The Evolution of PoS RAM Scraper Malware
 View research paper: PoS RAM Scraper Malware: Past, Present, and Future
View research paper: PoS RAM Scraper Malware: Past, Present, and Future
Cybercriminals these days are more likely to go after data keepers than mere data owners because this gives them more bang for their buck. In the case of point-of-sale (PoS) RAM scrapers, that means going after the world’s biggest retailers instead of individual credit card users. Most recent case in point? The Home Depot breach put the personal credentials of 56 million credit card users at risk.
This research paper on Pos RAM scrapers takes an in-depth look at the past, present, and future of one of today’s biggest security threats. It shows what happens to the data in the magnetic stripe of your credit card after it’s swiped to pay for products and services. We also traced how today’s PoS RAM scrapers evolved to become industrialized threats from simple beginnings by analyzing some of the most well-known malware families since 2008. All of these helped us predict what the next generation of PoS RAM scrapers will be like and allow us to protect Trend Micro product users from the threats they currently pose.
It’s not surprising that the United States topped the list of most PoS-RAM-scraper-affected countries, as the country’s economy is heavily geared toward buying goods and services using credit cards. Consumers in other countries still tend to use cash or debit cards more than credit cards.
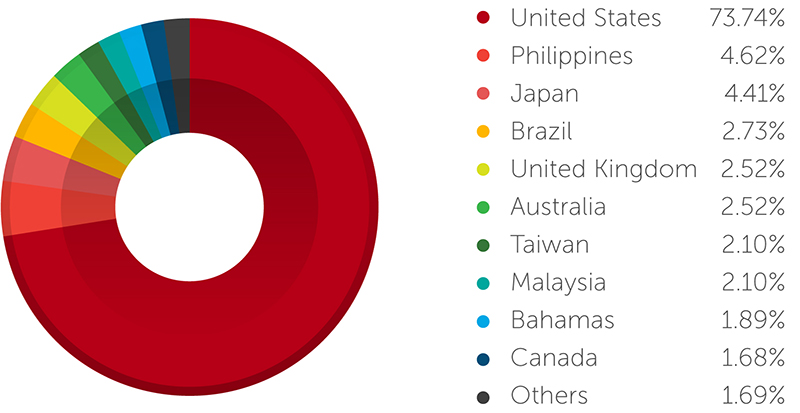
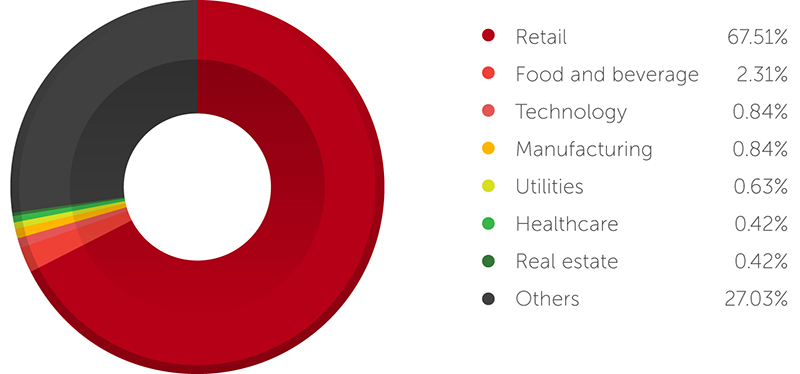
Figure 2: PoS RAM scraper detection distribution by industry
Note: The data in the figures represents the Trend Micro customer base and may not accurately present a view of the entire spectrum, but it does provide a good approximation of observed general trends
Like Verizon’s findings, our data also revealed that most PoS attacks target retailers. Since they handle huge volumes of credit card transactions, it makes them lucrative targets. Besides, compromising a single PoS system usually yields data for thousands of credit cards and is preferable to infecting thousands of victims’ systems in hopes of stealing their card data
Unlike the first PoS RAM scraper seen in 2008, which tried installing debugging tools on PoS systems to dump credit card data from their RAM, today’s scrapers use multiple components and exfiltration techniques; single binaries; network, bot, and kill-switch functionality; encryption; and development kits.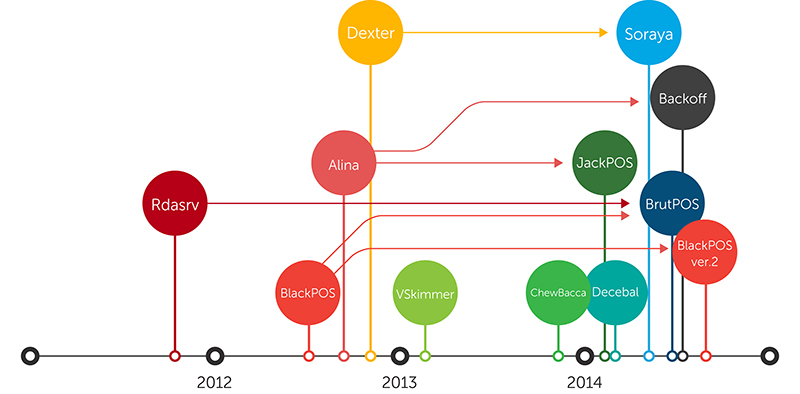
Figure 3: PoS RAM scraper family tree [click to enlarge]
Note: A malware variant may have existed long before its discovery. Tracking exact discovery dates is extremely difficult to do. Almost four years’ worth of PoS RAM scrapers were available to study for traits though.
We uncovered PoS RAM scrapers’ past and present versions and found that they collect and exfiltrate system information. They also have bot functionality, which means they can receive commands remotely sent by attackers. Using memory snapshots, blacklists, and custom search functions proved to be the most efficient ways to harvest credit card data. HTTP POST requests, meanwhile, were the preferred data-exfiltration method used by both pre- and 2014 PoS RAM scrapers because these aren’t cached nor saved in history and don’t have data-sending length restrictions.
New credit card technologies are being introduced in the North American market to help curb fraud and better secure transactions. Though these will help reduce counterfeiting and lost or stolen credit card fraud, they can’t prevent PoS RAM scraper attacks. Their use will also introduce new attack vectors that cybercriminals can exploit to steal credit card data.
That said, we believe that Bob Russo’s Statement for the Record is accurate, “Our work is broad for a simple reason: there is no single answer to securing payment card data. No one technology is a panacea; security requires a multilayered approach across the payment chain.”
For more details on, in-depth analyses of, and tips to stay safe from PoS RAM scrapers and related attacks, read “PoS RAM Scraper Malware: Past, Present, and Future.”
Like it? Add this infographic to your site:
1. Click on the box below. 2. Press Ctrl+A to select all. 3. Press Ctrl+C to copy. 4. Paste the code into your page (Ctrl+V).
Image will appear the same size as you see above.
Artículos Recientes
- How Unmanaged AI Adoption Puts Your Enterprise at Risk
- Estimating Future Risk Outbreaks at Scale in Real-World Deployments
- The Next Phase of Cybercrime: Agentic AI and the Shift to Autonomous Criminal Operations
- Reimagining Fraud Operations: The Rise of AI-Powered Scam Assembly Lines
- The Devil Reviews Xanthorox: A Criminal-Focused Analysis of the Latest Malicious LLM Offering

 Complexity and Visibility Gaps in Power Automate
Complexity and Visibility Gaps in Power Automate AI Security Starts Here: The Essentials for Every Organization
AI Security Starts Here: The Essentials for Every Organization Ransomware Spotlight: DragonForce
Ransomware Spotlight: DragonForce Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One
Stay Ahead of AI Threats: Secure LLM Applications With Trend Vision One