 Download What Decision-Makers Need to Know About Ransomware Risk
Download What Decision-Makers Need to Know About Ransomware Risk
By Vladimir Kropotov, Bakuei Matsukawa, Robert McArdle, Fyodor Yarochkin, Shingo Matsugaya (Trend Micro), Erin Burns, Eireann Leverett (Waratah Analytics)
Ransomware has become a different animal over the years, made a more insidious threat by attackers who have turned to increasingly sophisticated playbooks and a slew of payment options at their disposal. As part of its continuous evolution, it now takes a holistic approach to better grasp the complexities of the current-day ransomware ecosystem.
In this joint research, “What Decision-Makers Need to Know About Ransomware Risk: Data Science Applied to Ransomware Ecosystem Analysis,” researchers at Trend Micro and Waratah Analytics investigated strategic, tactical, operational, and technical threat intelligence to find emerging trends and developments in the ransomware landscape. The authors collected data from a multitude of sources, including ransomware group leak sites, network-based and host-based telemetry, cryptocurrency transactions, and leaked internal chat logs, which allowed them to understand how ransomware groups operate from different angles.
Using data-science experiments and visualization tools to map out ransomware-related activity allowed the researchers behind this paper to determine changes in ransomware groups’ scope of targets, compare similarities in their business processes, and ascertain difficulties in their day-to-day operations like the procurement of ransom payments. The methodologies laid out in this paper provide a snapshot of the goings-on in present-day ransomware circles, but more importantly, detail how these data-science approaches can be used to help defenders in their own investigation of ransomware risks to their organizations.
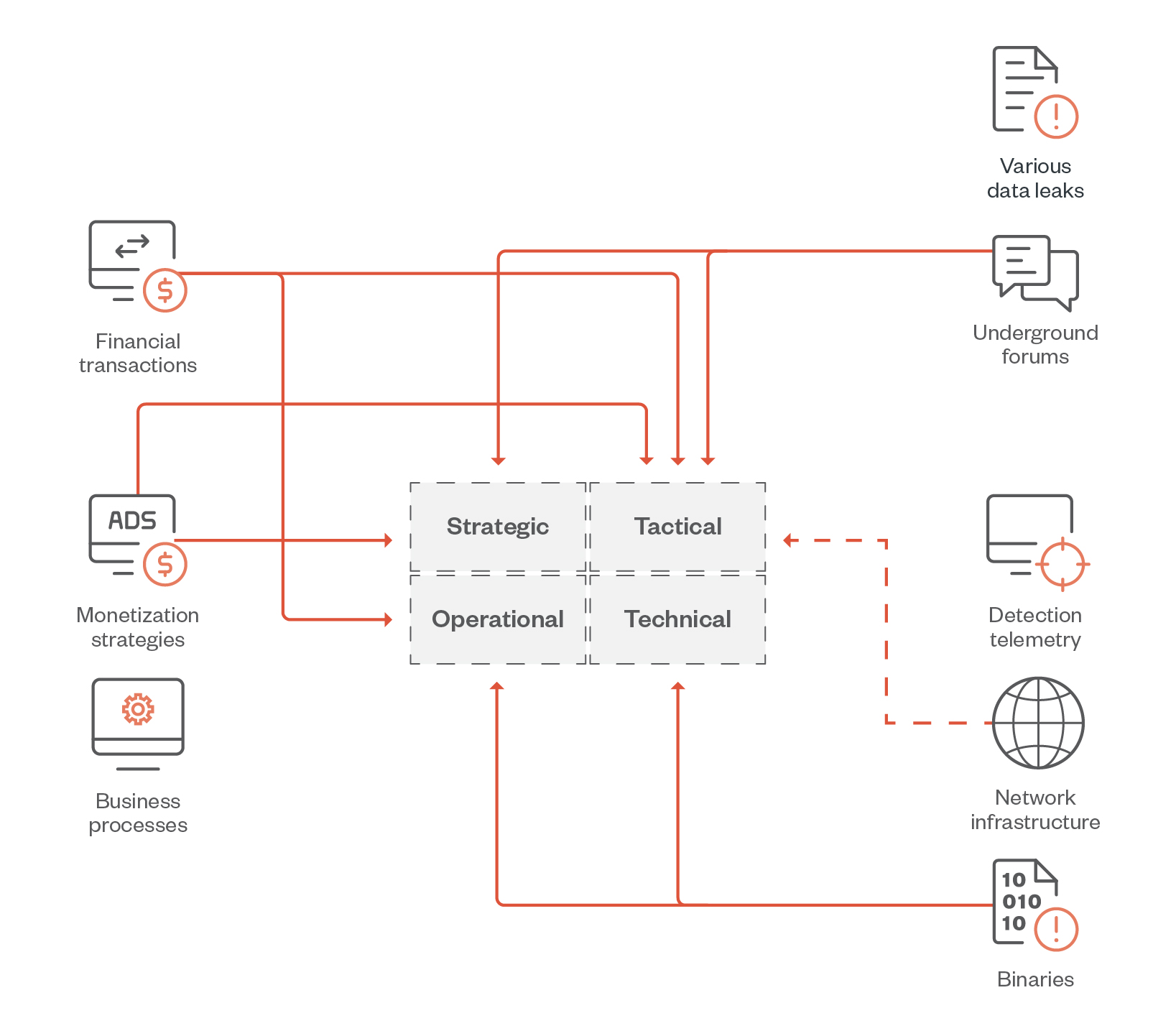
Figure 1. The data sources used in this research and the types of threat intelligence they provide
Victims who pay cover the operational costs of attacks on those who don't
Ransomware attacks are often financially driven, and the operational costs of ransomware groups vary depending on their business model. These costs can be used to predict the primary tactics, techniques, and procedures (TTPs) that a ransomware group uses. Most groups have moved past the days when ransomware payments were limited to locally available financial capabilities; more recent business models have adapted to the emergence of cryptocurrency. Nowadays, some groups opt to launch volume-based attacks and demand a fixed ransom amount from all their victims, whereas others set ransom amounts based on targeted profiling of their victims, including knowledge of a victim’s income.
This is best illustrated in the case of LockBit and the historic Conti, whose ransom payment rates are both at 16%, likely because these ransomware groups operate with a highly targeted business model. This is notably higher than groups that have a more volume-based model such as the DeadBolt ransomware, which has a payment rate that peaked at 8%. It’s important to note that most victims do not pay the ransoms — the few that do are, in effect, covering the cost of future ransomware attacks on another six to 10 victims, as the paid ransom amount covers the cost of operations for attacks on those who do not pay.
Ransomware risk varies across regions, industries, and organization size
The distribution of risk of ransomware attacks is not homogenous: There are a multitude of deciding factors that might explain why organizations in some lines of business and countries are targeted more than others. These include any government interventions that might hamper ransom payment collection, communication, and language issues that might arise between attackers and potential victims, as well as the attackers’ political ties — all of which help cybercriminals determine where to strike next.
This is demonstrated by our analysis of Conti and LockBit’s leak sites, which revealed that ransom payment rates differ among victims. For example, between these two ransomware groups, Europe had the lowest payment rate regionally at 11.1%, whereas Africa had a comparatively high rate at 34.8%. In terms of organization size, larger companies overall exhibited lower payment rates, while ransomware victims in the finance and legal industries tended to pay the ransom compared to other industries. Attackers are also aware that certain industries and countries that pay ransoms also tend to pay more often, so organizations belonging to those industries and countries are also more likely to find themselves at the receiving end of ransomware attacks.
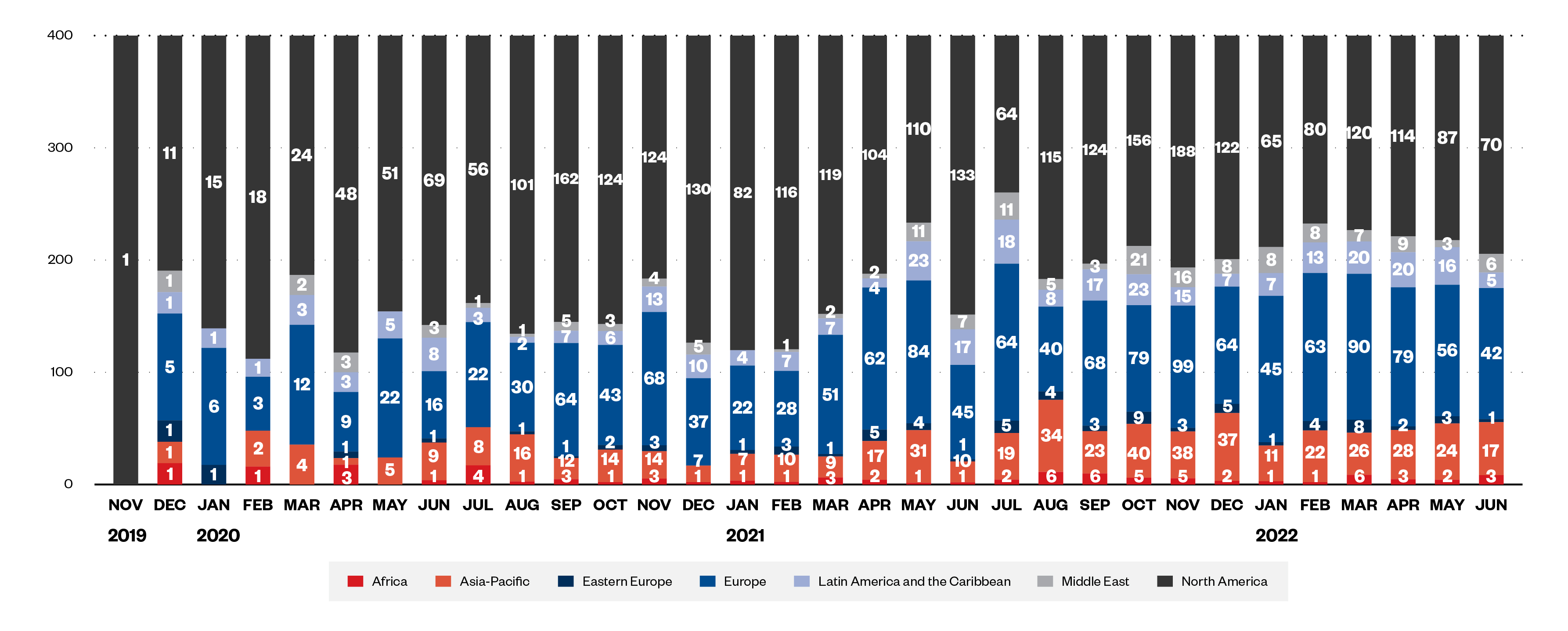
Figure 2. Ransomware targets by region from November 2019 to June 2022
Most ransomware victims don’t pay up — but those that do, pay fast
Non-payment is not only a viable option for victims but also the norm. After all, ransomware actors don’t profit from most of their attacks and are keenly aware that the longer ransom negotiations go on, the less likely they are to see a payout at all. To illustrate this point, a survivor analysis of the ransom payments for DeadBolt ransomware attacks showed that among the victims who paid, over 50% did so within 20 days, while 75% paid within 40 days.
For victims whose income relies on systems that have been affected by a ransomware attack, these systems must be fixed quickly, which explains the speed with which these victims concede to ransom demands. However, it’s important to note that paying the ransom only drives up the overall incident cost for victims: Even the eventual decryption of their data upon payment won’t undo the business disruption and brand reputation damage that a victim organization might have already suffered from the attack.
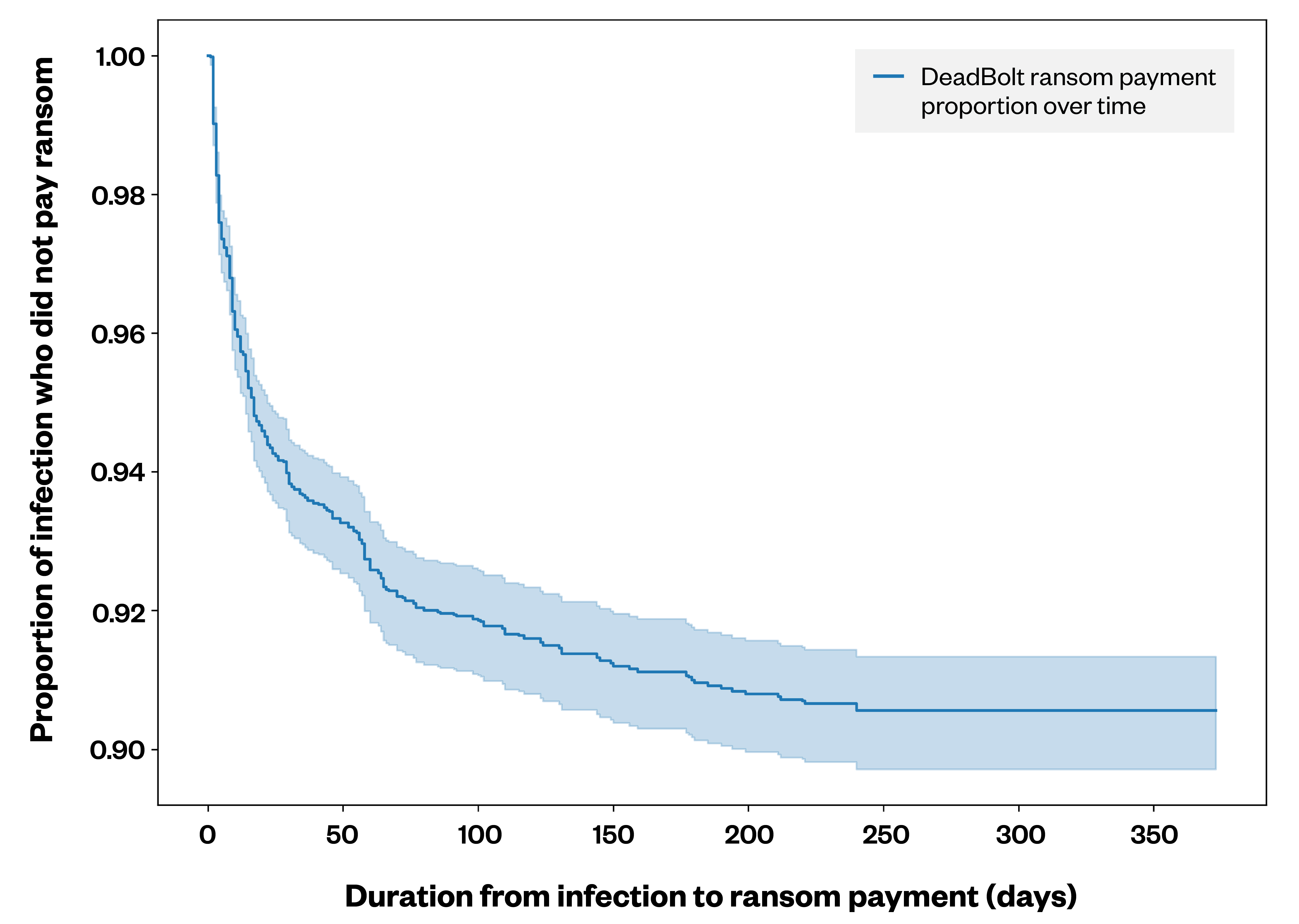
Figure 3. A Kaplan-Meier curve depicting the percentage of DeadBolt ransomware victims who paid the ransom versus the number of days until payment was made
Challengers are gunning for top spots in the ransomware arena
Our investigation of the leak sites of 69 ransomware groups demonstrated that, on average, a new victim’s data was leaked approximately every four days. Of these, the top 30 groups could be organized into four categories based on their victim count and the frequency with which they leak stolen victim data:
- Core groups are those that have been active for over a year, have over 300 leaks on their sites, and release new leaks every three days or less on average.
- Legends are no longer active but have more than 300 total leaks; they also used to release new leaks every three days or less.
- Regulars have been active for more than a year, have less than 300 leaks in total, and release new leaks more than every three days.
- Challengers have been active for less than a year and have less than 300 leaks in total. However, unlike regular groups, the periods between their leaks vary, so these groups need to be more closely monitored.
Using these categories to classify groups can enable incident responders and decision-makers to assess the state of the ransomware landscape, pinpointing any up-and-coming cybercriminal operations that might shape up to be a bigger threat in the future.
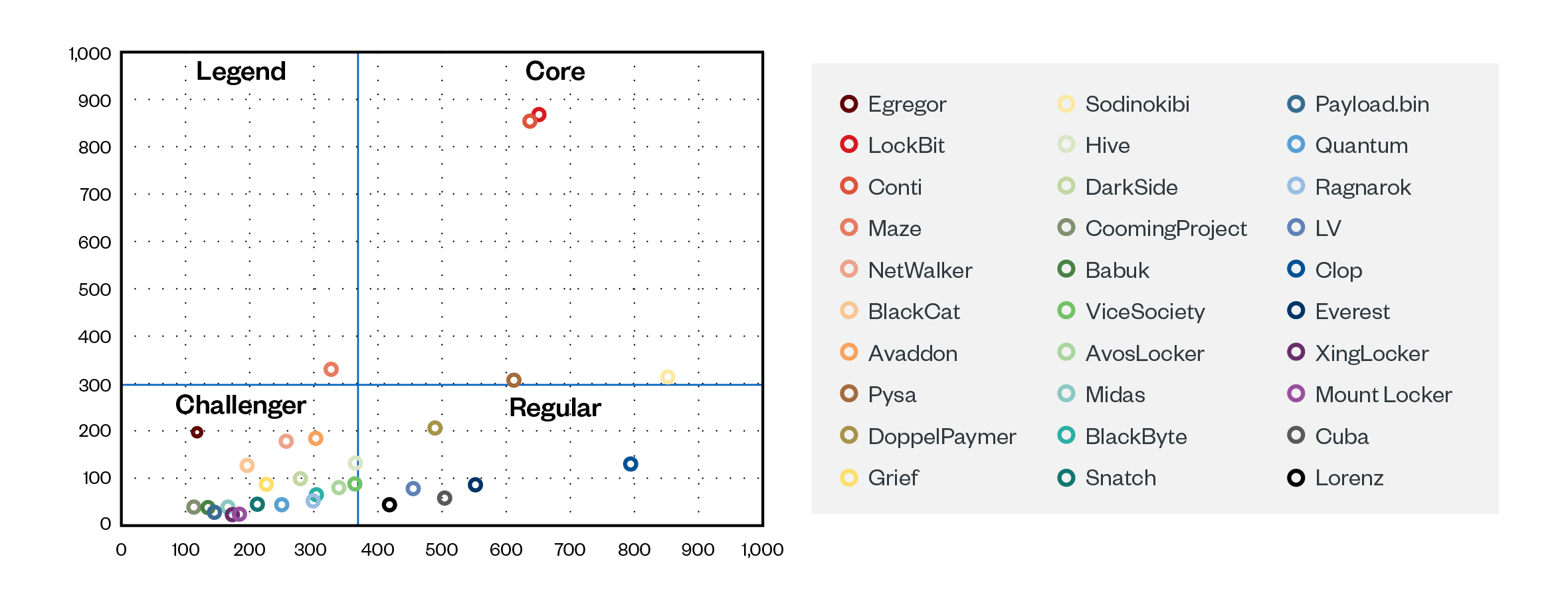
Figure 4. Grouping ransomware groups by duration days and victim counts
Mitigating ransomware attacks with a zero-trust approach
While there is no silver-bullet solution to ransomware, a zero-trust approach can help organizations detect malicious activity and minimize the impact of these cyberattacks. Implementing zero trust can help defenders profile known ransomware indicators so that they are better informed when updating their security policies and developing new alert rules. Defenders can also be informed immediately upon any signs of suspicious behavior in their organization’s systems, such as any of the following:
- Detection of outliers in pre-established profiles of what are considered normal encryption patterns, algorithms, and key lengths within an organization’s network.
- Detection of anomalous behavior in interhost connectivity profiles, as hosts should have set behaviors with regard to connections, communication peers, volume of transferred data, and the like.
- Detection of a 50/50 read-write ratio when files are encrypted on the host, as this could be outside the host’s normal behavior.
- Detection of partial encryption of files, as this is used by some ransomware families for speed optimization purposes.
Because there are so many variables that contribute to ransomware risk, it might be difficult for any one organization to fully fathom it from the perspective of just its own location and industry. Cross-country collaboration among business leaders and policymakers to create friction at any point in a ransomware group’s business processes can go a long way toward impeding these cybercriminals’ operations. To gain a better understanding of the intricacies that shape this cyberthreat, read our research paper, “What Decision-Makers Need to Know About Ransomware Risk: Data Science Applied to Ransomware Ecosystem Analysis.”
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Artículos Recientes
- They Don’t Build the Gun, They Sell the Bullets: An Update on the State of Criminal AI
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One