs.
Hijacking web search results
Poisoned Google search results redirect victims to a phishing page.
Customizing “404 Not Found” pages
Error pages pose as login forms to steal victims’ credentials.
New techniques used in phishing campaigns in 2019
BEC attempts
Business email compromise (BEC) is a social engineering scheme that typically involves the impersonation of a person of authority in an organization to trick another member into transferring funds into a fraudulent account. In 2019, the top five spoofed positions in the BEC attempts that we detected were unsurprisingly high-ranking ones. But among the top five targeted positions, along with the usual financial higher-ups, were accountant and professor, supporting our security prediction for 2019 that BEC scammers would target employees several levels down the company hierarchy. This appeared to be the case particularly in the education sector, where a number of BEC attacks were reported in the past year.
Distribution of targeted positions in BEC attempts detected in 2019
VULNERABILITIES
RDP flaws
BlueKeep, a critical vulnerability (CVE-2019-0708) in Microsoft’s Remote Desktop Protocol (RDP), made headlines for its “wormability,” which could allow the rapid spread of malware in a manner similar to how WannaCry infected systems around the world in 2017. If successfully exploited, BlueKeep — which affects the legacy systems Windows 7, Windows 2003, Windows Server 2008 R2, Windows Server 2008, and Windows XP — could be used for remote code execution attacks.
A BlueKeep exploit was found in a campaign that installed and ensured the persistence of malicious cryptocurrency miners. But while this campaign did not exhibit the self-propagation capability that BlueKeep had been expected to facilitate, Microsoft maintained that future exploits could exact more damage and reiterated the importance of patching vulnerable systems. Despite BlueKeep’s severity, however, more than 800,000 vulnerable systems were still found unpatched two months after its disclosure.

The number of disclosed RDP-related vulnerabilities from May to December 2019
If nothing else, the discovery of BlueKeep brought attention to vulnerabilities in RDP, a number of which were disclosed in its wake. RDP enables enterprises to operate with better flexibility via remote access, but a successful exploit could negate this advantage, allowing threat actors to take control over enterprise systems.
IoT botnets
Dealing with vulnerabilities remained one of the challenges faced by the internet of things (IoT), given that patching devices could be quite slow and problematic. Threat actors knew this all too well in 2019, as evidenced by the prevalence of IoT botnets that used the same old and known vulnerabilities in their exploits.
| Echobot | Hakai | Mirai | Momentum | Neko | Yowai | ||
| CVE-2014-8361 (Realtek SDK-based routers) | |||||||
| CVE-2016-6277 (Netgear R6400 and R7000 routers) | |||||||
| CVE-2017-17215 (Huawei HG532 routers) | |||||||
Three vulnerabilities used by multiple IoT botnets in 2019
IoT botnets are also known for brute-force attacks, in which they try out a large number of consecutive login credential guesses to gain access to unsecure devices. They typically use leaked, common, or even default usernames and passwords for their brute-force attempts, taking advantage of many IoT adopters’ failure to change and update their devices’ credentials. In 2019, the number of brute-force logins we detected was nearly triple the corresponding count in 2018.
Year-on-year comparison of the number of triggered inbound and outbound events involving brute-force logins
SUPPLY CHAIN ATTACKS
E-commerce site compromise
Supply chain attacks, which compromise a service or organization through an external partner or third-party provider that has access to its data or systems, gained prominence thanks to campaigns involving a consortium of hacking groups called Magecart. These groups compromise e-commerce websites usually by going after their third-party shopping cart systems to steal customer payment card information.
One such group is Magecart Group 12, which infected hundreds of e-commerce sites by first attacking their third-party advertising service provider. Another is FIN6, which compromised thousands of online shops hosted on a popular e-commerce platform.

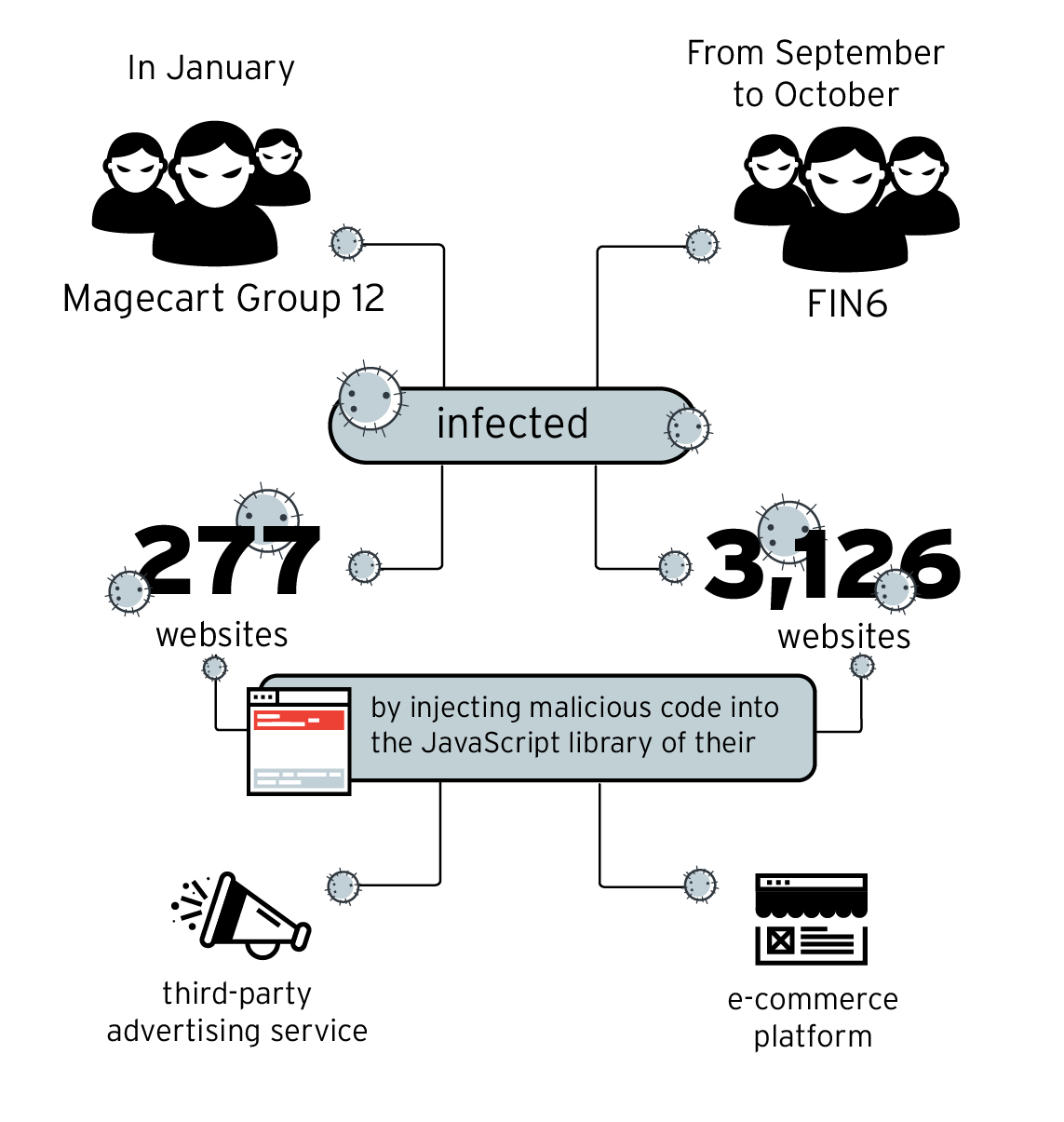
E-commerce site compromise campaigns carried out by Magecart Group 12 and FIN6 in 2019
Threats to software development tools
Threat actors can undermine the development pipeline of an enterprise by interfering with a part of its software supply chain. And gaps in DevOps tools and platforms, which streamline the development and deployment of software, could enable them to that end.
Kubernetes, a container orchestration system, disclosed a high-severity vulnerability in its command-line interface that could allow an attacker to use a malicious container to create or replace files in an affected workstation. And we discovered flaws in Jenkins, an automation server, including one that could allow remote code execution and four others that could lead to the theft of sensitive user credentials. More than 2,000 hosts on the container platform Docker were also found infected by a cryptocurrency-mining worm.
Threat Landscape
Half-year comparison of the numbers of email, file, and URL threats blocked in 2019
Half-year comparison of the number of fileless events blocked in 2019
Half-year comparison of the number of malicious Android apps blocked in 2019
To be able to thwart these and other complex and persistent threats, enterprises should choose solutions that can detect malicious activity across gateways, networks, servers, and endpoints. They should consider a multilayered strategy, couple with industry best practices, for addressing security gaps and preventing cyberattacks that could have an impact on their operations, reputations, and bottom lines.
For more insights into the most important cybersecurity issues of 2019 and their corresponding solutions, read our full report, "The Sprawling Reach of Complex Threats."

Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Artículos Recientes
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering
- AI Security Starts Here: The Essentials for Every Organization

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One